Pinned
1 minute to read
We are given an APK file (pinned.apk) and a README.txt file:
1. Install this application in an API Level 29 or earlier (i.e. Android 10.0 (Google APIs)).
Dynamic analysis
Let’s start MobSF and Genymotion to do a dynamic analysis:
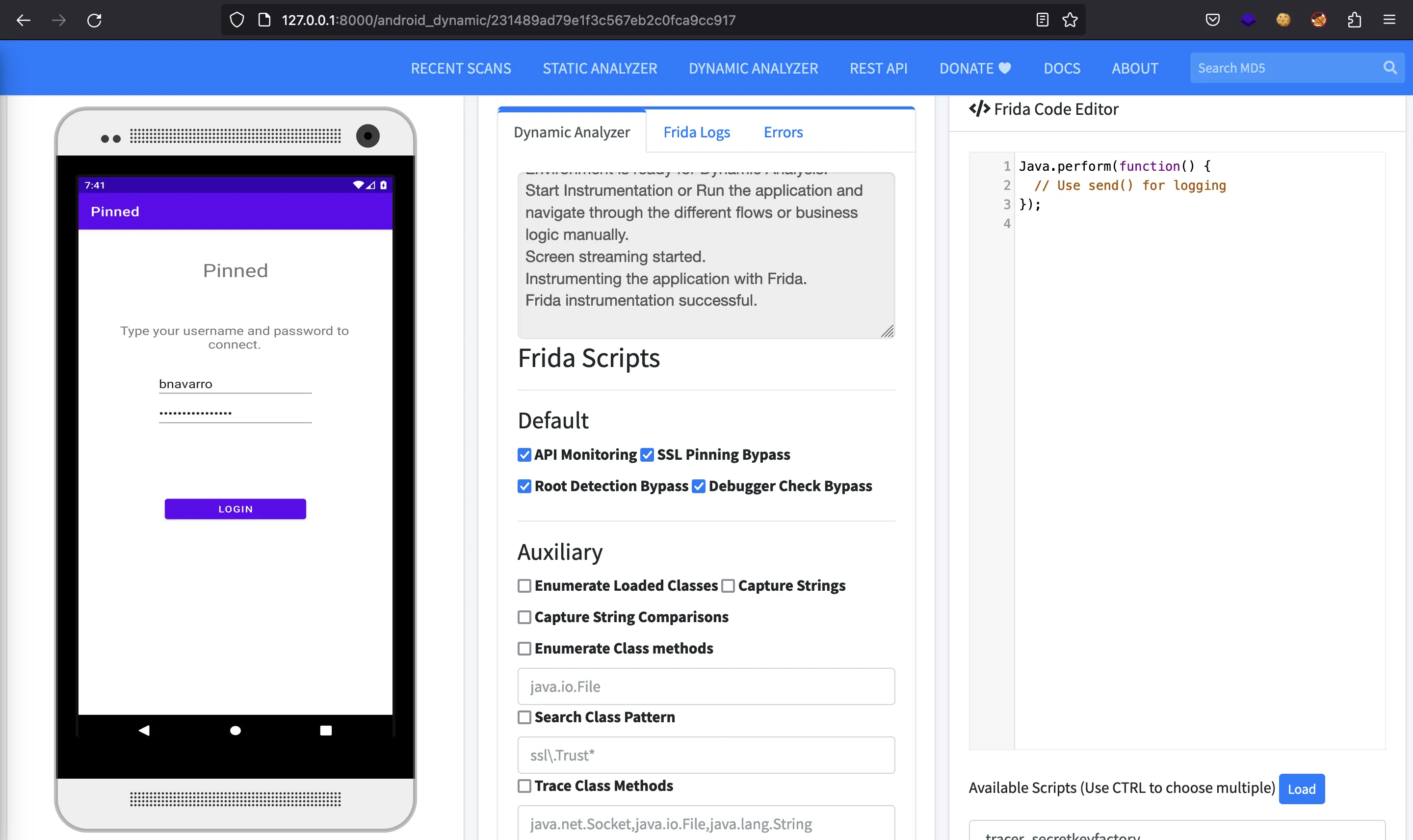
