Man In The Middle
2 minutes to read
We are given a file called mitm.log:
$ file mitm.log
mitm.log: BTSnoop version 1,
If we search for this type of file, we see that we can open it with Wireshark:
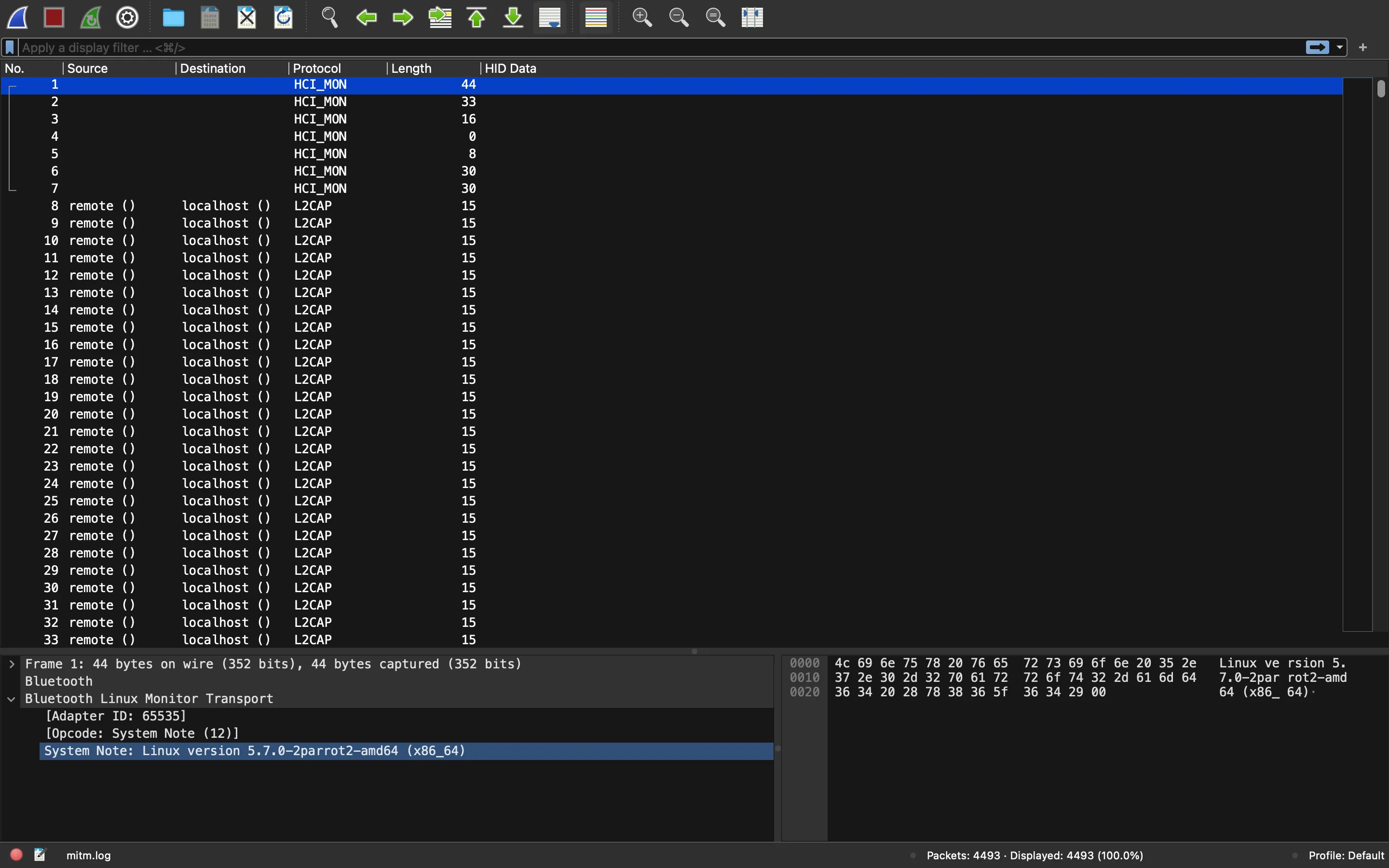
