Da Vinci
3 minutes to read
We are given three JPEG images:
monalisa.jpg:

Plans.jpg:
Thepassword_is_the_small_name_of_the_actor_named_Hanks.jpg:

$ file monalisa.jpg
monalisa.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 300x300, segment length 16, comment: "CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 92", comment: "Optimized by JPEGmini 3.9.20.0L Internal 0x8c97c7da", baseline, precision 8, 1280x1936, components 3
$ file Plans.jpg
Plans.jpg: JPEG image data, JFIF standard 1.02, aspect ratio, density 100x100, segment length 16, baseline, precision 8, 800x600, components 3
$ file Thepassword_is_the_small_name_of_the_actor_named_Hanks.jpg
Thepassword_is_the_small_name_of_the_actor_named_Hanks.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 1x1, segment length 16, baseline, precision 8, 376x490, components 3
Since they are a JPEG images, we can think of steganography using steghide. Actually, this method works for the third image (Thepassword_is_the_small_name_of_the_actor_named_Hanks.jpg) using TOM as password:
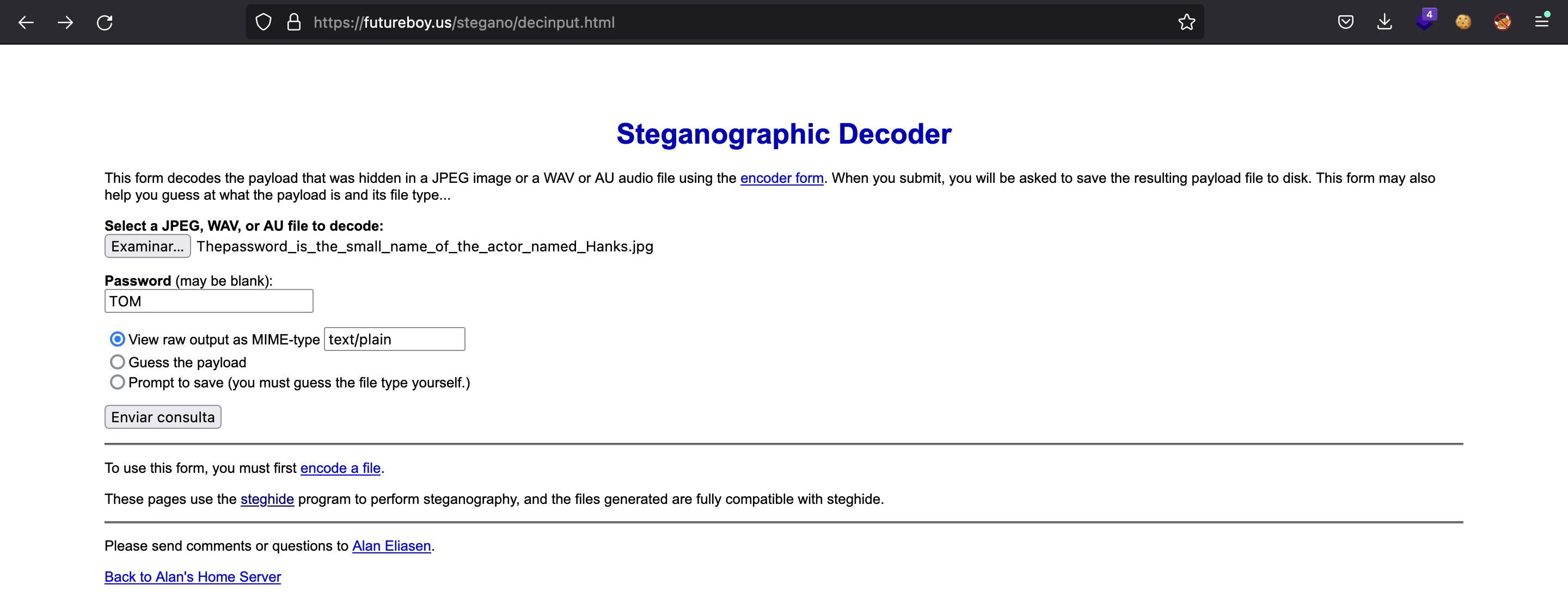
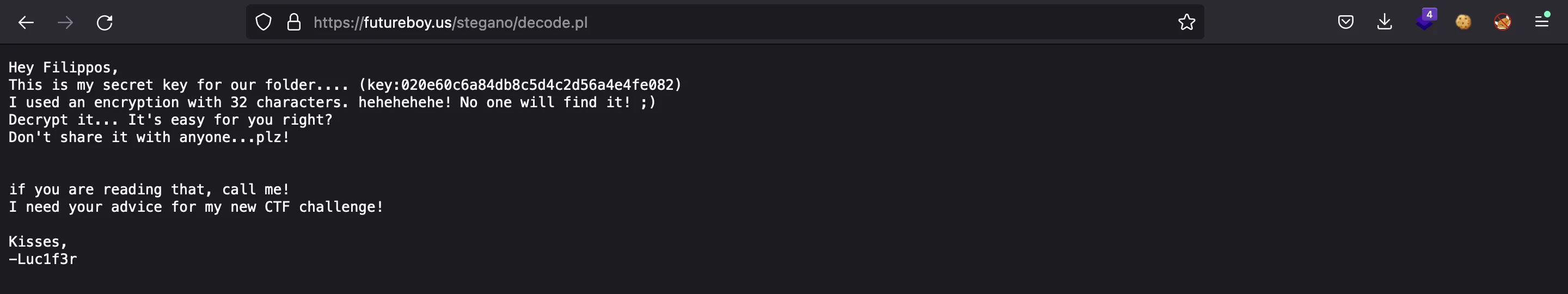
We obtain a text with a key 020e60c6a84db8c5d4c2d56a4e4fe082. This looks like an MD5 hash, so let’s put it in crackstation.net:
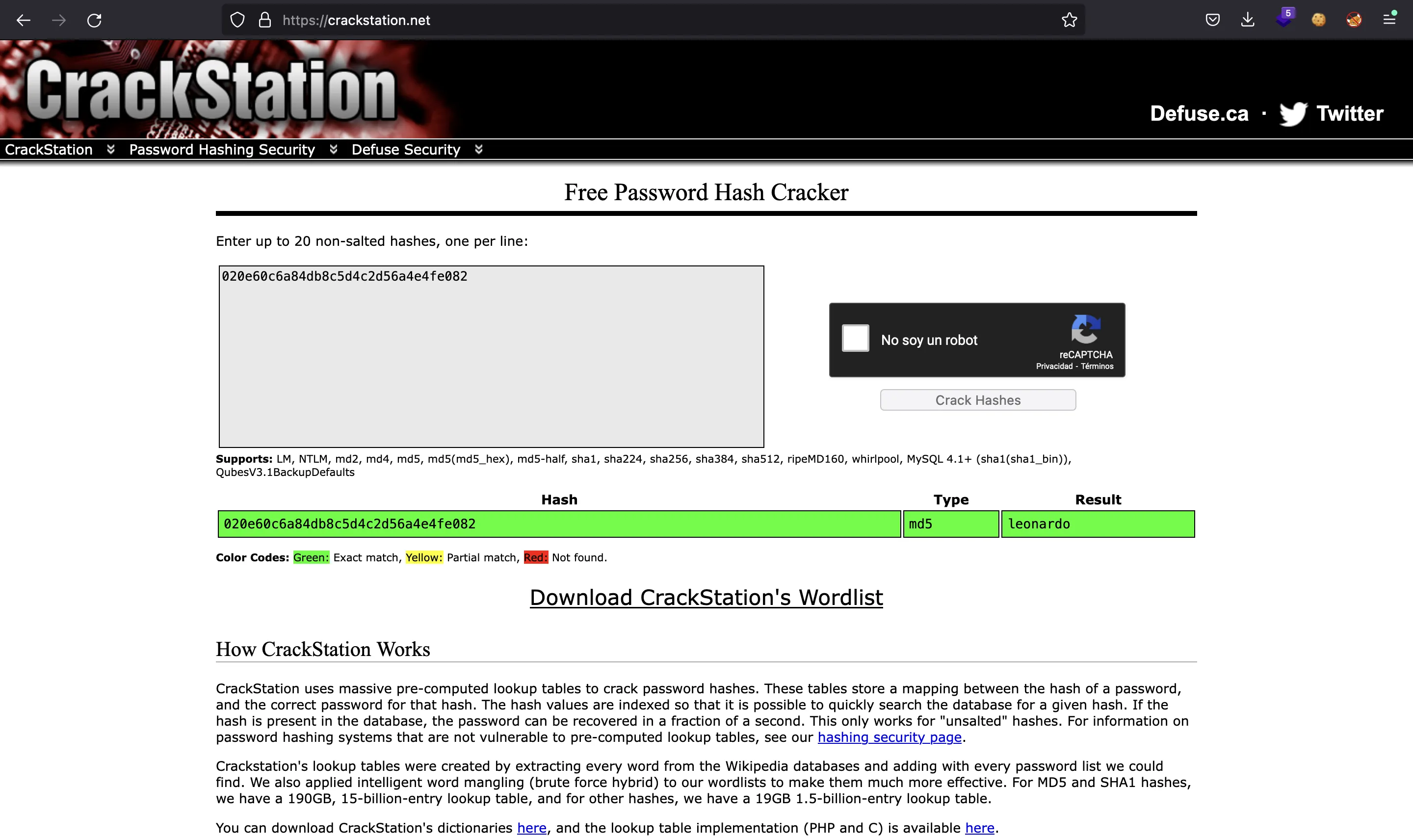
Now we have a password (leonardo). If we check the printable strings of monalisa.jpg we will see famous.zip at the bottom:
$ strings -10 monalisa.jpg
;CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 92
5Optimized by JPEGmini 3.9.20.0L Internal 0x8c97c7da
/2.)2&*+)
))))))))))))))))))))))))))))))))))))))))))))))))))
#BQaRbq$3r
EK:p%q%FvR\e
d'v[{EmXx1
zGToLjg?'}
T\c!`.w0x-B ].
