Keep Tryin'
1 minute to read
We are given a PCAP file with some of TCP segments, HTTP messages and DNS queries:
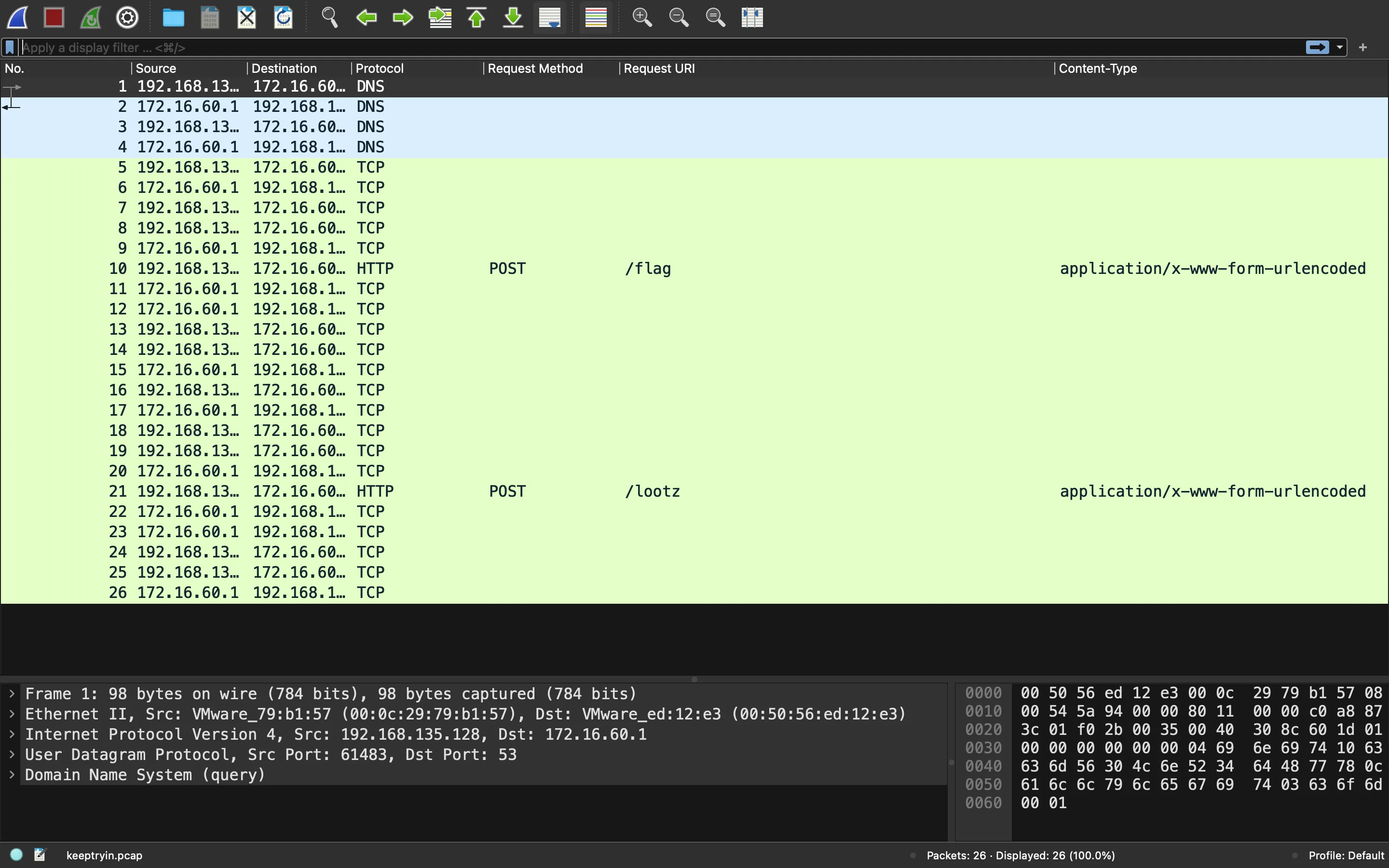
HTTP traffic
