Secure Digital
2 minutes to read
We are told that someone has read the master key of a microSD card, and we are given the signal traces in a trace_captured.sal file.
Signal analysis
We can use Saleae Logic 2 to analyze the traces, and we have this:
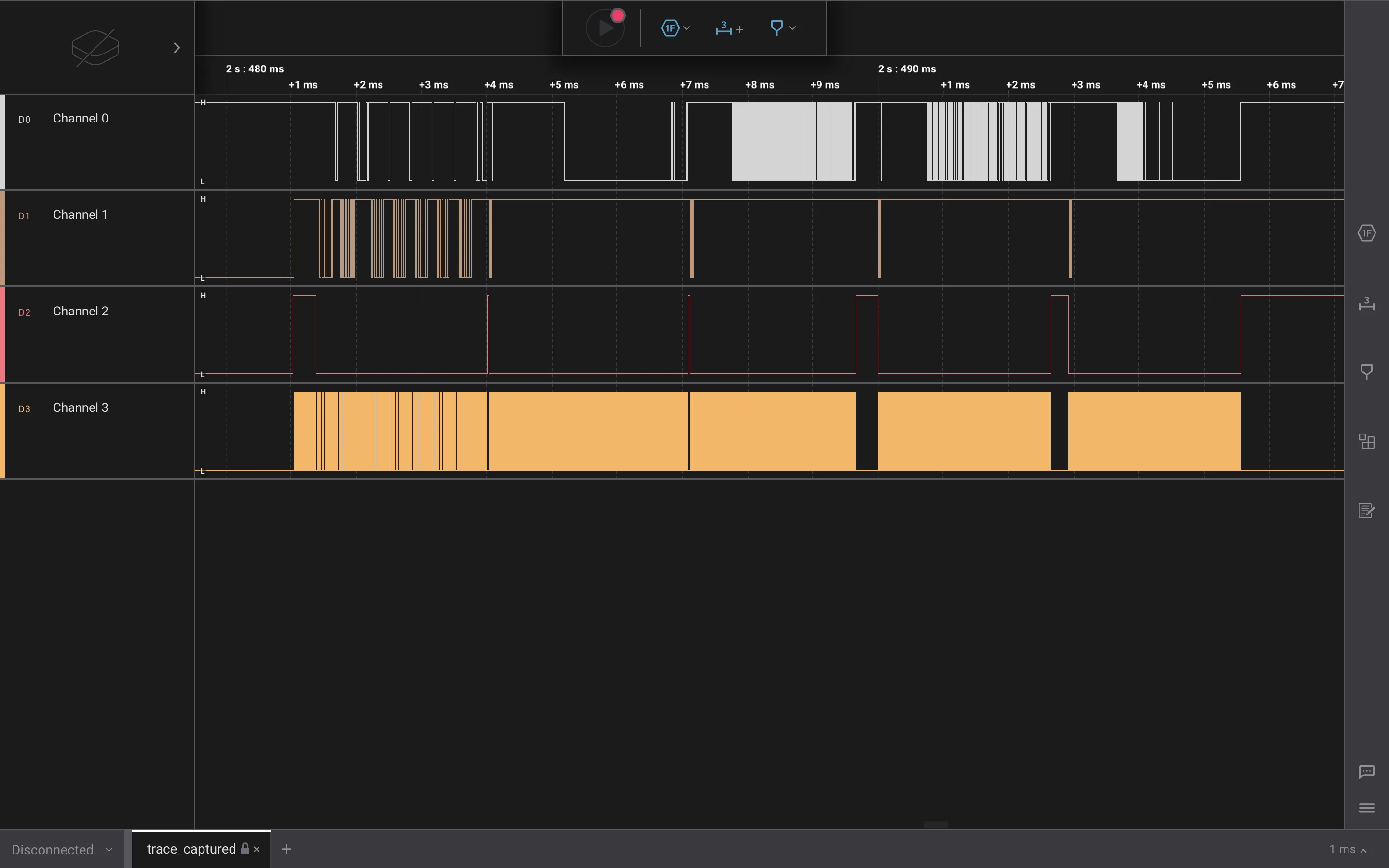
SPI
If we research a bit, we will find out that microSD cards use Serial Peripheral Interface (SPI) as a communication protocol. Comparing the signals we have to the ones we see in SPI Analyzer - User Guide, we can guess that Channel 0 and Channel 