Downgrade
4 minutos de lectura
Se nos proporcionan un montón de logs de Eventos de Windows (archivos .evtx):
$ tree Logs
Logs
├── Application.evtx
├── HardwareEvents.evtx
├── Internet Explorer.evtx
├── Key Management Service.evtx
├── Microsoft-Windows-AppModel-Runtime%4Admin.evtx
├── Microsoft-Windows-AppReadiness%4Admin.evtx
├── Microsoft-Windows-AppReadiness%4Operational.evtx
├── Microsoft-Windows-AppXDeployment%4Operational.evtx
├── Microsoft-Windows-AppXDeploymentServer%4Operational.evtx
├── Microsoft-Windows-AppXDeploymentServer%4Restricted.evtx
├── Microsoft-Windows-ApplicationResourceManagementSystem%4Operational.evtx
├── Microsoft-Windows-Bits-Client%4Operational.evtx
├── Microsoft-Windows-CodeIntegrity%4Operational.evtx
├── Microsoft-Windows-Compat-Appraiser%4Operational.evtx
├── Microsoft-Windows-CoreApplication%4Operational.evtx
├── Microsoft-Windows-Crypto-DPAPI%4BackUpKeySvc.evtx
├── Microsoft-Windows-Crypto-DPAPI%4Operational.evtx
├── Microsoft-Windows-DSC%4Admin.evtx
├── Microsoft-Windows-DSC%4Operational.evtx
├── Microsoft-Windows-DataIntegrityScan%4Admin.evtx
├── Microsoft-Windows-DataIntegrityScan%4CrashRecovery.evtx
├── Microsoft-Windows-DeviceSetupManager%4Admin.evtx
├── Microsoft-Windows-DeviceSetupManager%4Operational.evtx
├── Microsoft-Windows-Dhcp-Client%4Admin.evtx
├── Microsoft-Windows-Dhcpv6-Client%4Admin.evtx
├── Microsoft-Windows-Diagnosis-DPS%4Operational.evtx
├── Microsoft-Windows-Forwarding%4Operational.evtx
├── Microsoft-Windows-GroupPolicy%4Operational.evtx
├── Microsoft-Windows-HomeGroup Control Panel%4Operational.evtx
├── Microsoft-Windows-International%4Operational.evtx
├── Microsoft-Windows-Iphlpsvc%4Operational.evtx
├── Microsoft-Windows-Kernel-ApphelpCache%4Operational.evtx
├── Microsoft-Windows-Kernel-Boot%4Operational.evtx
├── Microsoft-Windows-Kernel-EventTracing%4Admin.evtx
├── Microsoft-Windows-Kernel-PnP%4Configuration.evtx
├── Microsoft-Windows-Kernel-PnPConfig%4Configuration.evtx
├── Microsoft-Windows-Kernel-Power%4Thermal-Operational.evtx
├── Microsoft-Windows-Kernel-ShimEngine%4Operational.evtx
├── Microsoft-Windows-Kernel-StoreMgr%4Operational.evtx
├── Microsoft-Windows-Kernel-WDI%4Operational.evtx
├── Microsoft-Windows-Kernel-WHEA%4Errors.evtx
├── Microsoft-Windows-Kernel-WHEA%4Operational.evtx
├── Microsoft-Windows-Known Folders API Service.evtx
├── Microsoft-Windows-LanguagePackSetup%4Operational.evtx
├── Microsoft-Windows-MUI%4Admin.evtx
├── Microsoft-Windows-MUI%4Operational.evtx
├── Microsoft-Windows-MiStreamProvider%4Operational.evtx
├── Microsoft-Windows-NCSI%4Operational.evtx
├── Microsoft-Windows-NetworkAccessProtection%4WHC.evtx
├── Microsoft-Windows-NetworkProfile%4Operational.evtx
├── Microsoft-Windows-NetworkProvider%4Operational.evtx
├── Microsoft-Windows-Ntfs%4Operational.evtx
├── Microsoft-Windows-Ntfs%4WHC.evtx
├── Microsoft-Windows-PowerShell%4Admin.evtx
├── Microsoft-Windows-PowerShell%4Operational.evtx
├── Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager%4Operational.evtx
├── Microsoft-Windows-Powershell-DesiredStateConfiguration-PullServer%4Operational.evtx
├── Microsoft-Windows-PrintService%4Admin.evtx
├── Microsoft-Windows-RemoteDesktopServices-RdpCoreTS%4Admin.evtx
├── Microsoft-Windows-RemoteDesktopServices-RdpCoreTS%4Operational.evtx
├── Microsoft-Windows-Resource-Exhaustion-Detector%4Operational.evtx
├── Microsoft-Windows-RestartManager%4Operational.evtx
├── Microsoft-Windows-SMBClient%4Operational.evtx
├── Microsoft-Windows-SMBServer%4Audit.evtx
├── Microsoft-Windows-SMBServer%4Connectivity.evtx
├── Microsoft-Windows-SMBServer%4Operational.evtx
├── Microsoft-Windows-SMBServer%4Security.evtx
├── Microsoft-Windows-Security-SPP-UX-Notifications%4ActionCenter.evtx
├── Microsoft-Windows-ServerManager-DeploymentProvider%4Operational.evtx
├── Microsoft-Windows-ServerManager-MgmtProvider%4Operational.evtx
├── Microsoft-Windows-ServerManager-MultiMachine%4Admin.evtx
├── Microsoft-Windows-ServerManager-MultiMachine%4Operational.evtx
├── Microsoft-Windows-Shell-ConnectedAccountState%4ActionCenter.evtx
├── Microsoft-Windows-Shell-Core%4ActionCenter.evtx
├── Microsoft-Windows-Shell-Core%4Operational.evtx
├── Microsoft-Windows-SmartCard-DeviceEnum%4Operational.evtx
├── Microsoft-Windows-SmbClient%4Connectivity.evtx
├── Microsoft-Windows-SmbClient%4Security.evtx
├── Microsoft-Windows-Storage-Tiering%4Admin.evtx
├── Microsoft-Windows-StorageSpaces-Driver%4Diagnostic.evtx
├── Microsoft-Windows-StorageSpaces-Driver%4Operational.evtx
├── Microsoft-Windows-StorageSpaces-ManagementAgent%4WHC.evtx
├── Microsoft-Windows-TWinUI%4Operational.evtx
├── Microsoft-Windows-TZSync%4Operational.evtx
├── Microsoft-Windows-TaskScheduler%4Maintenance.evtx
├── Microsoft-Windows-TaskScheduler%4Operational.evtx
├── Microsoft-Windows-TerminalServices-LocalSessionManager%4Admin.evtx
├── Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
├── Microsoft-Windows-TerminalServices-Printers%4Admin.evtx
├── Microsoft-Windows-TerminalServices-Printers%4Operational.evtx
├── Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx
├── Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx
├── Microsoft-Windows-UAC%4Operational.evtx
├── Microsoft-Windows-User Profile Service%4Operational.evtx
├── Microsoft-Windows-User-Loader%4Operational.evtx
├── Microsoft-Windows-UserPnp%4ActionCenter.evtx
├── Microsoft-Windows-UserPnp%4DeviceInstall.evtx
├── Microsoft-Windows-WER-Diag%4Operational.evtx
├── Microsoft-Windows-WMI-Activity%4Operational.evtx
├── Microsoft-Windows-Wcmsvc%4Operational.evtx
├── Microsoft-Windows-WinINet-Config%4ProxyConfigChanged.evtx
├── Microsoft-Windows-WinRM%4Operational.evtx
├── Microsoft-Windows-Windows Firewall With Advanced Security%4ConnectionSecurity.evtx
├── Microsoft-Windows-Windows Firewall With Advanced Security%4Firewall.evtx
├── Microsoft-Windows-WindowsUpdateClient%4Operational.evtx
├── Microsoft-Windows-Winlogon%4Operational.evtx
├── OpenSSH%4Admin.evtx
├── OpenSSH%4Operational.evtx
├── Security.evtx
├── Setup.evtx
├── System.evtx
├── Windows PowerShell.evtx
└── WitnessClientAdmin.evtx
0 directories, 113 files
También tenemos una instancia remota a la que conectarnos para contestar algunas preguntas.
