No Place To Hide
3 minutes to read
We are given these log files from a Windows RDP session:
$ file Cache0000.bin
Cache0000.bin: data
$ file bcache24.bmc
bcache24.bmc: empty
$ du -h Cache0000.bin bcache24.bmc
17M Cache0000.bin
0B bcache24.bmc
And this is the description of the challenge:
We found evidence of a password spray attack against the Domain Controller, and identified a suspicious RDP session. We’ll provide you with our RDP logs and other files. Can you see what they were up to?
Bitmap extraction
Searching for tools to analyze .bmc files, we find bmc_tools, which is a Python script that extracts bitmap images (.bmp) from the log files we have.
For the moment, we can use the default configuration:
$ git clone https://github.com/ANSSI-FR/bmc-tools
...
$ python3 bmc-tools/bmc-tools.py -h
usage: bmc-tools.py [-h] -s SRC -d DEST [-c COUNT] [-v] [-o] [-b] [-w WIDTH]
RDP Bitmap Cache parser (v. 3.00, 2022/02/10)
options:
-h, --help show this help message and exit
-s SRC, --src SRC Specify the BMCache file or directory to process.
-d DEST, --dest DEST Specify the directory where to store the extracted bitmaps.
-c COUNT, --count COUNT
Only extract the given number of bitmaps.
-v, --verbose Determine the amount of information displayed.
-o, --old Extract the old bitmap data found in the BMCache file.
-b, --bitmap Provide a big bitmap aggregating all the tiles.
-w WIDTH, --width WIDTH
Specify the number of tiles per line of the aggregated bitmap (default=64).
$ mkdir bitmaps
$ python3 bmc-tools/bmc-tools.py -s . -d bitmaps
[+++] Processing a directory...
[!!!] Unable to retrieve file contents; aborting.
[===] 1162 tiles successfully extracted in the end.
[===] Successfully exported 1162 files.
Now we get a lot of .bmp images:
$ ls bitmaps | head
Cache0000.bin_0000.bmp
Cache0000.bin_0001.bmp
Cache0000.bin_0002.bmp
Cache0000.bin_0003.bmp
Cache0000.bin_0004.bmp
Cache0000.bin_0005.bmp
Cache0000.bin_0006.bmp
Cache0000.bin_0007.bmp
Cache0000.bin_0008.bmp
Cache0000.bin_0009.bmp
$ ls bitmaps | wc -l
1162
BMP to JPEG conversion
To view these images we need to convert them to JPEG or PNG formats, so we can use mogrify from ImageMagick. To avoid installing all the program suite, we can use Docker:
$ docker run --rm -v "${PWD}":/tmp --entrypoint=bash -it dpokidov/imagemagick
root@e1710a97fea6:/imgs# cd /tmp/bitmaps
root@e1710a97fea6:/tmp/bitmaps# mogrify -format jpg *.bmp
root@e1710a97fea6:/tmp/bitmaps# mkdir ../images
root@e1710a97fea6:/tmp# mv *.jpg ../images
Now we can examine these JPEG images. Unfortunately, their width is 64 pixels (the default one), so they show a small fraction of the screen:
Joining all tiles
Therefore, let’s try adding more options to bmc_tools. For example, -b to join all tiles:
$ python3 bmc-tools/bmc-tools.py -s . -d bitmaps -b
[+++] Processing a directory...
[!!!] Unable to retrieve file contents; aborting.
[===] 1162 tiles successfully extracted in the end.
[===] Successfully exported 1162 files.
[===] Successfully exported collage file.
$ ls bitmaps | wc -l
1163
$ docker run --rm -v "${PWD}":/tmp --entrypoint=bash -it dpokidov/imagemagick
root@1d683a9c7246:/imgs# cd /tmp/bitmaps/
root@1d683a9c7246:/tmp/bitmaps# mogrify -format jpg Cache0000.bin_collage.bmp
root@1d683a9c7246:/tmp/bitmaps# mv *.jpg ../images/
The tool will generate a collage with all 1162 tiles. The resulting image looks a bit weird:

There’s no automatic tool to join the tiles, since the tile images come from a cache memory, which might not be sorted.
Flag
Nevertheless, we can zoom in and glimpse some characters of the flag and reconstruct it ourselves:
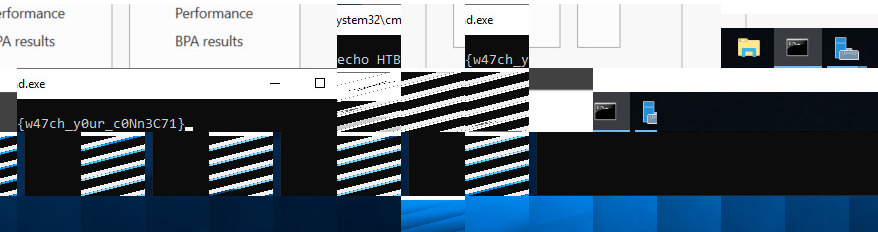
HTB{w47ch_y0ur_c0Nn3C71}