Chase
1 minute to read
We are given a PCAP file with some HTTP messages and TCP segments:
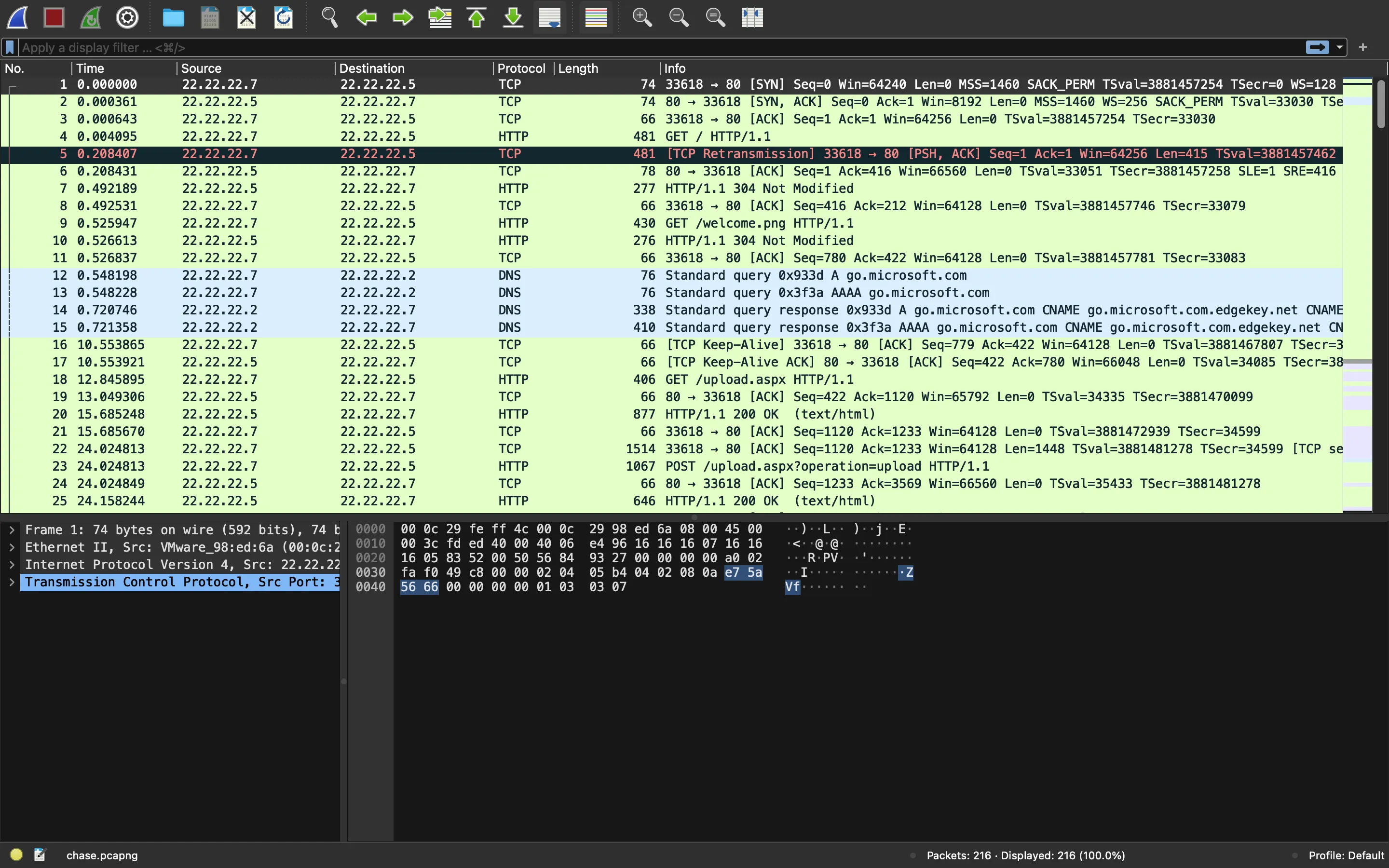
HTTP traffic
If we filter by HTTP, we will see some requests and responses:
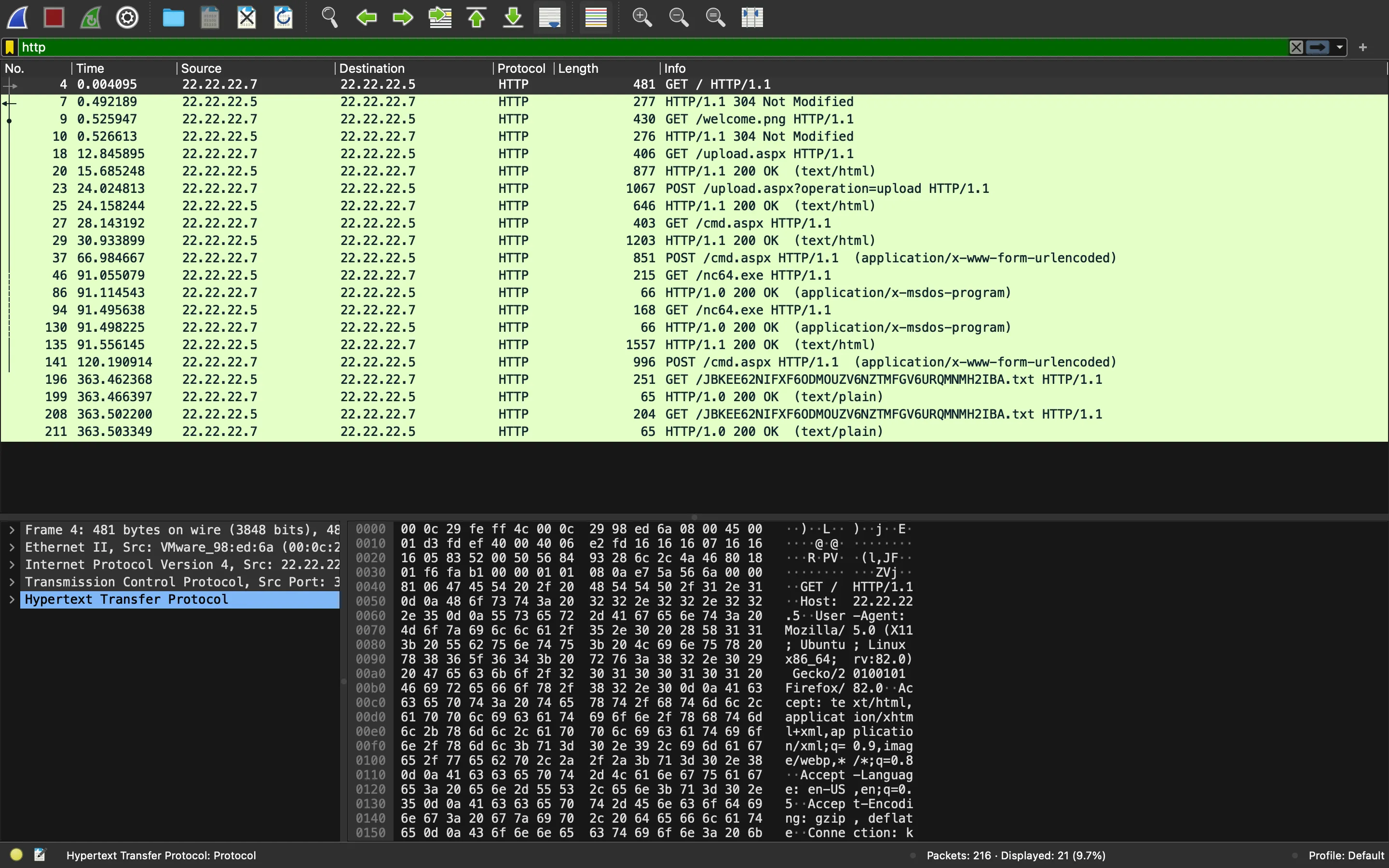
We might think that the cyber criminal found a remote file upload vulnerability and uploaded cmd.aspx and then uploaded nc64.exe to