Trick or Breach
4 minutos de lectura
Se nos proporciona un archivo con una captura de tráfico de red llamado capture.pcap:
Análisis de tráfico
Podemos usar Wireshark para analizarlo:
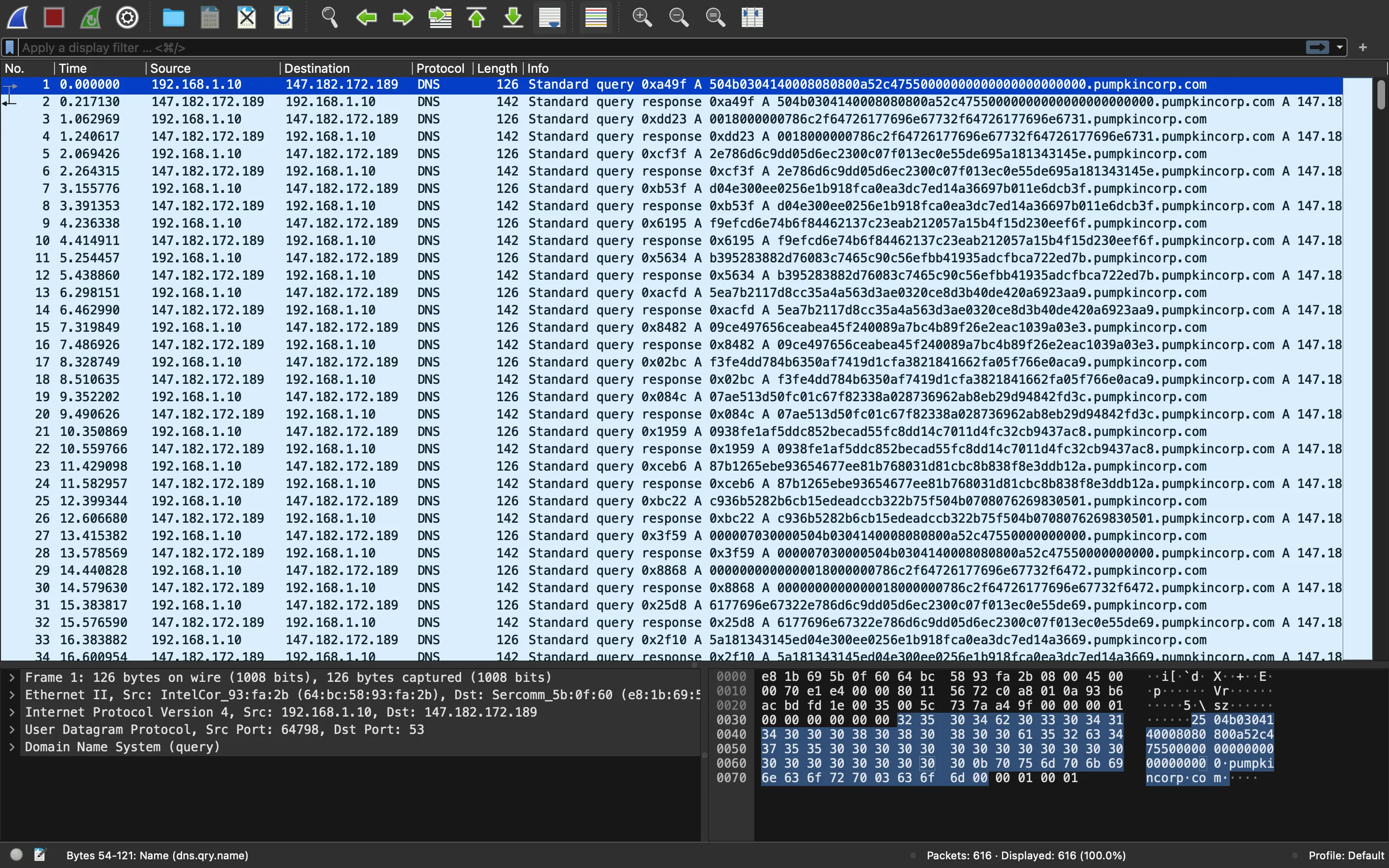
Consultas DNS
Todos los paquetes corresponden a consultas DNS (y respuestas). Lo que destaca es el subdominio: todas las consultas preguntan por hex-data.pumpkincorp.com.