It simply shows a login form with the credentials already written. I was not able to read the password from there. If we click the button, we will see a successful message:
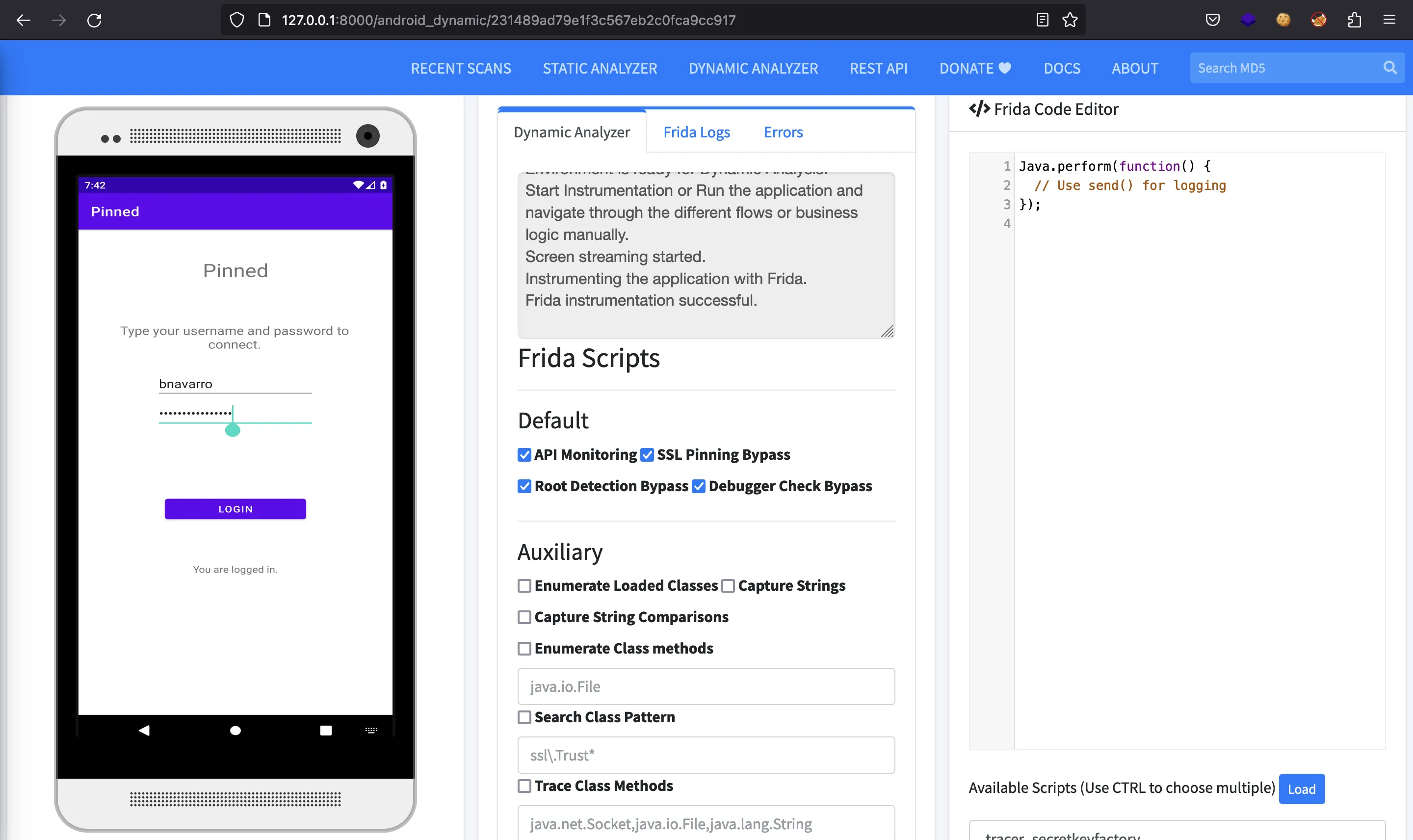
Solving the challenge
The challenge is probably related to SSL/TLS certificate pinning (because the challenge is named “Pinned”). However, I did not solve it with this approach.
