Walkie Hackie
5 minutes to read
We are given four radiofrequency signal captures (1.complex to 4.complex) and a website to test codes:
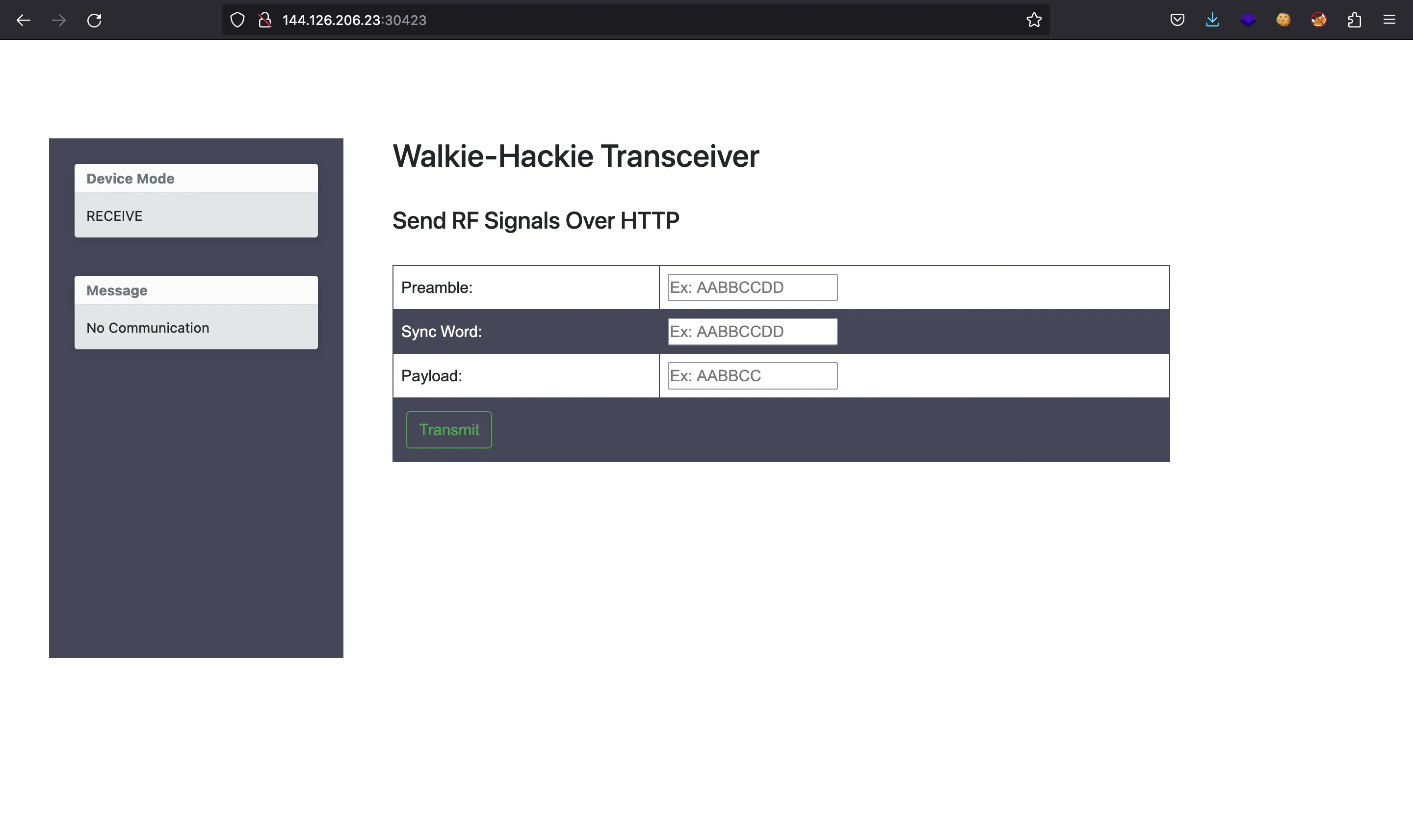
Moreover, this is the description of the challenge:
Our agents got caught during a mission and found that the guards are using old walkie-talkies for their communication. The field team captured their transmissions. Can you interrupt their communication to help our agents escape from the guards?
Radiofrequency analysis
Although there is a hint in the HTML source code of the website pointing to Universal Radio Hacker, I prefer using inspectrum.
