Watch Tower
2 minutes to read
We are told that someone has been collecting and altering information in the network. Plus, we are given a file called tower_logs.pcapng.
Network traffic analysis
If we open the PCAP file in Wireshark, we will see a lot of Modbus packets:
Modbus
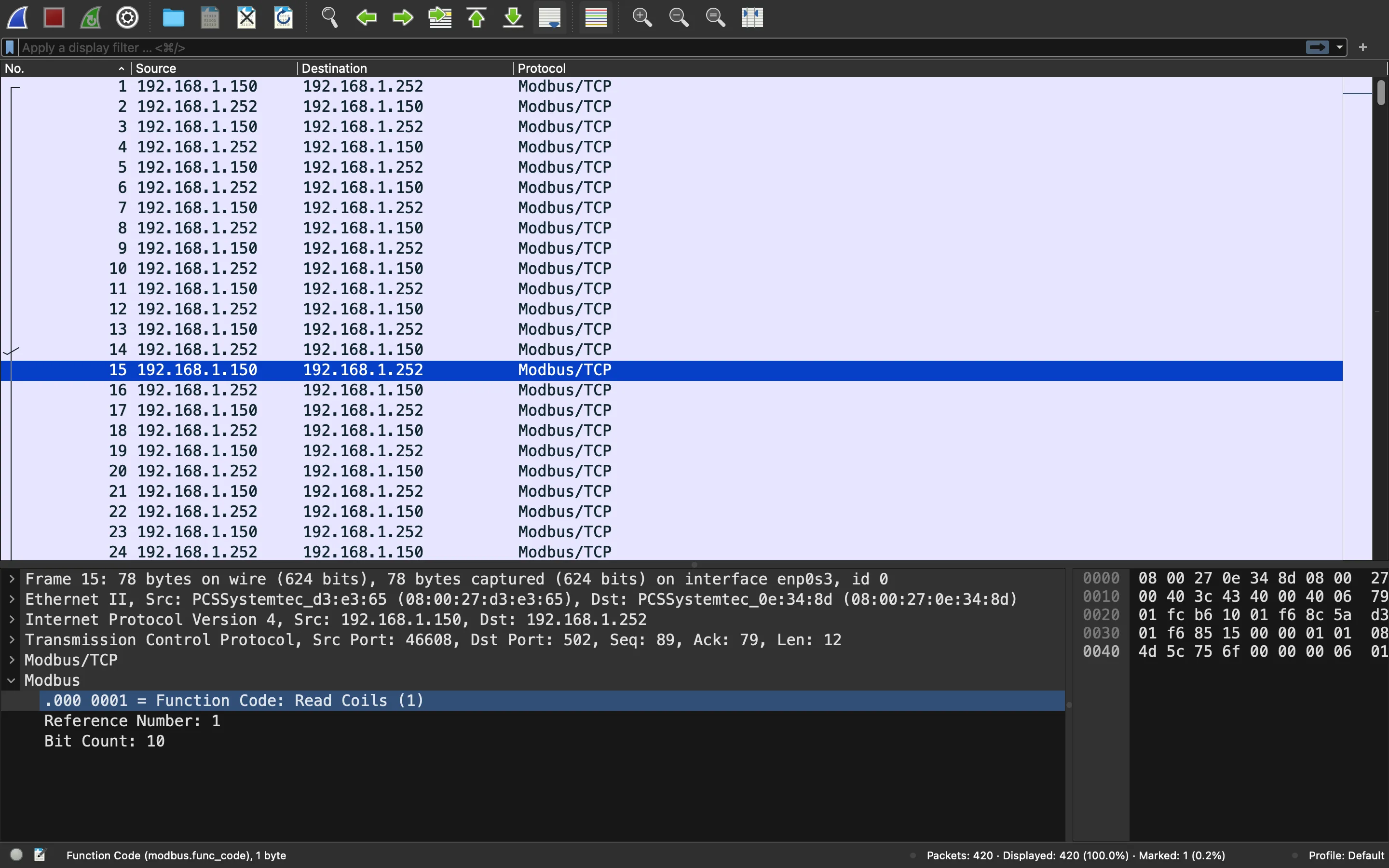
One thing to notice is the function code. There are three function codes involved in this trace (more information in Wikipedia):
Write Multiple CoilsRead CoilWrite Multiple Registers
The one that looks relevant is Write Multiple Registers because there are only 2 packets with Write Multiple Coils and Read Coil packets