I saw in the “API Monitor” tab some function calls and some interesting results:
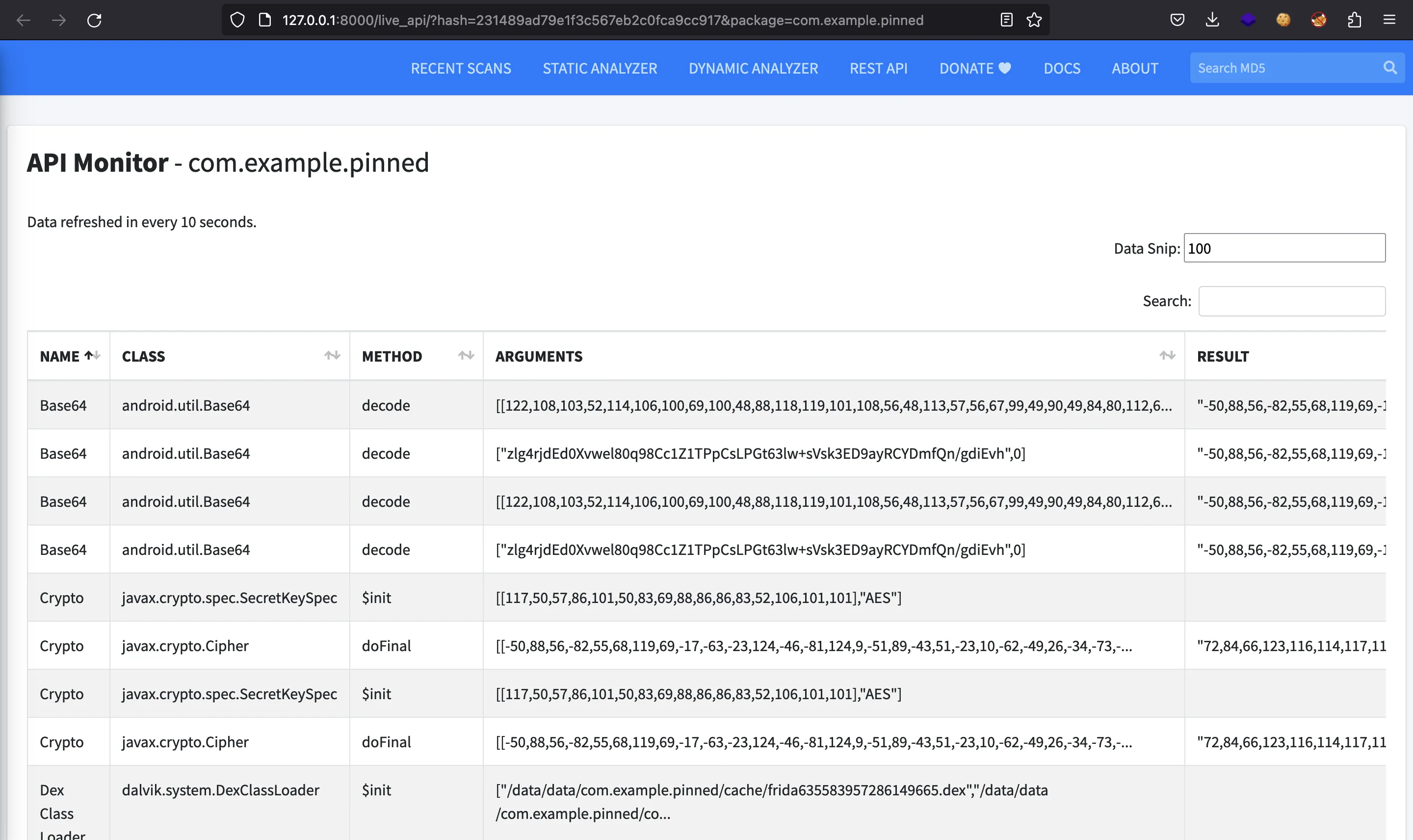
There are values 72,84,66,123,116,..., which are valid ASCII decimal codes for HTB{t. So, there was the flag. This “API Monitor” tab logs all calls to external Java packages (android.utils.Base64, javax.crypto.Cipher…), so we can guess that the