First of all, let’s analyze the HTTP messages:
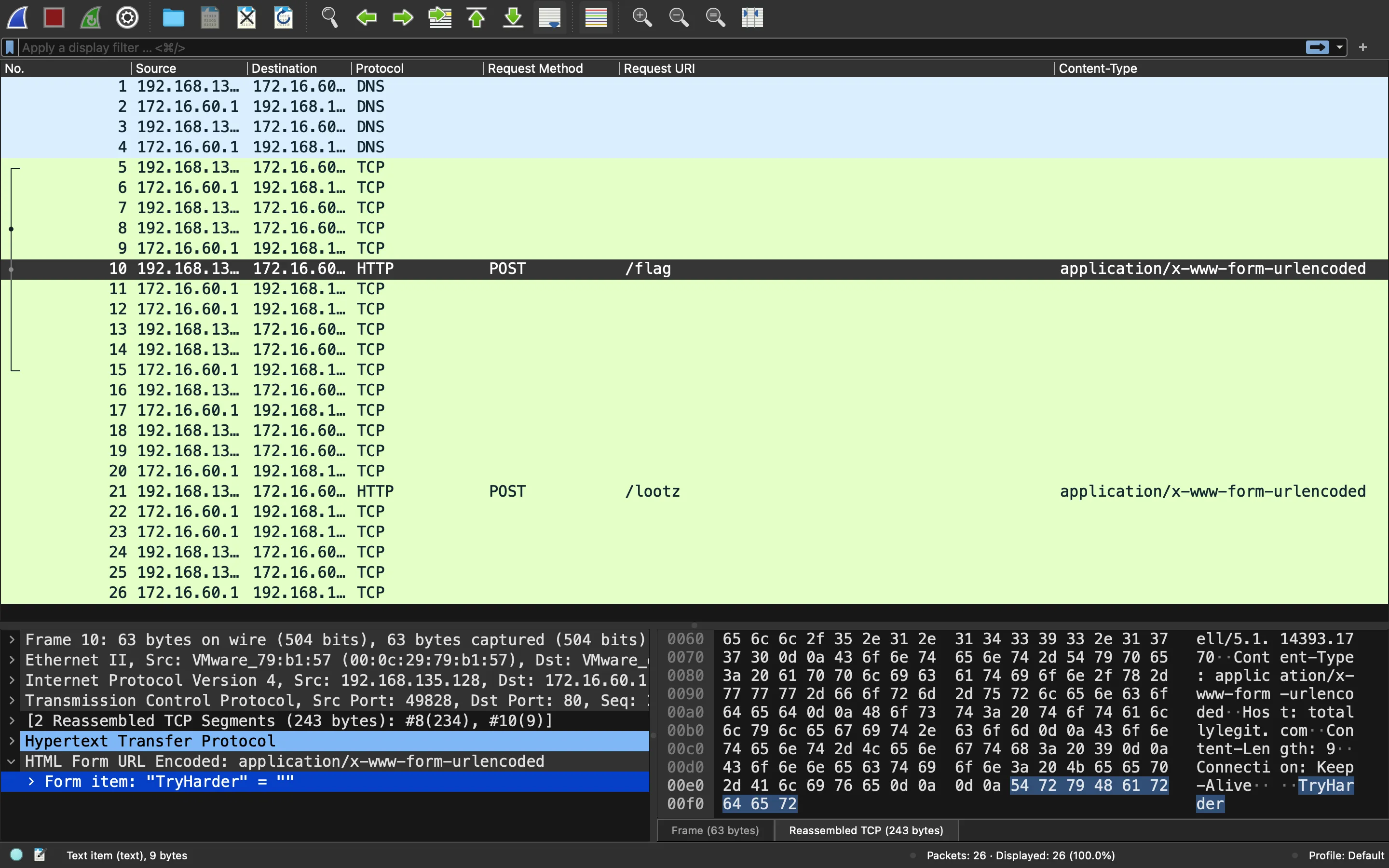
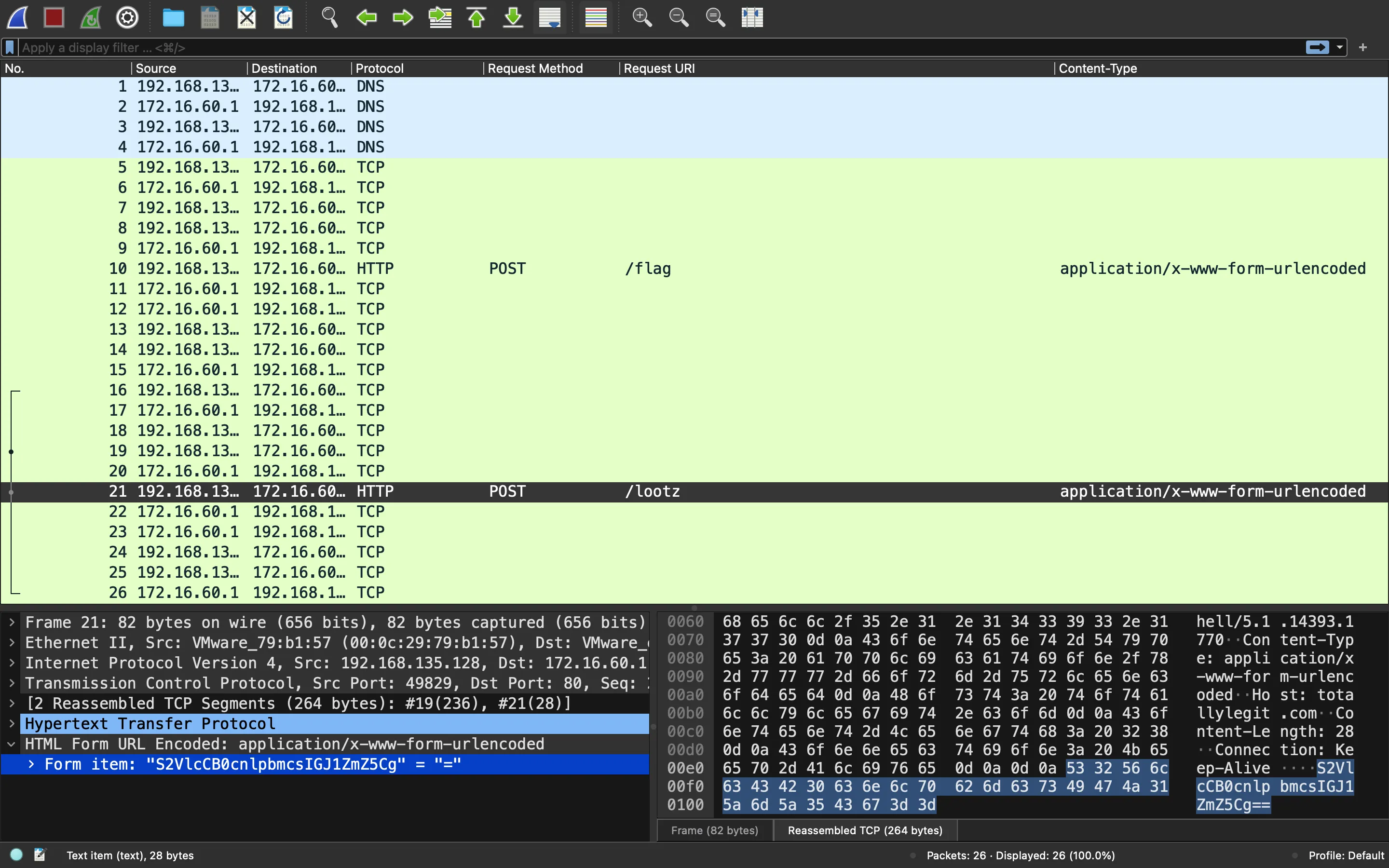
The first one looks