dk*bbJB[>X[e
O:V=v,Tee3n-7Y
EbqL%g>@Dq$
$A4bIqxctS
8V7:3k/1-0
`SDLKS.etQ
_4s{K6!:dW
&bXfPKAt-?
hwUuAX)WX[
z#iWV(mO)~PL
c<[;pg],s{p
NbfVh1Y~v":>
vcqlh+tSk(
jBWBuFz:V2
k^*kTJ$2LT^BC
hQd.!%lJE4
6Yw6L<7(^]i
T::Ks\"c'e8
?AE%T*"+OD
Q5N1W-)X@X
_JR%<U$ Kx
famous.zipUT
Mona.jpgUT
%=S!dS2GA)
NhY`&<kwl3
ia
\2nA{D9x
FayU)W^[Ja=
6$}%U.cU(s
Mona.jpgUT
famous.zipUT
So we can guess that the image file has an embedded ZIP file. We can verify it and extract it using binwalk:
$ binwalk monalisa.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
450363 0x6DF3B Zip archive data, at least v2.0 to extract, uncompressed size: 117958, name: famous.zip
450440 0x6DF88 Zip archive data, encrypted at least v2.0 to extract, compressed size: 117776, uncompressed size: 122869, name: Mona.jpg
568411 0x8AC5B End of Zip archive, footer length: 22
568537 0x8ACD9 End of Zip archive, footer length: 22
$ binwalk -e monalisa.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
450363 0x6DF3B Zip archive data, at least v2.0 to extract, uncompressed size: 117958, name: famous.zip
450440 0x6DF88 Zip archive data, encrypted at least v2.0 to extract, compressed size: 117776, uncompressed size: 122869, name: Mona.jpg
568411 0x8AC5B End of Zip archive, footer length: 22
568537 0x8ACD9 End of Zip archive, footer length: 22
$ ls _monalisa.jpg.extracted/
6DF3B.zip famous.zip
And we have a ZIP file that contains another JPEG image called Mona.jpg:
$ file _monalisa.jpg.extracted/famous.zip
_monalisa.jpg.extracted/famous.zip: Zip archive data, at least v2.0 to extract
$ unzip -l _monalisa.jpg.extracted/famous.zip
Archive: _monalisa.jpg.extracted/famous.zip
Length Date Time Name
--------- ---------- ----- ----
122869 2017-09-22 20:57 Mona.jpg
--------- -------
122869 1 file
The ZIP file is encrypted, but we have the password (leonardo):
$ unzip -P leonardo _monalisa.jpg.extracted/famous.zip
Archive: _monalisa.jpg.extracted/famous.zip
inflating: Mona.jpg
$ file Mona.jpg
Mona.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 612x612, components 3

Before analyzing this new image, we can take a look at Plans.jpg. We can find a URL in the printable strings of the file:
$ strings -10 Plans.jpg
//33//@@@@@@@@@@@@@@@
#0+.'''.+550055@@?@@@@@@@@@@@@
?:Vn.$R0!B@X2
rLXn0~uHg*T
zS?jh_{3&!
nI"L(oK'b4
zX^(1*cxY3:
(CDRYFLD8,
RN;m@.
VebJ
https://www.youtube.com/watch?v=jc1Nfx4c5LQ
This URL goes to a YouTube video called “Guernica 3D”, and talks about this famous Picasso painting.
