Hackerman
2 minutes to read
We are given a JPEG image called hackerman.jpg:
$ file hackerman.jpg
hackerman.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 960x540, components 3

Since it is a JPEG image, we can think of steganography using steghide. But it does not seem to work for the moment.
If we check the printable strings that are inside the image file, we will see a string that seems to be an MD5 hash (32 hexadecimal digits):
$ strings -20 hackerman.jpg | xxd
00000000: 0c0c 0c0c 0c0c 0c0c 0c0c 0c0c 0c0c 0c0c ................
00000010: 0c0c 0c0c 0c0c 0c0c 0c0c 0c0c 0a0c 0c0c ................
00000020: 0c0c 0c0c 0c0c 0c0c 0c0c 0c0c 0c0c 0c0c ................
00000030: 0c0c 0c0c 0c0c 0c0c 0c0a 2526 2728 292a ..........%&'()*
00000040: 3435 3637 3839 3a43 4445 4647 4849 4a53 456789:CDEFGHIJS
00000050: 5455 5657 5859 5a63 6465 6667 6869 6a73 TUVWXYZcdefghijs
00000060: 7475 7677 7879 7a0a 2627 2829 2a35 3637 tuvwxyz.&'()*567
00000070: 3839 3a43 4445 4647 4849 4a53 5455 5657 89:CDEFGHIJSTUVW
00000080: 5859 5a63 6465 6667 6869 6a73 7475 7677 XYZcdefghijstuvw
00000090: 7879 7a0a 3536 3334 3237 3564 3639 3466 xyz.5634275d694f
000000a0: 3836 3635 3935 3737 3436 6339 3631 3931 8665957746c96191
000000b0: 3332 6630 0a 32f0.
$ strings -20 hackerman.jpg | grep -v \\x0c
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
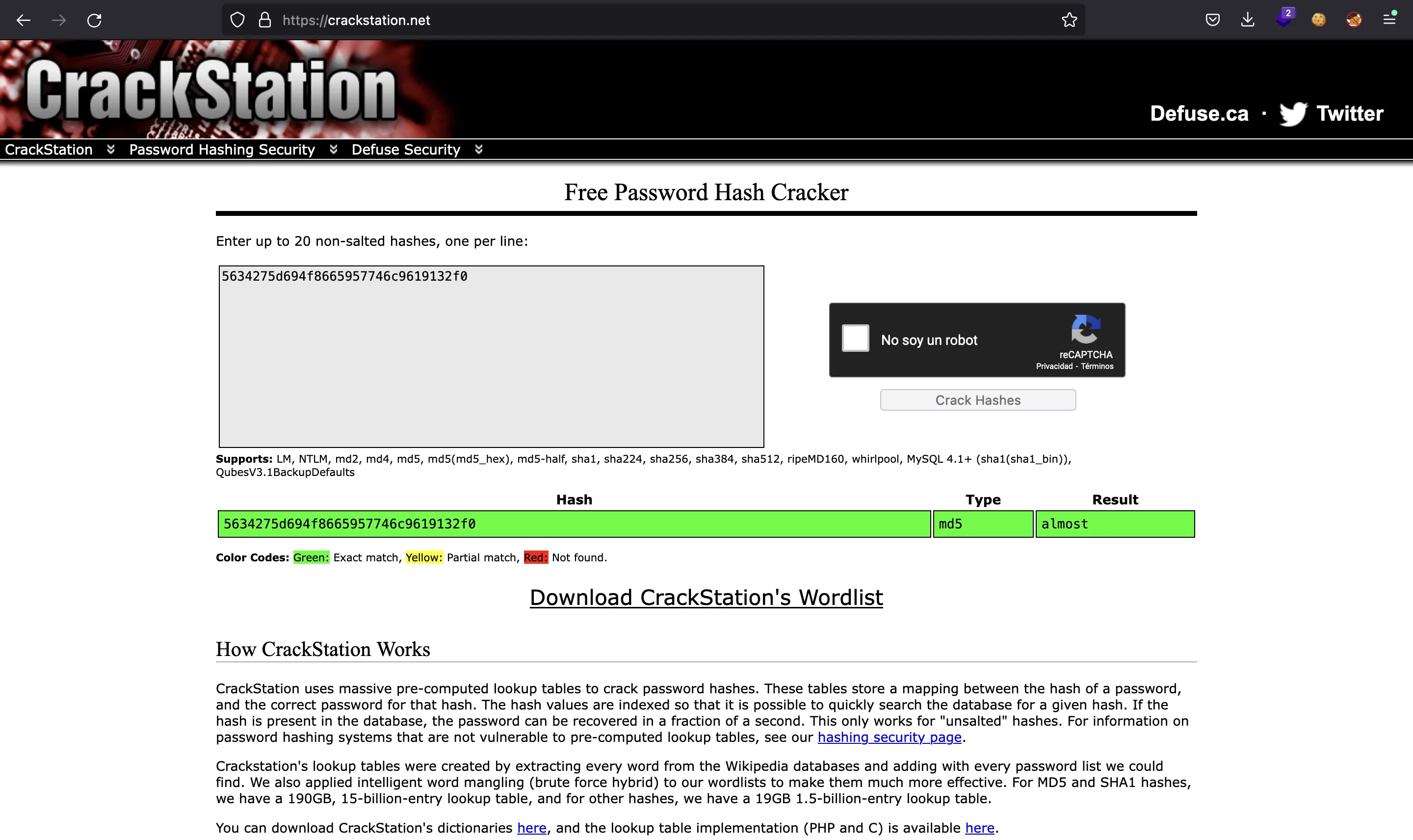
5634275d694f8665957746c9619132f0
$ echo -n 5634275d694f8665957746c9619132f0 | wc -c
32
If we put this hash in crackstation.net we will find that almost is the word whose MD5 hash is the one above.