execute commands. Actually, we can see that the cyber criminal got a reverse shell on the Windows host:
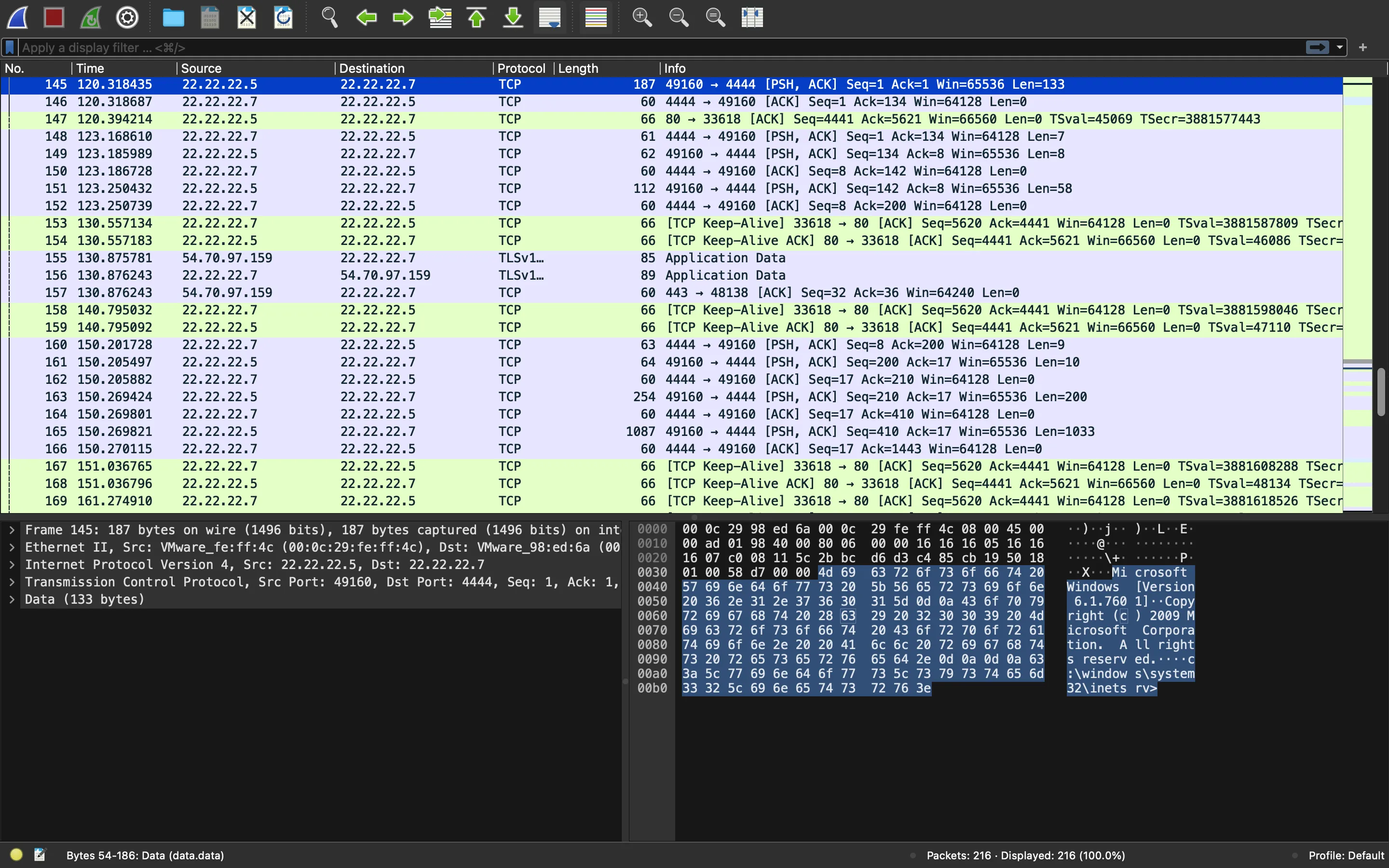
At the end of the PCAP capture, we see that the