0ld is g0ld
1 minute to read
We are given a PDF file called 0ld is g0ld.pdf, but it is protected with a password.
In order to obtain the password, we can use pdf2john to extract a hash and pass it to john to perform a dictionary attack using rockyou.txt:
$ pdf2john 0ld\ is\ g0ld.pdf | tee hash
0ld is g0ld.pdf:$pdf$4*4*128*-1060*1*16*5c8f37d2a45eb64e9dbbf71ca3e86861*32*9cba5cfb1c536f1384bba7458aae3f8100000000000000000000000000000000*32*702cc7ced92b595274b7918dcb6dc74bedef6ef851b4b4b5b8c88732ba4dac0c
$ john --wordlist=$WORDLISTS/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (PDF [MD5 SHA2 RC4/AES 32/64])
Cost 1 (revision) is 4 for all loaded hashes
Press 'q' or Ctrl-C to abort, almost any other key for status
jumanji69 (0ld is g0ld.pdf)
1g 0:00:01:28 DONE 0.01126g/s 76825p/s 76825c/s 76825C/s jumapi..jumanee
Use the "--show --format=PDF" options to display all of the cracked passwords reliably
Session completed.
So we got the password (jumanji69). If we open now the PDF file, we will see a portrait for Samuel Morse:

And if we zoom a bit, we will see a stream of . and - (that’s Morse code):
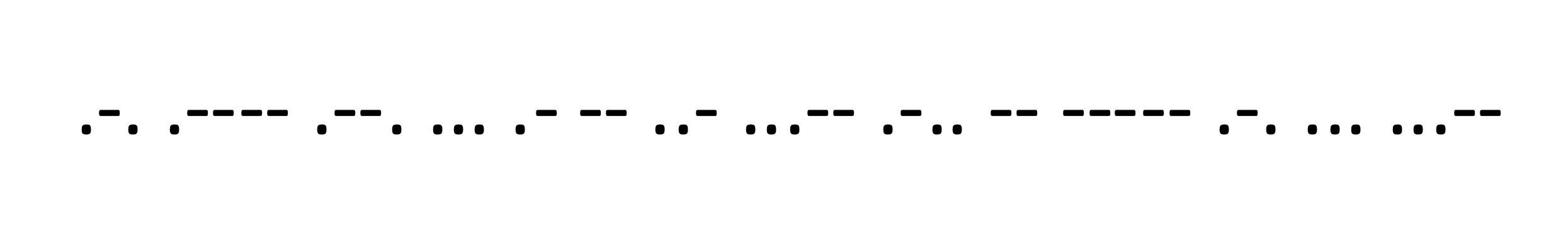
We can take this string and decode it:
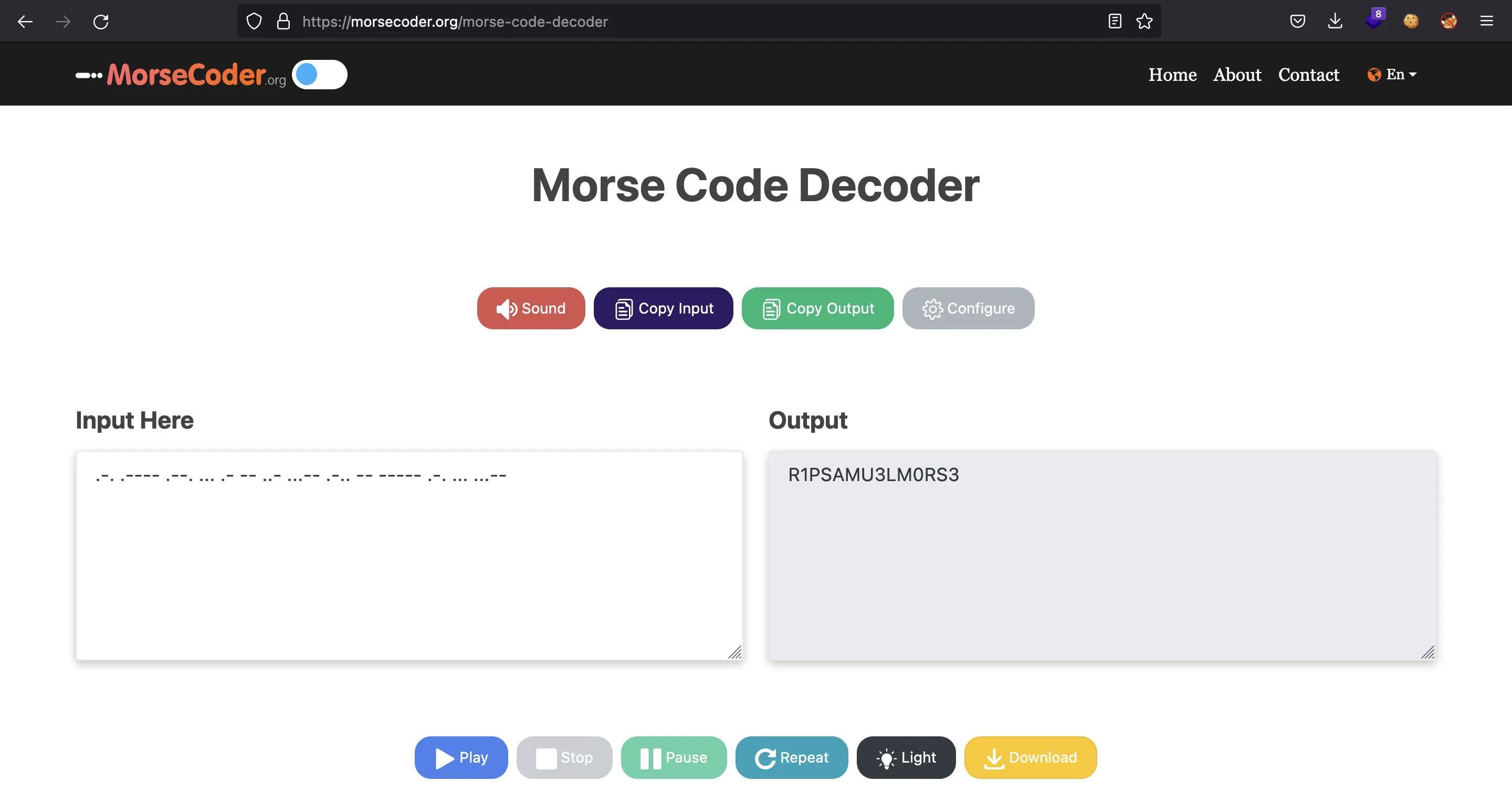
So the flag is: HTB{R1PSAMU3LM0RS3}.