Micro-CMS v1
2 minutes to read
We have a simple website that allows us to edit and create posts using Markdown:
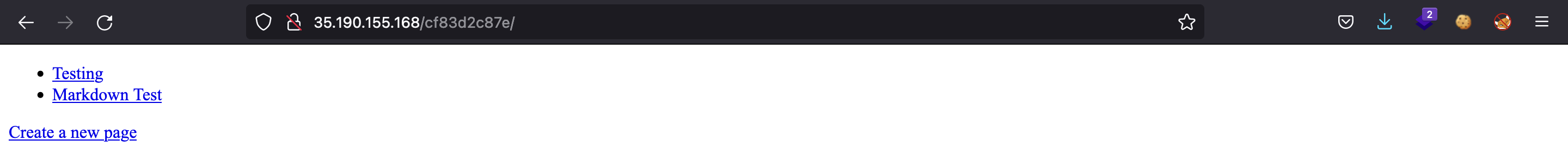
Let’s click on “Testing”:
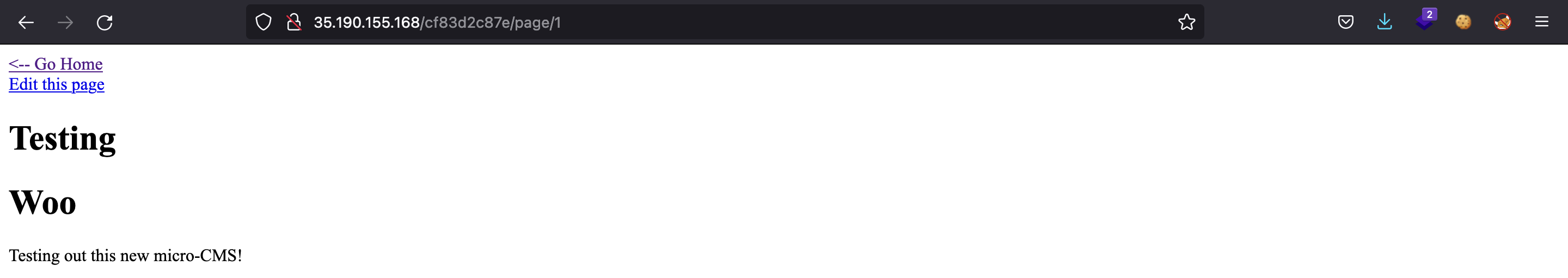
Now, we can try to edit the current post. A text area is shown in order to write Markdown code:
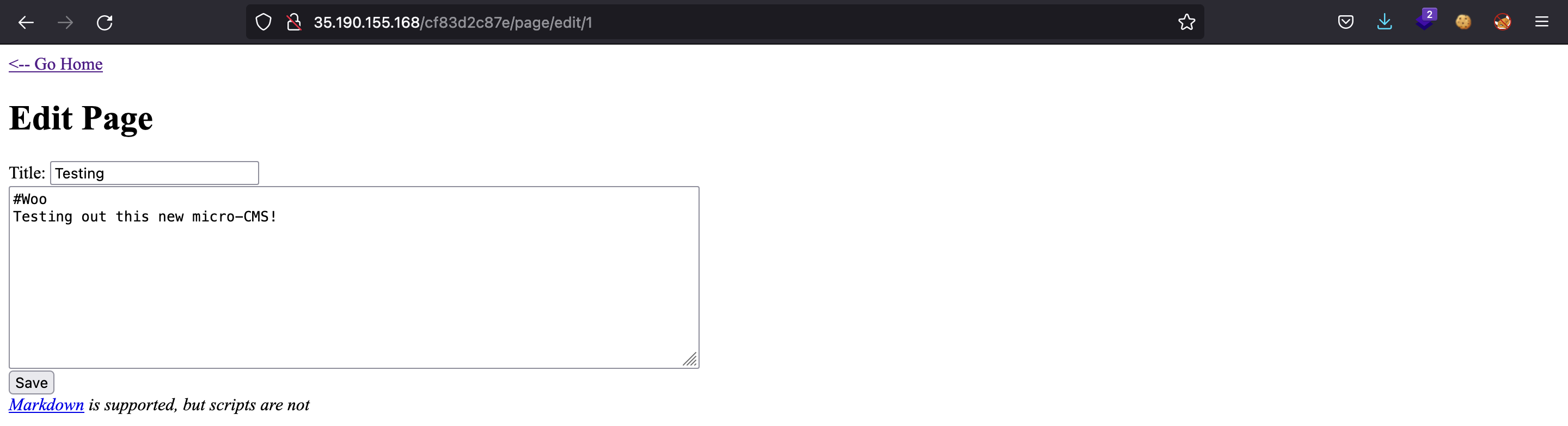
Markdown is a markup language similar to HTML but simpler and easier. Furthermore, Markdown supports the