Downgrade
4 minutes to read
We are given a lot of Windows Event logs (.evtx files):
$ tree Logs
Logs
├── Application.evtx
├── HardwareEvents.evtx
├── Internet Explorer.evtx
├── Key Management Service.evtx
├── Microsoft-Windows-AppModel-Runtime%4Admin.evtx
├── Microsoft-Windows-AppReadiness%4Admin.evtx
├── Microsoft-Windows-AppReadiness%4Operational.evtx
├── Microsoft-Windows-AppXDeployment%4Operational.evtx
├── Microsoft-Windows-AppXDeploymentServer%4Operational.evtx
├── Microsoft-Windows-AppXDeploymentServer%4Restricted.evtx
├── Microsoft-Windows-ApplicationResourceManagementSystem%4Operational.evtx
├── Microsoft-Windows-Bits-Client%4Operational.evtx
├── Microsoft-Windows-CodeIntegrity%4Operational.evtx
├── Microsoft-Windows-Compat-Appraiser%4Operational.evtx
├── Microsoft-Windows-CoreApplication%4Operational.evtx
├── Microsoft-Windows-Crypto-DPAPI%4BackUpKeySvc.evtx
├── Microsoft-Windows-Crypto-DPAPI%4Operational.evtx
├── Microsoft-Windows-DSC%4Admin.evtx
├── Microsoft-Windows-DSC%4Operational.evtx
├── Microsoft-Windows-DataIntegrityScan%4Admin.evtx
├── Microsoft-Windows-DataIntegrityScan%4CrashRecovery.evtx
├── Microsoft-Windows-DeviceSetupManager%4Admin.evtx
├── Microsoft-Windows-DeviceSetupManager%4Operational.evtx
├── Microsoft-Windows-Dhcp-Client%4Admin.evtx
├── Microsoft-Windows-Dhcpv6-Client%4Admin.evtx
├── Microsoft-Windows-Diagnosis-DPS%4Operational.evtx
├── Microsoft-Windows-Forwarding%4Operational.evtx
├── Microsoft-Windows-GroupPolicy%4Operational.evtx
├── Microsoft-Windows-HomeGroup Control Panel%4Operational.evtx
├── Microsoft-Windows-International%4Operational.evtx
├── Microsoft-Windows-Iphlpsvc%4Operational.evtx
├── Microsoft-Windows-Kernel-ApphelpCache%4Operational.evtx
├── Microsoft-Windows-Kernel-Boot%4Operational.evtx
├── Microsoft-Windows-Kernel-EventTracing%4Admin.evtx
├── Microsoft-Windows-Kernel-PnP%4Configuration.evtx
├── Microsoft-Windows-Kernel-PnPConfig%4Configuration.evtx
├── Microsoft-Windows-Kernel-Power%4Thermal-Operational.evtx
├── Microsoft-Windows-Kernel-ShimEngine%4Operational.evtx
├── Microsoft-Windows-Kernel-StoreMgr%4Operational.evtx
├── Microsoft-Windows-Kernel-WDI%4Operational.evtx
├── Microsoft-Windows-Kernel-WHEA%4Errors.evtx
├── Microsoft-Windows-Kernel-WHEA%4Operational.evtx
├── Microsoft-Windows-Known Folders API Service.evtx
├── Microsoft-Windows-LanguagePackSetup%4Operational.evtx
├── Microsoft-Windows-MUI%4Admin.evtx
├── Microsoft-Windows-MUI%4Operational.evtx
├── Microsoft-Windows-MiStreamProvider%4Operational.evtx
├── Microsoft-Windows-NCSI%4Operational.evtx
├── Microsoft-Windows-NetworkAccessProtection%4WHC.evtx
├── Microsoft-Windows-NetworkProfile%4Operational.evtx
├── Microsoft-Windows-NetworkProvider%4Operational.evtx
├── Microsoft-Windows-Ntfs%4Operational.evtx
├── Microsoft-Windows-Ntfs%4WHC.evtx
├── Microsoft-Windows-PowerShell%4Admin.evtx
├── Microsoft-Windows-PowerShell%4Operational.evtx
├── Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager%4Operational.evtx
├── Microsoft-Windows-Powershell-DesiredStateConfiguration-PullServer%4Operational.evtx
├── Microsoft-Windows-PrintService%4Admin.evtx
├── Microsoft-Windows-RemoteDesktopServices-RdpCoreTS%4Admin.evtx
├── Microsoft-Windows-RemoteDesktopServices-RdpCoreTS%4Operational.evtx
├── Microsoft-Windows-Resource-Exhaustion-Detector%4Operational.evtx
├── Microsoft-Windows-RestartManager%4Operational.evtx
├── Microsoft-Windows-SMBClient%4Operational.evtx
├── Microsoft-Windows-SMBServer%4Audit.evtx
├── Microsoft-Windows-SMBServer%4Connectivity.evtx
├── Microsoft-Windows-SMBServer%4Operational.evtx
├── Microsoft-Windows-SMBServer%4Security.evtx
├── Microsoft-Windows-Security-SPP-UX-Notifications%4ActionCenter.evtx
├── Microsoft-Windows-ServerManager-DeploymentProvider%4Operational.evtx
├── Microsoft-Windows-ServerManager-MgmtProvider%4Operational.evtx
├── Microsoft-Windows-ServerManager-MultiMachine%4Admin.evtx
├── Microsoft-Windows-ServerManager-MultiMachine%4Operational.evtx
├── Microsoft-Windows-Shell-ConnectedAccountState%4ActionCenter.evtx
├── Microsoft-Windows-Shell-Core%4ActionCenter.evtx
├── Microsoft-Windows-Shell-Core%4Operational.evtx
├── Microsoft-Windows-SmartCard-DeviceEnum%4Operational.evtx
├── Microsoft-Windows-SmbClient%4Connectivity.evtx
├── Microsoft-Windows-SmbClient%4Security.evtx
├── Microsoft-Windows-Storage-Tiering%4Admin.evtx
├── Microsoft-Windows-StorageSpaces-Driver%4Diagnostic.evtx
├── Microsoft-Windows-StorageSpaces-Driver%4Operational.evtx
├── Microsoft-Windows-StorageSpaces-ManagementAgent%4WHC.evtx
├── Microsoft-Windows-TWinUI%4Operational.evtx
├── Microsoft-Windows-TZSync%4Operational.evtx
├── Microsoft-Windows-TaskScheduler%4Maintenance.evtx
├── Microsoft-Windows-TaskScheduler%4Operational.evtx
├── Microsoft-Windows-TerminalServices-LocalSessionManager%4Admin.evtx
├── Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
├── Microsoft-Windows-TerminalServices-Printers%4Admin.evtx
├── Microsoft-Windows-TerminalServices-Printers%4Operational.evtx
├── Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx
├── Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx
├── Microsoft-Windows-UAC%4Operational.evtx
├── Microsoft-Windows-User Profile Service%4Operational.evtx
├── Microsoft-Windows-User-Loader%4Operational.evtx
├── Microsoft-Windows-UserPnp%4ActionCenter.evtx
├── Microsoft-Windows-UserPnp%4DeviceInstall.evtx
├── Microsoft-Windows-WER-Diag%4Operational.evtx
├── Microsoft-Windows-WMI-Activity%4Operational.evtx
├── Microsoft-Windows-Wcmsvc%4Operational.evtx
├── Microsoft-Windows-WinINet-Config%4ProxyConfigChanged.evtx
├── Microsoft-Windows-WinRM%4Operational.evtx
├── Microsoft-Windows-Windows Firewall With Advanced Security%4ConnectionSecurity.evtx
├── Microsoft-Windows-Windows Firewall With Advanced Security%4Firewall.evtx
├── Microsoft-Windows-WindowsUpdateClient%4Operational.evtx
├── Microsoft-Windows-Winlogon%4Operational.evtx
├── OpenSSH%4Admin.evtx
├── OpenSSH%4Operational.evtx
├── Security.evtx
├── Setup.evtx
├── System.evtx
├── Windows PowerShell.evtx
└── WitnessClientAdmin.evtx
0 directories, 113 files
We also have a remote instance to connect to and answer some questions.