Información básica de logs de Windows
$ nc 178.62.85.130 31120
+-----------+---------------------------------------------------------+
| Title | Description |
+-----------+---------------------------------------------------------+
| Downgrade | During recent auditing, we noticed that |
| | network authentication is not forced upon remote |
| | connections to our Windows 2012 server. That |
| | led us to investigate our system for |
| | suspicious logins further. Provided the server's event |
| | logs, can you find any suspicious successful |
| | login? |
+-----------+---------------------------------------------------------+
Which event log contains information about logon and logoff events? (for example: Setup)
>
Existen cinco logs principales en Windows:
- Aplicación
- Sistema
- Seguridad
- Instalación
- Eventos reenviados
El que aporta información sobre logon y logoff es Seguridad (o Security en inglés):
Which event log contains information about logon and logoff events? (for example: Setup)
> security
[+] Correct!
What is the event id for logs for a successful logon to a local computer? (for example: 1337)
>
Si buscamos por este identificador de evento, veremos que es el 4624 (más información aquí):
What is the event id for logs for a successful logon to a local computer? (for example: 1337)
> 4624
[+] Correct!
Which is the default Active Directory authentication protocol? (for example: http)
>
Esta pregunta es bien sabida para aquellos que resuelven máquinas Windows en Hack The Box…
Which is the default Active Directory authentication protocol? (for example: http)