cyber criminal tries to access a file named JBKEE62NIFXF6ODMOUZV6NZTMFGV6URQMNMH2IBA.txt and it shows Hey there!:
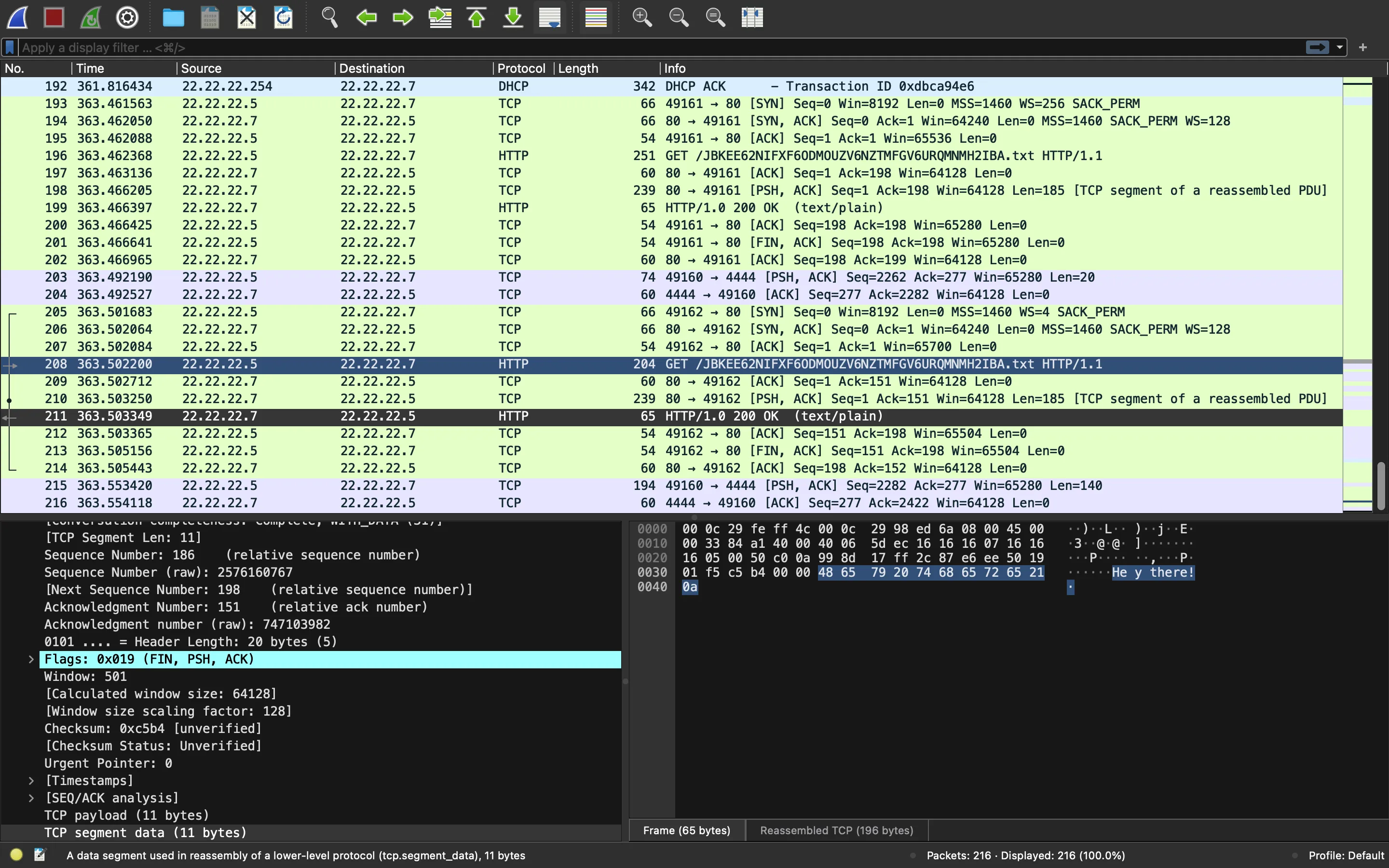
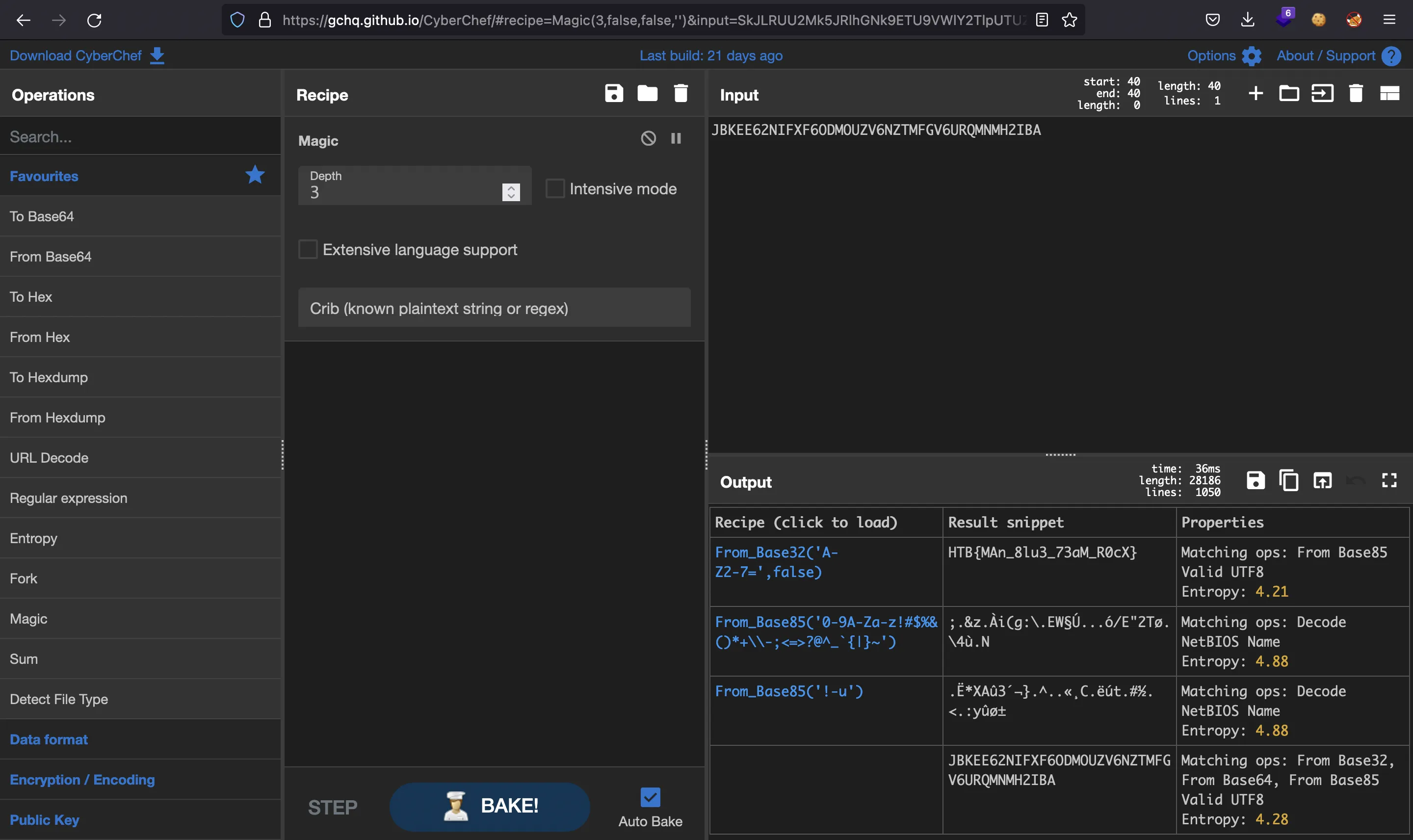
Flag
The key here is that the filename is encoded. If we enter it in CyberChef with Magic recipe, we will see that it is encoded in Base32, and it is the flag (HTB{MAn_8lu3_73aM_R0cX} ):