Actually, we can use Guernica as the password for steghide in Mona.jpg:
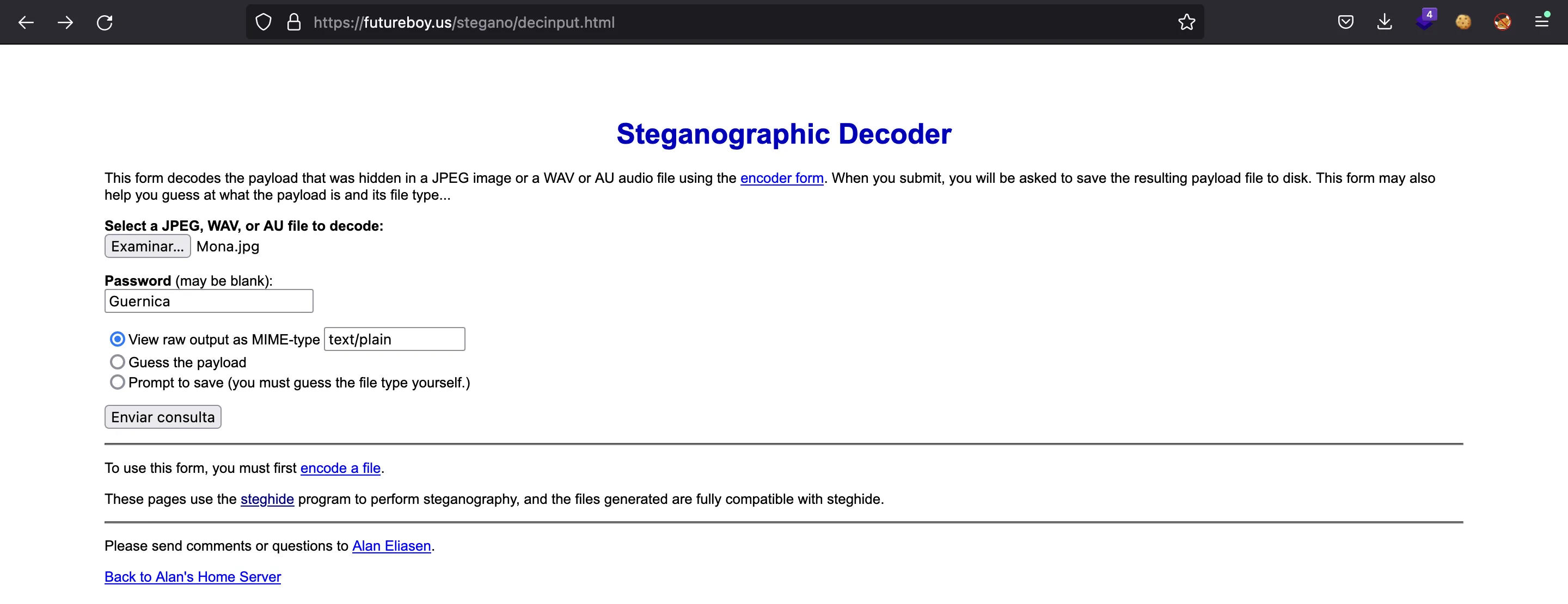
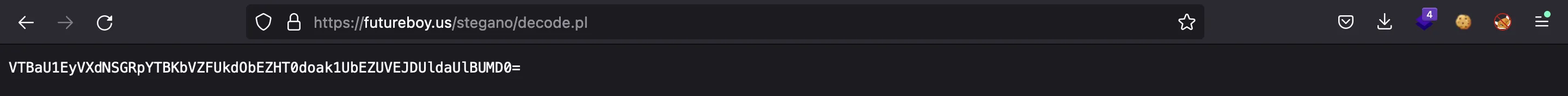
And we get a string that seems to be encoded in Base64 (actually, multiple times). And there’s the flag:
$ echo VTBaU1EyVXdNSGRpYTBKbVZFUkdObEZHT0doak1UbEZUVEJDUldaUlBUMD0= | base64 -d
U0ZSQ2UwMHdia0JmVERGNlFGOGhjMTlFTTBCRWZRPT0=
$ echo VTBaU1EyVXdNSGRpYTBKbVZFUkdObEZHT0doak1UbEZUVEJDUldaUlBUMD0= | base64 -d | base64 -d
SFRCe00wbkBfTDF6QF8hc19EM0BEfQ==
$ echo VTBaU1EyVXdNSGRpYTBKbVZFUkdObEZHT0doak1UbEZUVEJDUldaUlBUMD0= | base64 -d | base64 -d | base64 -d
HTB{M0n@_L1z@_!s_D3@D}