useless, it only shows TryHarder. And the second one has a Base64-encoded string: S2VlcCB0cnlpbmcsIGJ1ZmZ5Cg==. But…
$ echo S2VlcCB0cnlpbmcsIGJ1ZmZ5Cg== | base64 -d
Keep trying, buffy
DNS queries
These are the DNS queries above:
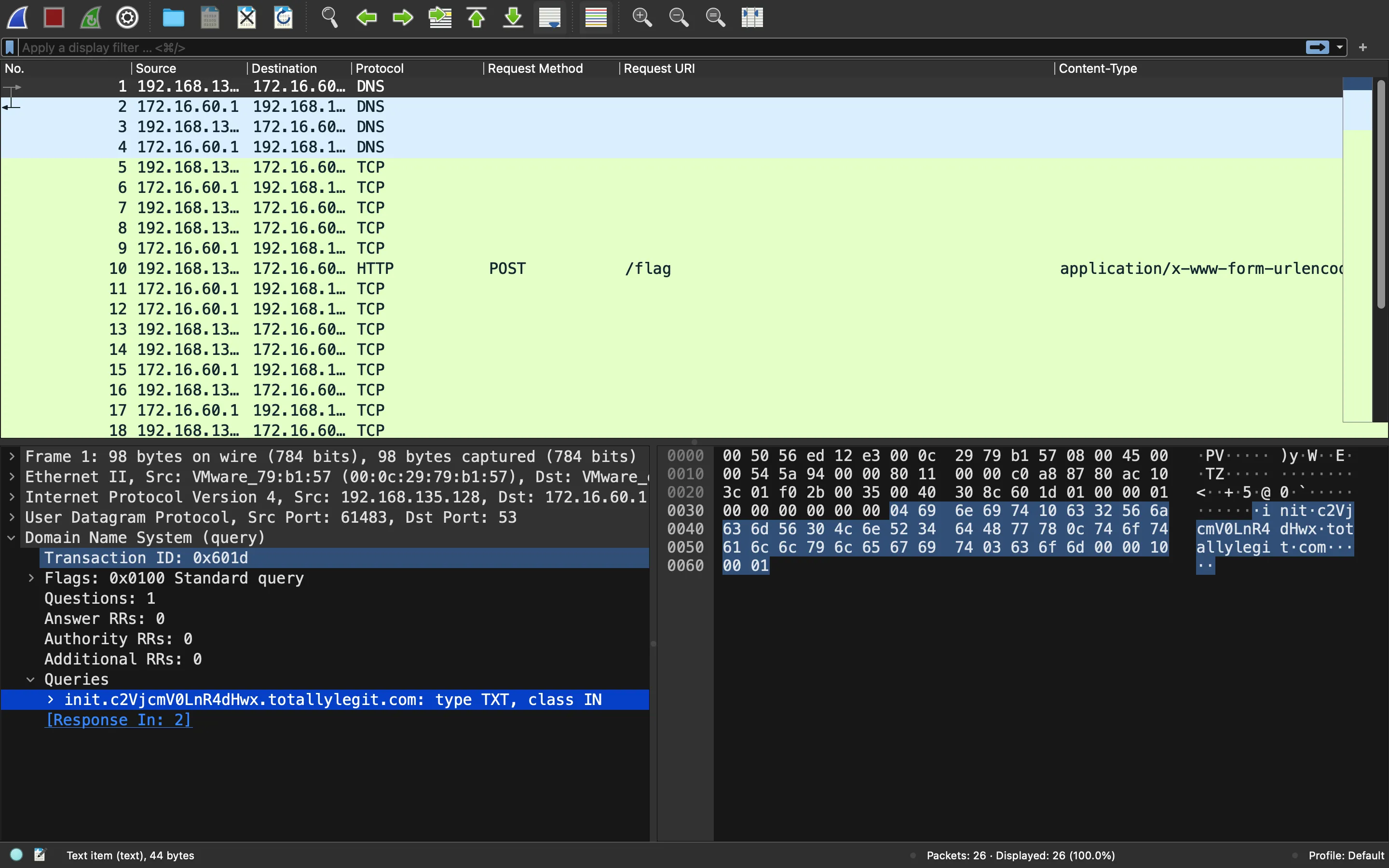
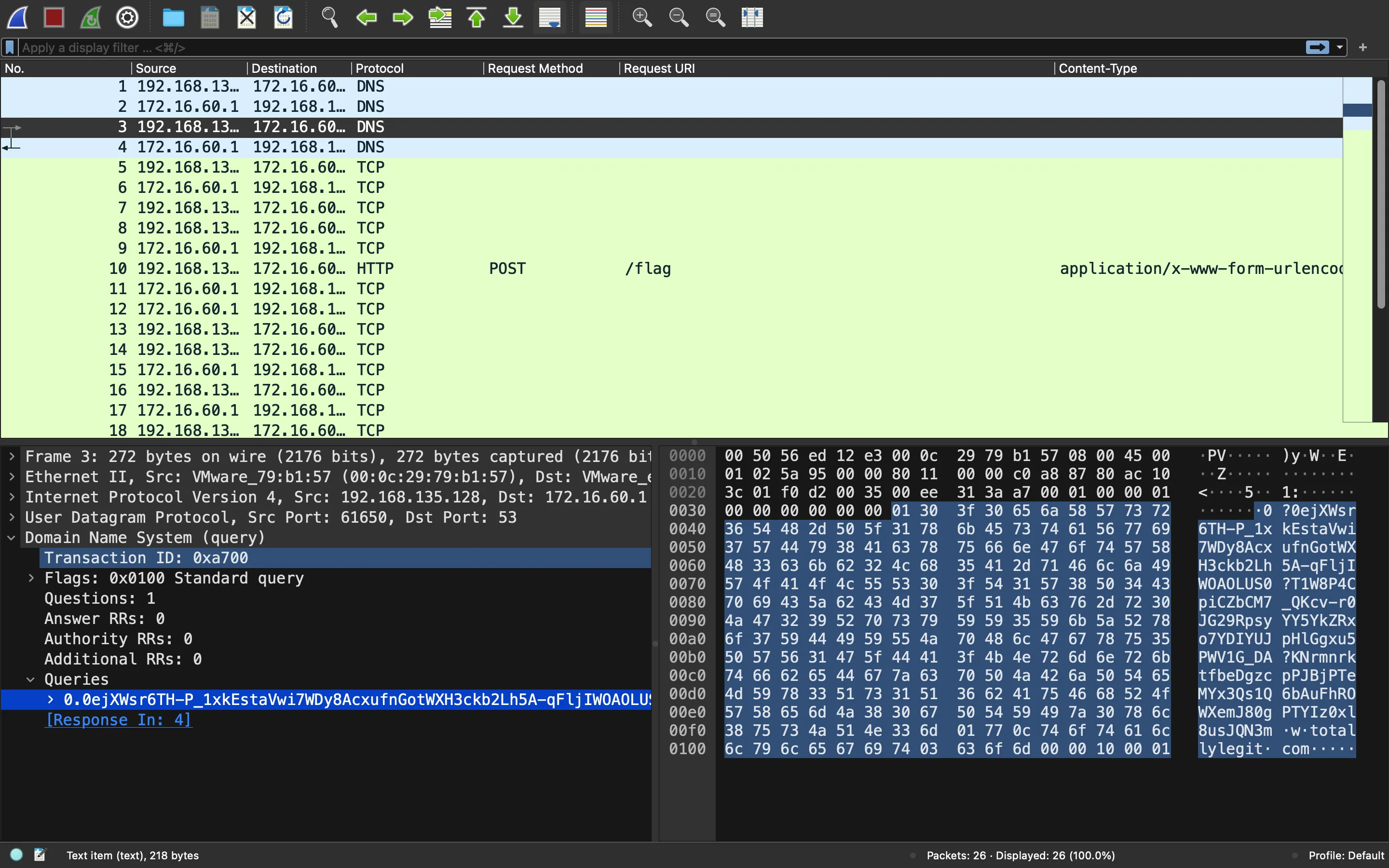
They look very strange. In fact, the first one contains a Base64-encoded string:
$ echo c2VjcmV0LnR4dHwx | base64 -d
secret.txt|1
The second query subdomain looks encrypted.