1 are MISO or MOSI, Channel 2 is Enable and Channel 3 is Clock, so we can add the analyzer:
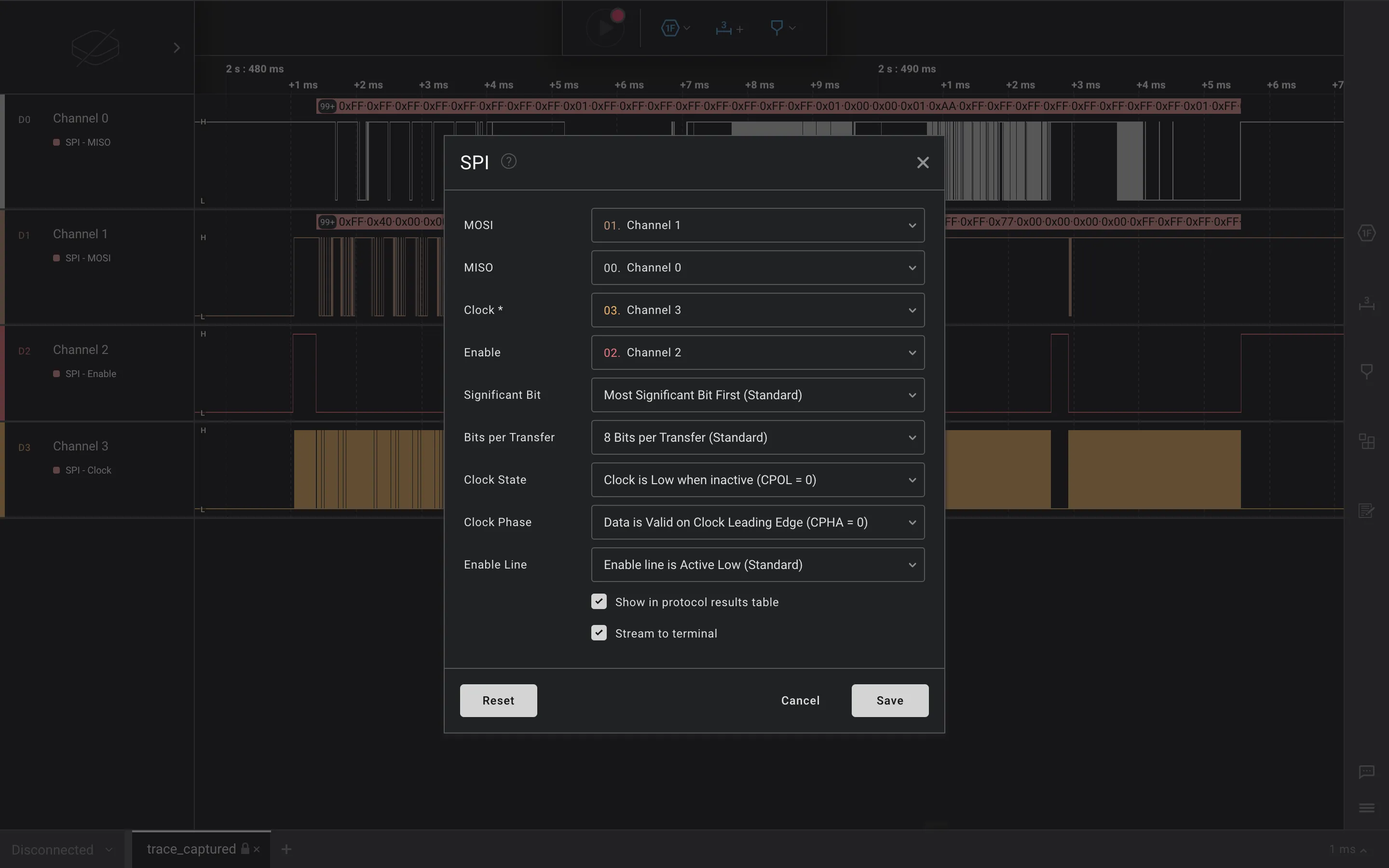
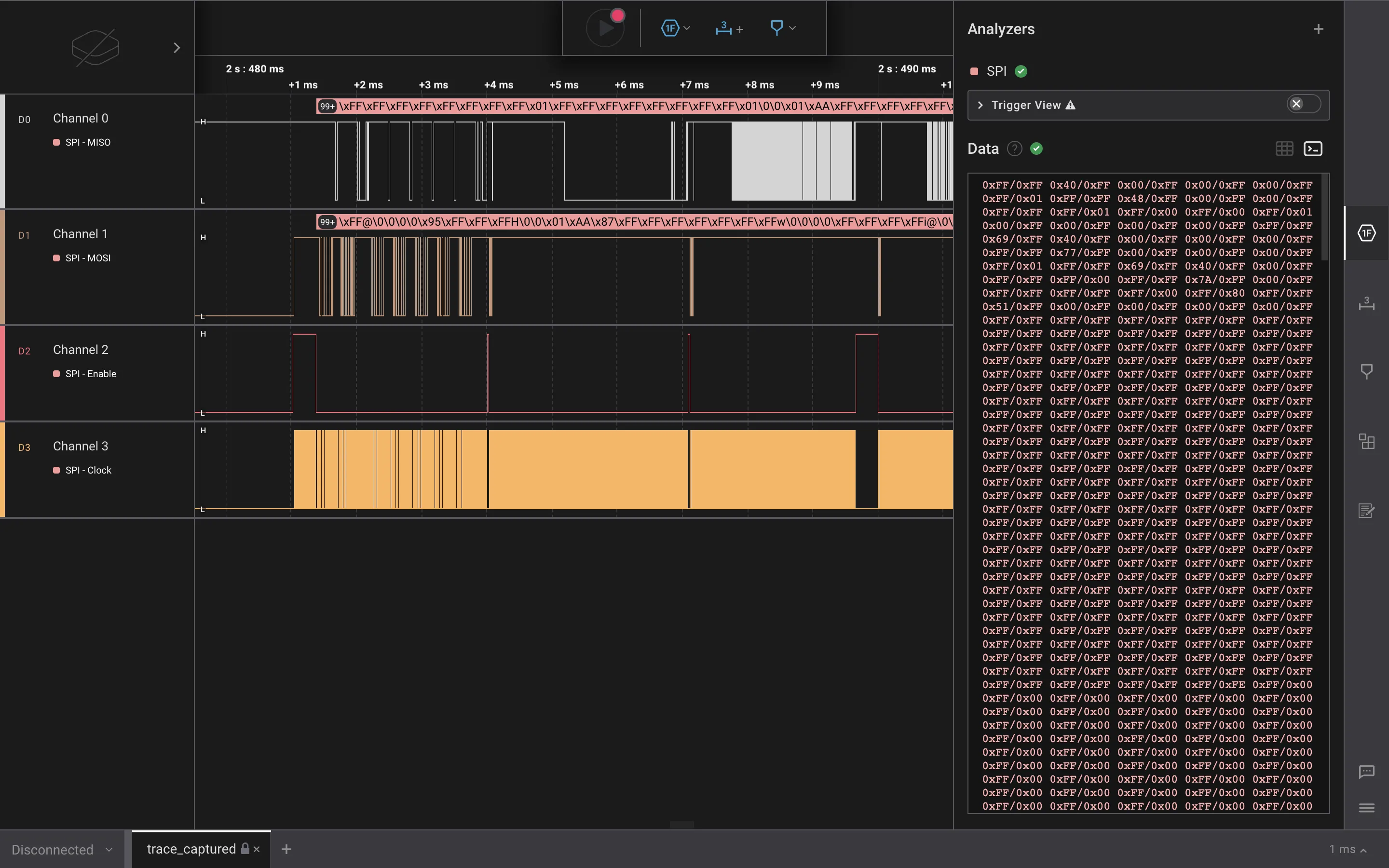
At this point, we see that there are no errors in the console, so everything looks correct.