flag was decrypted somehow and the result was logged. This is the full log:
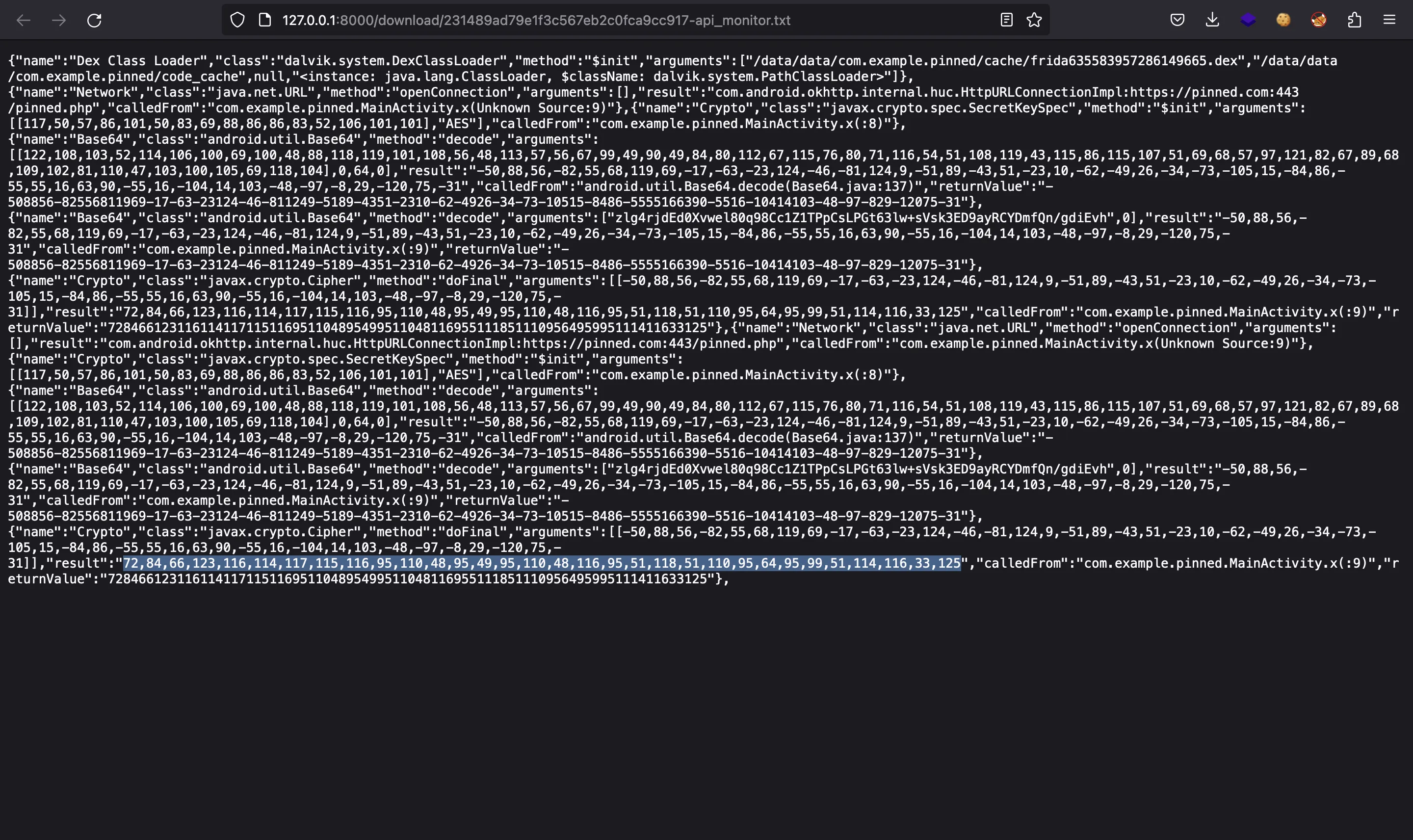
Flag
We can use Python to decode all ASCII codes to bytes and capture the flag:
$ python3 -q
>>> bytes((72,84,66,123,116,114,117,115,116,95,110,48,95,49,95,110,48,116,95,51,118,51,110,95,64,95,99,51,114,116,33,125))
b'HTB{trust_n0_1_n0t_3v3n_@_c3rt!}'