Identifying the device
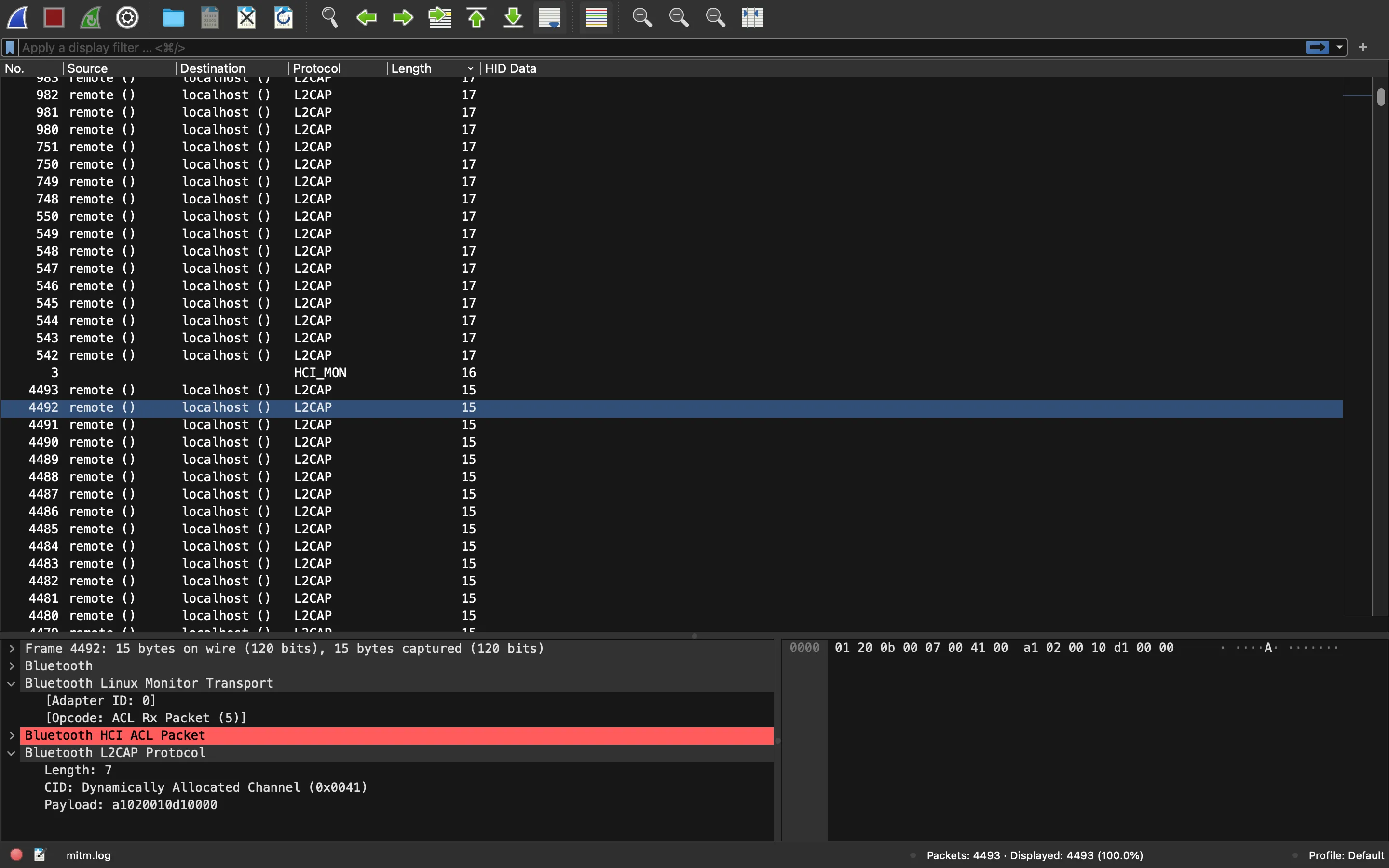
The third event shows that the USB device is a Bluetooth keyboard (LiteonTe):
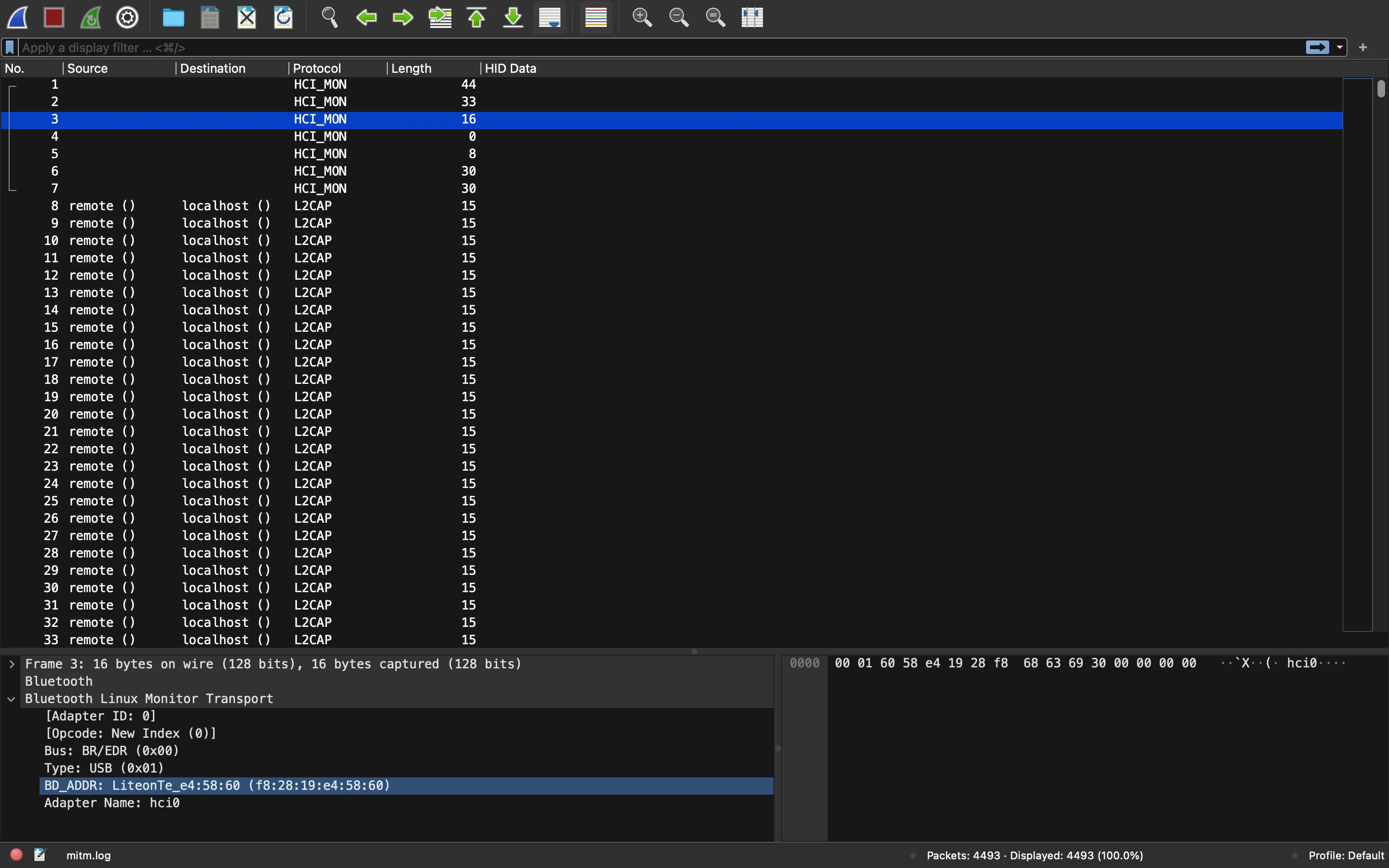
Therefore, we will need to analyze key strokes, like in Logger. Hardware devices