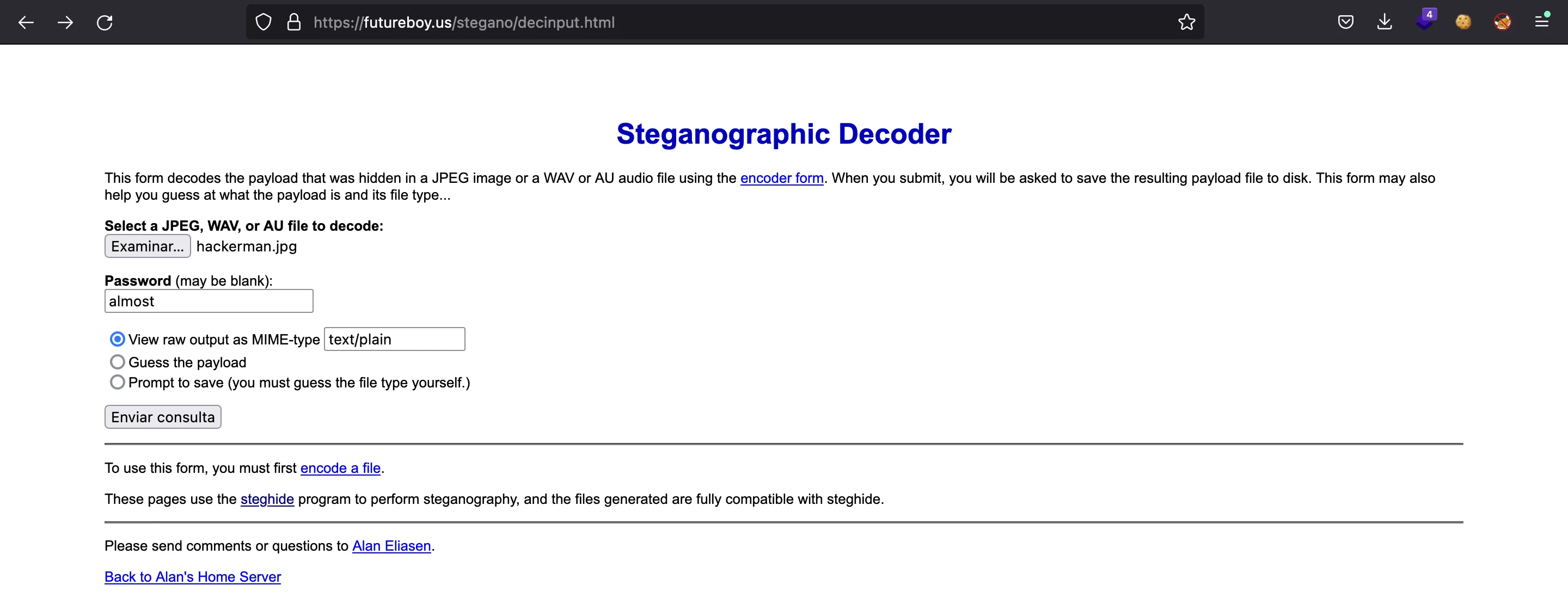
So we got can try almost as password for steghide:
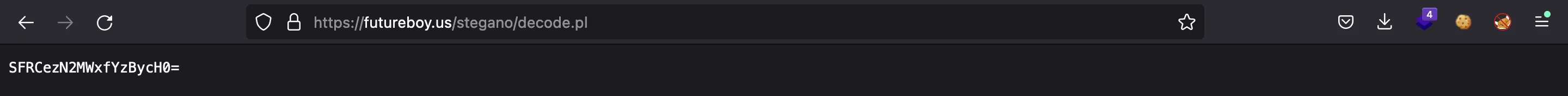
And we get a string that seems to be encoded in Base64. And there’s the flag:
$ echo SFRCezN2MWxfYzBycH0= | base64 -d
HTB{3v1l_c0rp}