Solution
After some tests, using CyberChef we discover that the second query was Base64-encoded (URL-safe alphabet) and encrypted with RC4, using TryHarder as passphrase:
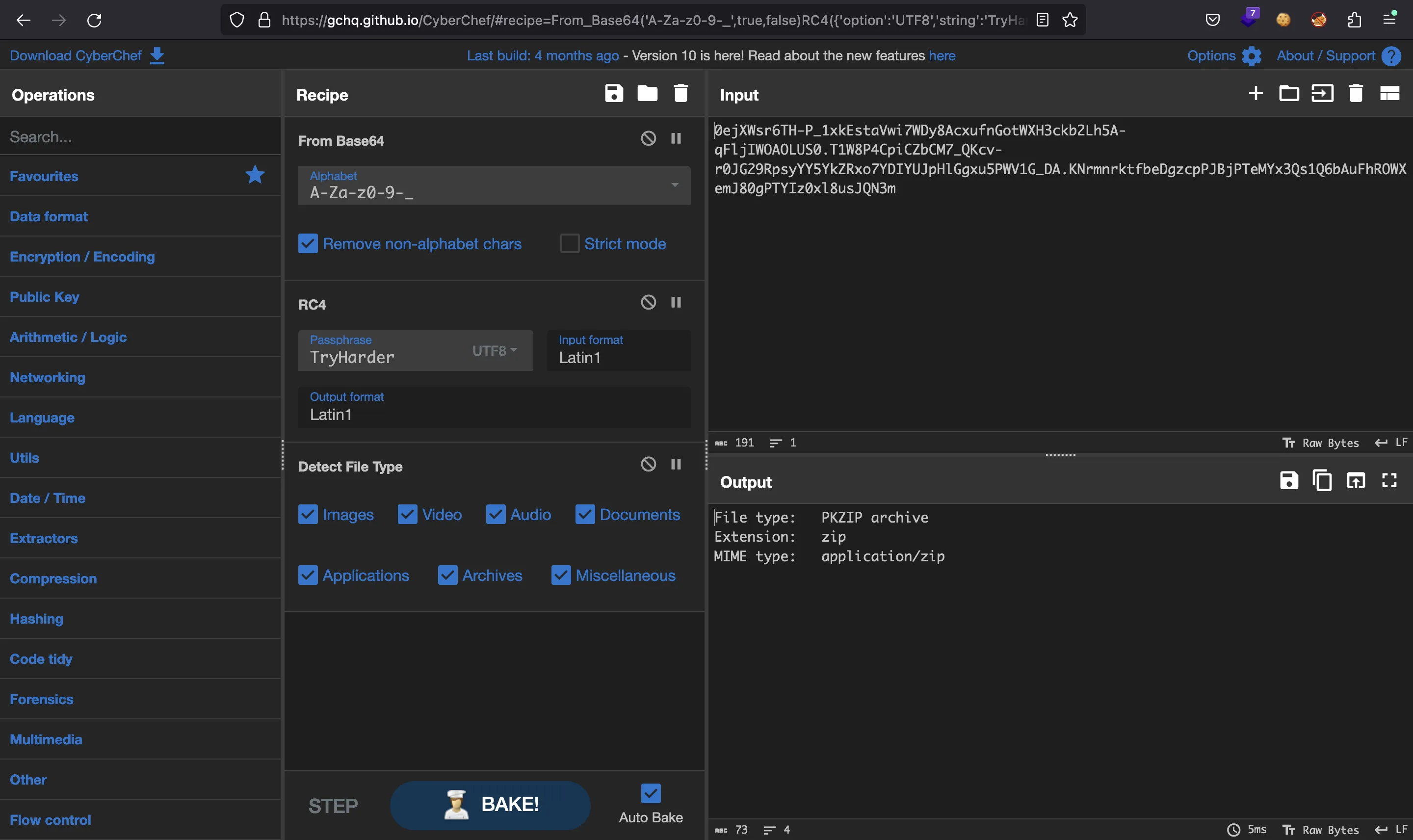