Decoding information
Next thing we can do is dump all this information to a CSV file. We can decode it as ASCII:
And we have this CSV file:
$ head data.csv; echo; tail data.csv
Time [s],Packet ID,MOSI,MISO
2.481394520000000,0,\xFF,\xFF
2.481428680000000,0,@,\xFF
2.481472660000000,0,\0,\xFF
2.481513460000000,0,\0,\xFF
2.481550740000000,0,\0,\xFF
2.481584520000000,0,\0,\xFF
2.481618060000000,0,\x95,\xFF
2.481651280000000,0,\xFF,\xFF
2.481685000000000,0,\xFF,\x01
2.495525140000000,0,\xFF,\0
2.495528780000000,0,\xFF,\0
2.495532400000000,0,\xFF,\0
2.495536040000000,0,\xFF,\0
2.495539660000000,0,\xFF,\0
2.495543300000000,0,\xFF,\0
2.495546920000000,0,\xFF,\0
2.495550560000000,0,\xFF,\0
2.495556180000000,0,\xFF,\x86
2.495560320000000,0,\xFF,b
If we take a look at the whole CSV file, we will notice a lot of \xFF,\xFF and \xFF,\0 values. Let’s get rid of them:
$ grep -vE '\\xFF,\\xFF|\\xFF,\\0' data.csv | tail
2.494027840000000,0,\xFF,v
2.494031460000000,0,\xFF,1
2.494035100000000,0,\xFF,c
2.494038720000000,0,\xFF,3
2.494042340000000,0,\xFF,5
2.494045980000000,0,\xFF,}
2.494049600000000,0,\xFF,\r
2.494053240000000,0,\xFF,\n
2.495556180000000,0,\xFF,\x86
2.495560320000000,0,\xFF,b
Looks promising, right? Let’s take some more values:
$ grep -vE '\\xFF,\\xFF|\\xFF,\\0' data.csv | tail -55
2.493864540000000,0,\xFF,H
2.493868160000000,0,\xFF,T
2.493871800000000,0,\xFF,B
2.493875420000000,0,\xFF,{
2.493879060000000,0,\xFF,u
2.493882680000000,0,\xFF,n
2.493886320000000,0,\xFF,p
2.493889940000000,0,\xFF,2
2.493893560000000,0,\xFF,0
2.493897200000000,0,\xFF,7
2.493900820000000,0,\xFF,3
2.493904460000000,0,\xFF,c
2.493908080000000,0,\xFF,7
2.493911720000000,0,\xFF,3
2.493915340000000,0,\xFF,d
2.493918980000000,0,\xFF,_
2.493922600000000,0,\xFF,5
2.493926220000000,0,\xFF,3
2.493929860000000,0,\xFF,2
2.493933480000000,0,\xFF,1
2.493937120000000,0,\xFF,4
2.493940740000000,0,\xFF,1
2.493944380000000,0,\xFF,_
2.493948000000000,0,\xFF,p
2.493951620000000,0,\xFF,2
2.493955260000000,0,\xFF,0
2.493958880000000,0,\xFF,7
2.493962520000000,0,\xFF,0
2.493966140000000,0,\xFF,c
2.493969780000000,0,\xFF,0
2.493973400000000,0,\xFF,1
2.493977040000000,0,\xFF,5
2.493980660000000,0,\xFF,_
2.493984280000000,0,\xFF,0
2.493987920000000,0,\xFF,n
2.493991540000000,0,\xFF,_
2.493995180000000,0,\xFF,5
2.493998800000000,0,\xFF,3
2.494002440000000,0,\xFF,c
2.494006060000000,0,\xFF,u
2.494009700000000,0,\xFF,2
2.494013320000000,0,\xFF,3
2.494016940000000,0,\xFF,_
2.494020580000000,0,\xFF,d
2.494024200000000,0,\xFF,3
2.494027840000000,0,\xFF,v
2.494031460000000,0,\xFF,1
2.494035100000000,0,\xFF,c
2.494038720000000,0,\xFF,3
2.494042340000000,0,\xFF,5
2.494045980000000,0,\xFF,}
2.494049600000000,0,\xFF,\r
2.494053240000000,0,\xFF,\n
2.495556180000000,0,\xFF,\x86
2.495560320000000,0,\xFF,b
Great! We can see the flag!
Flag
In the end, we can find the flag using a bit of shell scripting:
$ grep -vE '\\xFF,\\xFF|\\xFF,\\0' data.csv | awk -F , '{ print $4 }' | tr -d \\n | grep -oE 'HTB{.*?}' | sort -u
HTB{unp2073c73d_532141_p2070c015_0n_53cu23_d3v1c35}