Si filtramos por los datos hexadecimales en el archivo capture.pcap, tenemos lo siguiente:
$ strings capture.pcap | grep -E '[0-9a-f]{32,}' | head
2504b0304140008080800a52c47550000000000000000000000
2504b0304140008080800a52c47550000000000000000000000
20018000000786c2f64726177696e67732f64726177696e6731
20018000000786c2f64726177696e67732f64726177696e6731
22e786d6c9dd05d6ec2300c07f013ec0e55de695a181343145e
22e786d6c9dd05d6ec2300c07f013ec0e55de695a181343145e
2d04e300ee0256e1b918fca0ea3dc7ed14a36697b011e6dcb3f
2d04e300ee0256e1b918fca0ea3dc7ed14a36697b011e6dcb3f
2f9efcd6e74b6f84462137c23eab212057a15b4f15d230eef6f
2f9efcd6e74b6f84462137c23eab212057a15b4f15d230eef6f
Nótese que todas las líneas empiezan por 2, que no es parte del subdominio (se comprueba en la imagen anterior), por lo que tenemos que quitarlo:
$ strings capture.pcap | grep -E '[0-9a-f]{32,}' | sed s/^2//g | head
504b0304140008080800a52c47550000000000000000000000
504b0304140008080800a52c47550000000000000000000000
0018000000786c2f64726177696e67732f64726177696e6731
0018000000786c2f64726177696e67732f64726177696e6731
2e786d6c9dd05d6ec2300c07f013ec0e55de695a181343145e
2e786d6c9dd05d6ec2300c07f013ec0e55de695a181343145e
d04e300ee0256e1b918fca0ea3dc7ed14a36697b011e6dcb3f
d04e300ee0256e1b918fca0ea3dc7ed14a36697b011e6dcb3f
f9efcd6e74b6f84462137c23eab212057a15b4f15d230eef6f
f9efcd6e74b6f84462137c23eab212057a15b4f15d230eef6f
Otra cosa a tener en cuenta es que tenemos líneas repetidas. Podemos usar uniq para eliminar estos datos repetidos:
$ strings capture.pcap | grep -E '[0-9a-f]{32,}' | sed s/^2//g | uniq | head
504b0304140008080800a52c47550000000000000000000000
0018000000786c2f64726177696e67732f64726177696e6731
2e786d6c9dd05d6ec2300c07f013ec0e55de695a181343145e
d04e300ee0256e1b918fca0ea3dc7ed14a36697b011e6dcb3f
f9efcd6e74b6f84462137c23eab212057a15b4f15d230eef6f
b395283882d76083c7465c90c56efbb41935adcfbca722ed7b
5ea7b2117d8cc35a4a563d3ae0320ce8d3b40de420a6923aa9
09ce497656ceabea45f240089a7bc4b89f26e2eac1039a03e3
f3fe4dd784b6350af7419d1cfa3821841662fa05f766e0aca9
07ae513d50fc01c67f82338a028736962ab8eb29d94842fd3c
Si convertimos los datos hexadecimales en bytes con xxd y pasamod la salida al comando file, veremos que se trata de un documento de Microsoft Excel:
$ strings capture.pcap | grep -E '[0-9a-f]{32,}' | sed s/^2//g | uniq | xxd -r -p | file -
/dev/stdin: Microsoft Excel 2007+
$ strings capture2.pcap | grep -E '[0-9a-f]{32,}' | sed s/^2//g | uniq | xxd -r -p > file.xlsx
Extracción de datos de Microsoft Office
El archivo está dañado, pero aun así podemos inspeccionarlo. Por si no lo sabías, cualquier documento de Microsoft Office es un archivo comprimidi ZIP (mira los bytes mágicos):
$ xxd file.xlsx | head
00000000: 504b 0304 1400 0808 0800 a52c 4755 0000 PK.........,GU..
00000010: 0000 0000 0000 0000 0000 1800 0000 786c ..............xl
00000020: 2f64 7261 7769 6e67 732f 6472 6177 696e /drawings/drawin
00000030: 6731 2e78 6d6c 9dd0 5d6e c230 0c07 f013 g1.xml..]n.0....
00000040: ec0e 55de 695a 1813 4314 5ed0 4e30 0ee0 ..U.iZ..C.^.N0..
00000050: 256e 1b91 8fca 0ea3 dc7e d14a 3669 7b01 %n.......~.J6i{.
00000060: 1e6d cb3f f9ef cd6e 74b6 f844 6213 7c23 .m.?...nt..Db.|#
00000070: eab2 1205 7a15 b4f1 5d23 0eef 6fb3 9528 ....z...]#..o..(
00000080: 3882 d760 83c7 465c 90c5 6efb b419 35ad 8..`..F\..n...5.