use a protocol known as Human Interface Device (HID). More information can be found at Wikipedia. In fact, there is a documentation manual attached: ww.usb.org, where some HID tables are found (Section 10: “Keyboard/Keypad Page (0x07)”):
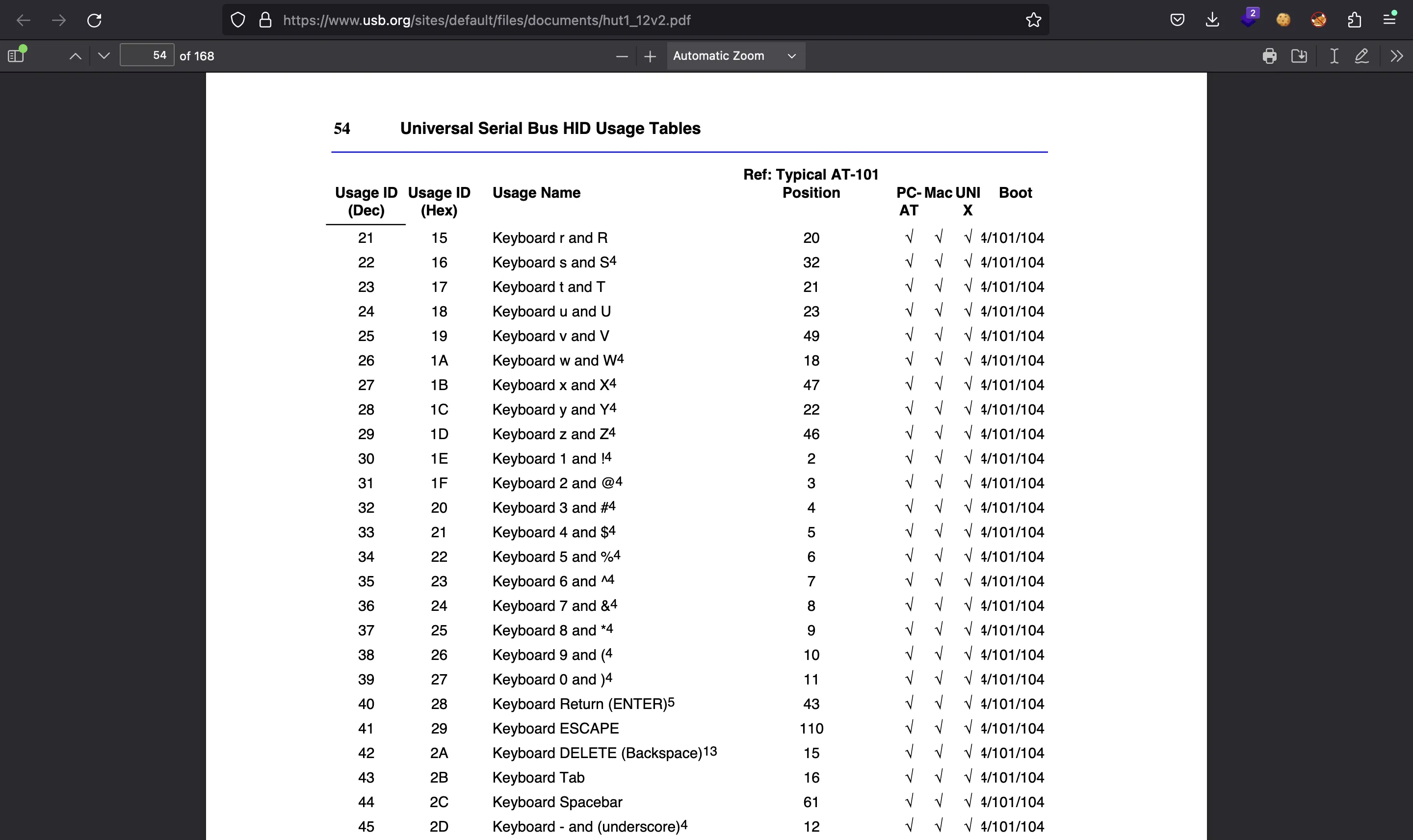
This table can also be found in this GitHub Gist.
Nevertheless, this time we are dealing with a Bluetooth keyboard, which uses L2CAP (more information at Wikipedia). This protocol contains the expected HID payloads.