Basic log information in Windows
$ nc 178.62.85.130 31120
+-----------+---------------------------------------------------------+
| Title | Description |
+-----------+---------------------------------------------------------+
| Downgrade | During recent auditing, we noticed that |
| | network authentication is not forced upon remote |
| | connections to our Windows 2012 server. That |
| | led us to investigate our system for |
| | suspicious logins further. Provided the server's event |
| | logs, can you find any suspicious successful |
| | login? |
+-----------+---------------------------------------------------------+
Which event log contains information about logon and logoff events? (for example: Setup)
>
There are five main logs in Windows:
- Application
- System
- Security
- Setup
- Forwarded events
The one that informs about logon and logoff events is Security:
Which event log contains information about logon and logoff events? (for example: Setup)
> security
[+] Correct!
What is the event id for logs for a successful logon to a local computer? (for example: 1337)
>
If we search for this event identifier, we will see that it is 4624 (more information here):
What is the event id for logs for a successful logon to a local computer? (for example: 1337)
> 4624
[+] Correct!
Which is the default Active Directory authentication protocol? (for example: http)
>
This question is well-known for people who solve Windows machines on Hack The Box…
Which is the default Active Directory authentication protocol? (for example: http)
> kerberos
[+] Correct!
Looking at all the logon events, what is the AuthPackage that stands out as different from all the rest? (for example: http)
>
Inspecting events
At this point, we can open the Event Viewer in Windows and inspect the events of Security.evtx:
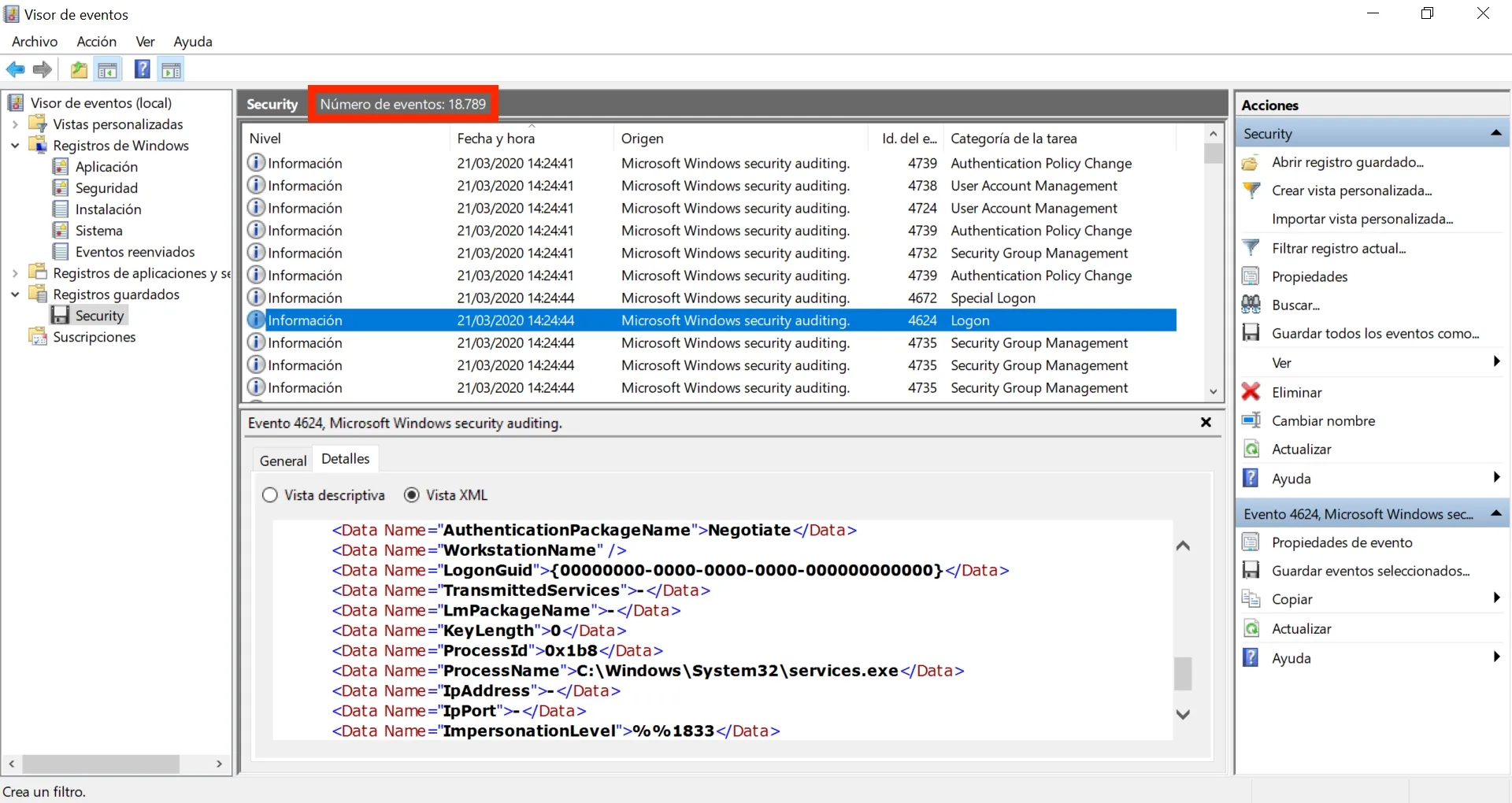
We have a lot of events (18789). Let’s apply a filter and show only successful logon events (ID 4624):
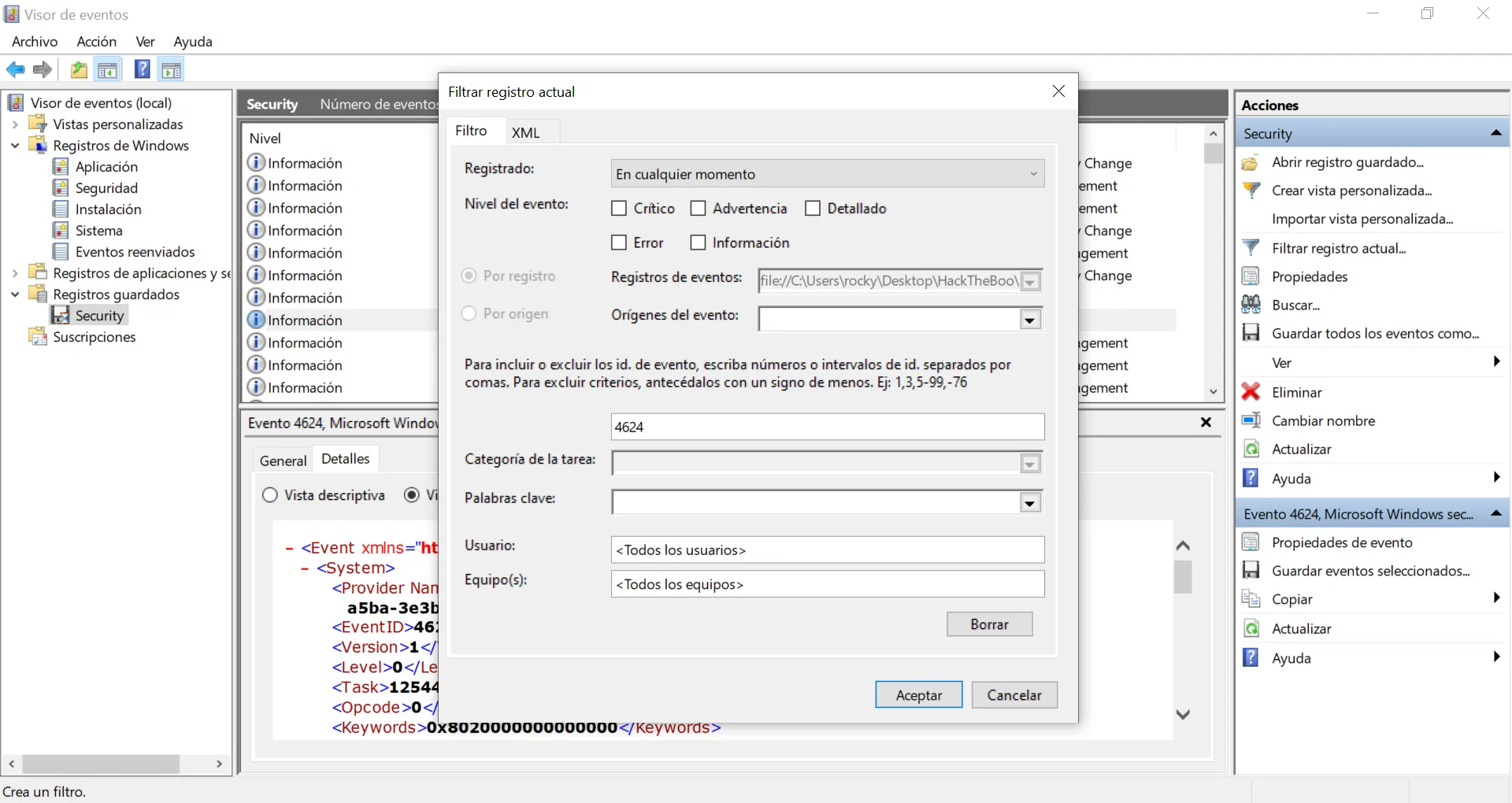