00000090: cfbc a722 ed7b 5ea7 b211 7d8c c35a 4a56 ...".{^...}..ZJV
Con unzip todavía aparece como corrupto, pero podemos usar 7z:
$ cp file.xlsx file.zip
$ unzip -l file.zip
Archive: file.zip
End-of-central-directory signature not found. Either this file is not
a zipfile, or it constitutes one disk of a multi-part archive. In the
latter case the central directory and zipfile comment will be found on
the last disk(s) of this archive.
unzip: cannot find zipfile directory in one of file.zip or
file.zip.zip, and cannot find file.zip.ZIP, period.
$ 7z l file.zip
7-Zip [64] 17.04 : Copyright (c) 1999-2021 Igor Pavlov : 2017-08-28
p7zip Version 17.04 (locale=utf8,Utf16=on,HugeFiles=on,64 bits,8 CPUs LE)
Scanning the drive for archives:
1 file, 7675 bytes (8 KiB)
Listing archive: file.zip
--
Path = file.zip
Type = zip
ERRORS:
Unexpected end of archive
Physical Size = 7675
Characteristics = Local
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2022-10-07 05:37:10 ..... 775 261 xl/drawings/drawing1.xml
2022-10-07 05:37:10 ..... 775 261 xl/drawings/drawing2.xml
2022-10-07 05:37:10 ..... 6170 1645 xl/worksheets/sheet1.xml
2022-10-07 05:37:10 ..... 298 179 xl/worksheets/_rels/sheet1.xml.rels
2022-10-07 05:37:10 ..... 3106 939 xl/worksheets/sheet2.xml
2022-10-07 05:37:10 ..... 298 180 xl/worksheets/_rels/sheet2.xml.rels
2022-10-07 05:37:10 ..... 853 405 xl/sharedStrings.xml
2022-10-07 05:37:10 ..... 10676 1081 xl/styles.xml
2022-10-07 05:37:10 ..... 874 347 xl/workbook.xml
2022-10-07 05:37:10 ..... 706 226 xl/_rels/workbook.xml.rels
2022-10-07 05:37:10 ..... 296 178 _rels/.rels
2022-10-07 05:37:10 ..... 1192 308 [Content_Types].xml
------------------- ----- ------------ ------------ ------------------------
2022-10-07 05:37:10 26019 6010 12 files
Errors: 1
Entonces, vamos a descomprimirlo:
$ mkdir file
$ cd file
$ mv ../file.zip .
$ 7z x file.zip
7-Zip [64] 17.04 : Copyright (c) 1999-2021 Igor Pavlov : 2017-08-28
p7zip Version 17.04 (locale=utf8,Utf16=on,HugeFiles=on,64 bits,8 CPUs LE)
Scanning the drive for archives:
1 file, 7675 bytes (8 KiB)
Extracting archive: file.zip
ERRORS:
Unexpected end of archive
--
Path = file.zip
Type = zip
ERRORS:
Unexpected end of archive
Physical Size = 7675
Characteristics = Local
Archives with Errors: 1
Open Errors: 1
Flag
Ahora podemos buscar la flag usando grep, y ahí está:
$ grep -r HTB .
<sst xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" count="28" uniqueCount="22"><si><t>Recipe Assignment</t></si><si><t>In this sheet there are assigned the ingredients of the punken pun secret project.</t></si><si><t>Subject</t></si><si><t>Assignment</t></si><si><t>Status</t></si><si><t>Time</t></si><si><t>Start date</t></si><si><t>Due on</t></si><si><t>Andrew</t></si><si><t>1 Fillet of a fenny snake</t></si><si><t>In progress</t></si><si><t>Nick</t></si><si><t>3 Lizard’s legs</t></si><si><t>Not started</t></si><si><t>3 Bat wings</t></si><si><t>Mike</t></si><si><t>3 Halloween chips</t></si><si><t>Done</t></si><si><t>HTB{M4g1c_c4nn0t_pr3v3nt_d4t4_br34ch}</t></si><si><t>Skipped</t></si><si><t>Team Members</t></si><si><t>Member of the Punkenpun project.</t></si></sst>
$ grep -r HTB . | grep -oE 'HTB{.*?}'
HTB{M4g1c_c4nn0t_pr3v3nt_d4t4_br34ch}