> kerberos
[+] Correct!
Looking at all the logon events, what is the AuthPackage that stands out as different from all the rest? (for example: http)
>
Inspecciando los eventos
En este punto, podemos abrir el Visor de Eventos de Windows para inspeccionar los eventos de Security.evtx:
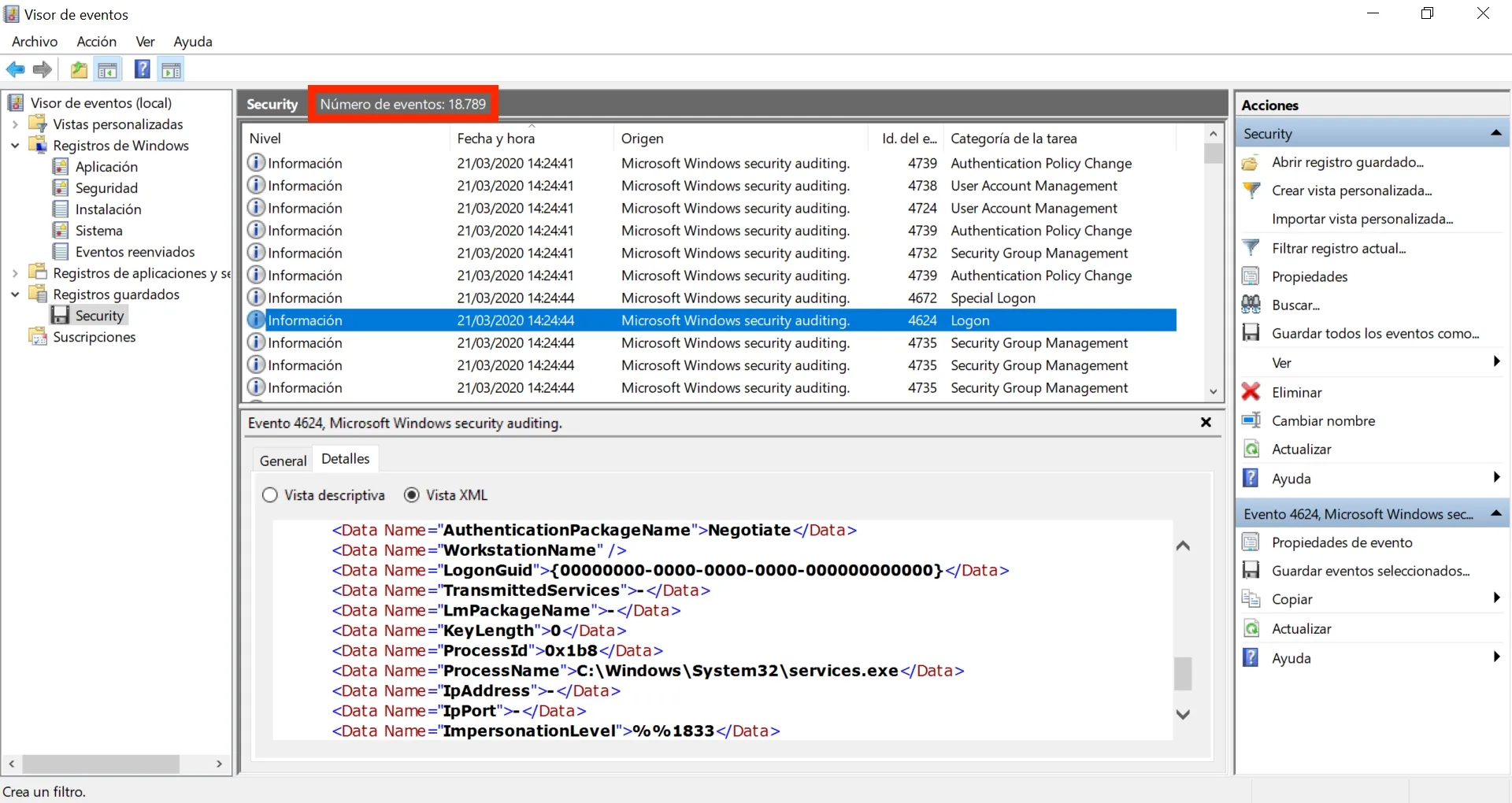
Tenemos un montón de eventos (18789). Vamos a aplicar un filtro para mostrar solamente los inicios de sesión exitosos (ID 4624):
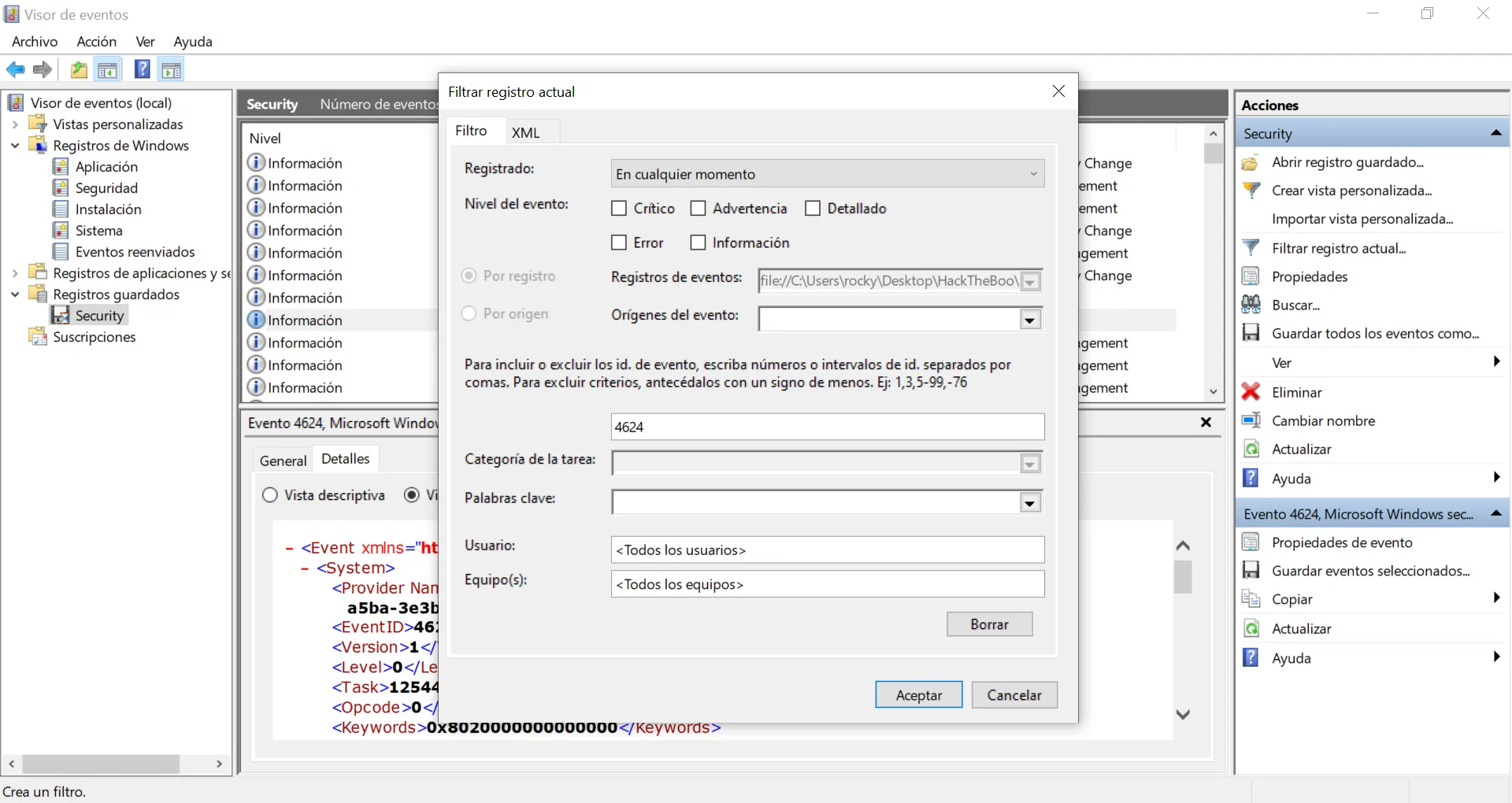