Filtering events
Now we need to find out which events have the key-stroke information. It seems that packets with length 17 bytes are interesting (notice that the events are sorted by length and there are only a few with 17 as length, mind the scroll bar at the right):
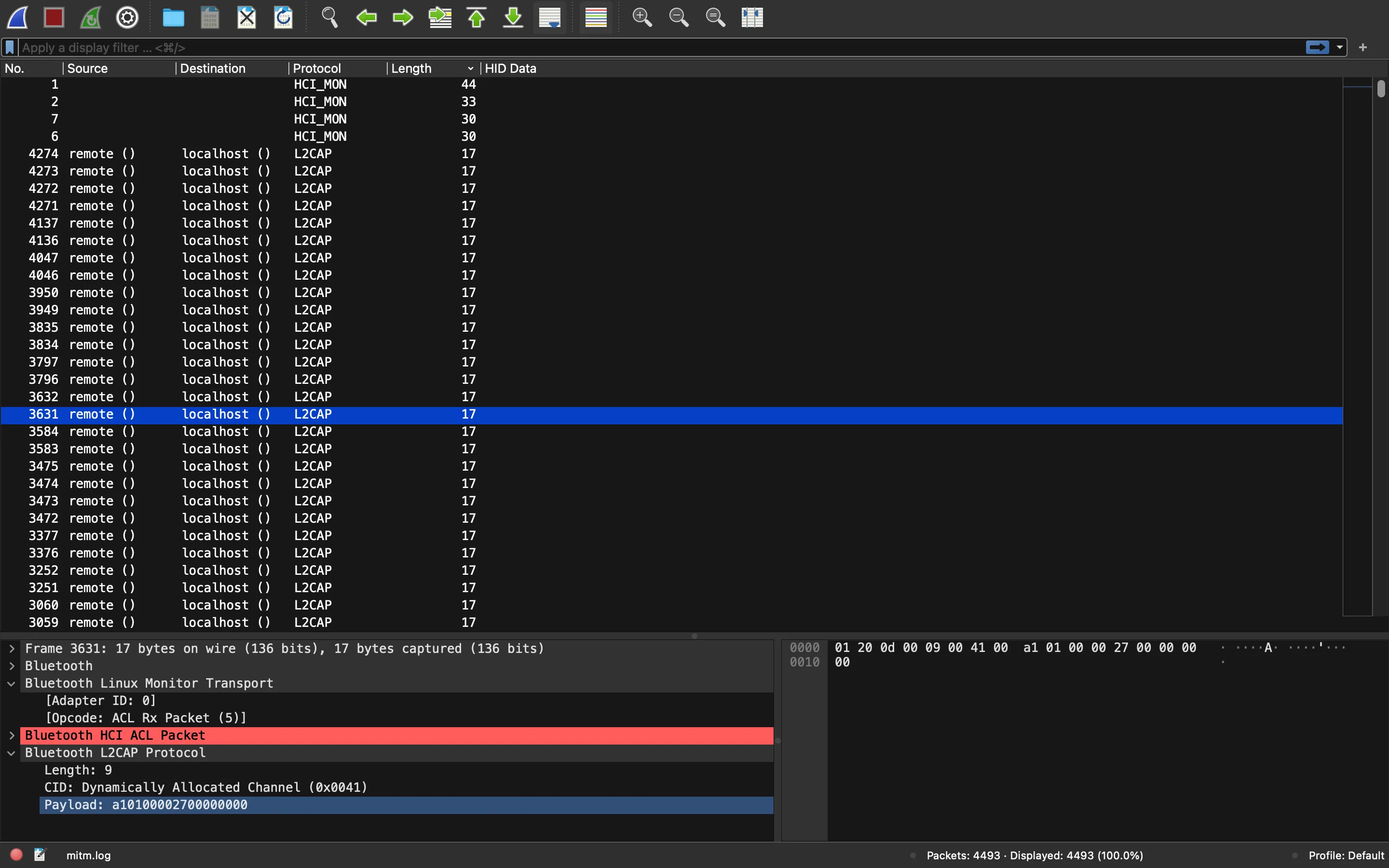
So, let’s filter them:
Let’s remove these payloads: a10100000000000000.