If we open 1.complex in inspectrum we will see this signal:
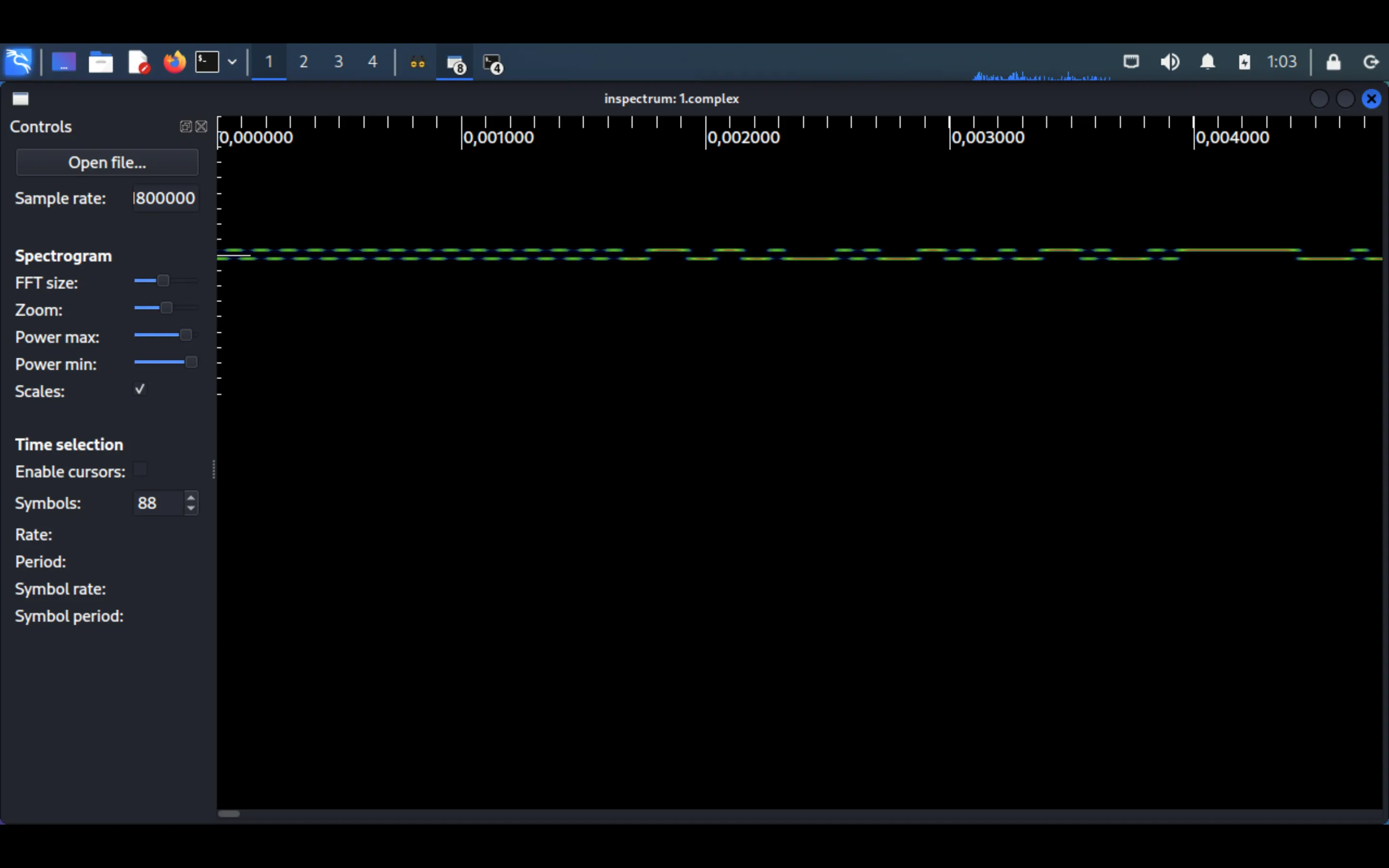
We can identify that it is modulated in 2FSK (Frequency Shift Keying), since there are two lines of frequency. Moreover, there does not seem to be any type of channel encoding (for instance, Manchester). At the beginning, there is a synchronization sequence, used to synchronize the receiver clock.