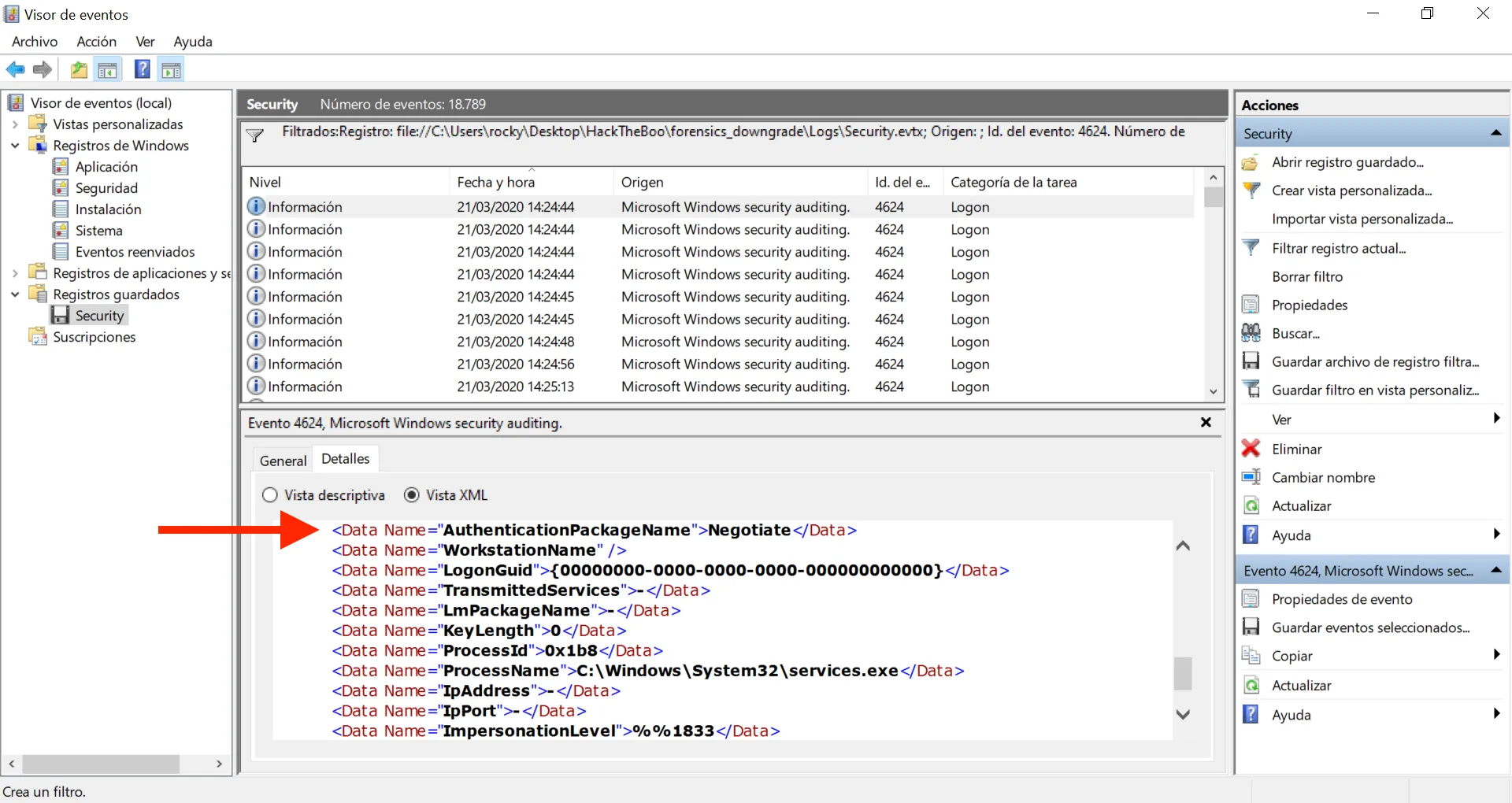
Aún tenemos un montón de eventos. Vamos a usar XML para filtrar por AuthenticationPackageName (que es el atributo que menciona la pregunta). Hay muchos eventos que tienen Negotiate como valor, por lo que vamos a suprimir estos eventos:
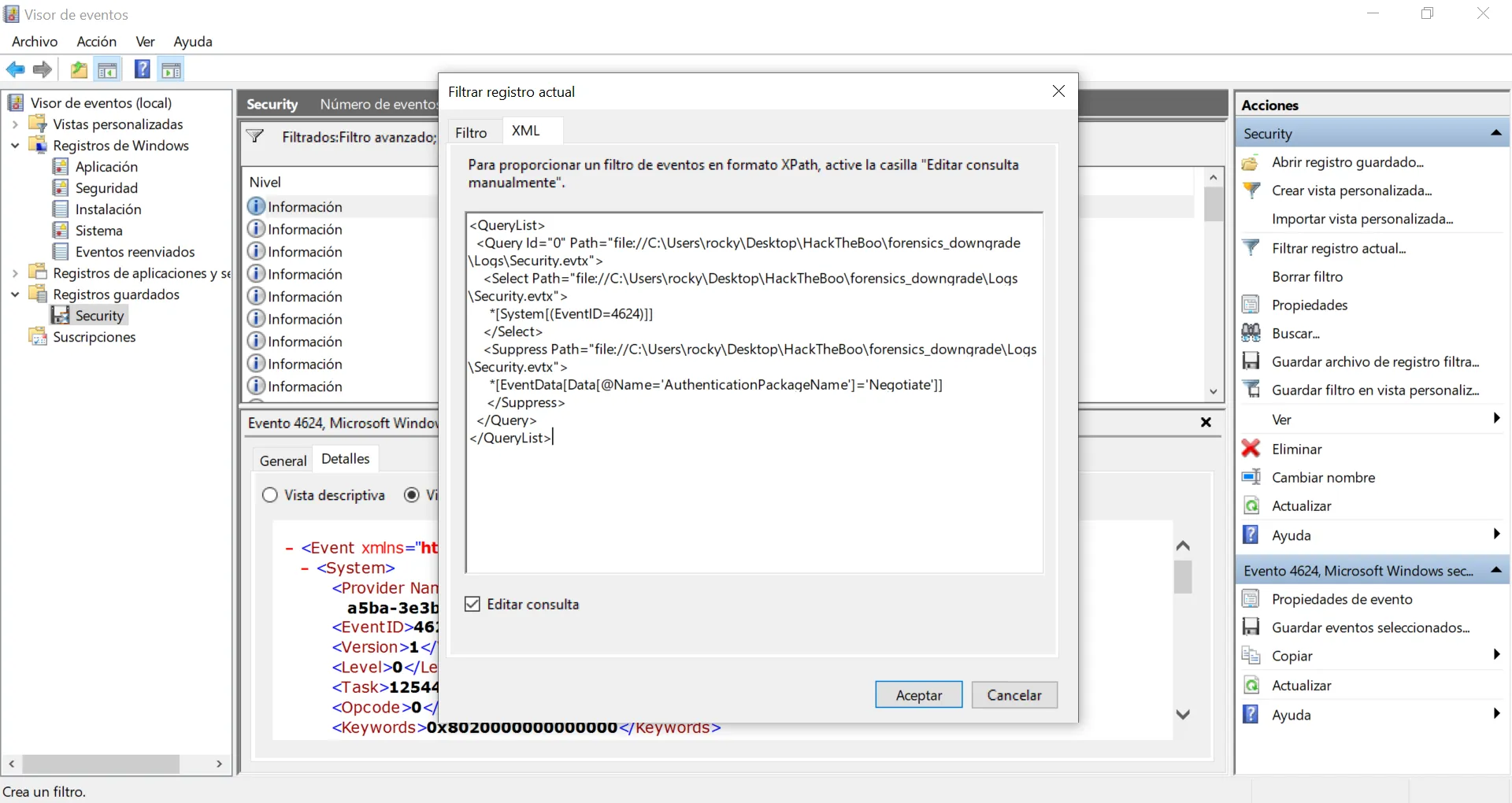
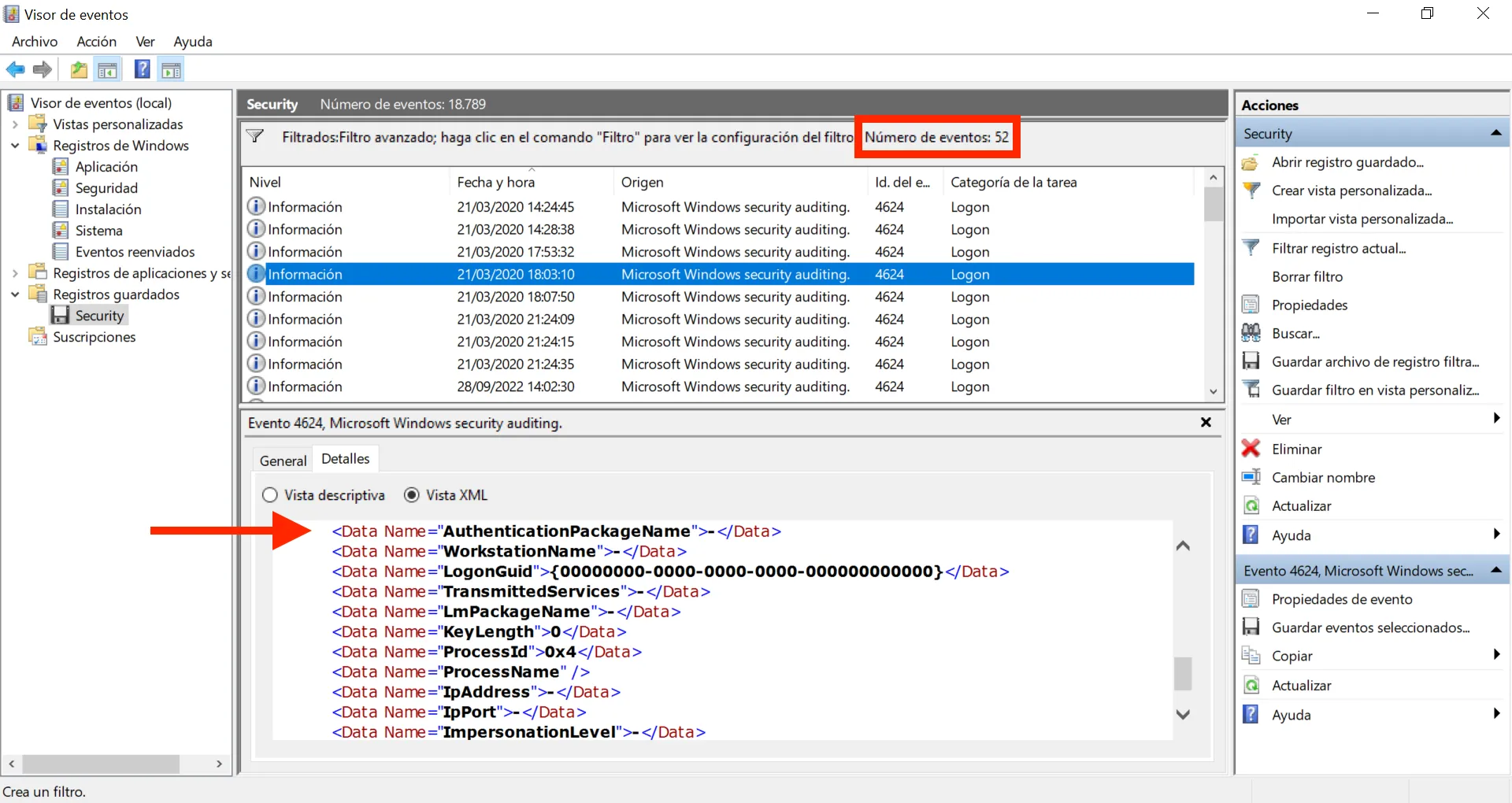
Ahora tenemos solo 52 eventos, pero algunos tienen un valor vacío para AuthenticationPackageName (-), vamos a filtrar un poco más:
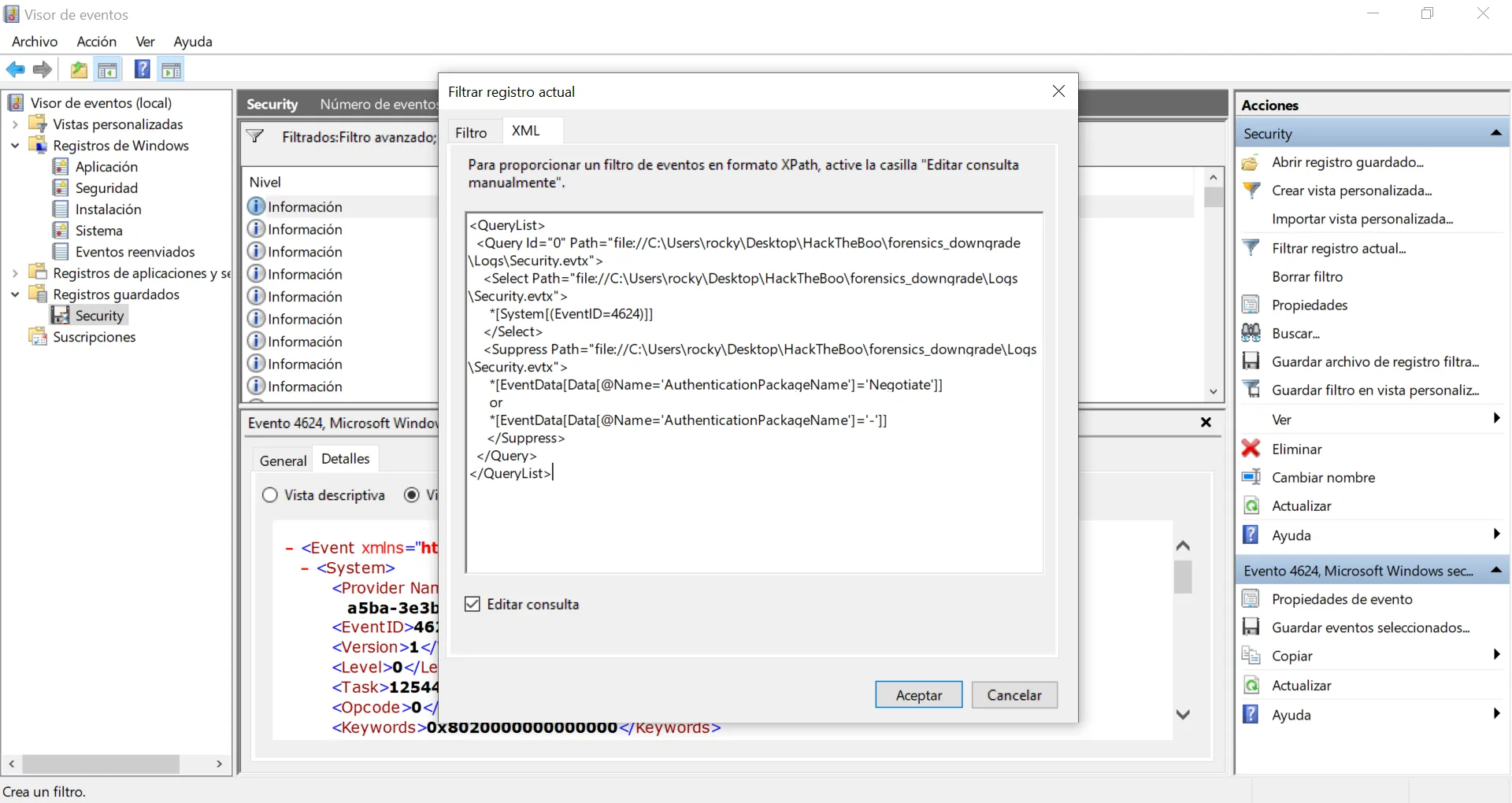