use of HTML tags as well. Hence, let’s try a Cross-Site Scripting (XSS) payload like:
<script>alert(123)</script>
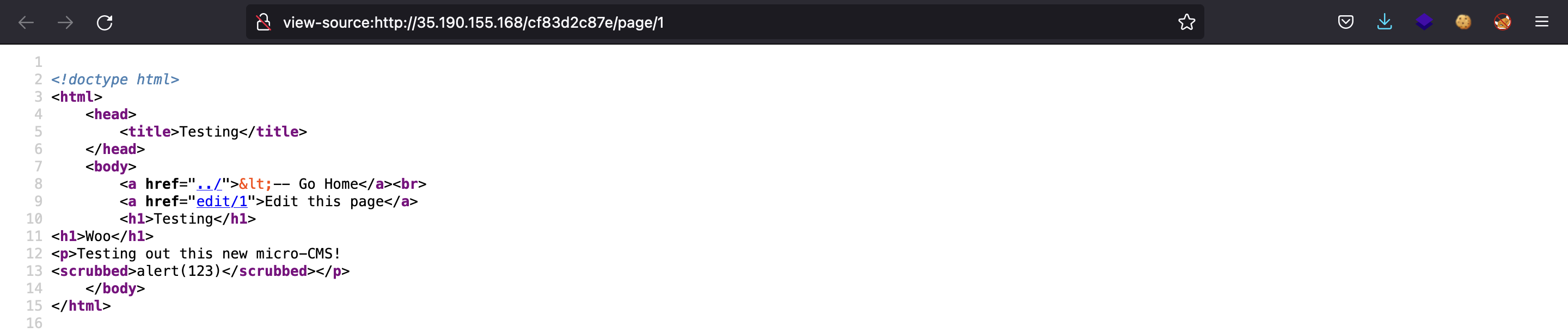
It seems not to work. In fact, if we show the source code of the updated page, our payload has been replaced:
So the payload has been blocked. Let’s try with this one:
<img src="x" onerror="alert(123)">
Now it seems to work, and the alert is shown:
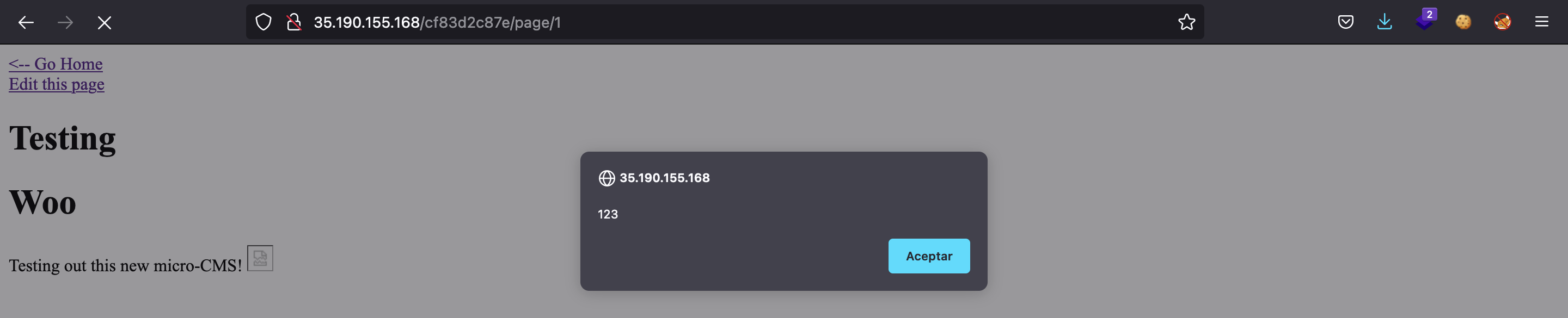