do not seem to hold any data. Indeed, all Write Multiple Registers packets are together (we can use “Apply as Column”):
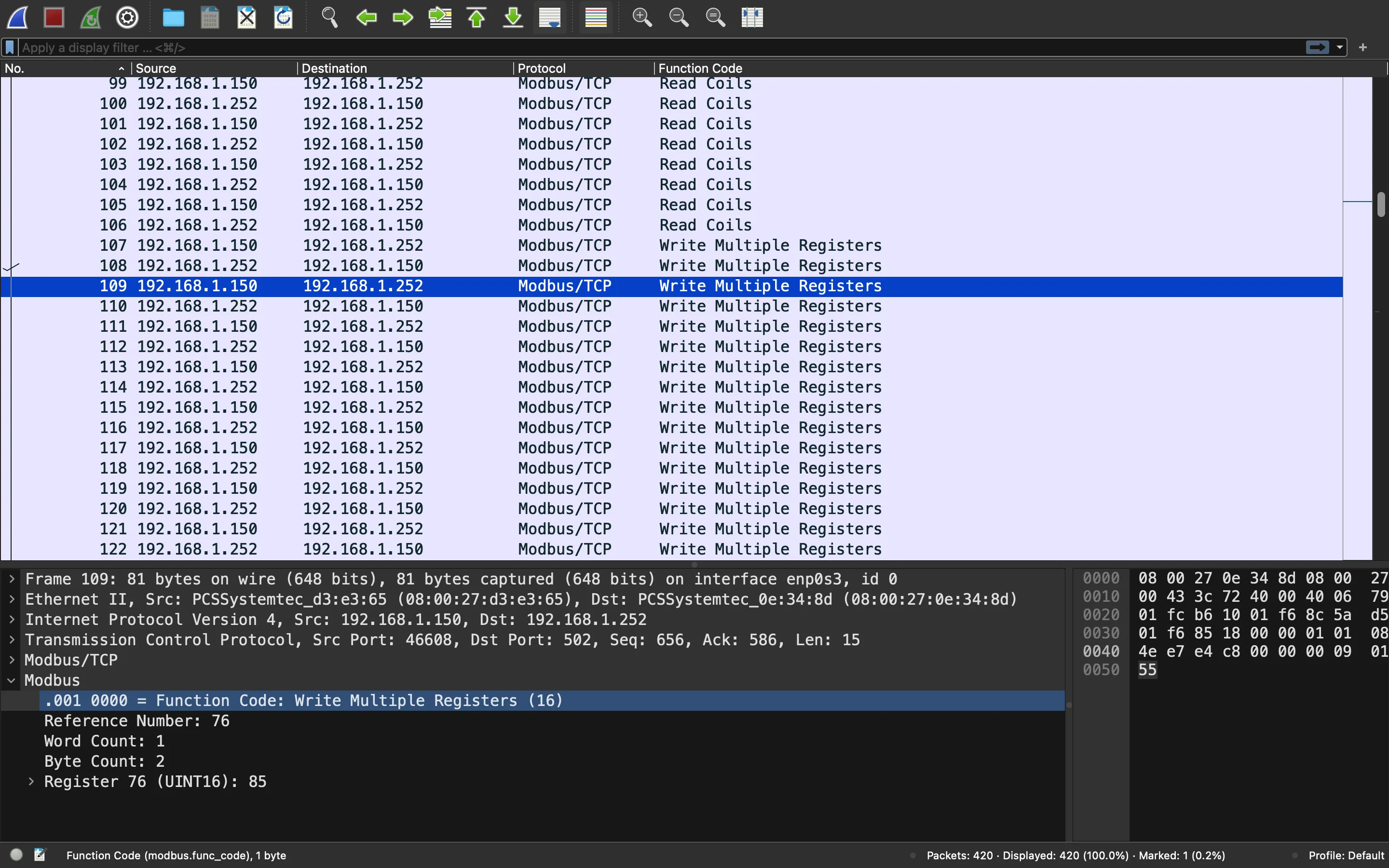
Decoding information
Now, we can notice that the Reference Number holds some special numbers:
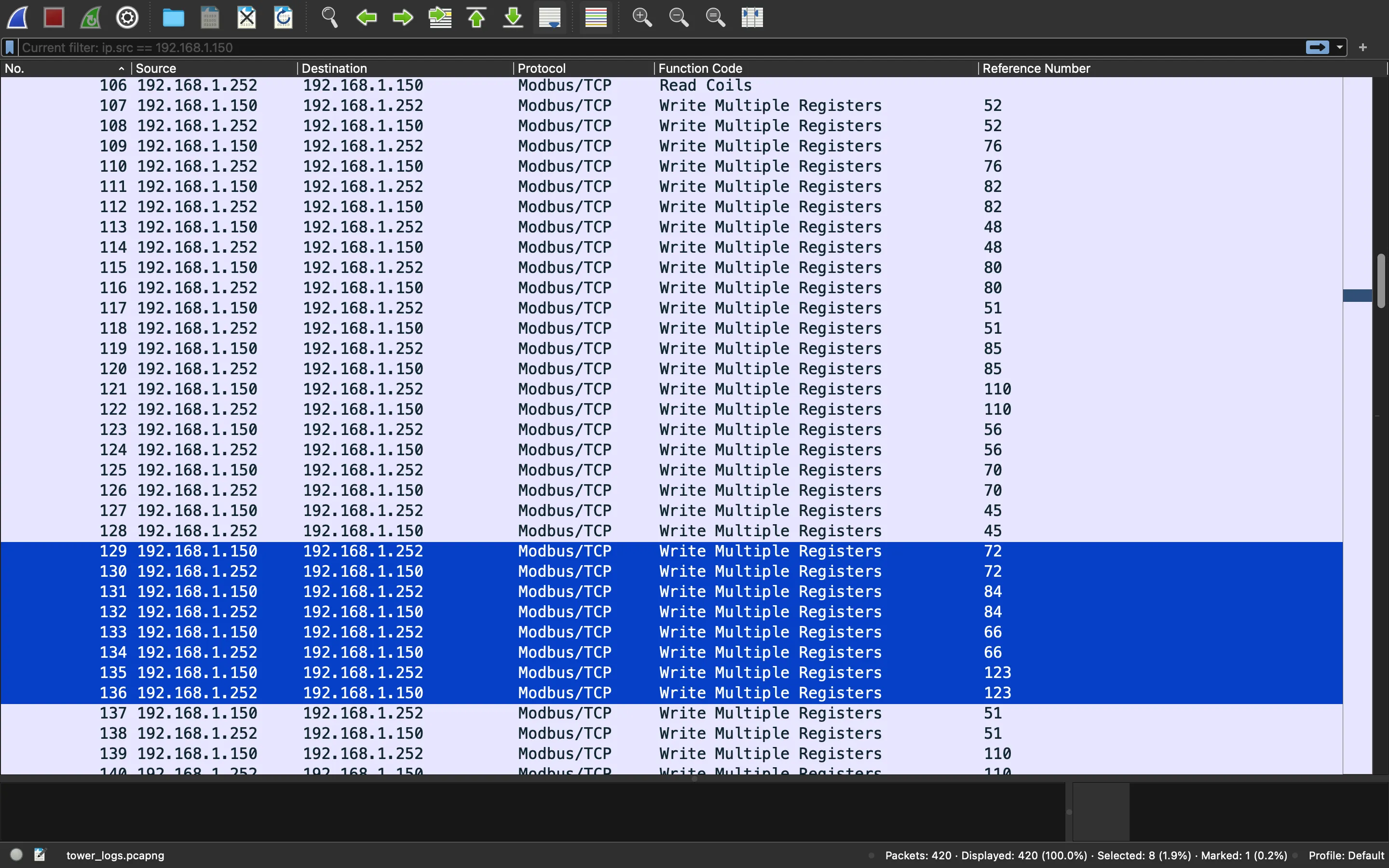
In fact, 72, 84, 66, 123 are the ASCII decimal codes for HTB{, so we have found the flag!
Flag
At this point, we can use tshark and some shell scripting techniques to capture the flag:
$ tshark -r tower_logs.pcapng -Tfields -Y 'ip.src == 192.168.1.150 and modbus.func_code == 16' -e 'modbus.reference_num' | xargs | tr ' ' ,
52,76,82,48,80,51,85,110,56,70,45,72,84,66,123,51,110,99,50,121,112,55,49,48,110,63,95,110,51,118,51,50,95,104,51,52,50,100,95,48,102,95,55,104,52,55,33,64,94,125,45,114,54,90,74,97,48
$ python3 -c "print(bytes([$(tshark -r tower_logs.pcapng -Tfields -Y 'ip.src == 192.168.1.150 and modbus.func_code == 16' -e 'modbus.reference_num' | xargs | tr ' ' ,)]))"
b'4LR0P3Un8F-HTB{3nc2yp710n?_n3v32_h342d_0f_7h47!@^}-r6ZJa0'
$ python3 -c "print(bytes([$(tshark -r tower_logs.pcapng -Tfields -Y 'ip.src == 192.168.1.150 and modbus.func_code == 16' -e 'modbus.reference_num' | xargs | tr ' ' ,)]))" | grep -oE 'HTB{.*?}'
HTB{3nc2yp710n?_n3v32_h342d_0f_7h47!@^}