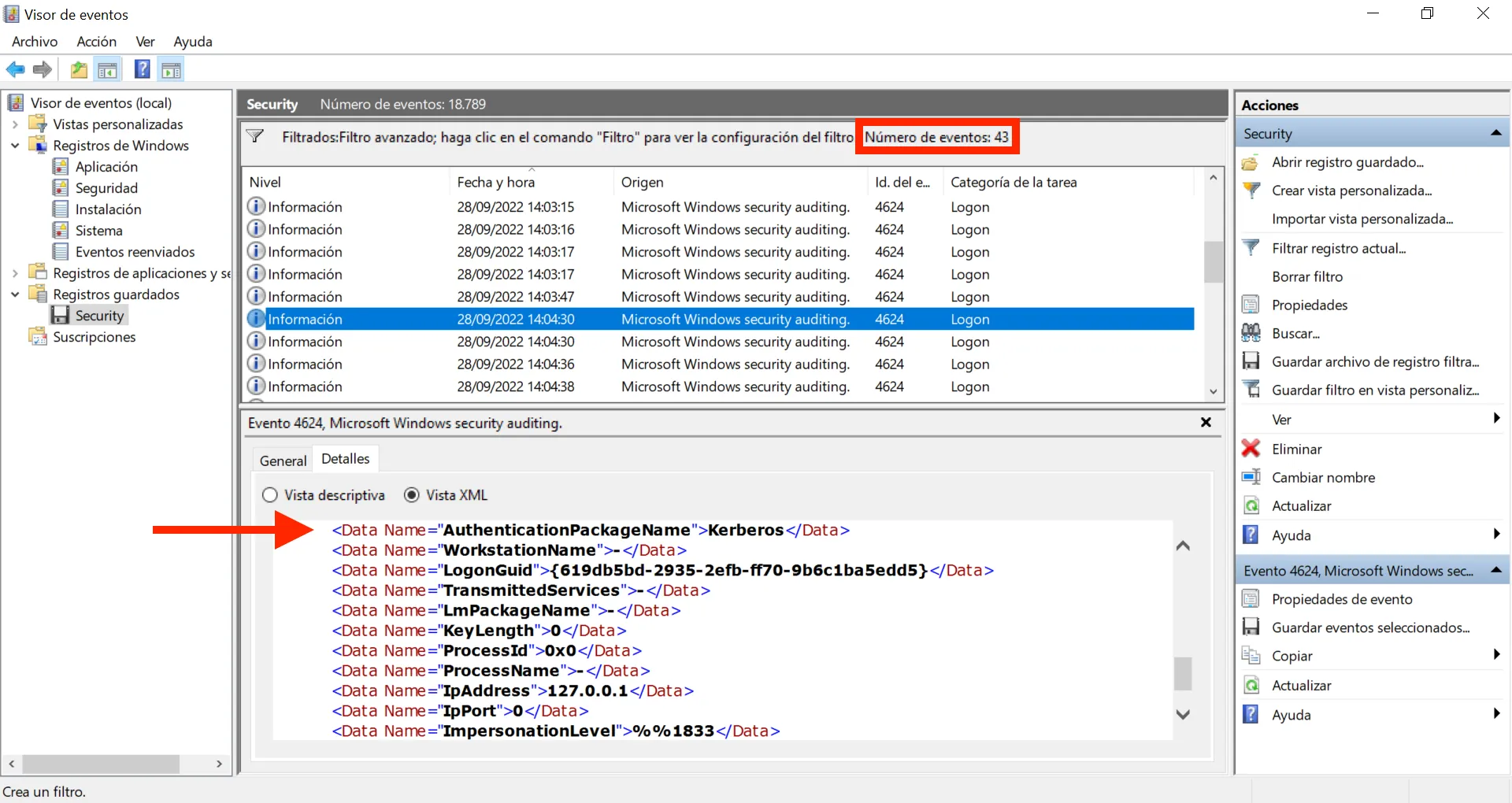
Vale, 43 eventos. Todavía hay algunos AuthenticationPackageName normales en los que el valor es Kerberos. Vamos a ponerlo en el filtro:
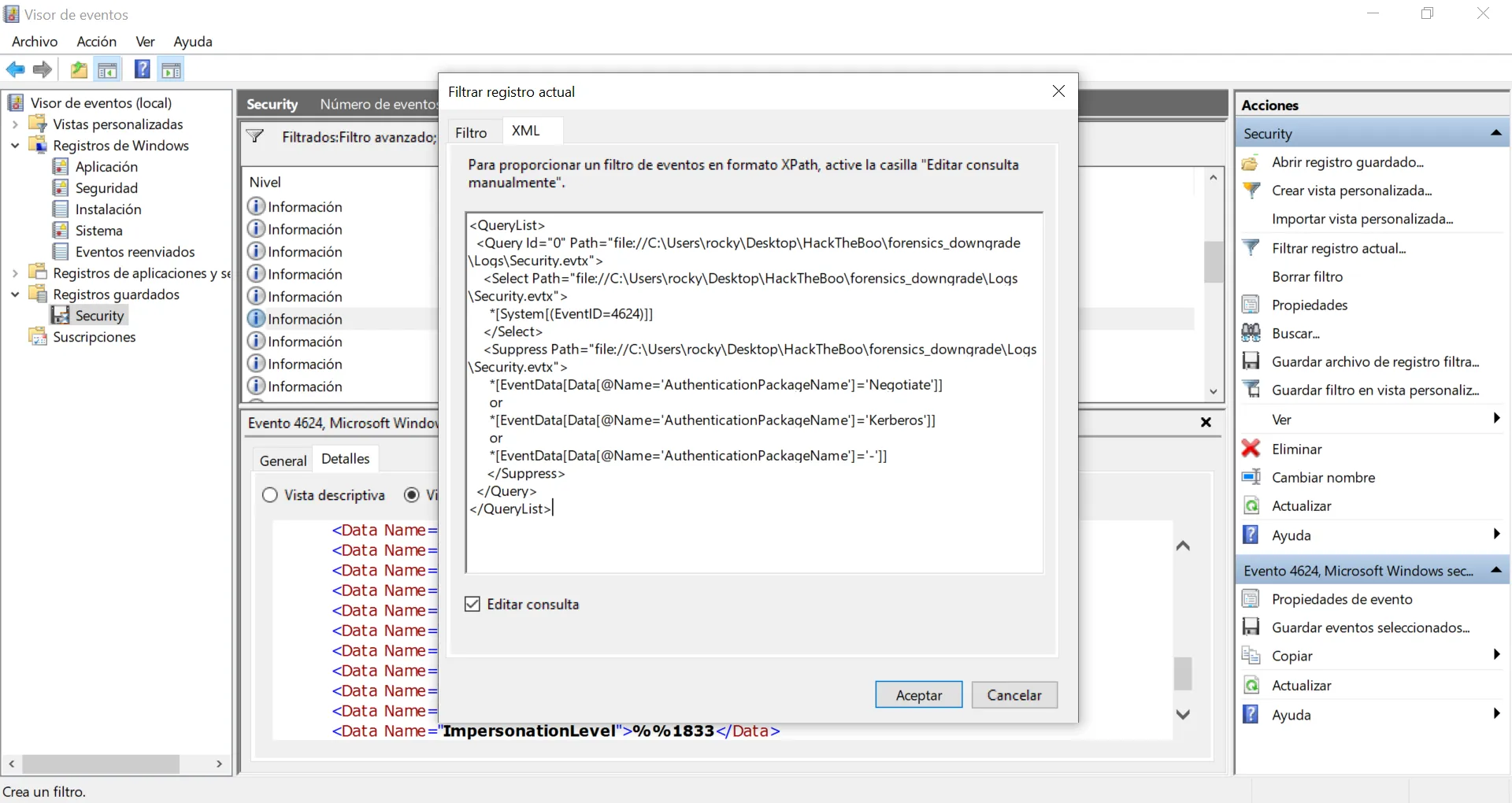
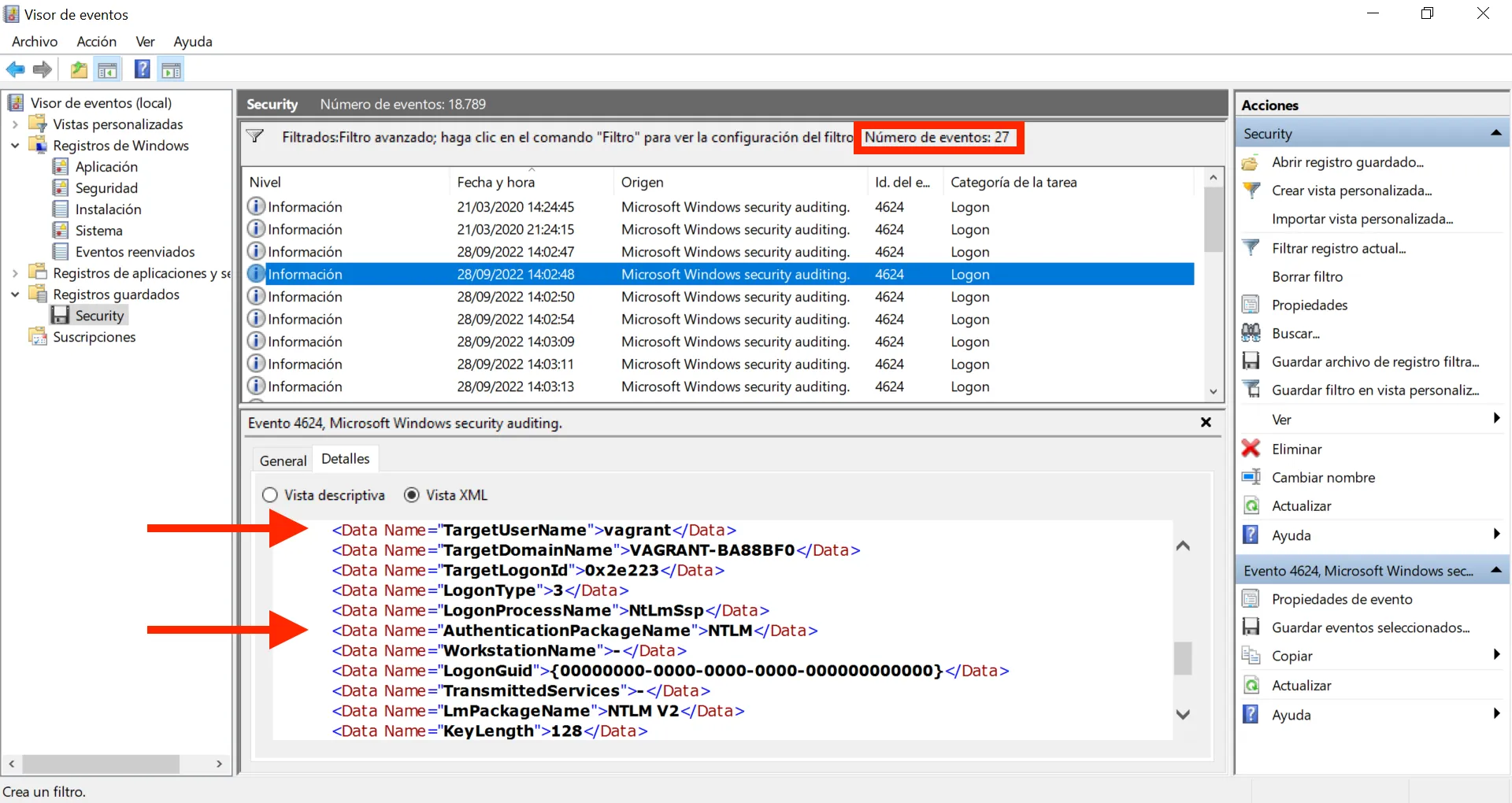
Genial, ahora solo tenemos NTLM como AuthenticationPackageName, y esta es la respuesta a la pregunta:
Looking at all the logon events, what is the AuthPackage that stands out as different from all the rest? (for example: http)
> ntlm
[+] Correct!