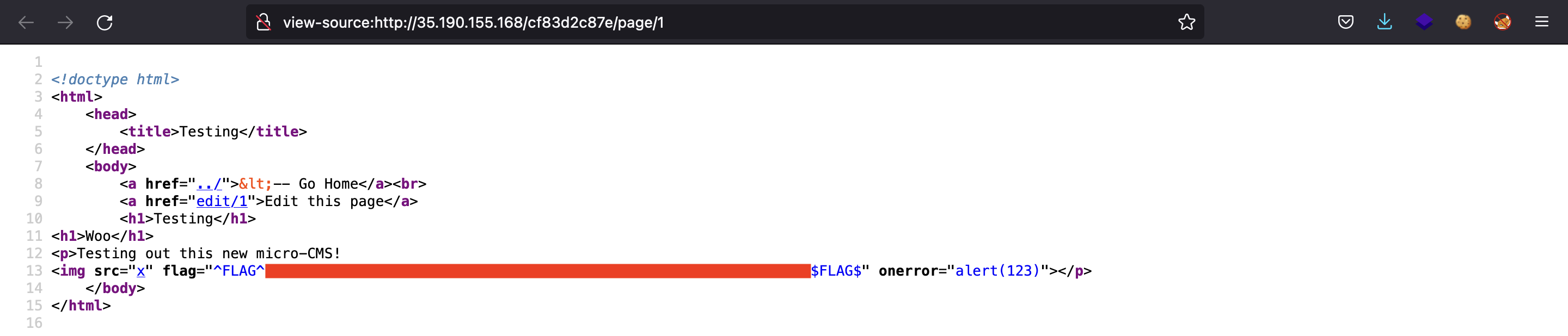
If we inspect the source code again, we obtain a flag:
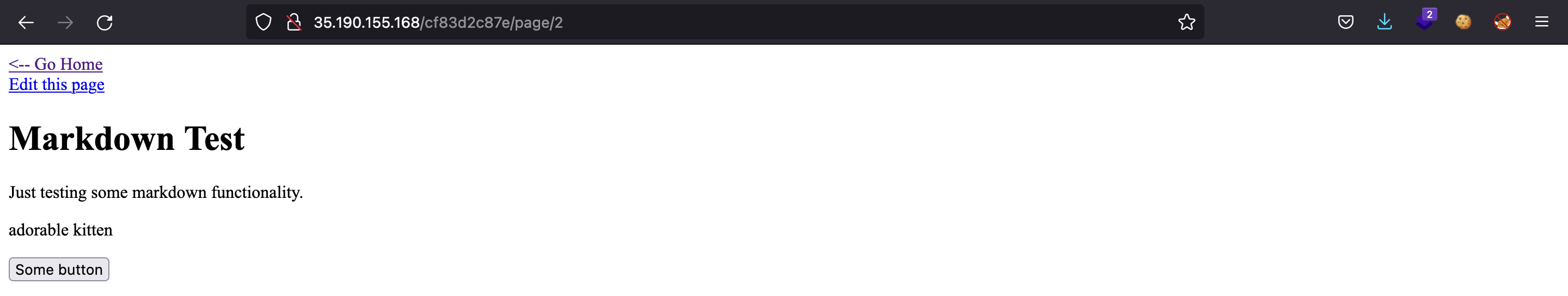
Looking at the URL, we can notice that there is a number at the end (/page/1). Let’s try putting other numbers: for /page/2 we have the “Markdown test”, for /page/3 we get a 404 Not Found error. However, for /page/4 we get 403 Forbidden:
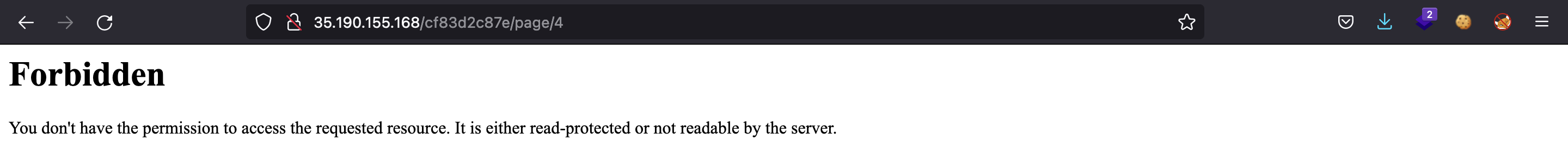
Trying more page numbers will only give 404 Not Found errors.