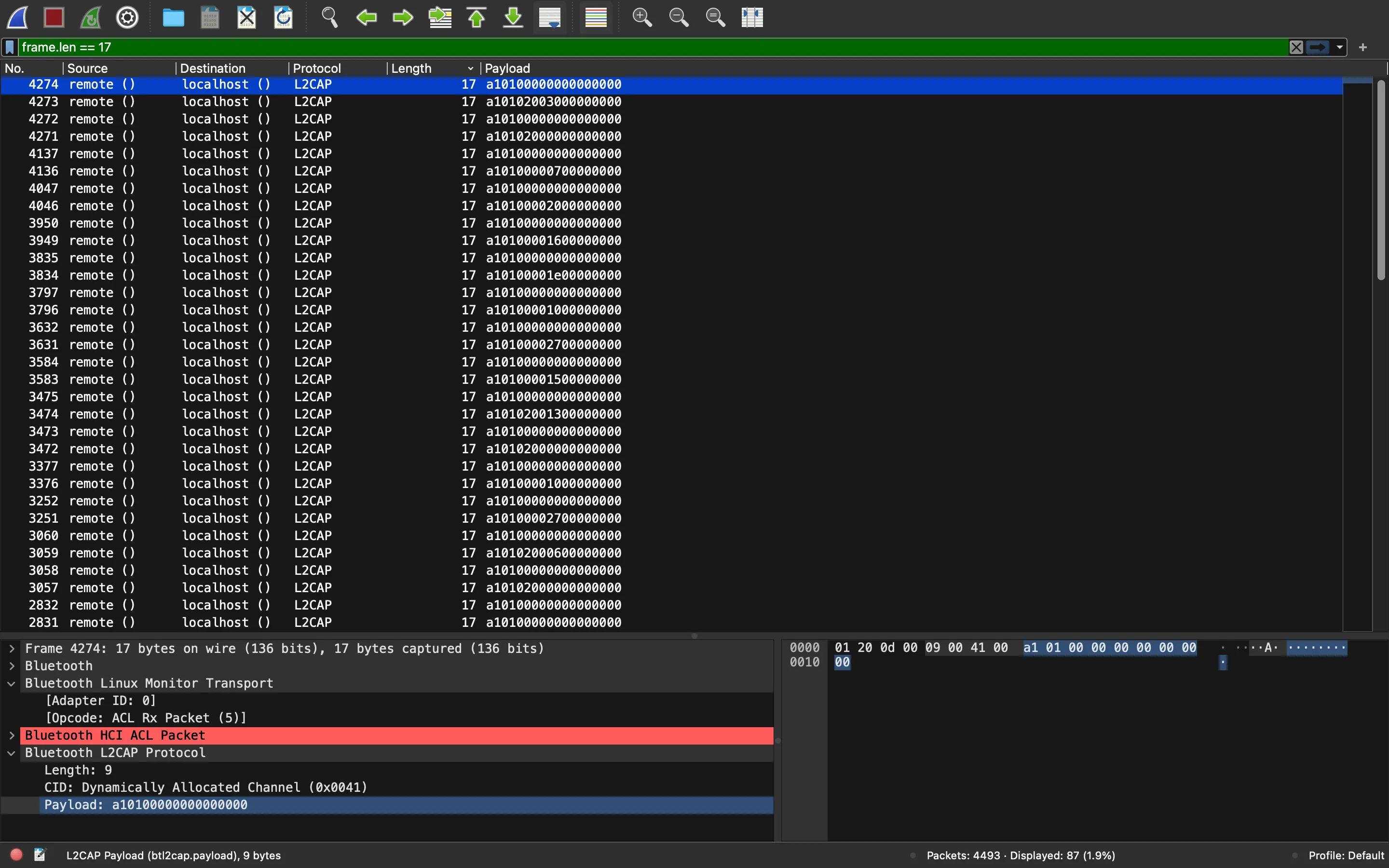
And also these ones: a10102000000000000.
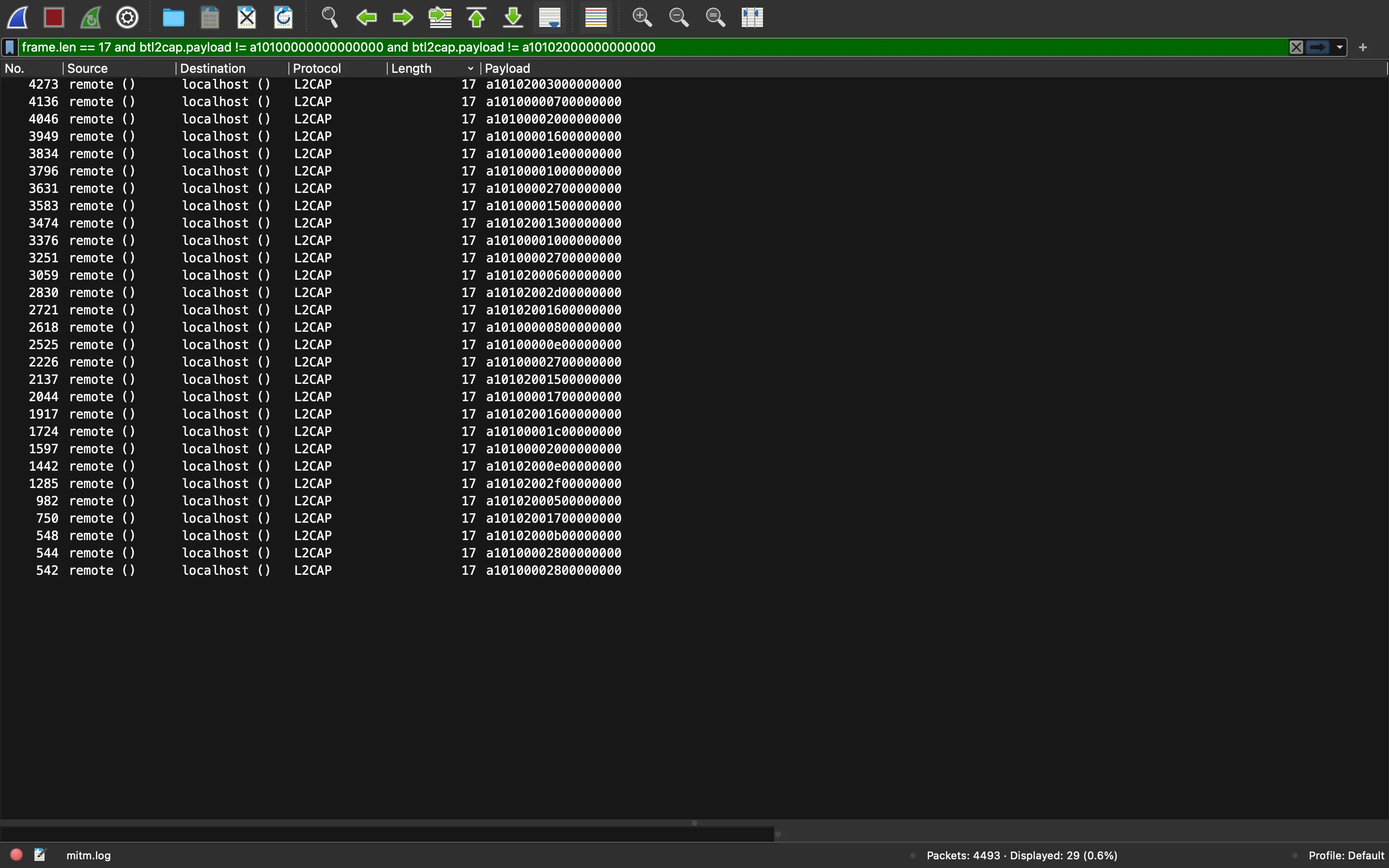
Alright, now we are left with all the key-stroke codes. The only thing we need to do is decode them.
Use of tshark
The above filtering can also be done with tshark from the command line:
$ tshark -r mitm.log | grep 'L2CAP 17 ' | grep -v a10100000000000000 | grep -v a10102000000000000 | awk '{ print $9 }'
a10100002800000000
a10100002800000000
a10102000b00000000
a10102001700000000
a10102000500000000
a10102002f00000000
a10102000e00000000
a10100002000000000
a10100001c00000000
a10102001600000000
a10100001700000000
a10102001500000000
a10100002700000000
a10100000e00000000
a10100000800000000
a10102001600000000
a10102002d00000000
a10102000600000000
a10100002700000000
a10100001000000000
a10102001300000000
a10100001500000000
a10100002700000000
a10100001000000000
a10100001e00000000
a10100001600000000
a10100002000000000
a10100000700000000
a10102003000000000
Decoding process
This time, I did the decoding manually, since there were some SHIFT keys involved (the ones that start with a101020):
ENTER - a10100002800000000
ENTER - a10100002800000000
H - a10102000b00000000
T - a10102001700000000
B - a10102000500000000
{ - a10102002f00000000
K - a10102000e00000000
3 - a10100002000000000
y - a10100001c00000000
S - a10102001600000000
t - a10100001700000000
R - a10102001500000000
0 - a10100002700000000
k - a10100000e00000000
e - a10100000800000000
S - a10102001600000000
_ - a10102002d00000000
C - a10102000600000000
0 - a10100002700000000
m - a10100001000000000
P - a10102001300000000
r - a10100001500000000
0 - a10100002700000000
m - a10100001000000000
1 - a10100001e00000000
s - a10100001600000000
3 - a10100002000000000
d - a10100000700000000
} - a10102003000000000
Flag
And here we have the flag: HTB{K3yStR0keS_C0mPr0m1s3d}.