With inspectrum we are able to add plots and set cursors. In order to get the next result, we must use “Add derived plot > Add amplitude plot” and then “Add derived plot > Add threshold plot”. After that, we can start setting up the cursors so that they match with each pulse of signal power. After that, we need to increase the “Power max” and “Power min” sliders until we see clear pulses in the threshold plot. After tweaking the parameters, we will get this:
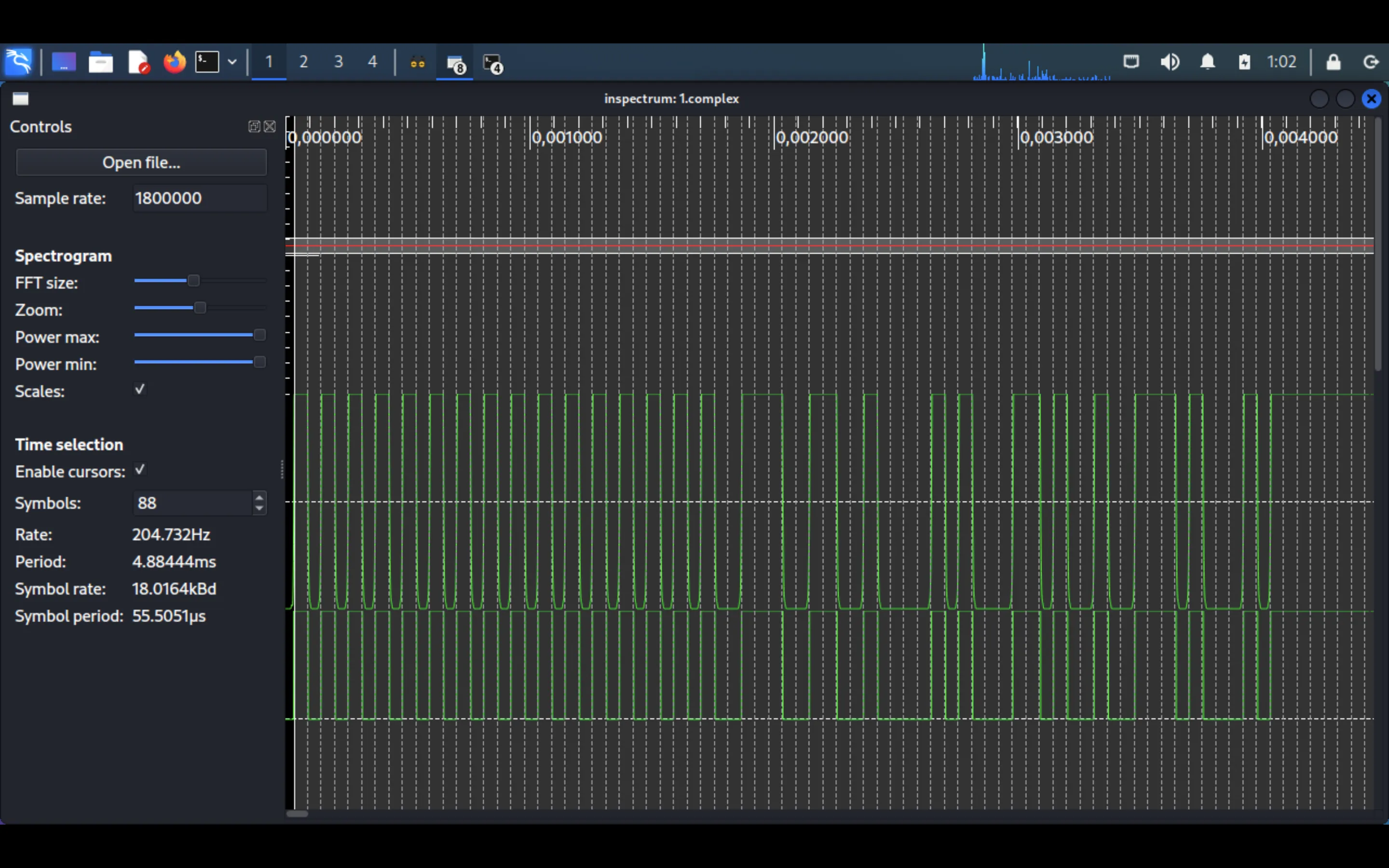
At this point, we can use “Extract symbols” to get the signal pulses encoded as bits. Once we hae this, we can transform bits to hexadecimal format with a Python / Bash one-liner:
$ function decode() { python3 -c "print(hex(int(''.join('$1'.split(', ')), 2)))" }
$ decode '1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 0, 1, 1, 0, 0, 1, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 0, 0, 0, 1, 0, 0, '
0xaaaaaaaa73214693a2ff84
If we repeat the process for the rest of the samples, we get these results:
$ decode '1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 0, 1, 1, 0, 0, 1, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 0, 0, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 0, 0, 1, 0, 1, 0, 0, '
0xaaaaaaaa73214693a1ff14
$ decode '1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 0, 1, 1, 0, 0, 1, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 0, 0, 1, 1, 1, 0, 1, 1, 0, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 0, 0, 1, 0, 0, 1, 0, 0, '
0xaaaaaaaa73214693b2ff24
$ decode '1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 0, 1, 1, 0, 0, 1, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 0, 0, 1, 1, 1, 0, 1, 1, 0, 0, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, '
0xaaaaaaaa73214693b1ff57
Reverse engineering
As can be seen, the signals are composed of three parts:
aaaaaaaa73214693a2ff84/a1ff14/b2ff24/b1ff57
The sizes match with the placeholders on the website text boxes. It looks like we only need to change the third part in order to get the flag, since the first two chunks are always the same.
Plus, it seems that the middle ff of the third part is fix, so we only need to apply brute force on two bytes (65536 possibilities).