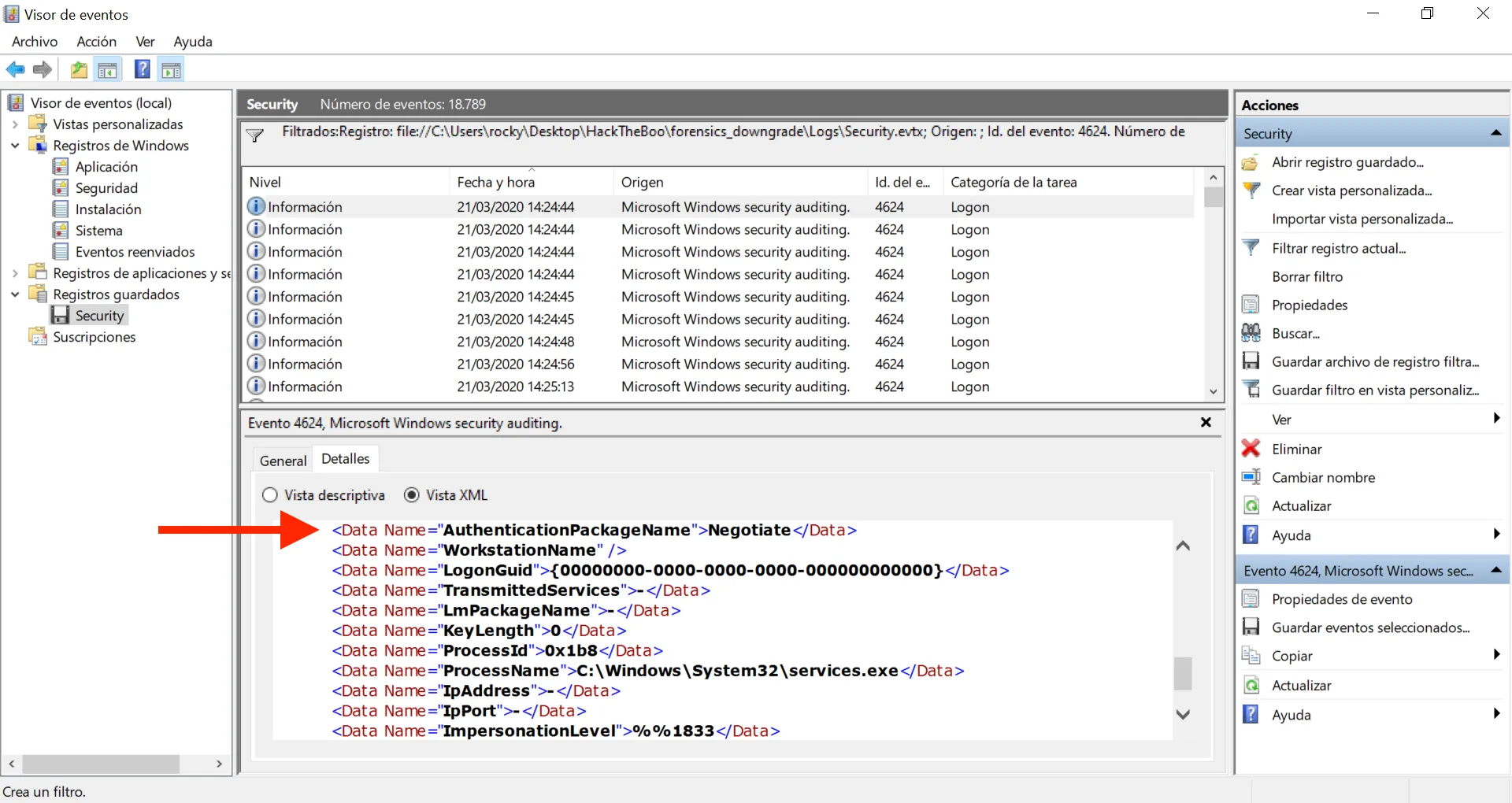
We still have a lot of events. Let’s use XML to filter by AuthenticationPackageName (the attribute that is referred by the question). There are a lot of events that have Negotiate as value, so let’s suppress these events:
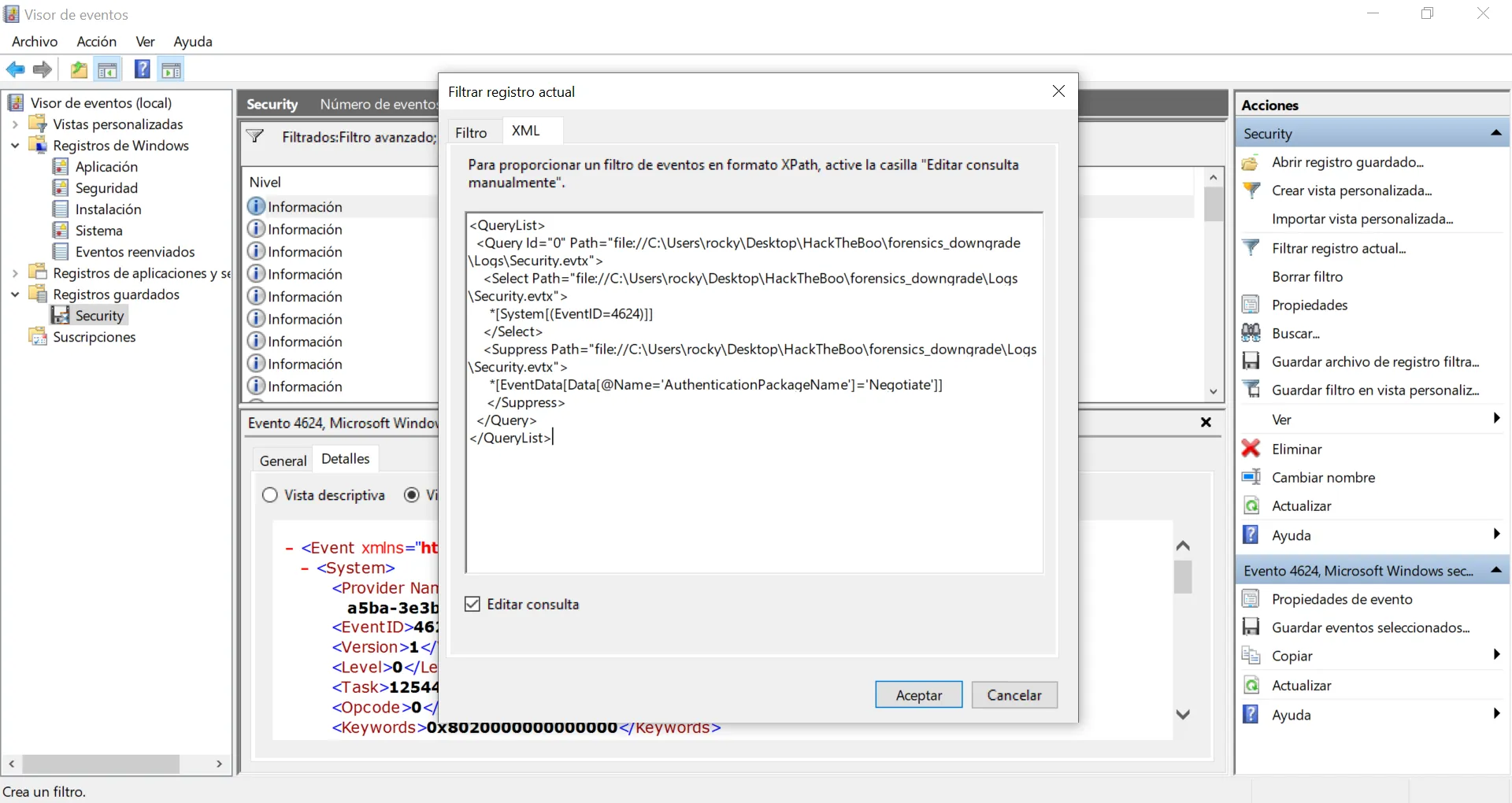
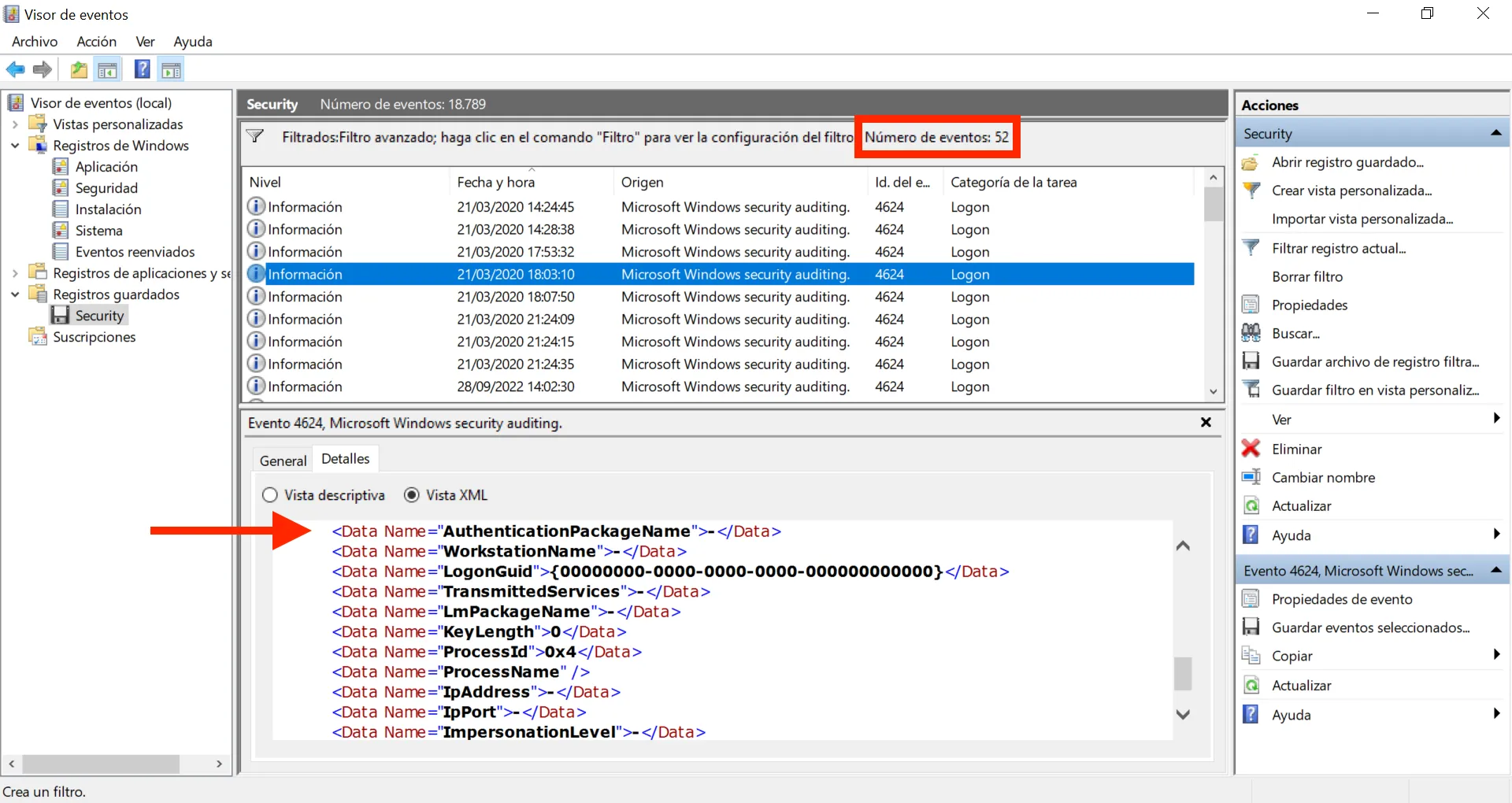
Now we have only 52 events, but some of them have a blank value for AuthenticationPackageName (-), let’s filter a bit more:
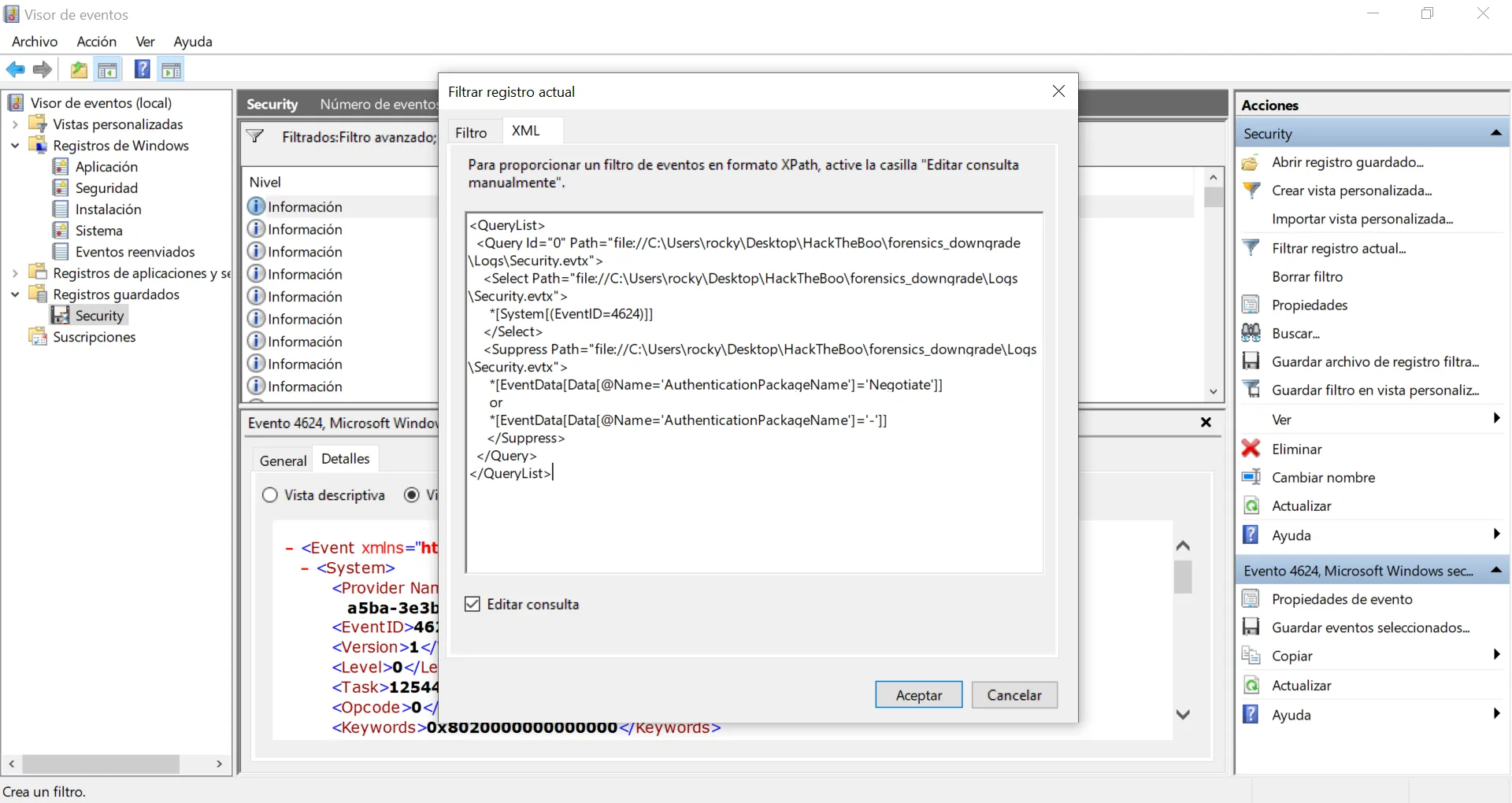
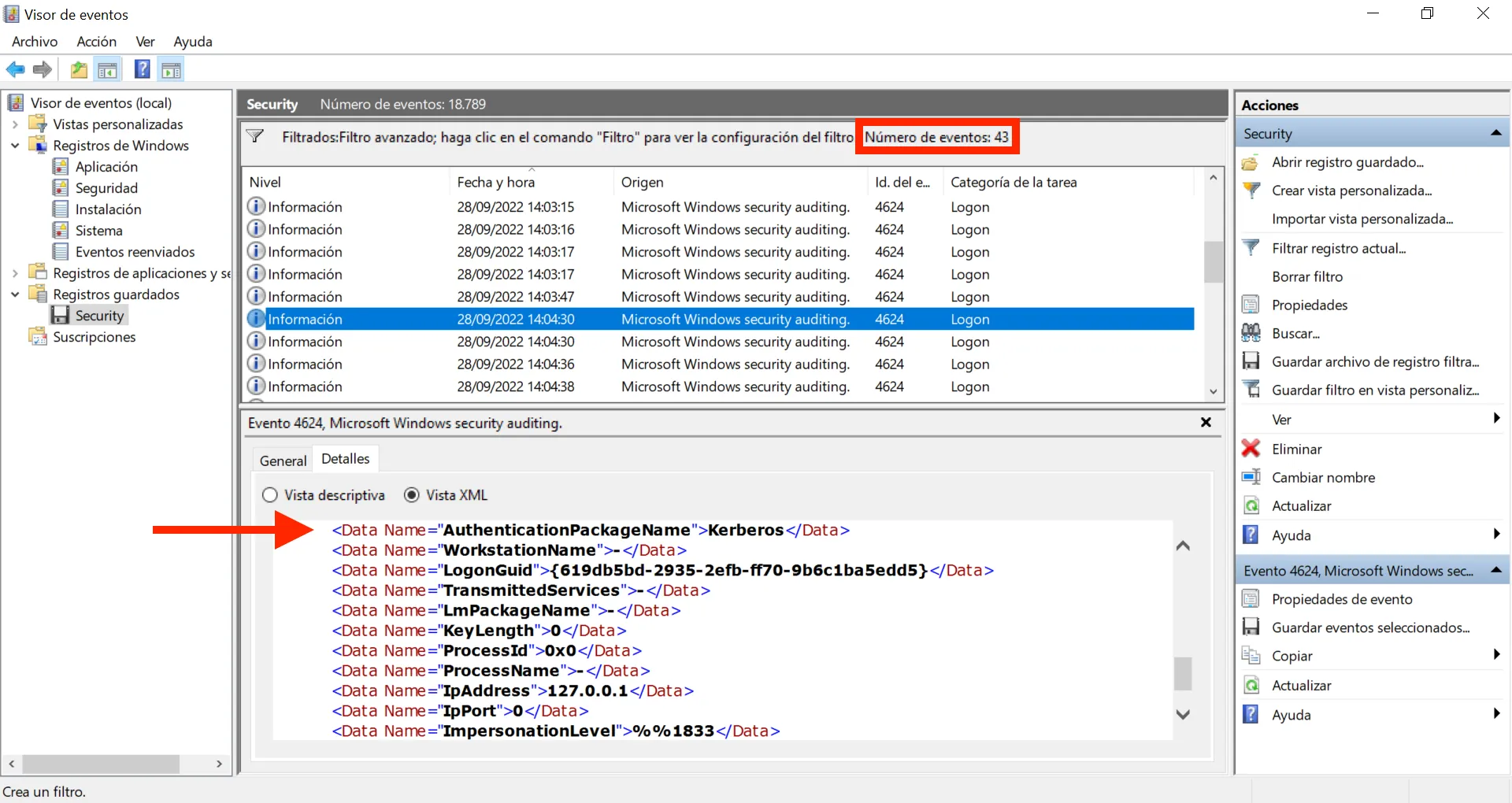
Alright, 43 events. Yet another normal AuthenticationPackageName is Kerberos, let’s add it to the filter:
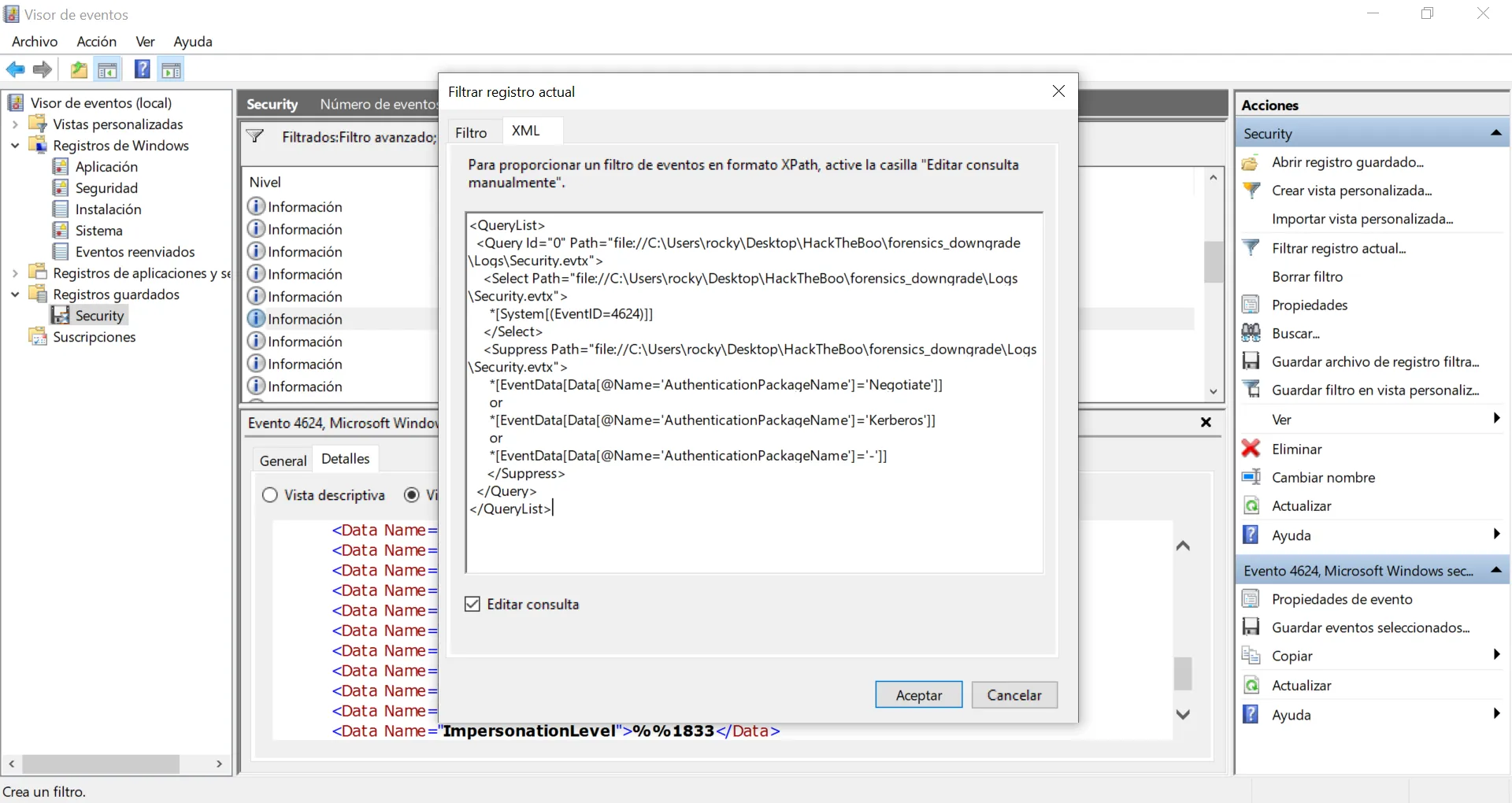
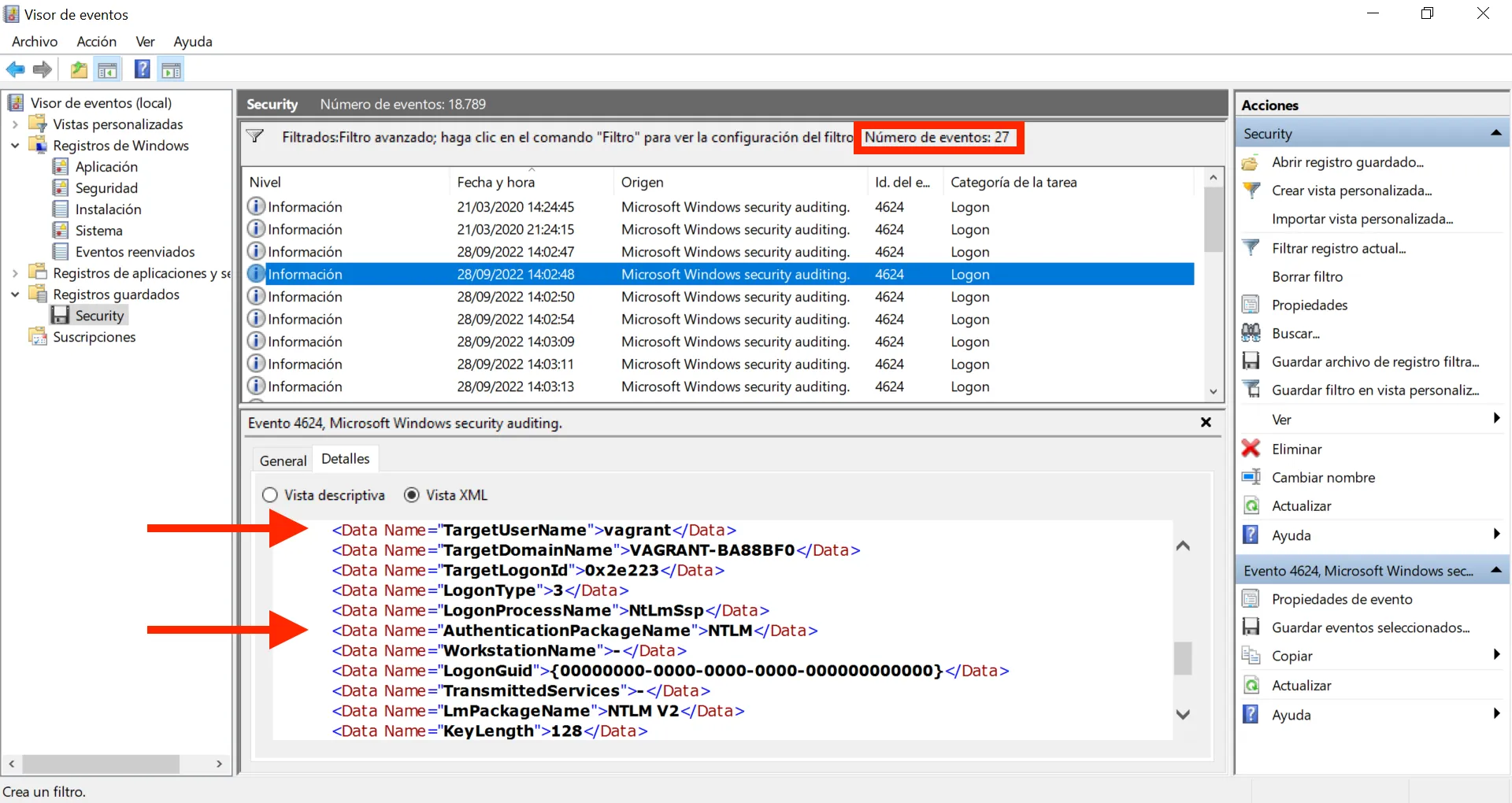
Great, now we only have NTLM as AuthenticationPackageName, and this is the answer to the question:
Looking at all the logon events, what is the AuthPackage that stands out as different from all the rest? (for example: http)
> ntlm
[+] Correct!
