Canvas
1 minute to read
We are given these files:
$ tree
.
├── css
│ └── style.css
├── dashboard.html
├── index.html
└── js
└── login.js
3 directories, 4 files
Analyzing the web
Since they are HTML, CSS and JavaScript files, let’s start an HTTP server and load the files in the browser:
$ python3 -m http.server 80
Serving HTTP on :: port 80 (http://[::]:80/) ...
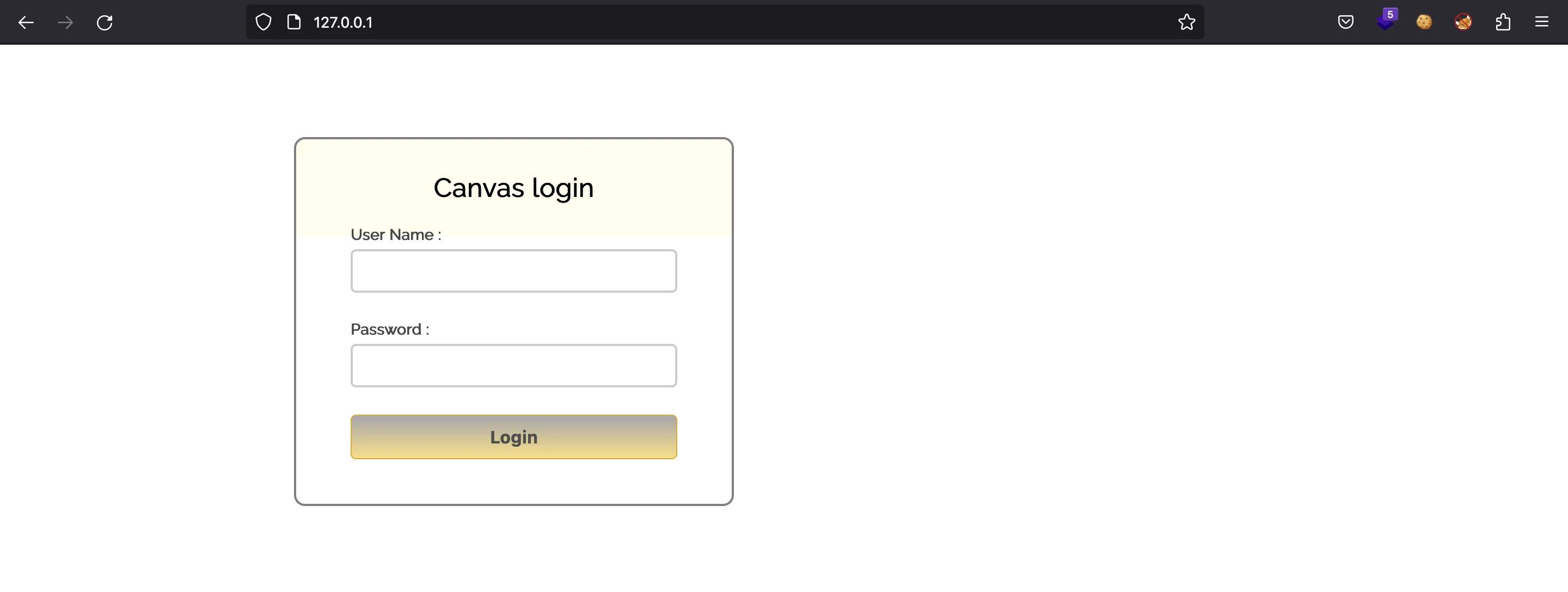
There is a login form, but the form tag does a POST request to the same URL. Since there is no remote HTTP server, this login form is useless:
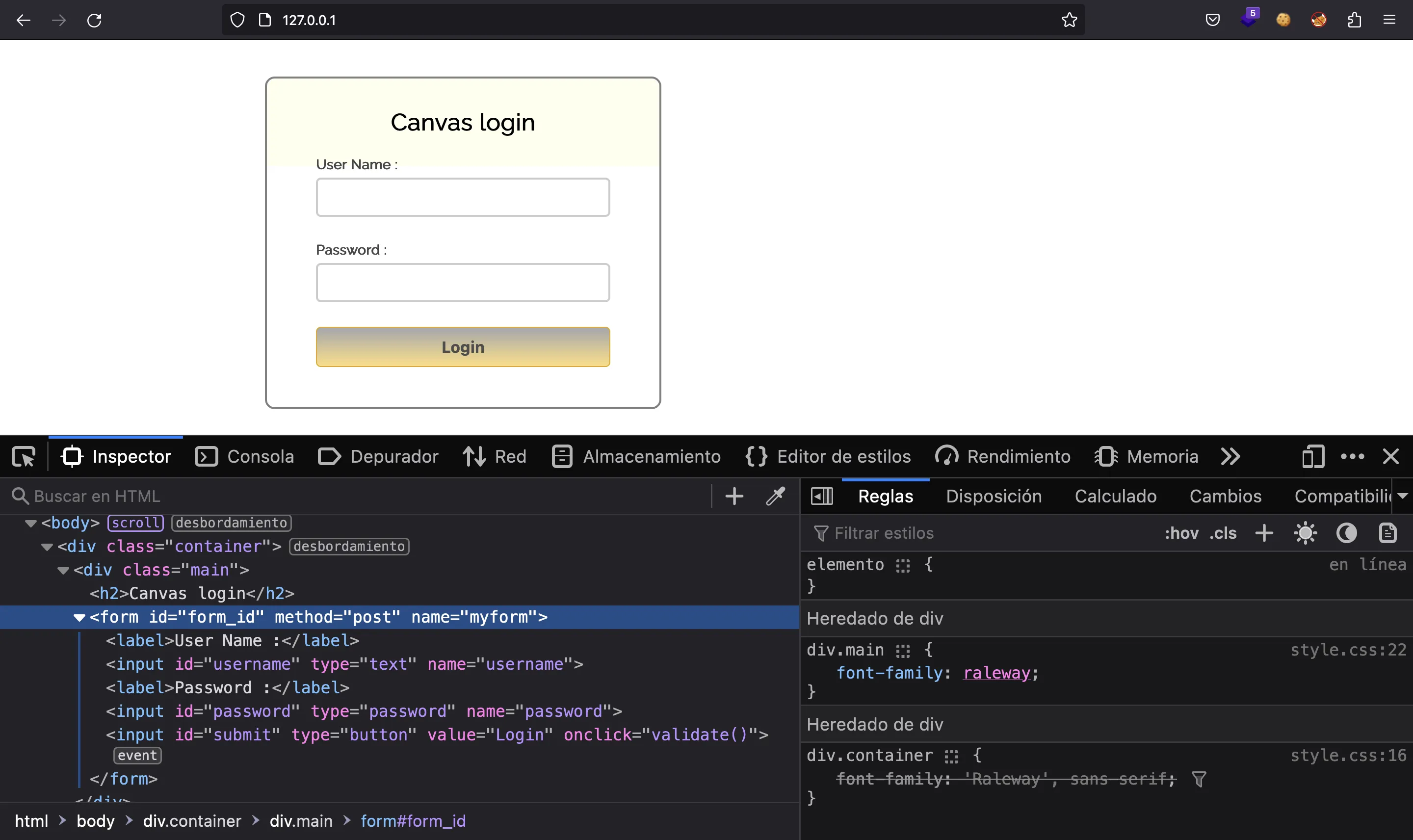
Analyzing JavaScript files
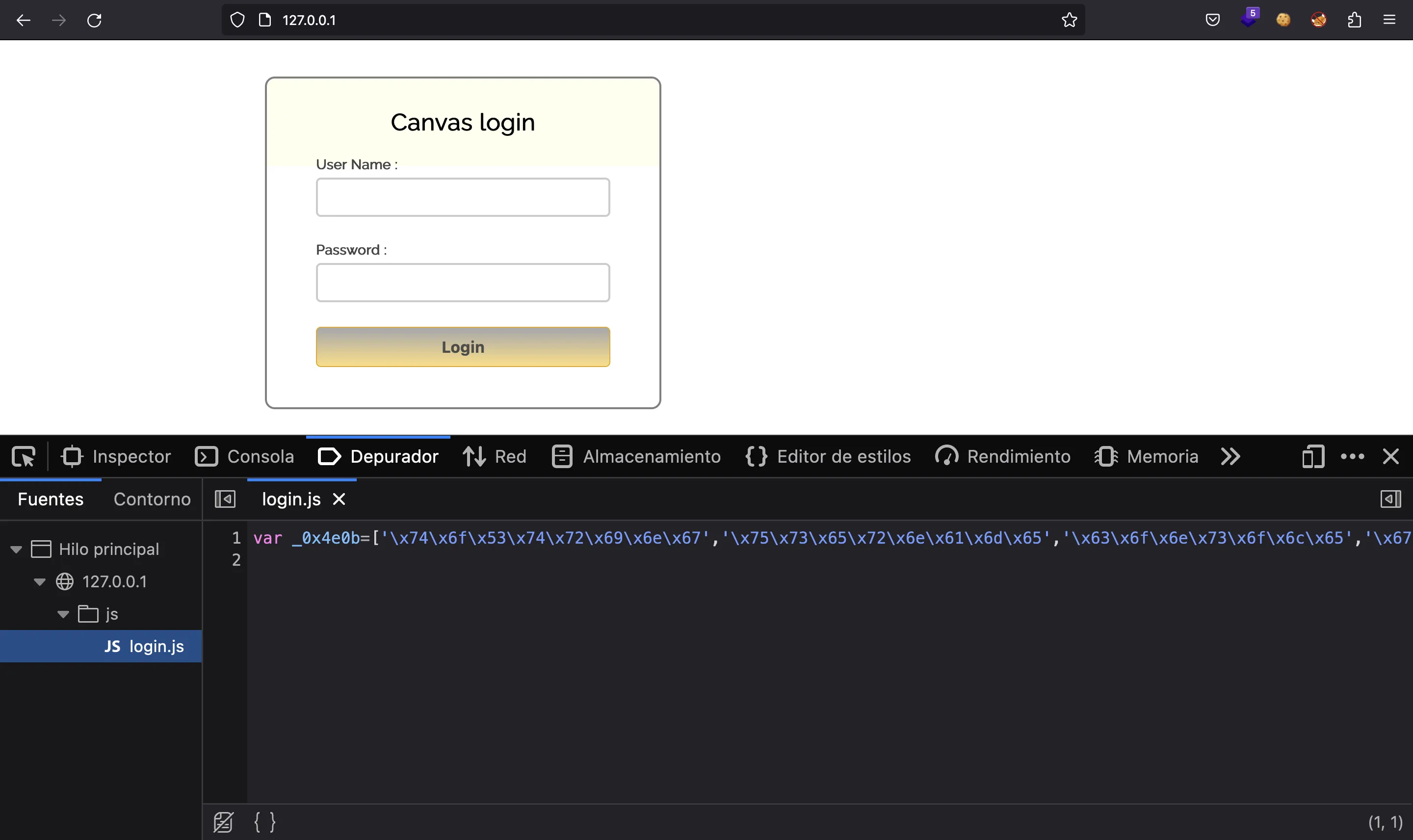
Let’s take a look at js/login.js. It looks obfuscated:
We can format the code in the browser and see that there is a strange variable at the very end:
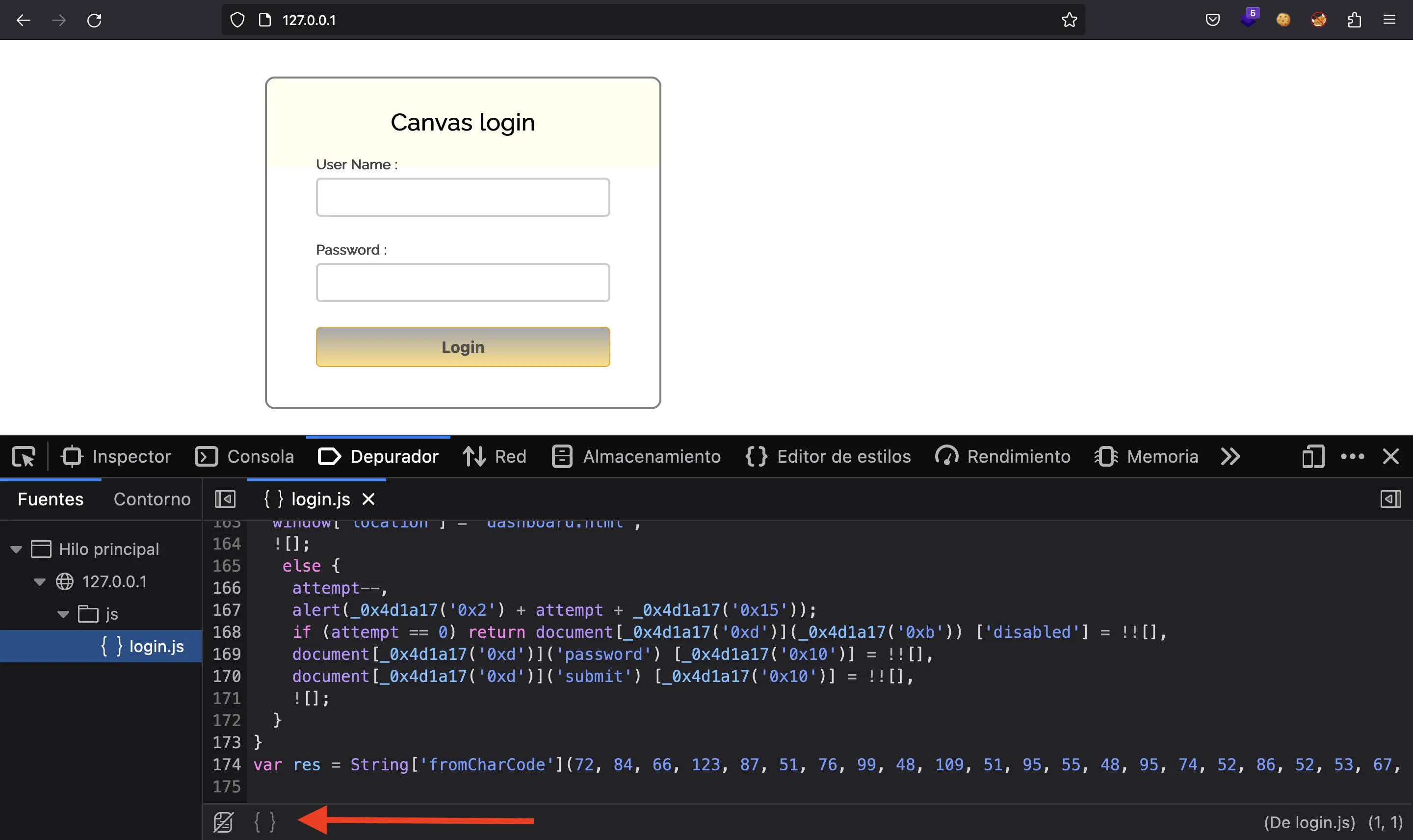
Flag
In fact, it is loaded in memory, so we can switch to the JavaScript console and print its value, which is the flag, surprisingly:
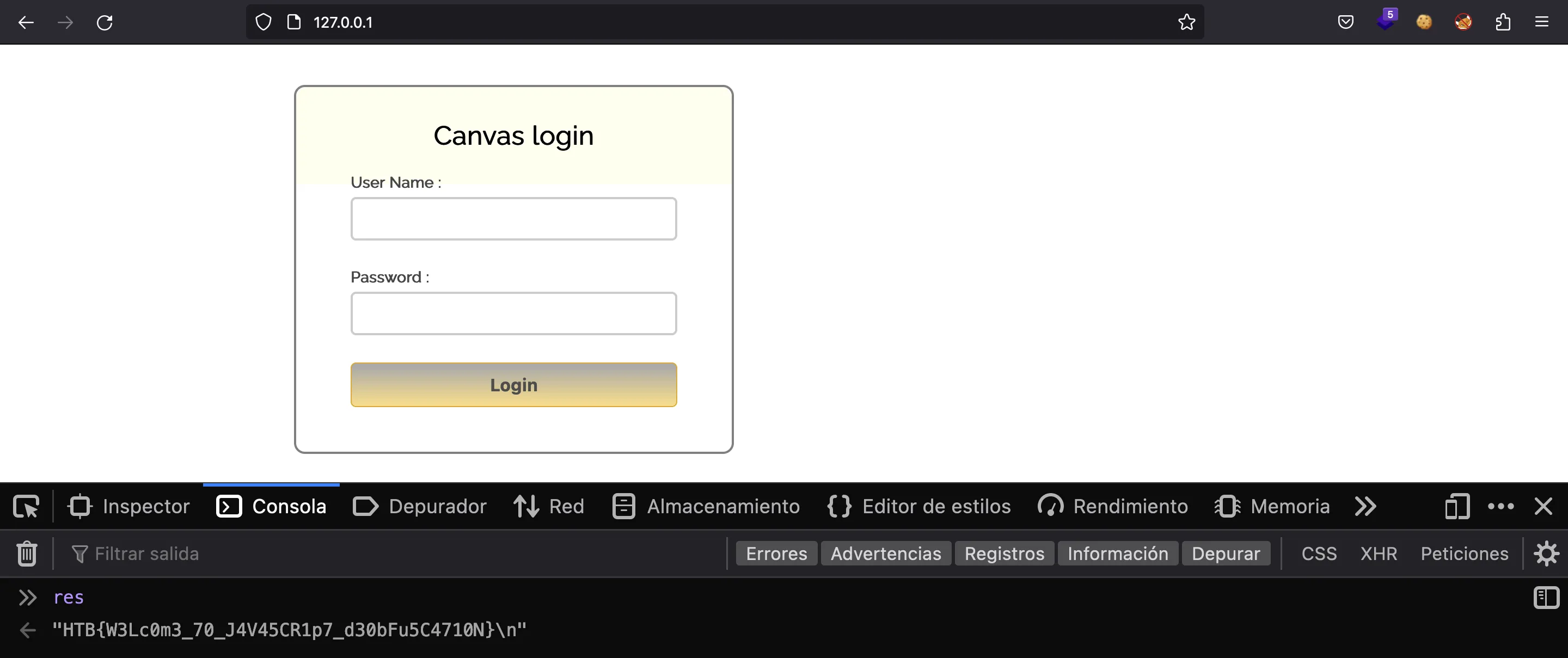
HTB{W3Lc0m3_70_J4V45CR1p7_d30bFu5C4710N}