The result is a ZIP archive (we can note the magic bytes PK, or use Detect File Type recipe):
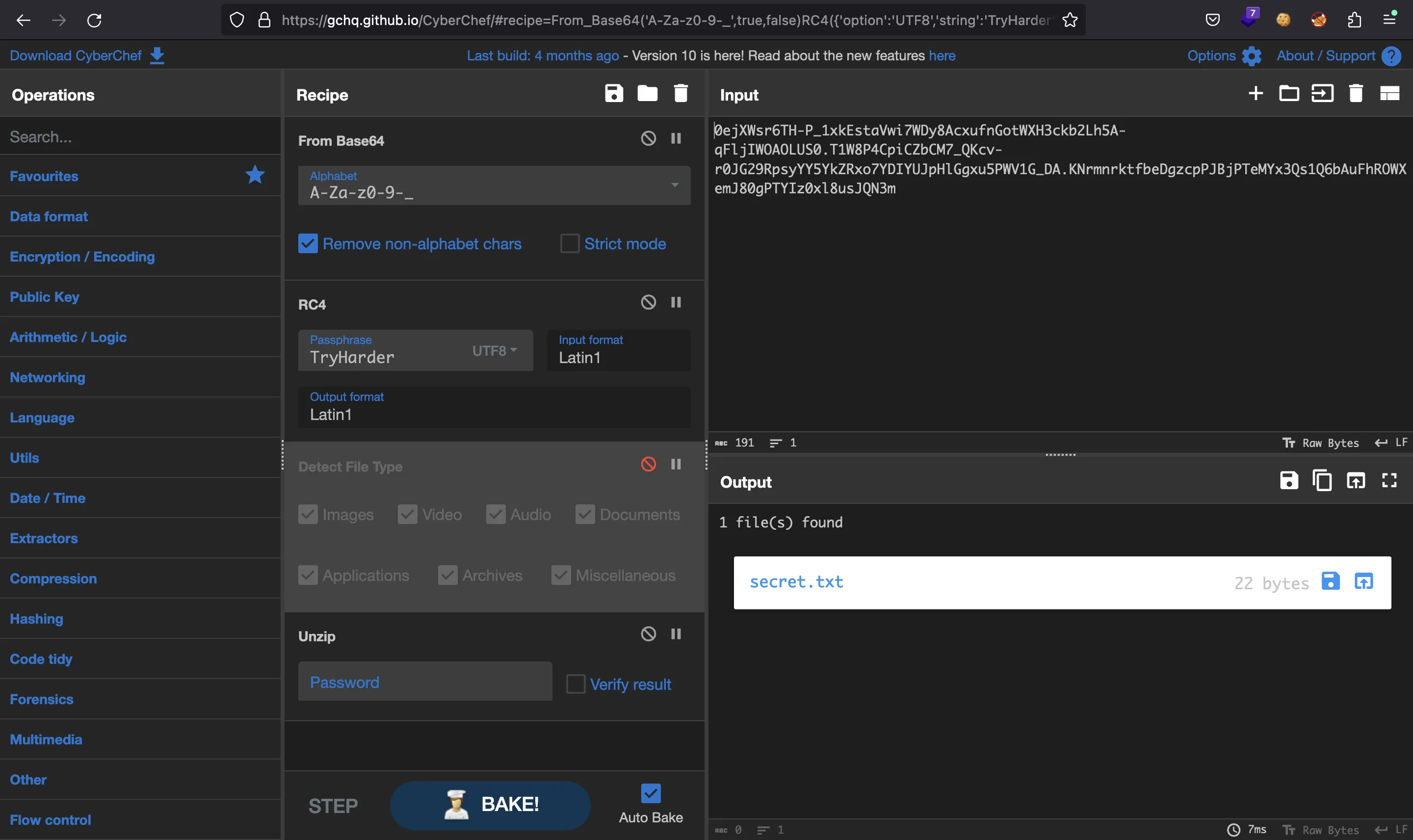
Flag
Finally, once we use Unzip recipe, we will see the file secret.txt, which contains the flag (HTB{$n3aky_DN$_Tr1ck$}):