Find The Easy Pass
1 minute to read
We have a 32-bit binary called EasyPass.exe which is a Windows PE file:
$ file EasyPass.exe
EasyPass.exe: PE32 executable (GUI) Intel 80386, for MS Windows
If we execute the binary in a Windows machine, it will a password:
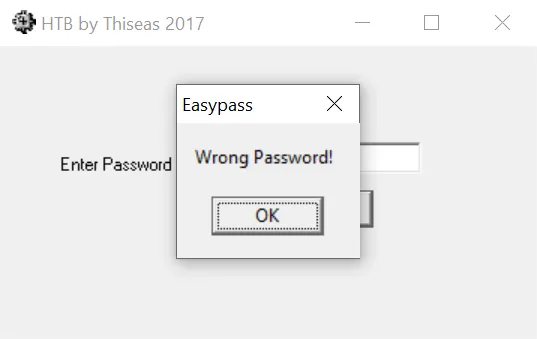
Since the password is wrong, we will see a message “Wrong Password!”:
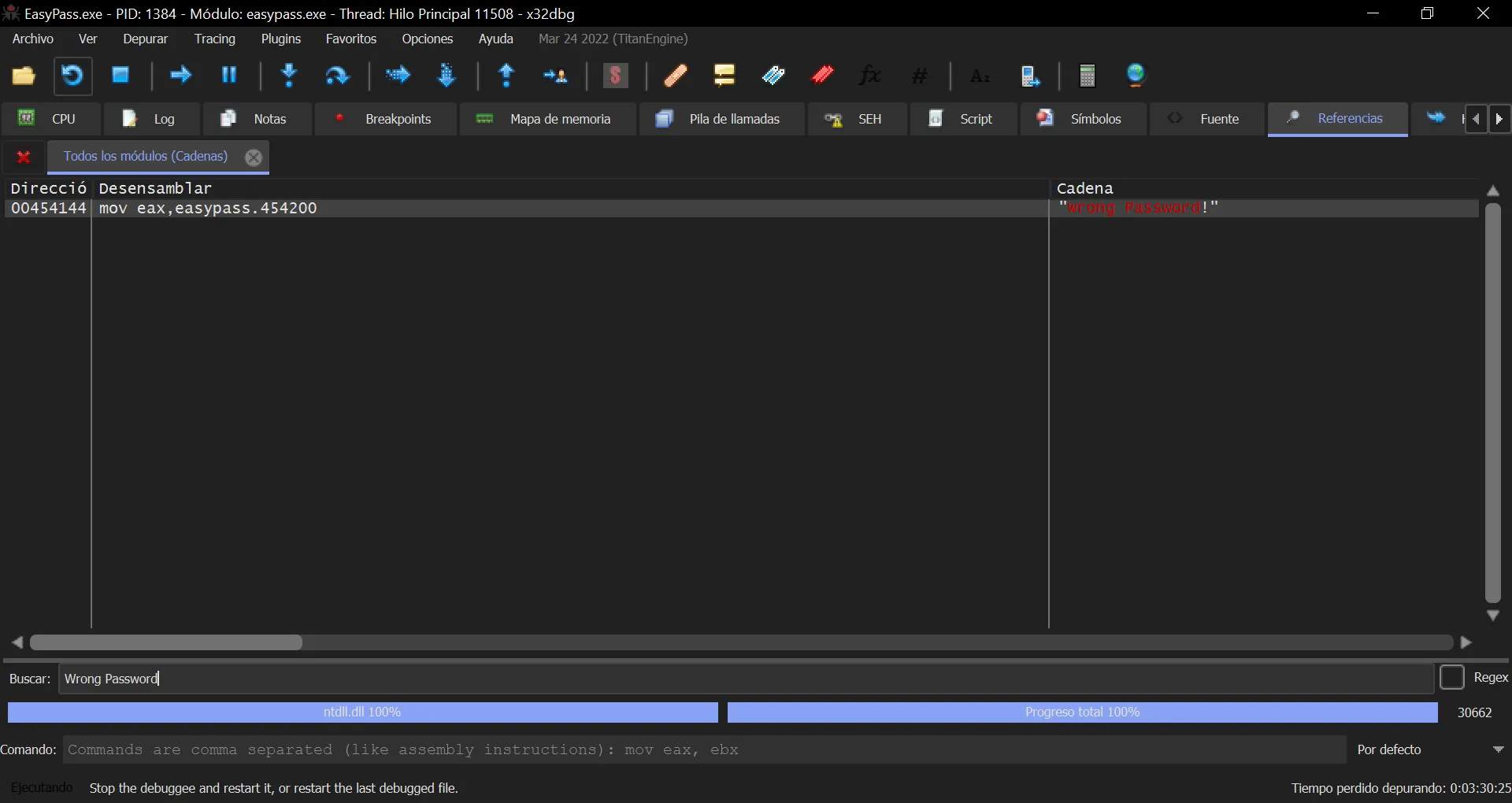
A static code analysis with Ghidra won’t be useful. Hence, let’s use a debugger like x32dbg to debug the binary. Once it is open, we can search for the previous error string:
And set a breakpoint into that address location (actually, at the jne instruction):
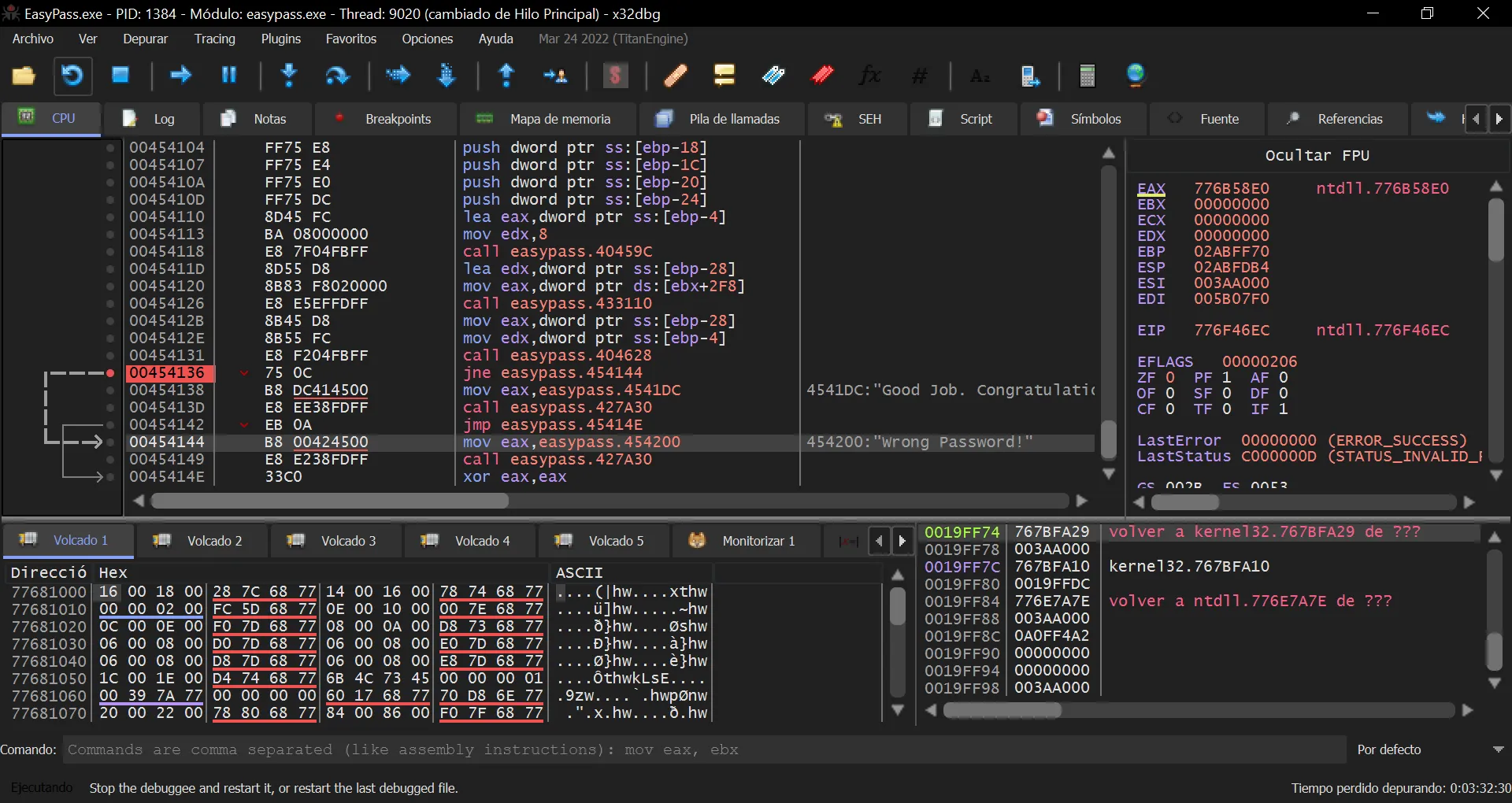
Once we run again the program, we will see the expected password:
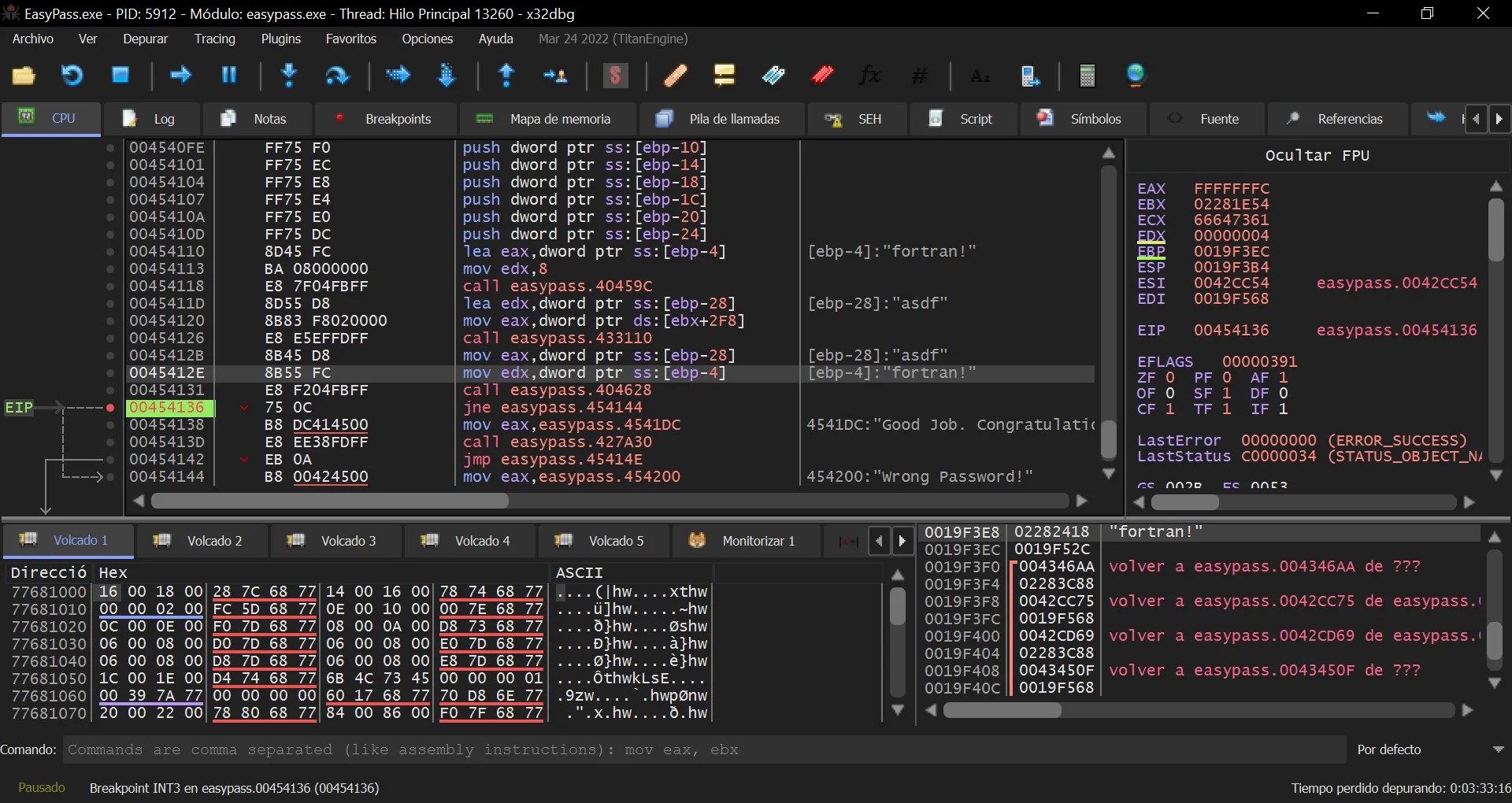
So the flag is: HTB{fortran!}.