What is the timestamp of the suspicious login (yyyy-MM-ddTHH:mm:ss) UTC? (for example, 2021-10-10T08:23:12)
>
Finalmente, podemos suprimir aquellos eventos en los que el usuario que se autentica es vagrant (como en la imagen anterior):
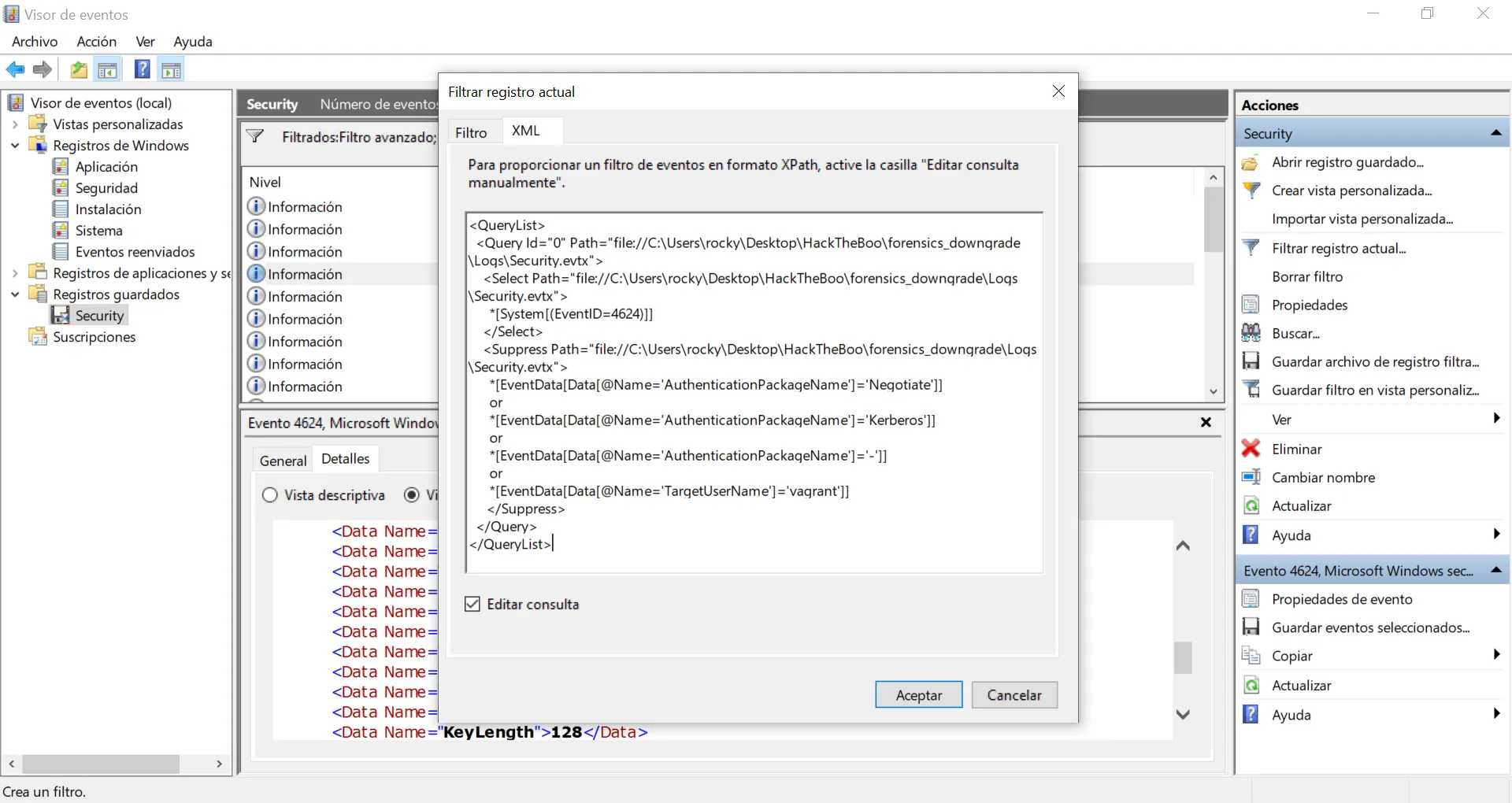
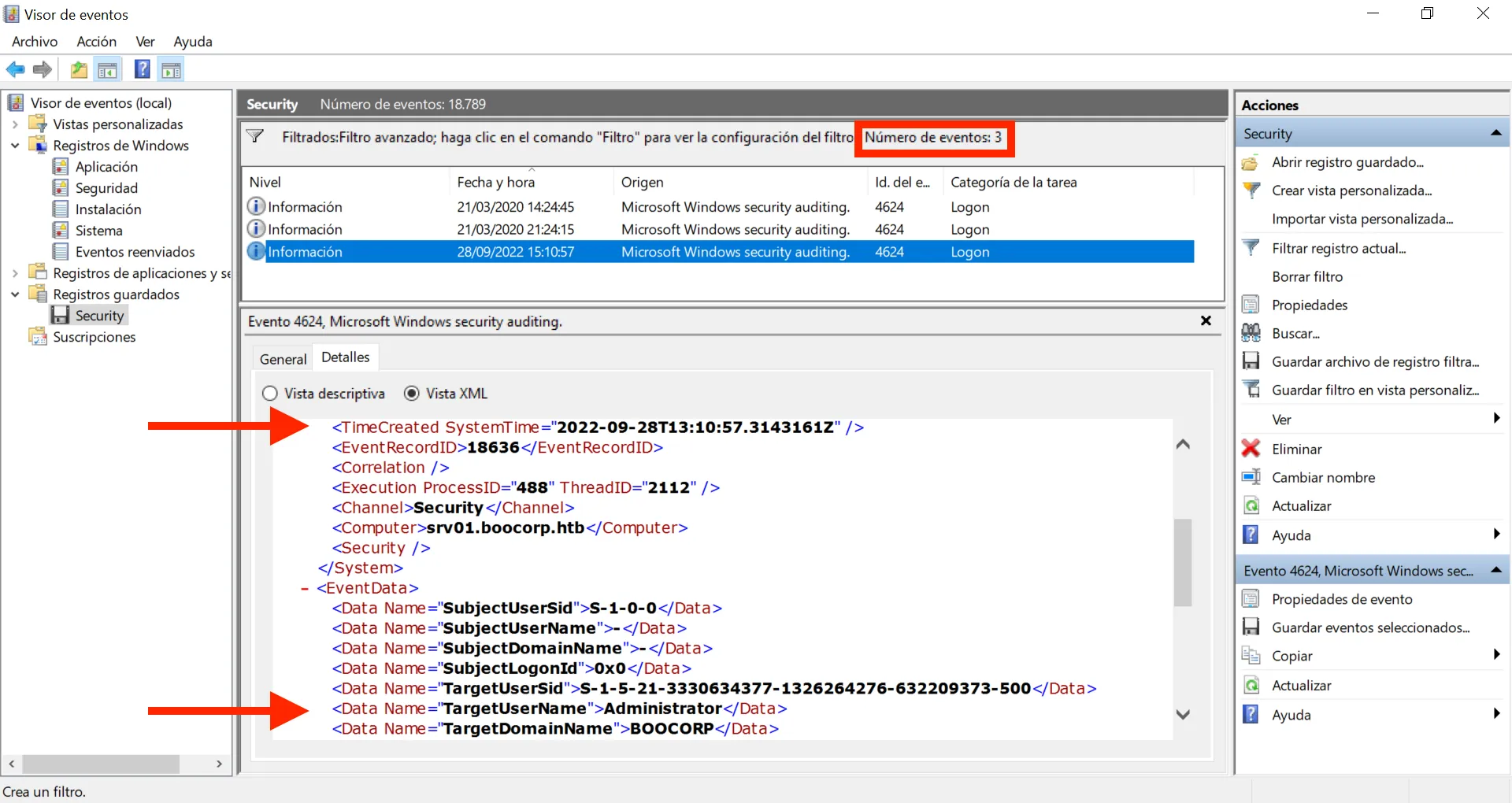
Y ahora solo tenemos 3 eventos. Dos de ellos son ANONYMOUS LOGON, y el último se está autenticando como Administrator, que es sospechoso.
Flag
Podemos coger la marca de tiempo (timestamp) del evento sospechoso y responder a la pregunta para conseguir la flag:
What is the timestamp of the suspicious login (yyyy-MM-ddTHH:mm:ss) UTC? (for example, 2021-10-10T08:23:12)
> 2022-09-28T13:10:57
[+] Correct!
[+] Here is the flag: HTB{4n0th3r_d4y_4n0th3r_d0wngr4d3...}