Let’s mess around with “Markdown test”:
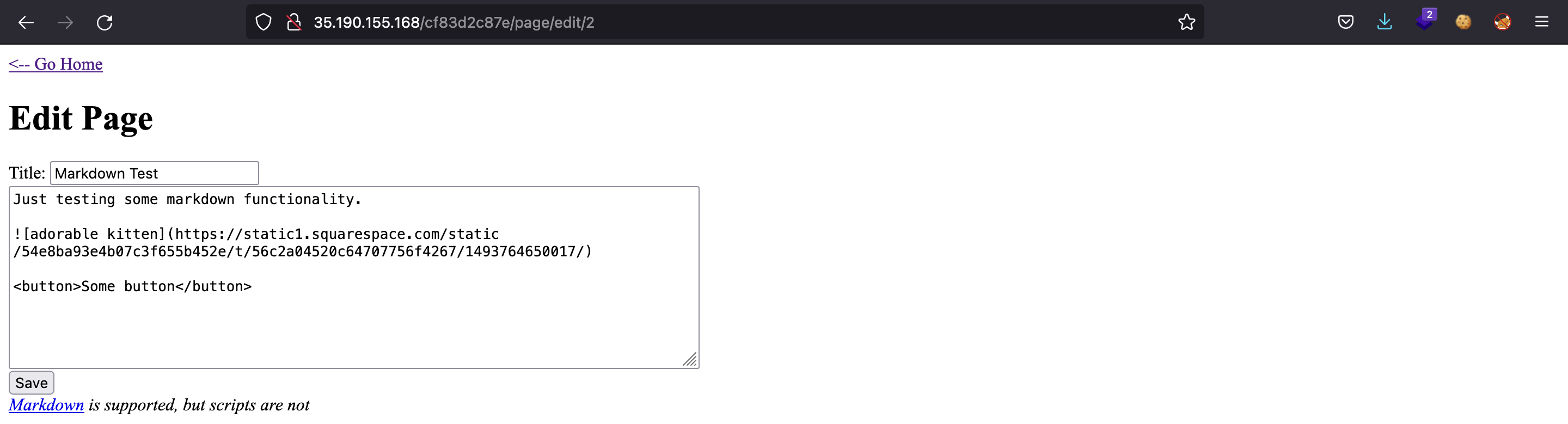
There is nothing more to do on this post. However, we can see that the URL has changed: now it is /page/edit/2. Let’s try to view /page/edit/4, the one that gave 403 Forbidden error:
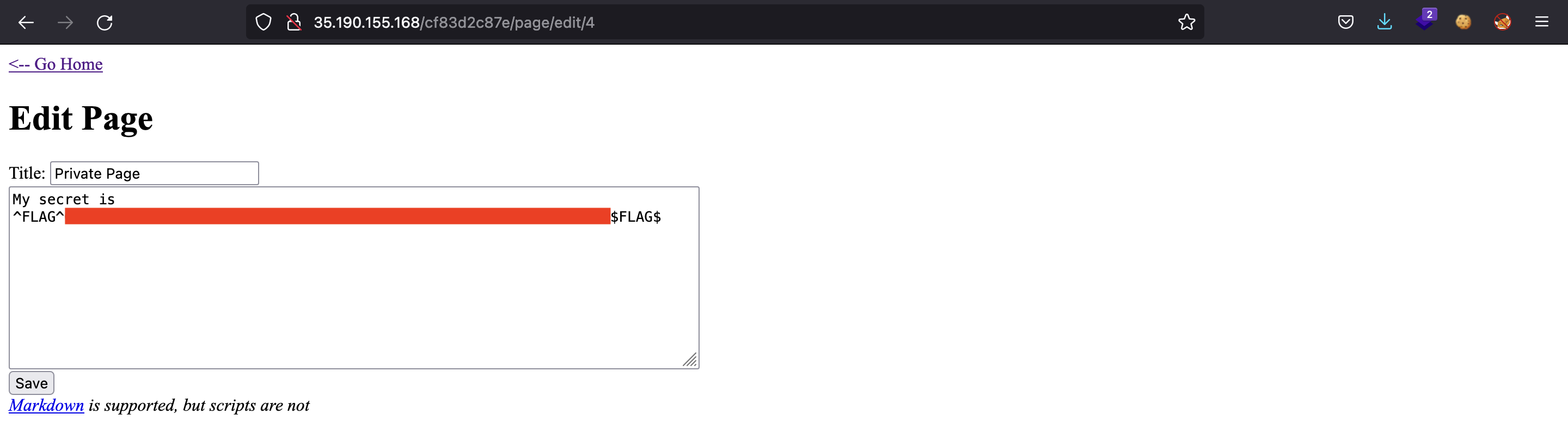
And we have the second flag, exploiting an Insecure Direct Object Reference (IDOR) vulnerability.