What is the timestamp of the suspicious login (yyyy-MM-ddTHH:mm:ss) UTC? (for example, 2021-10-10T08:23:12)
>
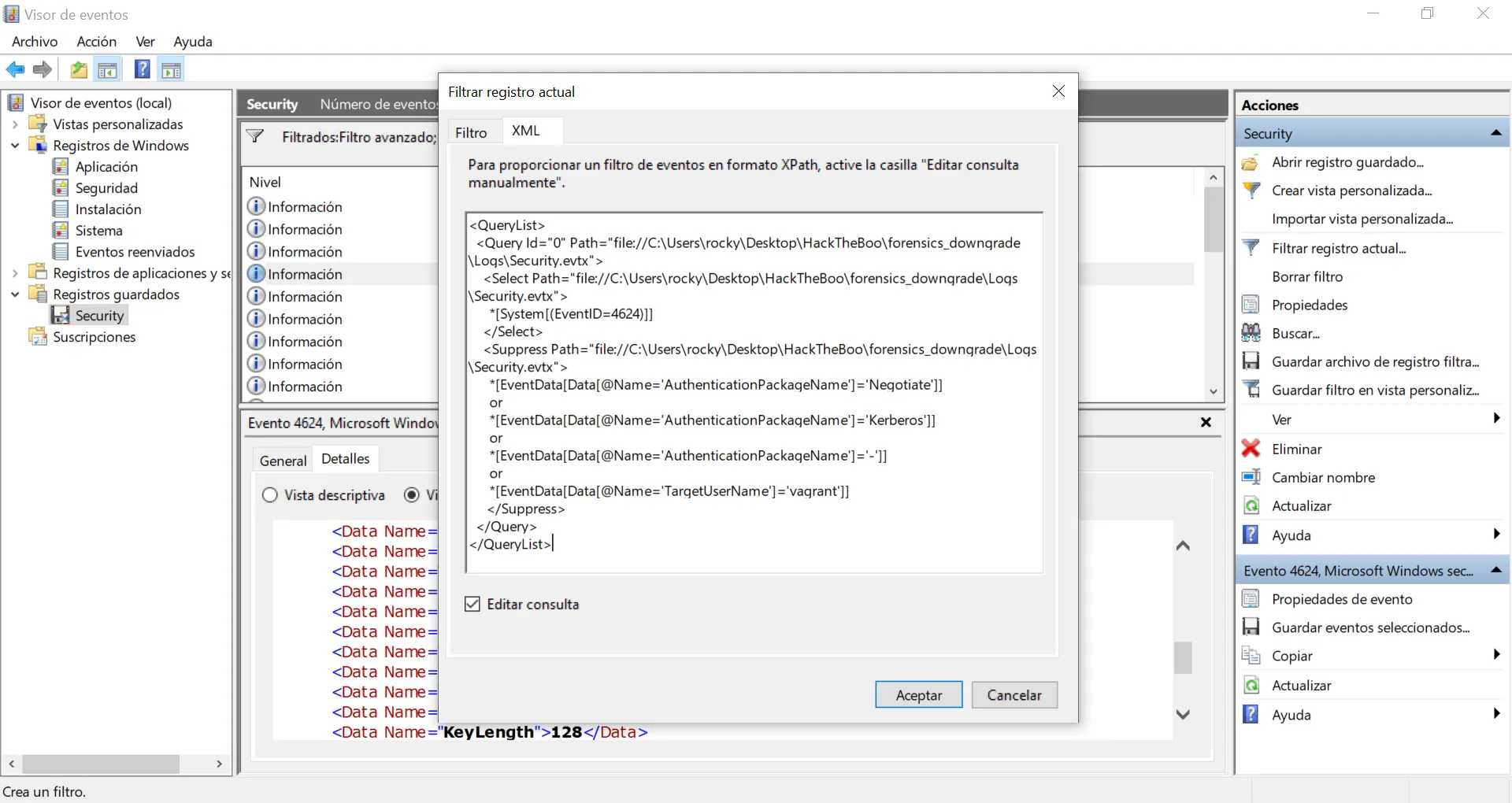
Finally, we can suppress those events where the user authenticating is vagrant (as shown in the previous image):
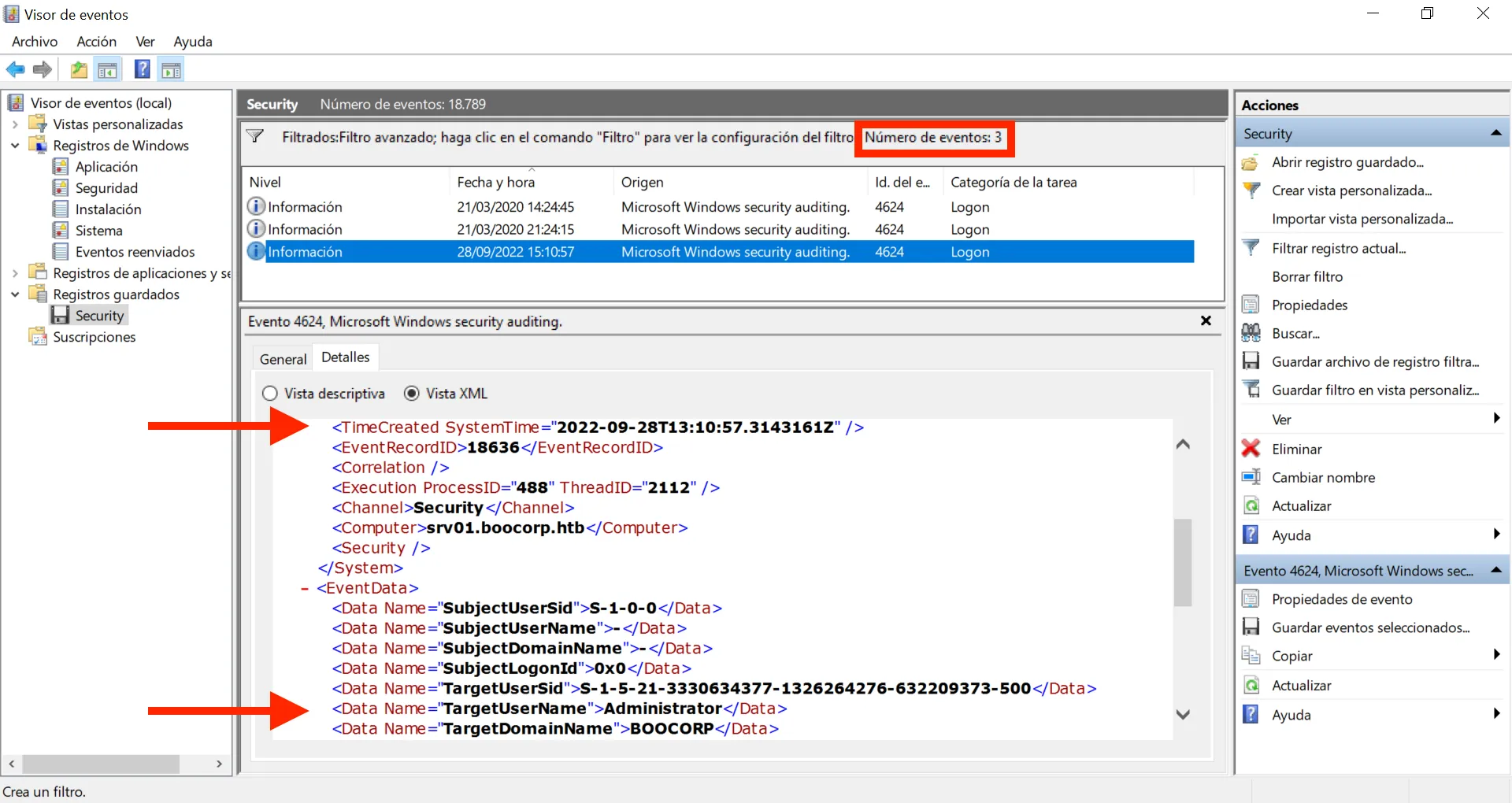
And we have only 3 events. Two of them are ANONYMOUS LOGON, and the last one is authenticating as Administrator, so it is suspicious.
Flag
We can take the timestamp of the suspicious event and answer the question to get the flag:
What is the timestamp of the suspicious login (yyyy-MM-ddTHH:mm:ss) UTC? (for example, 2021-10-10T08:23:12)
> 2022-09-28T13:10:57
[+] Correct!
[+] Here is the flag: HTB{34sy_t0_d0_4nd_34asy_t0_d3t3ct}