Finding the correct combination
Let’s use ffuf to apply brute force. But first, let’s create our hexadecimal dictionary:
$ for i in {0..9} {a..f}; do for j in {0..9} {a..f}; do echo $i$j; done; done > hex
Now we can use ffuf (there is more than one valid combination):
$ ffuf -w hex:XX -w hex:YY -u http://144.126.206.23:30423/transmit -d 'pa=aaaaaaaa&sw=73214693&pl=XXffYY' -H 'Content-Type: application/x-www-form-urlencoded' -fs 2831
[Status: 200, Size: 2896, Words: 420, Lines: 134, Duration: 69ms]
* XX: 00
* YY: f9
[Status: 200, Size: 2896, Words: 420, Lines: 134, Duration: 72ms]
* XX: 01
* YY: f9
...
Flag
So we can use one of these codes to get the flag:
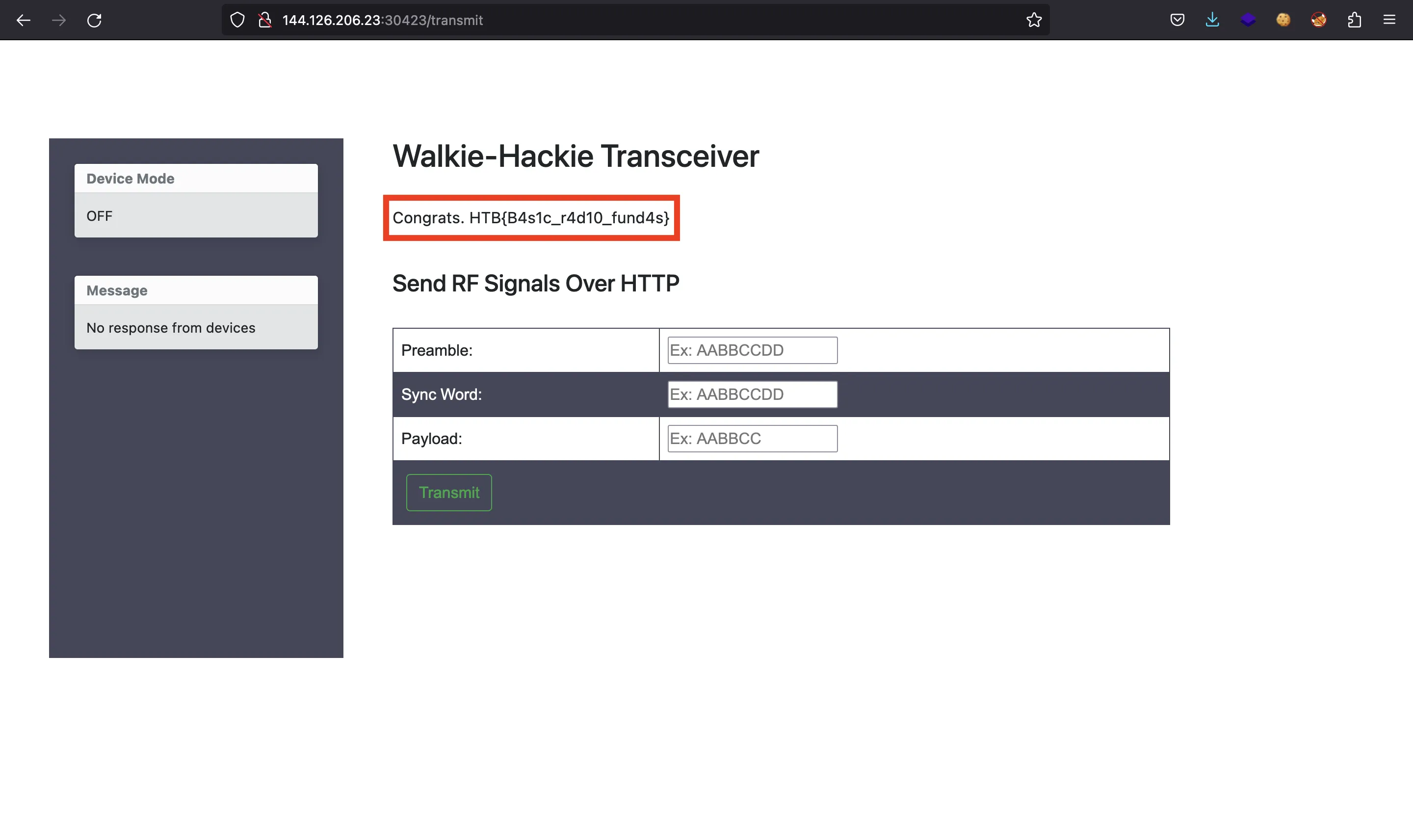
$ curl 144.126.206.23:30423/transmit -d 'pa=aaaaaaaa&sw=73214693&pl=00fff9' -s | grep -oE 'HTB{.*?}'
HTB{B4s1c_r4d10_fund4s}