Let’s continue creating a new post:
I decided to put New1 as title and Test1 as content. After that I created another post using New2 and Test2. Now, the main page looks like this:
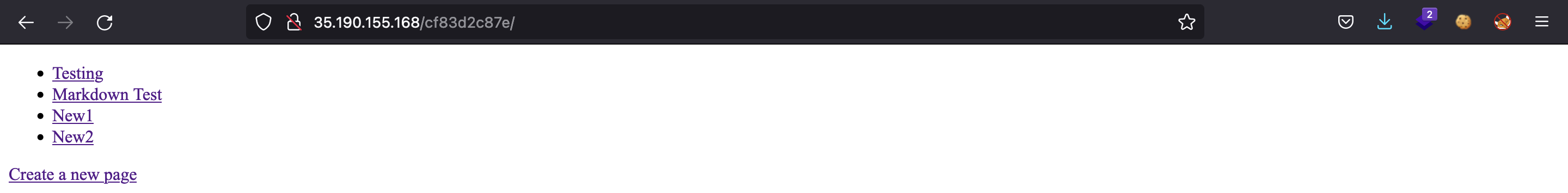
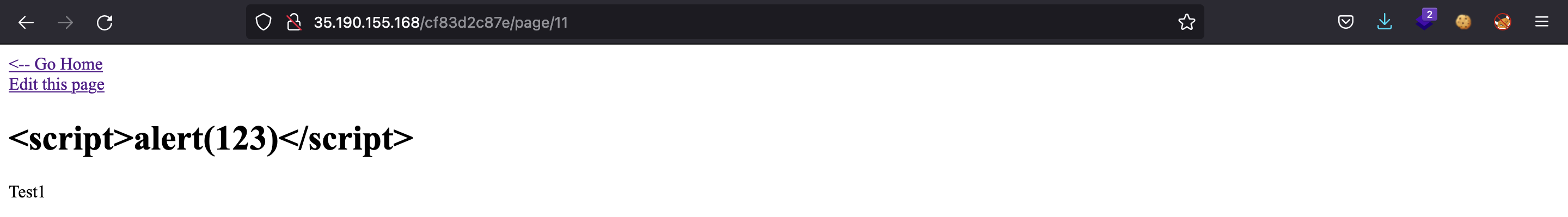
Let’s try the <img> XSS payload on the title of one of the posts. We do not see the HTML interpreted here:
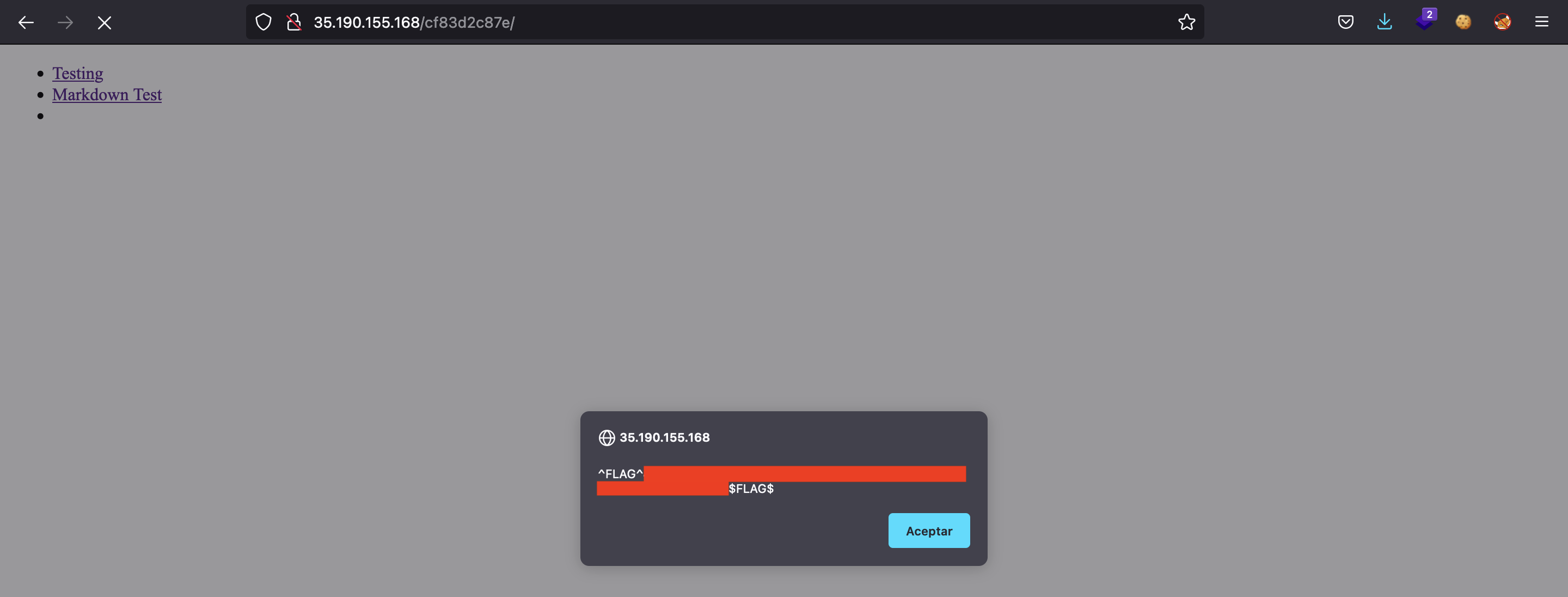
But if we go to the main page we get another flag:
And finally, we can guess that the web application is using a database to store the posts. Therefore, to show them, the server is performing a query on the database to obtain the actual posts. Hence, we can try som SQL injection payload.
For instance, we can add a single quote to break the SQL syntax:
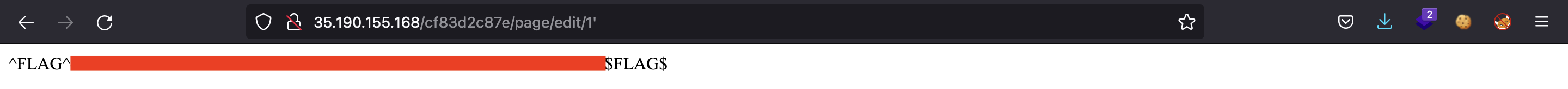
And we have the fourth and last flag.